A while back someone sent me a link to the following article, which discusses how to use the Python program EyeWitness in conjunction with Tor to screen shot .onion sites on the Dark Web: https://webbreacher.com/2017/09/02/dark-web-report-torghost-eyewitness-goodness/
EyeWitness can be found here: https://github.com/FortyNorthSecurity/EyeWitness and utilizes a background instance of FireFox to navigate to a .onion website and then screen shot it. You can take a list of links from a .txt file and have EyeWitness navigate to each one, take a screen shot (as well as capturing some other information), saving the results as a report in .html.
The idea behind it is great, but that post was published a couple of years ago, and when I got around to trying the same thing I couldn’t get it to work…..
As it turns out the most recent version of EyeWitness does not support the –proxy-type flag, and thus you can’t pipe the Tor requests through a proxy (which is required by Firefox to navigate Tor). After some tinkering and investigation, the last version of EyeWitness that supports the proxy option is 2.2.3, which is still available in the Releases tab on the EyeWitness GitHub repo: https://github.com/FortyNorthSecurity/EyeWitness/releases
################################################################################
# EyeWitness #
################################################################################
# FortyNorth Security - https://www.fortynorthsecurity.com #
################################################################################
[*] Error: You didn't specify a file! I need a file containing URLs!
usage: EyeWitness.py [--web] [--rdp] [--vnc] [--all-protocols] [-f Filename]
[-x Filename.xml] [--single Single URL] [--no-dns]
[--timeout Timeout] [--jitter # of Seconds]
[--threads # of Threads]
[--max-retries Max retries on a timeout]
[-d Directory Name] [--results Hosts Per Page]
[--no-prompt] [--user-agent User Agent]
[--cycle User Agent Type]
[--difference Difference Threshold]
[--proxy-ip 127.0.0.1] [--proxy-port 8080]
[--proxy-type socks5] [--show-selenium] [--resolve]
[--add-http-ports ADD_HTTP_PORTS]
[--add-https-ports ADD_HTTPS_PORTS]
[--only-ports ONLY_PORTS] [--prepend-https]
[--active-scan] [--resume ew.db] [--ocr]
EyeWitness is a tool used to capture screenshots from a list of URLs
Protocols:
--web HTTP Screenshot using Selenium
--rdp Screenshot RDP Services
--vnc Screenshot Authless VNC services
--all-protocols Screenshot all supported protocols, using Selenium for HTTP
Input Options:
-f Filename Line seperated file containing URLs to capture
-x Filename.xml Nmap XML or .Nessus file
--single Single URL Single URL/Host to capture
--no-dns Skip DNS resolution when connecting to websites
Timing Options:
--timeout Timeout Maximum number of seconds to wait while requesting a web page (Default: 7)
--jitter # of Seconds
Randomize URLs and add a random delay between requests
--threads # of Threads
Number of threads to use while using file based input
--max-retries Max retries on a timeout
Max retries on timeouts
Report Output Options:
-d Directory Name Directory name for report output
--results Hosts Per Page
Number of Hosts per page of VNC or RDP report
--no-prompt Don't prompt to open the report
Web Options:
--user-agent User Agent
User Agent to use for all requests
--cycle User Agent Type
User Agent Type (Browser, Mobile, Crawler, Scanner,
Misc, All
--difference Difference Threshold
Difference threshold when determining if user agent
requests are close "enough" (Default: 50)
--proxy-ip 127.0.0.1 IP of web proxy to go through
--proxy-port 8080 Port of web proxy to go through
--proxy-type socks5 Proxy type (socks5/http)
--show-selenium Show display for selenium
--resolve Resolve IP/Hostname for targets
--add-http-ports ADD_HTTP_PORTS
Comma-seperated additional port(s) to assume are http
(e.g. '8018,8028')
--add-https-ports ADD_HTTPS_PORTS
Comma-seperated additional port(s) to assume are https
(e.g. '8018,8028')
--only-ports ONLY_PORTS
Comma-seperated list of exclusive ports to use (e.g.
'80,8080')
--prepend-https Prepend http:// and https:// to URLs without either
--active-scan Perform live login attempts to identify credentials or
login pages.
Resume Options:
--resume ew.db Path to db file if you want to resume
RDP Options:
--ocr Use OCR to determine RDP usernames
After you’ve installed Tor (apt get tor and then
For example, if we look at the following 10 .onion links (links redacted for what I hope are obvious reasons).
And then run EyeWitness with the following options: python EyeWitness.py –web –timeout 60 -f links.txt –proxy-type socks5 –proxy-ip 127.0.0.1 –proxy-port 9050
It does a little thinking, and there are a few problems:
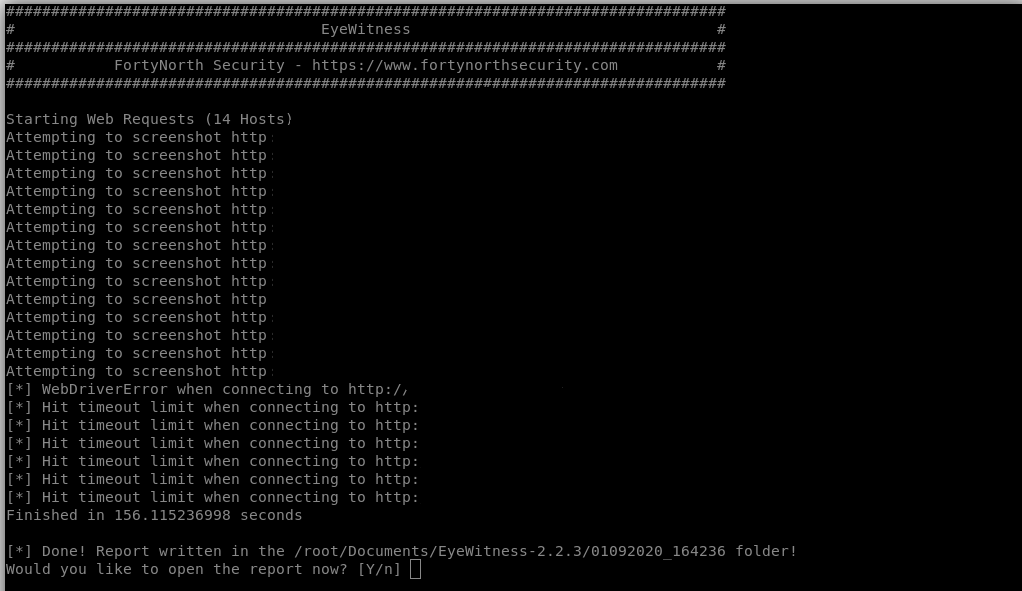
We see that based on response time from the .onion site, and the timeout limit, the results in our HTML report will not be in order. Additionally, there’s a bit of a problem regarding re-directs, in the sense that the .html report states there was an “unknown error” but when we click on the link, the site loads without any issues.
Further investigation is in order. I will update this post as I learn more.
Have you ever thought about creating an ebook or guest authoring on other sites? I have a blog centered on the same ideas you discuss and would love to have you share some stories/information. I know my viewers would appreciate your work. If you are even remotely interested, feel free to shoot me an e-mail.
Norma ISO 10816
Dispositivos de equilibrado: esencial para el desempeño suave y óptimo de las dispositivos.
En el entorno de la avances actual, donde la efectividad y la estabilidad del aparato son de máxima trascendencia, los dispositivos de calibración cumplen un función esencial. Estos dispositivos específicos están concebidos para equilibrar y estabilizar componentes móviles, ya sea en maquinaria industrial, medios de transporte de movilidad o incluso en equipos de uso diario.
Para los expertos en soporte de aparatos y los profesionales, utilizar con aparatos de balanceo es crucial para proteger el funcionamiento uniforme y seguro de cualquier aparato dinámico. Gracias a estas herramientas innovadoras avanzadas, es posible reducir sustancialmente las vibraciones, el estruendo y la carga sobre los cojinetes, extendiendo la duración de elementos valiosos.
De igual manera trascendental es el papel que desempeñan los aparatos de ajuste en la soporte al comprador. El apoyo experto y el reparación regular aplicando estos sistemas permiten proporcionar servicios de alta excelencia, elevando la satisfacción de los compradores.
Para los titulares de emprendimientos, la contribución en equipos de equilibrado y dispositivos puede ser esencial para aumentar la efectividad y eficiencia de sus equipos. Esto es sobre todo significativo para los emprendedores que dirigen reducidas y intermedias emprendimientos, donde cada aspecto cuenta.
Asimismo, los aparatos de calibración tienen una amplia uso en el campo de la protección y el supervisión de estándar. Posibilitan identificar eventuales fallos, evitando arreglos caras y perjuicios a los aparatos. Además, los información recopilados de estos equipos pueden utilizarse para maximizar procedimientos y potenciar la visibilidad en sistemas de consulta.
Las sectores de implementación de los sistemas de balanceo abarcan numerosas sectores, desde la manufactura de transporte personal hasta el seguimiento ecológico. No importa si se habla de extensas manufacturas manufactureras o reducidos establecimientos caseros, los dispositivos de balanceo son necesarios para garantizar un operación eficiente y sin riesgo de detenciones.
demais este conteúdo. Gostei bastante. Aproveitem e vejam este conteúdo. informações, novidades e muito mais. Não deixem de acessar para aprender mais. Obrigado a todos e até a próxima. 🙂